Welcome back, my novice hackers! The worst thing that can happen to any hacker is being detected by a security admin, the security technologies (IDS, firewall, etc.), or a forensic investigator.

Update: April 24, 2014 Looks the the one day availability was a precursor to a wider launch, as now anyone can buy a pair of the Glass Explorer Edition without needing an invite. Check out Google's Glass Shop for some easy ordering, still with the $1500 price tag.

While it may be impolite to play around on a smartphone at dinner, having it consume my attention while I'm on a deadline or trying to study can prove disastrous. With Netflix and social media just a tap away, it's a dangerous game of wills, one that the phone usually wins.

There's been a lot of discussion lately about the practical uses of Google Glass. Sure, you can use them for translating text instantly or further engraining yourself in social media, but how about saving someone's life? That's precisely what Dr. Steven Horng of Beth Israel Deaconess Medical Center has says happened with a recent patient of his. After launching a Google Glass pilot program late last year, the device was seen as a critical factor in saving the life of a patient in January.
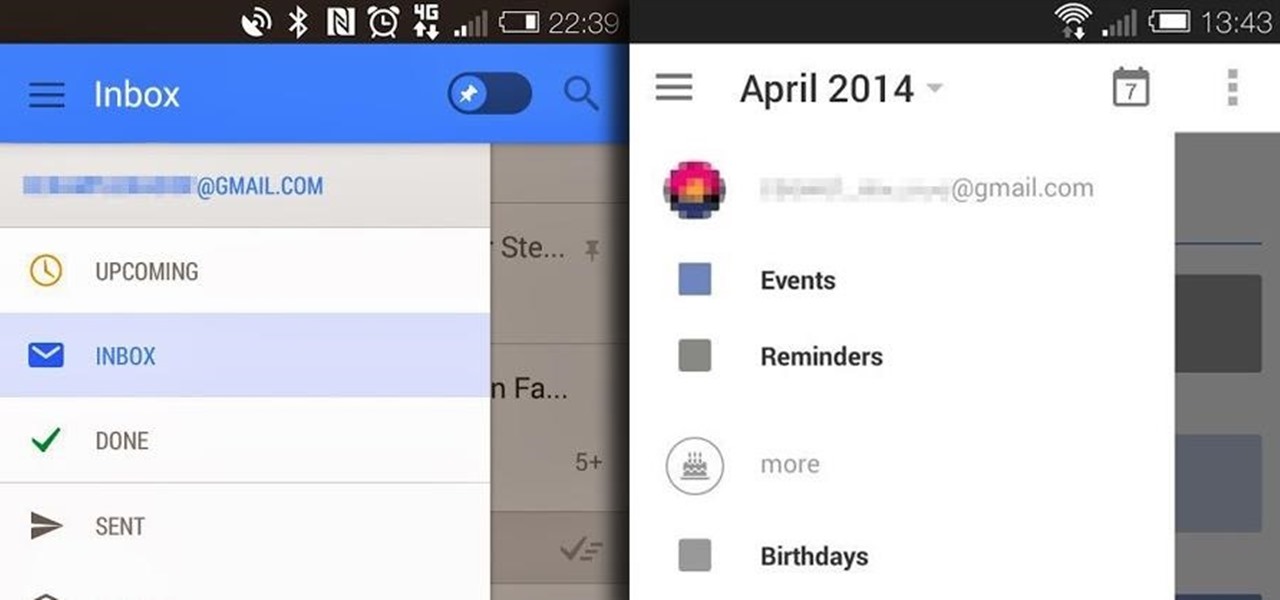
Google I/O may still be a couple of months away, and although we don't expect anything groundbreaking—no new Android versions, just fixes to KitKat—we could be treated to some new apps. No, not Pokémon inspired Maps, rather new versions of Google's Calendar and Gmail apps.

Earlier this morning, Twitter announced (through a tweet, naturally) that it has acquired Cover, roughly a minute after Cover made the same announcement. Cover Lock Screen, a lockscreen replacement app, has been vastly popular during its first year. The app places relevant shortcuts on your lockscreen that adapt to your habits, so whether you're at home, work, or in the car, you'll find the apps you use the most in these situations readily available for you. For more information on Cover, inc...

From personal photos and videos to online banking passwords saved in your web browser, your phone has all kinds of sensitive data that needs to be protected. One of the best things you can do for your Samsung Galaxy S4's data is have a lock screen with a hard-to-guess PIN or password.

Facebook makes it easy to show how much you appreciate a funny status, great picture, or cool news article using their iconic "thumbs up" button, but what about those terrible jokes and annoying baby pictures? Where's the "thumbs down" for that crap?

Welcome back, my novice hackers! This next subject might seem a bit obscure, but I promise you, this lesson will benefit you significantly either as a hacker or system admin. This tutorial will cover what is usually referred to as a regular expression, or regex for short.

Texting something as simple as "What up, bruh?" can be transformed into something way more baller by adding emojis, emoticons, GIFs, and textspeak. Some people would even argue that texting is a form of art, similar to Shakespearean sonnets, but it still has a ways to go if you ask me.

Welcome back, my fledgling hackers! As nearly everyone has heard, Target Corporation, one of the largest retailers in the U.S. and Canada, was hacked late last year and potentially 100 million credit cards have been compromised. Happening just before Christmas, it severely dampened Target's Christmas sales, reputation, and stock price (the company's value has fallen by $5B).

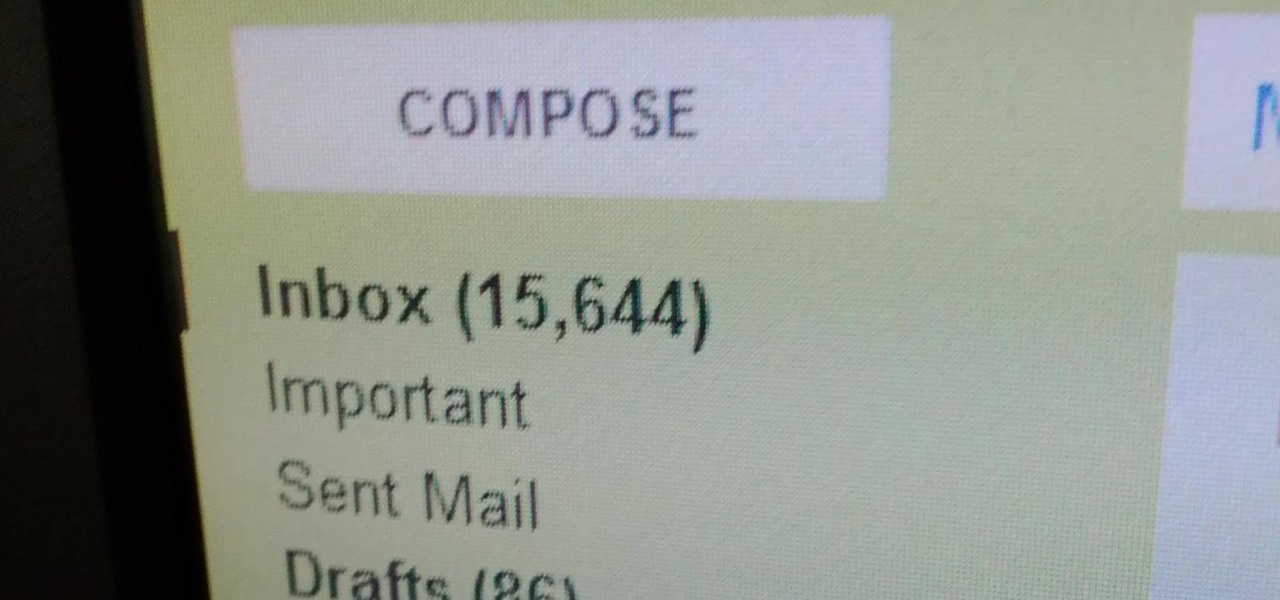
As of this week, Gmail is going to start letting Google+ users email each other using a new option called "Email via Google+." There's nothing wrong with making it easier to get in touch with people you want to hear from, but the default setting allows anyone with a Google+ account to send a message to your Gmail inbox. After the feature is in use, Gmail will start to suggest Google+ connections along with your other contacts as recipients. Email addresses will not be displayed for Google+ co...

For those of you who have (or had) and iPhone, one of the cooler photo apps for iOS was VSCO Cam, an extremely popular camera with pro-quality filters and effects. Now this app is available for Android on Google Play for your Nexus 7 tablet and any other devices running Android 4.0 and up.

Snapchat was created for the sole purpose of removing evidence from your mobile that a photo or video ever existed. That way, snoopers can't find any of these questionable selfies in your photo gallery. Of course, there are plenty of ways around this safeguard, but it's still more private than the standard social networking app.

I'm still amazed by all the things some people just don't know. Script-kiddies often refer to Metasploit if someone asks them how to hack a computer because they think there's simply no other way. Well here I am today trying to increase your set of tools and -of course- skills.

When the HTC One was announced, the fact that its IR transmitter was a side note more than a main feature made me dismiss it. When Samsung included one in the GS4, it became even less impressive. However, now that I actually have a One, I find that the "TV" app is way more than just one of Samsung's "S"-gimmicks. Step 1: Set Up Your Service Provider

The newer HTC One is arguably the best smartphone yet in terms of hardware, but its software moves considerably farther away from the stock Android experience. Even more so from HTC's own Sense.

As we all know, our attention spans are much shorter now that we're accustomed to getting information and news in tiny snippets via text messages, tweets, instagrams, and other constant updates.
Your company is deciding on starting new projects but there is a lot you need to do to make sure these projects are right for your company and will be financially rewarding to the bottom line. Before you begin you and your project management team will need to go through a Project Evaluation Process.

Self-restraint is one of the hardest thing to do. I'm a world-class procrastinator, and one of the biggest causes for my procrastination is my iPhone. Temple Run 2 was probably the best and worst thing that could have happened to me.

Being politically correct on social media sites is super boring. I've had my fair share of rage tweets and angry Facebook posts with some colorful wording, but sometimes using and F-bomb just gets the point across better. Now that Facebook is pushing out their new Graph Search, it might be time to clean up your profile. FaceWash is a web app that searches your Facebook profile for common bad words. You will need to give the app permission to access all of your wall posts (or course). Once acc...

Social media is where we post our thoughts for the world to see, but sometimes a little more exclusivity is needed. And that's where Scrambls comes in.

Humans clearly demonstrate altruistic tendencies towards other members of groups with which they identify.

There was recently a case that came to national attention where a gentleman was arrested at an airport for having a watch that looked like a bomb, among other things. As it came out, the watch was, in fact, not a bomb, and the man was just an artist who was probably trying to make a statement of some sort. Well, that message was lost amongst the hail of people shouting that either he had been stupid for bringing that watch on the plane and so deserved to be arrested, or that it's a free count...

Dianne Tice and Roy Baumeister gave a bunch of college students a questionnaire in which the students answered questions about their work habits. In a class which she taught, Tice also assigned a paper with a deadline which she said could be extended and observed which students availed themselves of the option to extend.

If you have a lot of friends on Facebook, chances are that every day is at least one of their birthdays. If you took the time to individually post a message every time, you'd spend ALL of your time on Facebook, but you don't want to be a bad friend either. Let's face it, some people take this stuff personally.

If you're like me, getting as much sleep as possible is priority number one. With more and more time spent on or around our cell phones, it's becoming harder and harder to block out all the noise.

With presidential voting going down on Tuesday, November 6th, voters are beginning to anchor down on their choice for president. But with the way the media works, this may be difficult for some people because the news sites they listen to give conflicting and sporadic information on the candidates.

An internet connection has become a basic necessity in our modern lives. Wireless hotspots (commonly known as Wi-Fi) can be found everywhere!

Numerous studies have shown that people are over-confident in their own abilities. Most people, for example, think that they are better drivers than average.

As if you needed another reason to lock down your Facebook profile, the company's sketchy new partnership with data mining firm Datalogix is geared towards giving advertisers more information on what you're doing—even when you're not online. It's just not enough that they can target ads based on your preferences, now they want to know how those ads are influencing your buying habits in the real world.

If you've ever logged on to the popular music application Pandora, your password is saved onto that computer in the local storage...for good.

There have been plenty of headlines recently about fake followers in both politics and entertainment. Everyone gets hit by a spam account here and there, but when a large percentage of someone's followers are fake, it can look pretty bad, especially with influential people being accused of buying their followers to look more popular.

Adding a peephole to your front door is a cheap and simple way to improve home security. This how to video shows you what to consider and how to install a peephole.

How to Hide IP from Hackers. Hide your IP address to get more security. Hotspot Shield (free) change your IP address and your location. To see the changes visit http://www.ip-adress.com/ before and after running program.

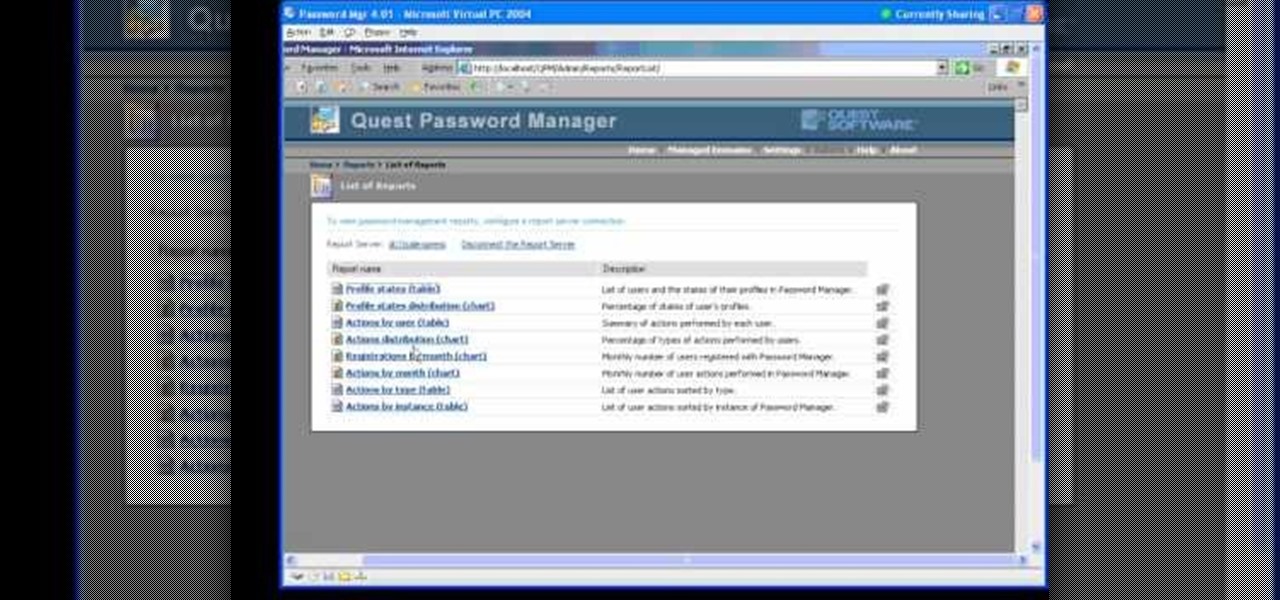
In this Webcast, Password Management for Windows and Beyond, you will learn how to: Increase security standards cross-organization by easily customizing and enforcing password policies for Windows, Unix, Linux, and Java users.

Watch as Karen's password is retrieved - both by hypnosis and with the help of technology. Plus, learn how to improve your password security.

There's a lot of fighting to endure in the Xbox 360 game Bayonetta. In Chapter 1 - The Angel's Metropolis, it's your first real battle. Central Station Platform - Go to the far side of the platform and go through the security gates. The door on the far side of this hall is locked, but on one wall in the hallway you'll see a strange sphere. Walk up to it and start doing combos to open a door.

Facebook is the most powerful social network web site that helps you to connect and share with the people in you life. You need to register an account with the face book website, which is free of cost, to use their service. In face book home page you can show others your live status updates. To do this first log in to your face book application. From the left hand side column select the status updates link. This opens the 'Status Updates' web page, where you can see the status updates of all ...

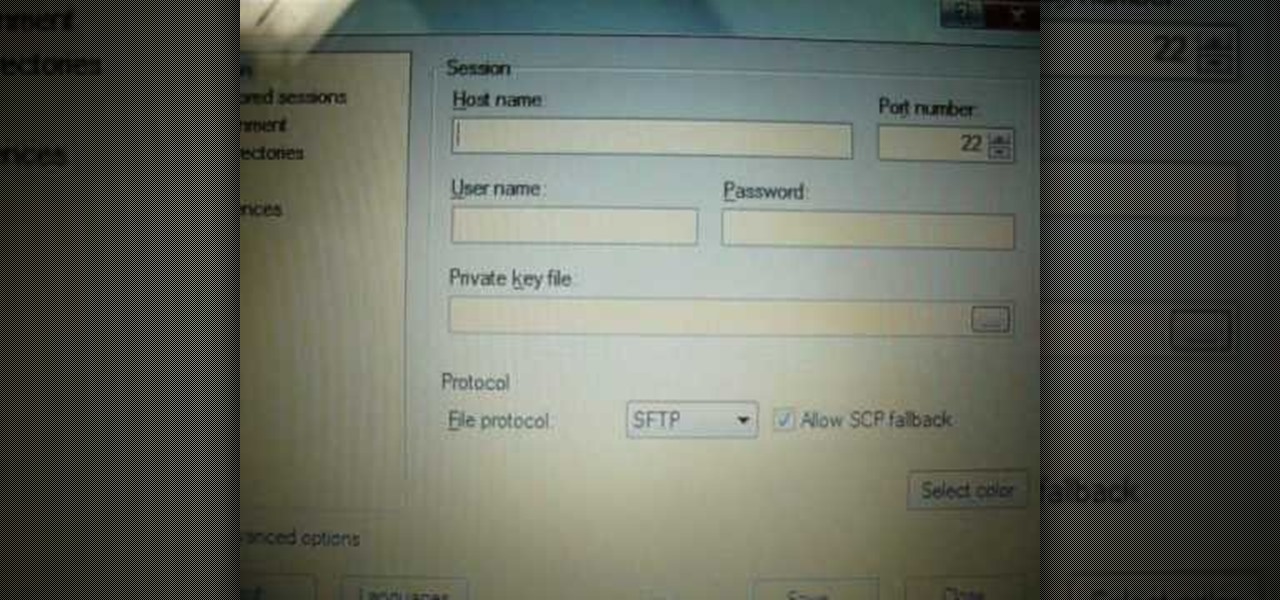
iPodTouchedMaster shows how one can easily SSH into their iPod Touch with all firmware! To SSH is the ability to hack into your iPod Touch's file system. First, your iPod Touch must be jailbroken. Next, you'll have to open Cydia. Click "Featured Packages" or search for the terms "Open SSH" (it will be listed under Console Utilities & Daemons). When you have OpenSSH click on it and click 'Install' and 'Confirm'. After this is finished, click return to 'Cydia'. This may take a lot of battery po...