Kipkay has developed a shoplifting prank, and all you need is a little electromagnetic strip to play this prank at Walmart (or wherever). You also need to bring a magnet. You swipe the strip thirty times with the magnet and this will actually magnetize the strip. Use this as inspiration for one of your April Fools Day pranks!
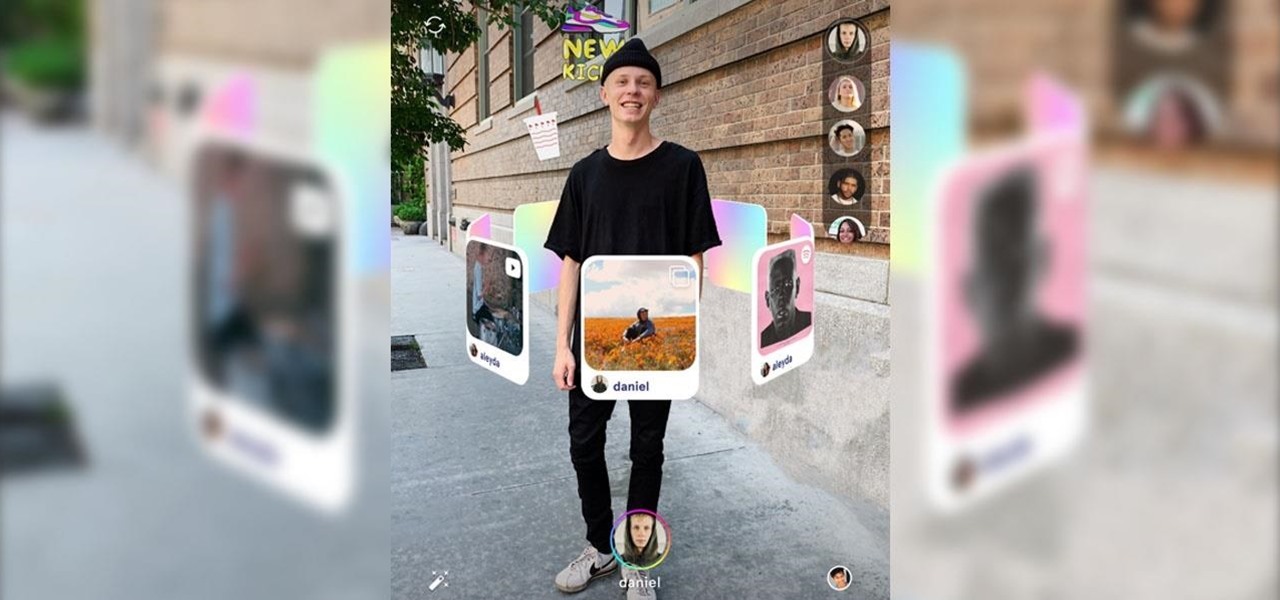
In a world full of augmented reality camera effects apps, one app is going in a more social direction.
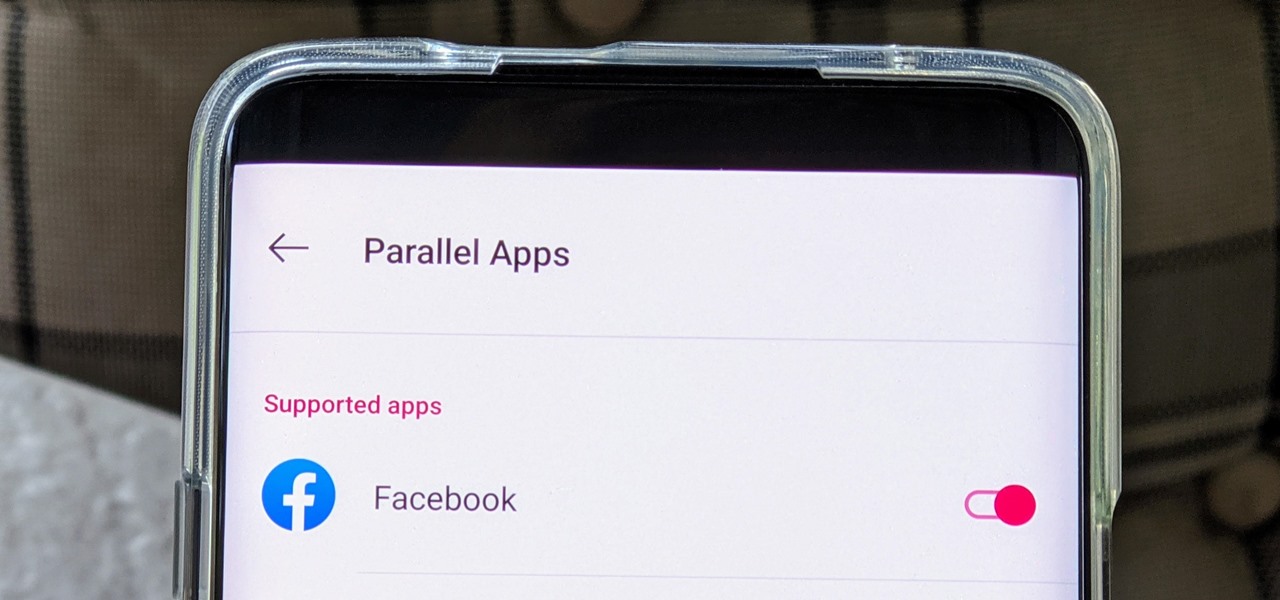
The Facebook app only supports one account being logged in at a time — but what if you need one for work and one for your personal life? That would normally involve logging out and logging in every time you need to switch accounts, but your OnePlus device offers a much better solution.

One of the biggest advantages of the front-mounted ultrasonic fingerprint sensor found on the Galaxy S10 and S10+ is that you no longer have to physically pick up your device and reach around the back to unlock it. Instead, you simply place your finger on the screen for easier access and added convenience — at least on paper.

The macOS 10.14 security update tried to make parts of the operating system difficult for hackers to access. Let's take a closer look at how its new feature works and what we can do to spoof the origin of an application attempting to access protected data.

When BlackBerry made the move to Android OS, they were aware of the limitations it presented. Unlike with BB10, they didn't create the operating system and would have to deal with the vulnerabilities already included. As a result, they added numerous security enhancements, and at the heart of this is DTEK.

A massive leak appeared the web today, and it's got some huge security implications for every iPhone on the market. On the plus side, it also has some potential for enabling deep-level modifications and jailbreak tweaks.

While Snap's third quarter financial reports disappointed Wall Street, China's Tencent took the opportunity to expand its investment in the social media company.

As the level of data being generated grows exponentially, past the Information Age and into the coming Hyper-Information Age of immersive computing — as resistant as many of us are to the idea — personal data security is becoming a necessary consideration in our everyday lives. Recognizing this, Mastercard, Qualcomm, and Osterhout Design Group have teamed up to show what secure shopping could look like in the very near future with iris authentication.

Due to the overnight success of smartphones, millions of people are connecting with others. Currently, over 15 million text messages are sent every minute worldwide. Most of this communication is happening in the open where any hacker can intercept and share in the discussion unbeknownst to the participants. However, we don't need to communicate insecurely.

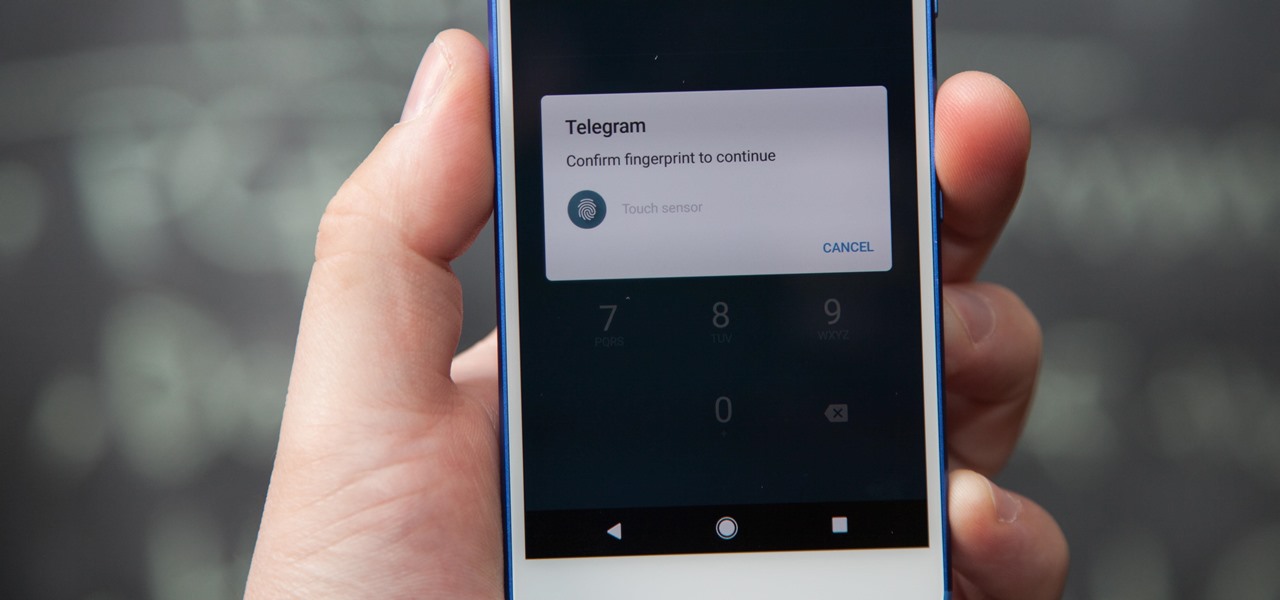
If you're using Telegram for its "Secret Chats" feature, which provides end-to-end encryption for your messages, then I'd highly recommend locking down the app itself with a passcode, PIN, or password. While your phone itself may have a secure lock screen already, if that gets compromised, you'll at least have an extra layer of security on your important conversations.

When you first set up an iPhone, you'll be prompted to create a six-digit passcode to unlock your screen and access certain system settings. If you skip this step, you can always go back and create one, which we highly recommend. Without a passcode, everything on your iPhone is accessible by anyone who gets their hands on it — nosey friends, hackers, thieves, local law enforcement, the FBI — and you don't want that, do you?

Apple has yet to create a successful social networking app, but that doesn't mean they want to be left out of the social video conversation. Case in point: Today they announced a new video app set to debut for iOS in April called Clips.

A market research report, posted on February 27, 2017, forecasts that the image recognition market will grow to nearly $40 billion worldwide by 2021. The market, which includes augmented reality applications, hardware, and technology, generated an estimated $15.95 billion in 2016. The report estimates the market to grow by a compound annual growth rate of 19.5% over the next five years.

BlackBerry has formally announced the arrival of its flagship, the KeyOne, during Mobile World Congress 2017 in Barcelona. The all-Android KeyOne looks distinctly BlackBerry, with its 4.5" screen and physical QWERTY keyboard. Here's the lowdown on this elegant handset that hearkens back to BlackBerry's heyday, which had previously been known by its code name, the BlackBerry Mercury. Aluminum Unibody with Physical Keyboard

Starting with the Priv, BlackBerry's become an Android manufacturer. This move gives BlackBerry's phones access to Google's sizable app store, but it also presents several hurdles to keeping the security brand they've built intact.

Social Engineering was mentioned a few times here on Null Byte, but not very many explained what it is, or how to do it. I love this quote because it's true: Social Engineering is the key to carrying out client side attacks, and all you need is a little creativity!

Thanks to a couple of photoshopped images that made rounds across Twitter last year, iPhone users were duped into thinking that iOS 8 included a security feature that would lock individual apps. Of course, none of it ended up being true, but we covered other features and apps that could accomplish roughly the same thing.

Yes, "Safer Internet Day" is a real thing, and it's actually been around for 12 years. This year, Google again will be commemorating the event by giving away a 2-gigabyte storage bump for their Google Drive cloud service if you simply run through a security checkup.

Losing your phone is a much bigger ordeal today than it was just 10 years ago. Our smartphones carry with them lots of sensitive data that, in the wrong hands, is capable of being used for identity theft and fraud.

This tutorial is about how to create the floating bar with social media buttons on a weebly website. Weebly has change its layout on the dashboard. Its a new video of new layout of weebly dashboard. I found many quesiton regarding 4 different HTML files instead of one index.html. Users were asking about in which they have to change the code so here is the solution. Watch the video, drop your comments and feel free to ask.

While websites may run smoothly without any noticeable vulnerabilities, there's always the looming threat that any background weakness in the site can be exploited by hackers. Once a site is compromised, it can be difficult to get it fixed without the proper help. Google has recently launched a new series entitled "Webmasters help for hacked sites”, which teaches web developers and site owners how to avoid getting hacked and how to recover their website if it gets compromised in any way.

We've all had that awful, sinking feeling when something you've been typing away at is suddenly gone. Maybe you accidentally hit the Back button, lost your internet connection, or your computer crashed, but whatever the reason, losing your work totally sucks. A lot of word processing programs have a built-in auto-save feature to prevent you from losing everything, but most websites and blogs haven't gotten there yet. An extension for Chrome and Firefox called Lazarus: Form Recovery can help y...

It's no secret that there's a lot of surveillance going on these days. It's easier than ever to end up in a database, and even former government agents are speaking out about the atrocious amount of spying being done against our own citizens. They've targeted our laptops, cars, IP addresses, and now they're coming for our iPhones. AntiSec hackers managed to get their hands on a list of over 12 million Apple UDIDs (Universal Device IDs) from an FBI computer, and they published 1,000,001 of the...

Curious about Google's new social network, Google+? Get the rundown by watching this video and learn the ins and outs of Google plus, including the circles feature, the chat feature, photos and more. This is your video guide to Google+.

Check out this video for an introduction to the new Google+ app for iOS. You can use Google plus from any of your iDevices, including iPhone, iPod Touch and iPad. Make the most of Google's new social network with this app.

If you're using Social Media to promote your business, don't forget to promote yourself as well. Put a face to your Facebook page by watching this video and learning how to display the Page Owner feature on your business' Facebook page.

Facebook is a great tool for businesses. Watch these videos to learn how to maximize the effectiveness of your business' Facebook page. Reach out to your customers with social media and networking with the methods demonstrated in these how to videos.

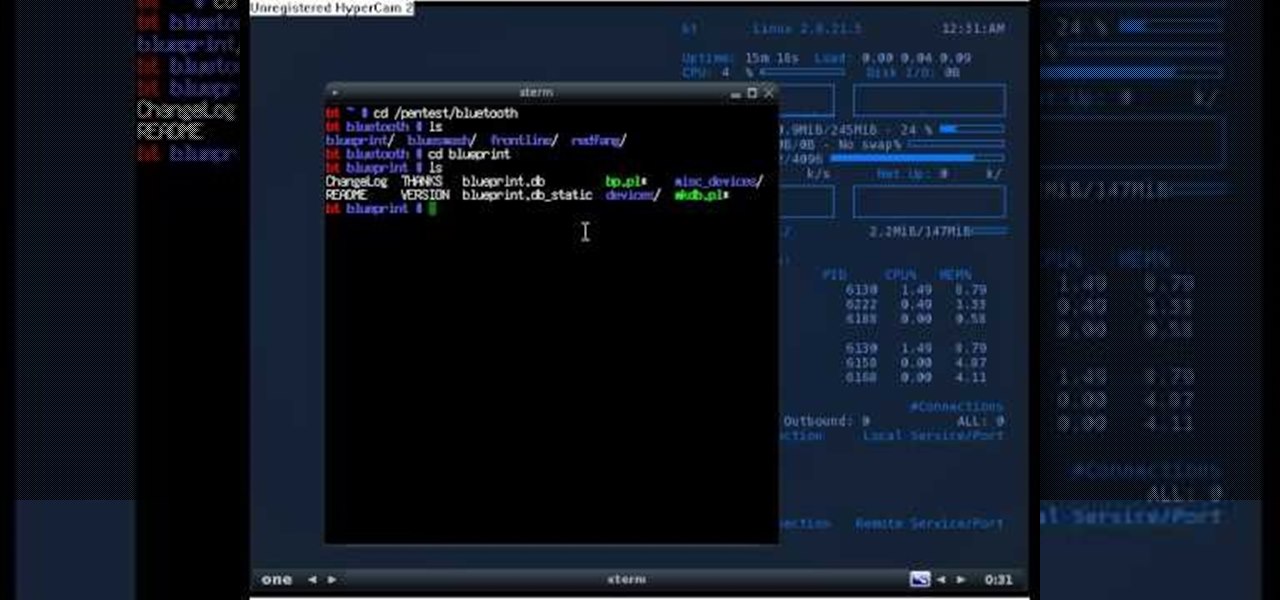
If you're new to the Bluetooth hacking world, here's a little background on using Linux BackTrack to hack a Bluetooh device: Linux Backtrack is a Live DVD device that offers security tools - like password crackers - that allow you penetrate networks.

This tutorial will let you hack into a wide selection of web cams and online security cameras. The hack is actually quite easy, and is best done with a browser like Mozilla Firefox. Navigate to Google in your browser, and then type in "inurl:viewerframe?mode+refresh". This piece of code will open up a list of active webcams. Then just surf through your choices and watch whatever you want. You can even change the camera angle and zoom in and out of the picture!

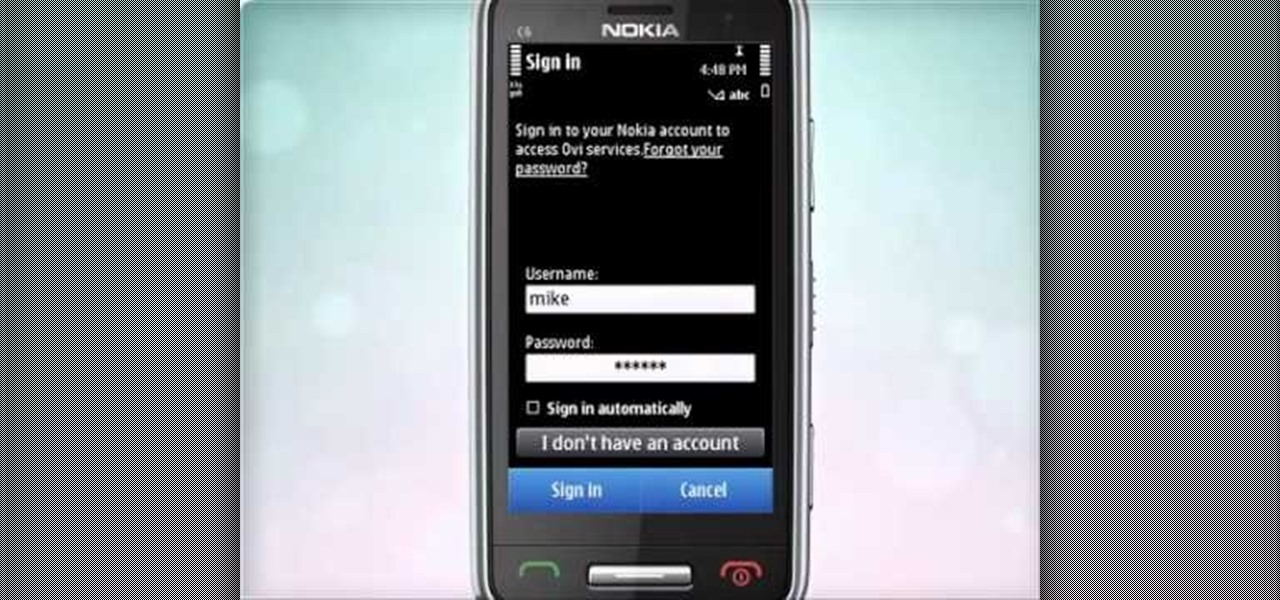
Learn how to start using Social application: sign in and add multiple services (such as Facebook or other). Also learn how to see your friends' status updates and to post your own status update. It's easy and this clip will teach you everything you need to know. For all of the details, including complete, step-by-step instructions, watch this brief, official C6-01 owner's guide from the folks at Nokia!

Learn how to upload pictures to social networking services. It's easy and this clip will teach you everything you need to know. For all of the details, including complete, step-by-step instructions, watch this brief, official C6-01 owner's guide from the folks at Nokia!

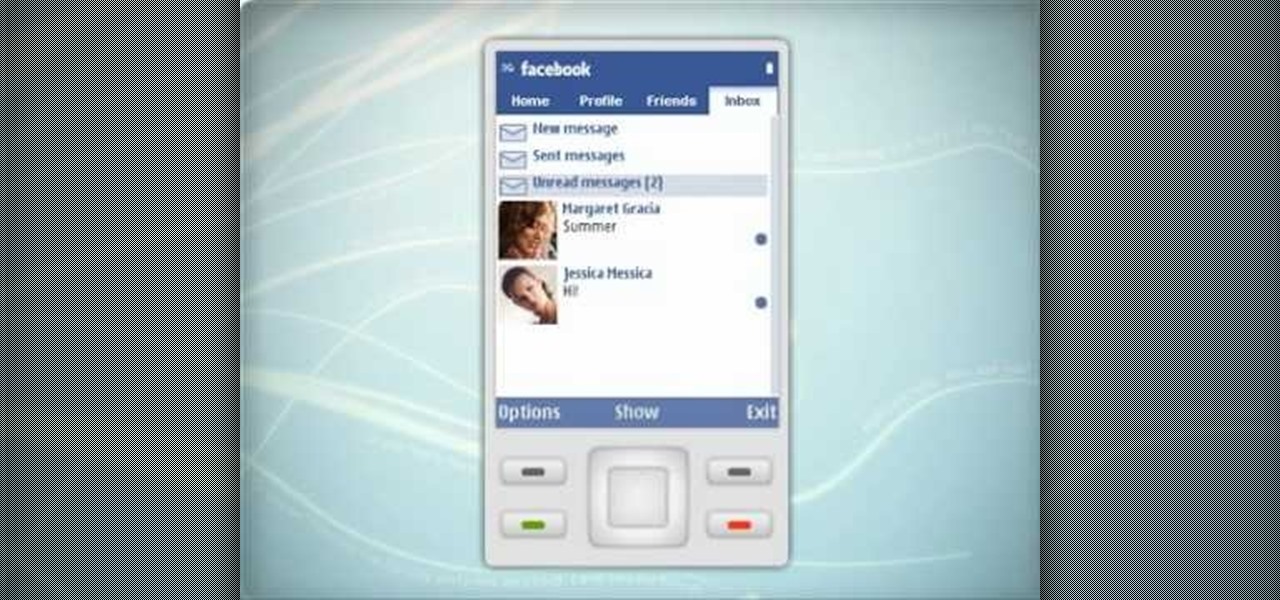
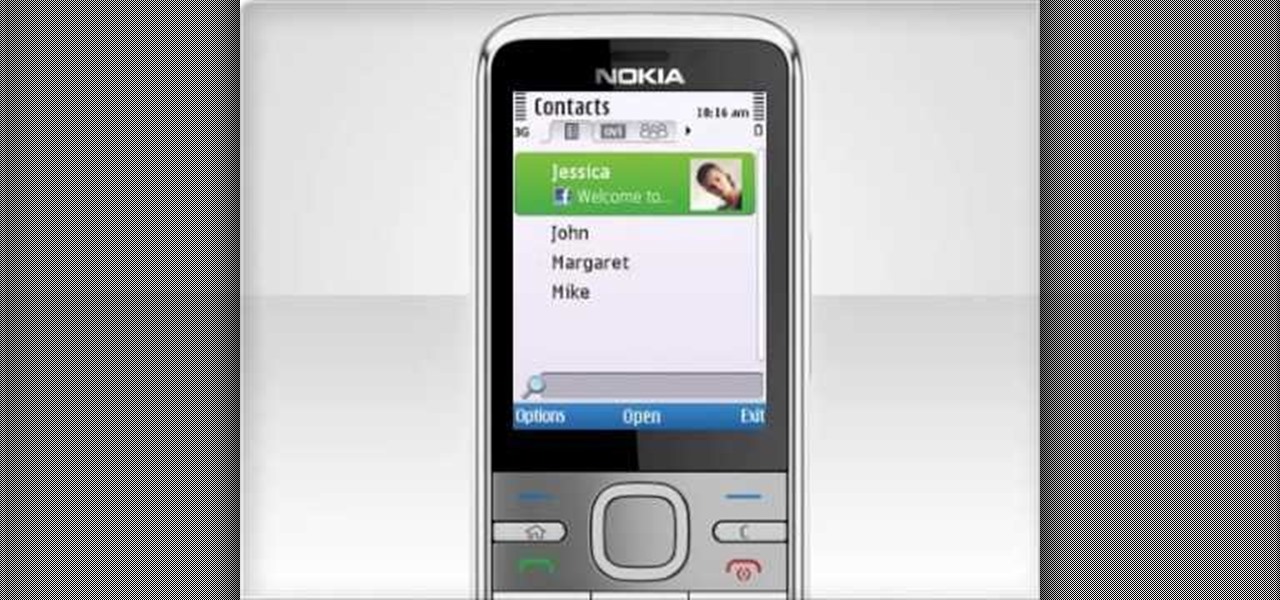
In this video, we learn how to use the Nokia C5's social networking features to read, open and respond to Facebook messages. The C5 is the first offering in Nokia's new "C" series of mobile phones. It runs on Nokia's Symbian OS and features a 2.2-inch screen and 3.2-megapixel camera. Want more? Search WonderHowTo's sizable collection of C5 video tutorials.

In this clip, we learn how to use the Nokia C5's social networking feature. The C5 is the first offering in Nokia's new "C" series of mobile phones. It runs on Nokia's Symbian OS and features a 2.2-inch screen and 3.2-megapixel camera. Want more? Search WonderHowTo's sizable collection of C5 video tutorials.

Security is tighter than ever in U.S. airports. From the recent instigation of the hotly debated full-body scans and pat-downs to the TSA limiting every ounce of body lotion you bring, it's hard to make it through the security gates without some major airport hate.

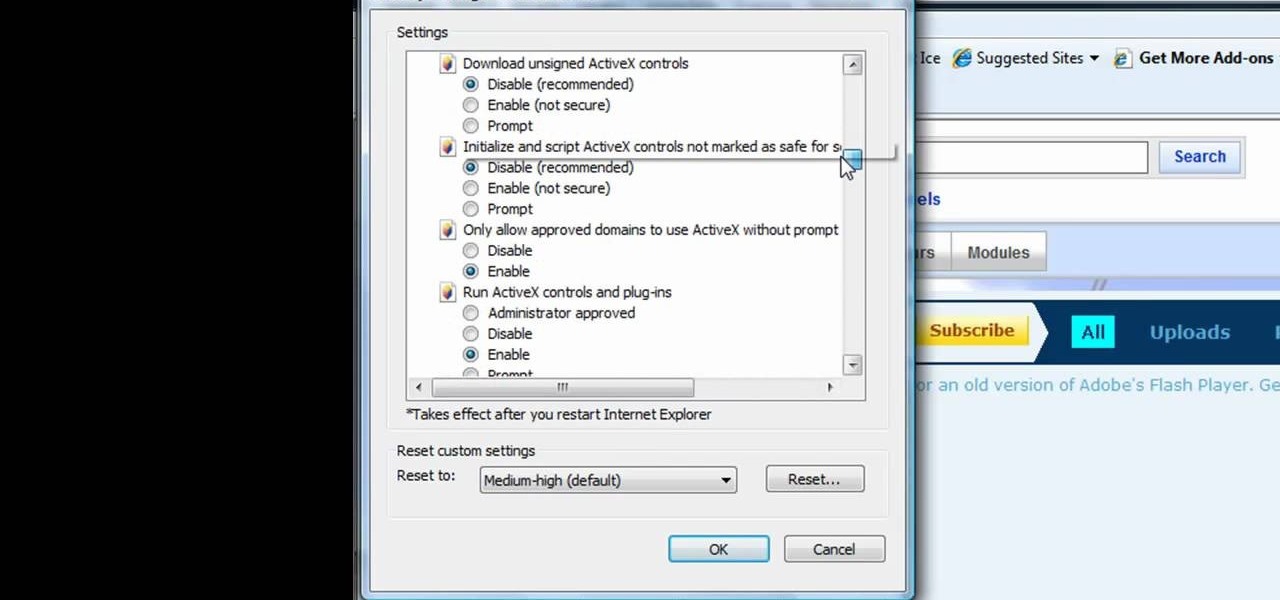
This tutorial shows us how to enable JavaScript in Internet Explorer. First, go to the top right of IE and click "tools". Then, click "internet options" and then go to the security tab. From here, select your security level that you want by clicking "custom level". Scroll down to the bottom and find the tab that says "active scripting" and make sure it's enabled. Click on "ok", then refresh the page that you are on. Now you should be able to watch videos and use anything that uses JavaScript ...

Pimples are the bane of many teenagers social lives, and covering them up is big business, especially for girl for whom the tools to cover zits are more readily available. This video will show you how to use exfoliator and concealer to hide zits completely.

Make a custom background for your Facebook, MySpace or YouTube profile using the Fireworks software! This tutorial, using the YouTube layout, shows you how to create a little extra personalization for your profile. Keep screen size and your file limitations in mind as you create your image!

The difference between an amateur piece of jewelry and a professional one often lies in the details. Almost anyone can link chains together into a necklace and add small floral baubles, but the professional will take care to make sure the baubles are attached almost imperceptibly and the closure blends in with the rest of the necklace and also won't budge.

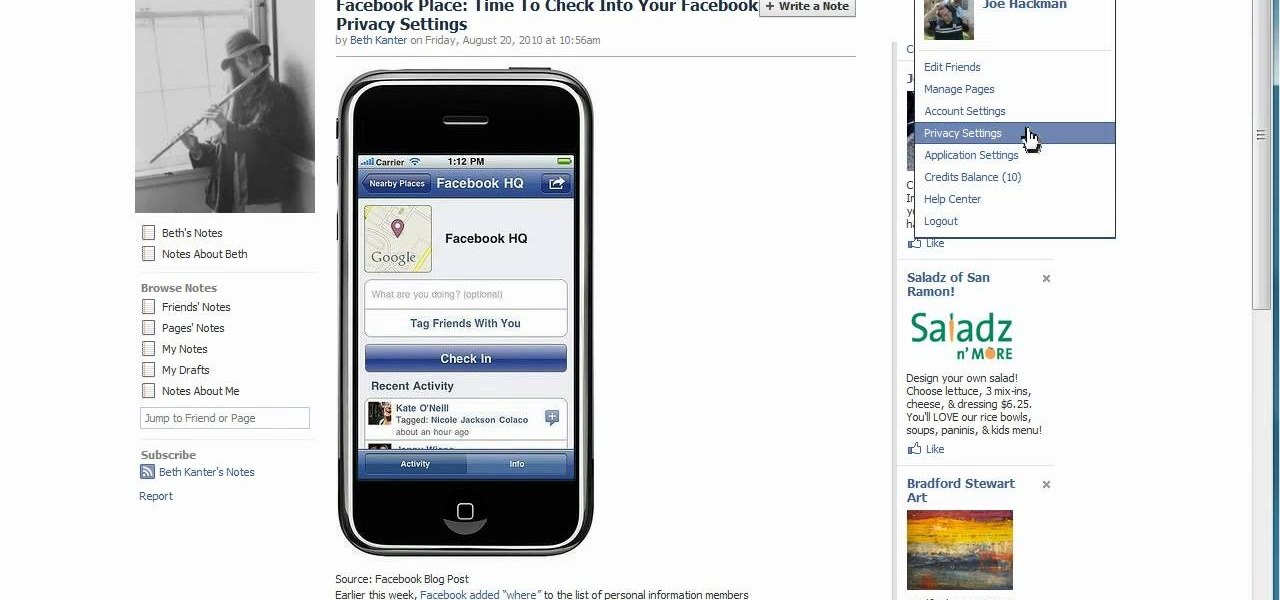
Underwhelmed by Facebook's new Places geo-tracking feature? Disable it. It's easy. Whether you're completely new to the Facebook's popular social networking site or simply require a small amount of clarification on how to deal with the Places feature, you're sure to benefit from this helpful video guide. For more information, including detailed, step-by-step instructions, take a look.