The Google Pixel's camera is a status symbol of sorts. When someone sees you with one, you become the photographer of choice for social events. And where do those photos end up? Social media, of course. It's how we share our lives now, and the smartphone camera defines how we approach that.

When it comes to social media, Google has had it a bit rough. But its next big app in this category is apparently steps away from completion, with a platform that allows small groups of users to edit and organize photos in unison.

With over a billion monthly active users, it seems that Facebook is nowhere close to being dethroned as the most popular social media service in the world (sorry, Ello). While their stats may be impressive, it doesn't mean that Facebook is as good as it can be.

Welcome back, my rookie hackers! Many newbie hackers focus upon the technical aspects of hacking and fail to give enough attention to social engineering. In fact, I would say that technical hacks should ONLY be attempted if social engineering attacks fail. Why bother spending hours or days trying to hack a password if someone will simply give it to you?

We all want to put our best face forwards on our social networking profiles. Facebook, MySpace, Twitter and all the rest are the best places to show great photos of yourself. You never know who might be looking. Employers, potential suitors, ex-high school classmates.. they are all snooping to see what you're doing and how you look these days.

So, you've downloaded Boxee... Experience TV in a brand new way! This video will help you get started.

One of the earliest players in the social virtual reality space, vTime, has just landed $7.6 million in new funding, which the company says is partially earmarked for developing and releasing an augmented reality version of its platform later this year.

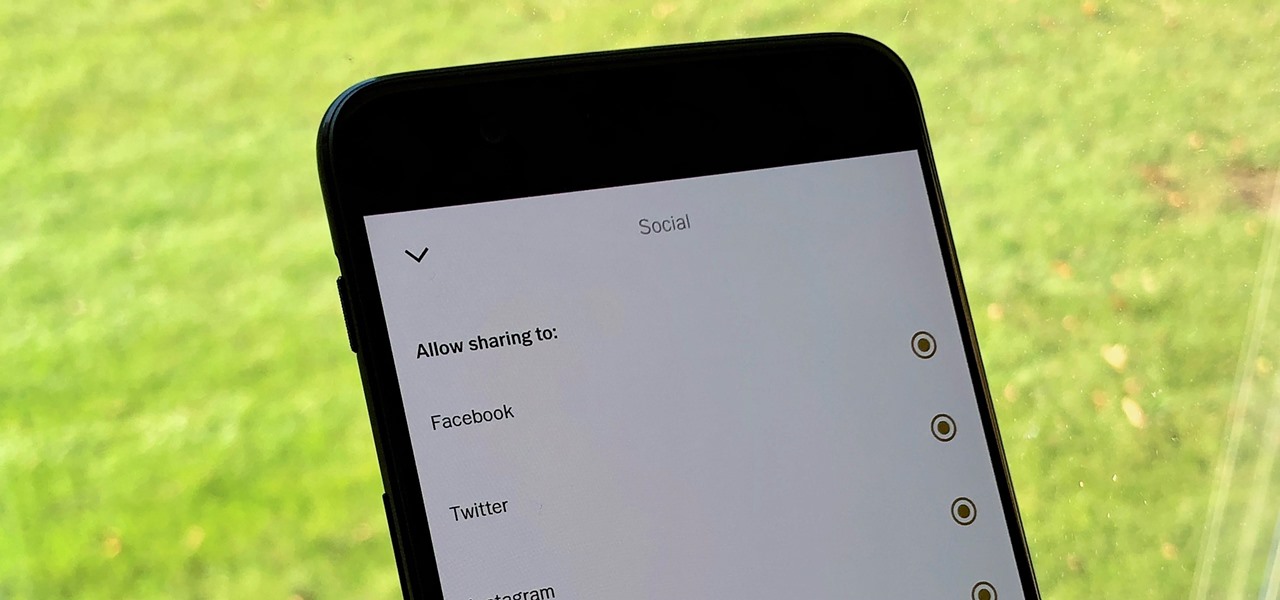
In this day and age, publishing content to one social media account just doesn't cut it. VSCO, Facebook, Twitter, Instagram ... you need to be active on all. And if you prefer editing and posting all of your photos on VSCO, you need a way to share those images with your other accounts.

Good day to everyone, today I will present some basic and advanced concepts that targets sophisticated attacks on the social basis, also I will write about some steps that can prevent this attacks from occuring, basically we will examine Social Engineering from the angle of attacker and victim, some people who are interested in security and work for middle-sized companys can learn and use something interesting from this post.

We all know about PRISM. The Surveillance Program allowing the U.S Government to access private user information. Such as, Google Searches, Tweets, Facebook Posts, Private Images, and other private user data. "Hiding" yourself can be very difficult, but it is possible. I'm here to show you How to Become Anonymous & Browse the Internet Safely.

For the average consumer, augmented reality is a fun way of dressing up photos and videos for social media. However, AR is also gaining momentum as a medium for storytelling, particularly in sharing powerful messages.

As long as you're on the internet, you can be hacked. With an estimated 2.65 billion social media users, these apps are prime targets for hackers.

Hello, hackers and engineers! Today we are going to dive a tiny bit deeper into the secrets of psychology, and how we can use them with hacking and social engineering attacks.

If you've ever searched for a new job online, chances are you've been completely overwhelmed by the process. Clicking through pages and pages of semi-relevant job postings, sending out hundreds of emailed résumés, and filling out applications is tiresome and dull.

The Droid 3 smartphone from Verizon has a great camera perfect for taking beautiful photos. If you want to learn how to perfect your on-the-go photography, take a look at this tutorial from Verizon Wireless that features instructions on all the different settings in the Camera app on the Android device.

Trying to get more traffic for your Wordpress blog? Looking to connect with the people who visit you online? This video will show you how to facilitate web interactions by adding social media icons to your blog's header. This video uses the 2010 theme to demonstrate. CSS may be intimidating, but this video will show you exactly what to do.

CreativeIceDesigns shows you how to make a "Polaroid"-style image on Photoshop CS3. Open a new 400 x 500 pixel image, and create a new layer, and drag underneath the original background layer. On the original "Layer 0" (the top-most layer), take the marquee tool and cut out (delete) a square, so that what you have in front of you looks like a Polaroid picture. Drag the the picture you want in, transform it into the right shape (ctrl + T) and drag it underneath "Layer 0." You can add effects (...

Bummed about your divorce? Feeling like a failure? Oh, stop! Get off the couch and jump-start your social life because there is life after a divorce! A great life! Get back into the swing of things by taking steps towards building a better you and regaining the confidence you once had. You might just look back on this period in your life and realize it was for the best!

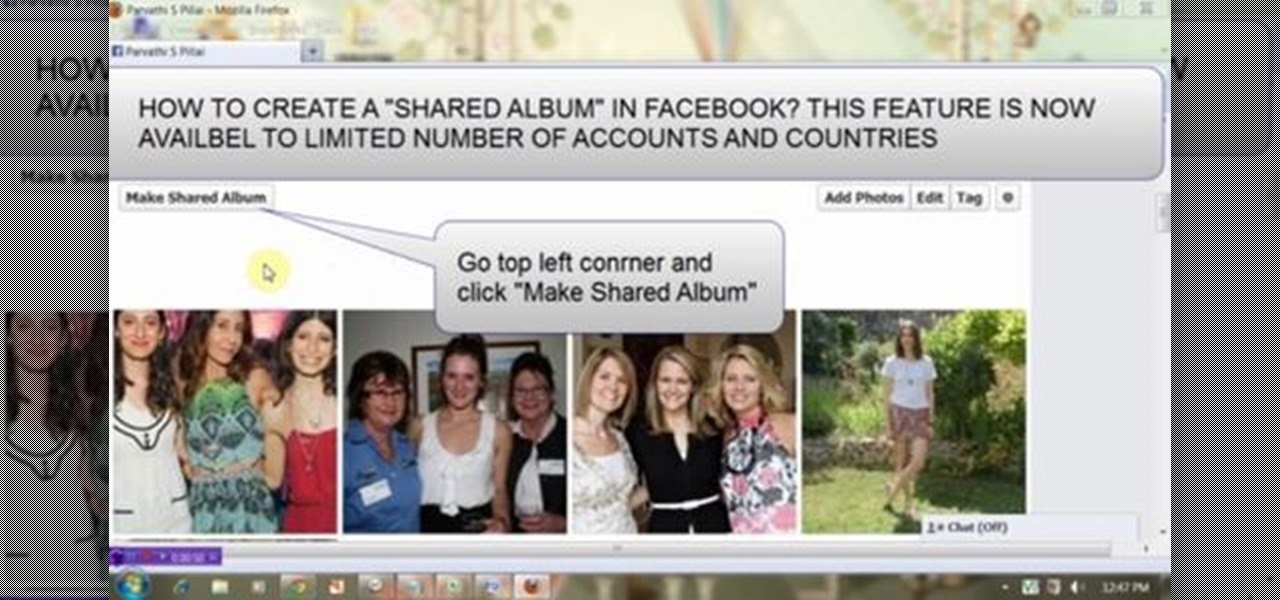
Facebook is a very useful social media sites. Shared album is a place where multiple users can upload, view and edit photos. Maximum of 50 people could share a Shared album. This video will show you how to create a shared album on Facebook. Hope this feature will be available to all users and countries in near future. Watch the video and Employ the technique in your Facebook account.

This video will show you how to add Social and Custom links in YouTube Channel Banner. You can employ it yourself. Watch the video and follow the steps carefully.

Welcome back, my hacker novitiates! Recently, I demonstrated a hack where you could redirect traffic intended for one site, such as bankofamerica.com, to your fake website. Of course, to really make this work, you would need to make a replica of the site you were spoofing, or better yet, you could simply simply make a copy of the original site and host it on your own server!

This weekend, hackers broke into the servers of the popular shoe shopping site Zappos, giving them access to the personal information of 24 million Zappos customers. The user data taken included names, email addresses, billing and shipping addresses, phone numbers, the last four digits of credit card numbers, and encrypted passwords. However, full credit card data was not lifted, and passwords were cryptographically scrambled.

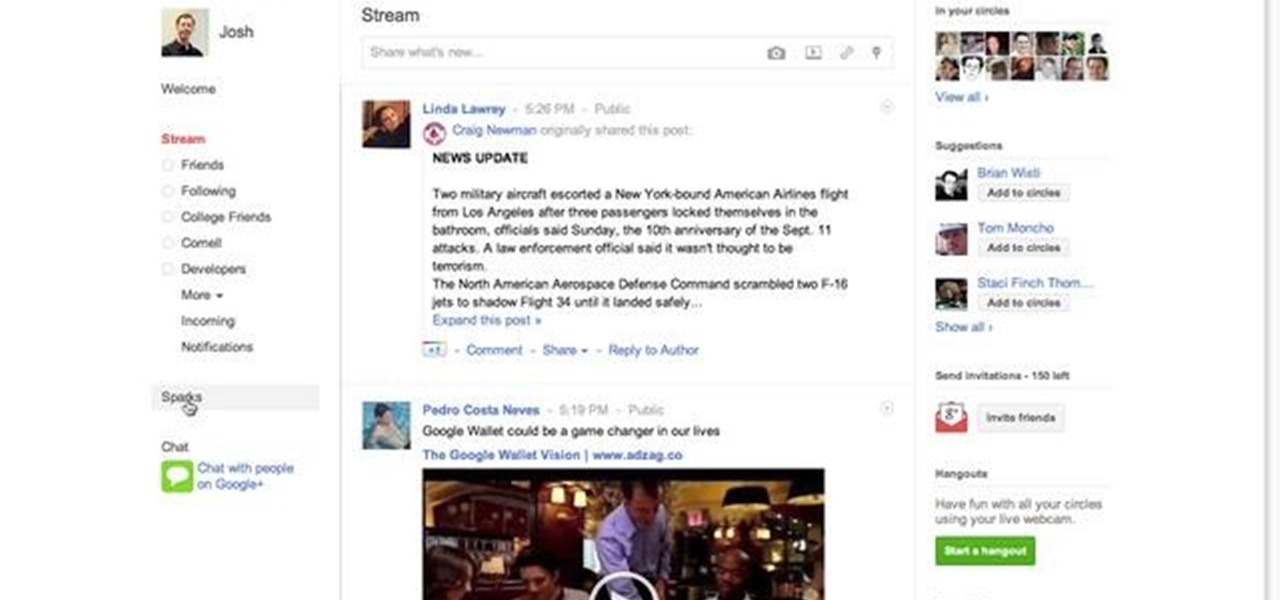
The Google+ Sparks feature is a kind of social search that allows you to find and read different articles and websites that have been selected by the people you follow and other Google+ users. It can help you find interesting posts and information on a specific topic.

If you're playing Deus Ex: Human Revolution on the Xbox 360, you can unlock the 'Ladies Man' achievement during the Corporate Warfare side quest. You will need to have the social enhancer augmentation to obtain the achievement. This guide will help you sweet talk the woman character until she provides you with the information you need.

Your mom probably told you not to play with matches, but now that you're a little older it's time to start breaking that rule. Watch this video to learn how to play a fun trick on / mind game with people at a bar or other social occasion using matches.

Light shows are one of the best parts of raves, bringing people together to participate in a whole new type of social interaction. Gloves have become the most popular tools of the lightshow trade, and this video will teach you how to make your own custom set exactly how you want them. It discusses types of lights, batteries, and everything else you need to know to make your first set of gloves.

Every photo you take is brimming with metadata such as iPhone model, date and time, shooting modes, focal length, shutter speed, flash use, and geolocation information. Share these pictures with friends, family, or acquaintances via texts, emails, or another direct share method, and you unwittingly share your location data. Even sharing via apps and social media sites can compromise your privacy.

When the Super Bowl airs, every other TV network puts on reruns because no one wants to face that juggernaut for ratings. The launch of a new iPhone is the Super Bowl of the tech world, with the launch of the iPhone X being the biggest one yet.

Social engineering makes headlines because human behavior is often the weakest link of even well-defended targets. Automated social engineering tools can help reclusive hackers touch these techniques, but the study of how to hack human interactions in person is often ignored. Today, we will examine how to use subtle, hard to detect persuasion techniques to compromise a human target.

Sophisticated hackers have been exploiting vulnerabilities in Chrome and Firefox to trick even the most careful internet users into logging into fake domains for sites like Apple, Google, and Amazon.

Instagram is the world's biggest photo-sharing site, narrowly edging out competitors like Imgur and Flickr. But unlike the competition, Instagram doesn't make it easy for users to download a full-resolution copy of any of the images hosted on their servers, as the site's main intention is to keep folks coming back and using the social media aspect of it all.

For most of us, the primary reason we capture videos on our iPhones is to post on one of the various social media platforms out there, like Facebook, Instagram, Snapchat, or Twitter, providing instant gratification by receiving a proverbial nod from our followers.

Many of us were left scratching our heads when the iOS 7 update removed the Twitter and Facebook options from the Notification Center. Allowing you to quickly tweet and post Facebook updates, these were features used, and missed, by many—including me.

Ladies and gentleman, it's official—"Selfie" has been named Word of the Year by Oxford Dictionaries.

Welcome back my social engineers/hackarians! Today we'll be looking into a fantastic piece of software, The Social-Engineer Toolkit or just SET for short. SET is designed, Developed and used by several Social-engineers. So... Let's get started!

We've all had that awful, sinking feeling when something you've been typing away at is suddenly gone. Maybe you accidentally hit the Back button, lost your internet connection, or your computer crashed, but whatever the reason, losing your work totally sucks. A lot of word processing programs have a built-in auto-save feature to prevent you from losing everything, but most websites and blogs haven't gotten there yet. An extension for Chrome and Firefox called Lazarus: Form Recovery can help y...

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to packet sniff networks with the fundamentals.

Today I am going to teach the various ways that you can use social engineering to hack a system. For those of you that have followed my past tutorials, you know that social engineering can unlock a world of possibilities. This is because no matter how many firewalls, no matter how many patches there are on a server, the password is kept in the minds of people...and people, are not as smart as computers.

As the Chromecast becomes more and more popular (it's even available overseas now), the market has seen an avalanche of Chromecast-compatible apps. We can play games, cast TV stations, and even mirror our screens, but today I'm going to show you a multifaceted tool that'll do everything from broadcasting your camera to displaying your documents.

Offensive pictures, depressing tweets, political statuses, and just plain old dumb comments are only a few of the reasons why people unfriend or unfollow others on social media sites. Sometimes it's just social spring cleaning, other times there's no reason at all.