This is the first of two Video's introducing you to your fingers from a Hand Analysis perspective. The Fingers mainly govern the mind and thinking. Somewhere in the vast fabric of time somebody discovered that the length and inclination of each particular finger can bring out certain personality traits. I still find it amazing and satisfying to see somebody with a longer than average 'little finger'(Mercury-communication), that sticks out that can't stop talking and buzzing around all excited...

Via WonderHowTo World, CAKES! CAKES! CAKES!: Martha Stewart Living Radio recently held a cupcake contest, and unfortunately the winner was NOT these Alexander McQueen cupcakes, by Julia Cunningham, DJ on SiriusXM U.

Martha Stewart Living Radio recently held a cupcake contest, and unfortunately the winner was NOT these Alexander McQueen cupcakes, by Julia Cunningham, DJ on SiriusXM U.
Cheating ruins everything. Cheating makes game play unfair for others who may be truly competitive and strategic. Cheating makes others disrespect and un-friend you. There can be unforeseen consequences, like getting viruses, trojans or your account hacked from downloading a cheat/bot program. And you will get banned from the game for violating terms of service.

Skoda has created an amazing car constructed with CAKE! for their latest advertisement. Via Car Pages,

Lifehacker provides a helpful guide for Facebook addicts everywhere. How does one get around an employer's website blocker? The trick is to set up a local web server running from home, from which you can use a proxy to access any site you please.

If you thought playing Scrabble in your grandparents' kitsch and musty old house was your most dangerous gaming experience, you haven't heard of Extreme Scrabble yet.

It certainly doesn't come easy, but that's what we want. Off the beaten path.

This Animal Welfare Foundation two-part video tutorial is from expert veterinary staff demonstrating the correct procedures for handling small mammals for clinical examination and medication. Its aim is to show that the primary consideration should be for the the welfare of the animal. This video guide will show you practical animal handling for a mouse.

What is the benefit of having a full backswing? Learn how to do a squash Forehand Recovery Deep in Back Corner.

So you've got your shiny new LG G3, your accounts are all set up, and Google has restored all of your apps. Well... almost all of them.

In the early 20th century, some people decided that it would be a great idea to play polo with cars. Sounds like a great idea, right? It was, and it wasn't.

One of the most annoying things about the PlayStation 3 is its lack of backward compatibility on some models. There are several hacks out there to do this, but most of them involve extra hardware, like the Cobra-USB Dongle, or downgrading, which can cause all sorts of problems. Photo by borisvolodnikov

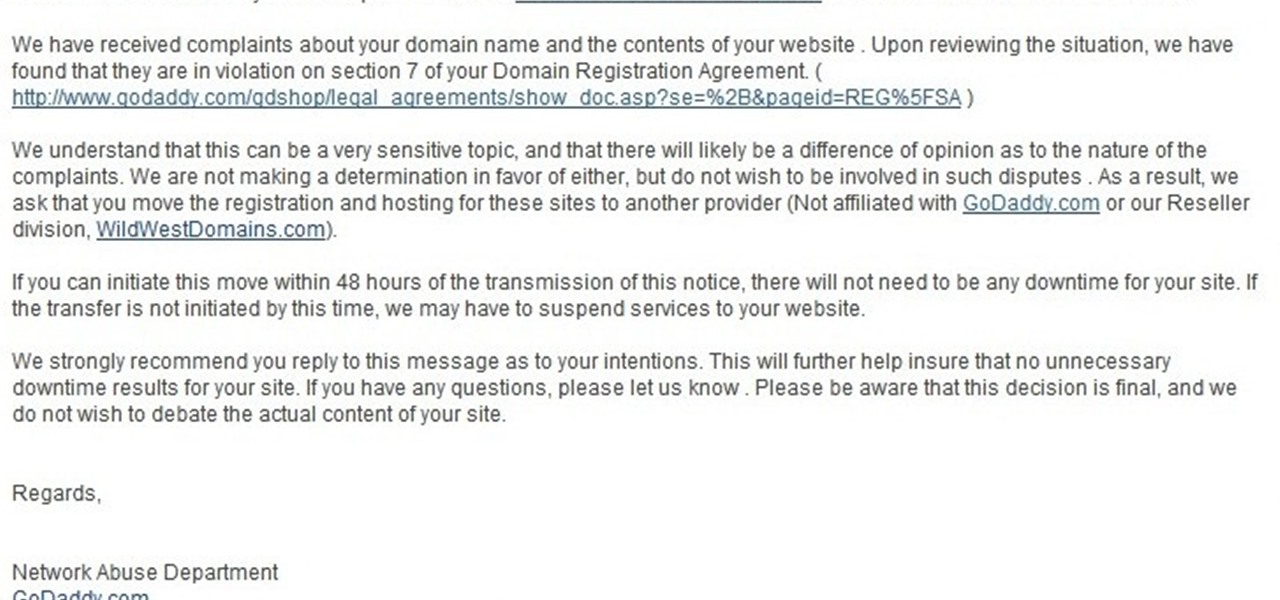
» ‘Obama Truth Team’ Orders GoDaddy To Shut Down Website. A political website that contained stinging criticism of the Obama administration and its handling of the Fast and Furious scandal was ordered to be shut down by the Obama campaign’s ‘Truth Team’. » Former Bush Attorney General Alberto Gonzales Confronted On Torture.

This past spring, British TV show Fifth Gear aired stuntman Steve Truglia performing a Hot Wheels inspired feat. The daredevil completed the world's largest 360° loop-the-loop. Death was a definite risk.

This is a fascinating exploration by a New Hampshire public health group. Their only known function is to teach people how to properly sneeze.

This video works. Watch this ordinary guy shovel mounds of bone-dry corn starch into his mouth. A combination of six step tutorial and gratuitous chestpounding, this video is a simple example of the cornstarch (or flour) bomb.

Starting in 1961 the FBI and an army of other non-believers, wiretapped MLK. All found nothing but gossip. No one was able to nail him with any evidence of sedition.

It's 1976. The hottest arcade game on the market is Blockade (or Blokade), an 8-bit maze game for 2 players. You and your opponent must move your characters around the screen in 90-degree angles, leaving a solid line behind them. Whoever runs into one of the solid lines first, loses. But soon you'll be able to play this fascinating game from the comfort of your own home—

"Connect via Facebook" — these words are coated on over a million websites nowadays, but Facebook Connect poses a risk of leaking personally identifiable information to those third parties. If you're not convinced Facebook Connect is safe, then turn off the flow of personal data to those websites!

Encapsulated PostScript, or EPS, is a graphics file format. In this QuarkXPress video tutorial you will learn how to import Illustrator EPS files. Learn also how to use remove solid background colours from EPS files. Make sure to hit "play tutorial" in the top left corner of the video to start the video. There is no sound, so you'll need to watch the pop-up directions. Import Illustrator EPS files in QuarkXPress.

Tired of plain solid colors? In this Fireworks 8 video tutorial you will learn how to work with gradients. Learn how to edit gradients, tweak, change and animate gradients. Make sure to hit "play tutorial" in the top left corner of the video to start the video. There is no sound, so you'll need to watch the pop-up directions. Work with gradients in Fireworks 8.

I am writing this quick post in response to the recent earthquakes and tsunamis that are affecting Japan. As soon as the news broke, and we began to hear of tsunami warning for our area, I immediately realized how under prepared I was for a natural disaster. The thing that drove this point home even deeper was the number of people asking me for advice on what they could do to prepare for the possibility that we are hit by one of the resultant tsunamis. Many thoughts raced through my mind, and...

One of the boys puts on a see through or clear suit that covers their body excluding theirP head and fill the suit with some sort of vile liquid or solid most likely poo (diharea if possible) or vomit from all of the cast members. after filling he suit walk around some busy street and ask people for directions or something just keep in contact with people!!!

Want to know how to start your own vlog? Starting a video blog is simple... Get a camera!

After years of being a PC technician and Windows System administrator, I had the blind hatred for Apple that I thought I was suppose to have. I swore that I'd never even touch an iPod, let alone buy an Apple product. But I found a new career that drug me out of the Windows server/PC tech room dungeon, and into the bright modern office of a web development firm. Then it happened. After a couple weeks with all this Apple stuff around me, my love for gadgets and (closet) Apple curiosity got the ...

Watch this video from This Old House to learn how to install attic stairs. Steps:

Most wouldn't think that "modern-boho" is appropriate for the office, but you can transform your gypsy garb into something professional and chic. In this video, Sydne Summer shows you how to do just that. Take cover

This tutorial shows you how to download bittorents with uTorrent without risking having your IP address get exposed or traced. You will need to find a proxy server for this to work. Download torrents safely.

Last weekend we had a fun workshop (not the redstone workshop from yesterday) in which a bunch of people got together and built mountains! Well, small mountains, at least. The workshop was only an hour, after all.
Collapse At Hand Ever since the beginning of the financial crisis and quantitative easing, the question has been before us: How can the Federal Reserve maintain zero interest rates for banks and negative real interest rates for savers and bond holders when the US government is adding $1.5 trillion to the national debt every year via its budget deficits? Not long ago the Fed announced that it was going to continue this policy for another 2 or 3 years. Indeed, the Fed is locked into the policy.

Hey, hackers! Now that you've hacked/owned your first "box" in my last article, let's look a little closer at another great feature of Metasploit, the Meterpreter, and then let’s move on to hacking a Linux system and using the Meterpreter to control and own it.

Another week has passed on the online battlefield as the CISPA legislation continues to grind away at our freedom. Here at Null Byte, we try to keep our community informed and knowledgeable at the same time—and that means creating content for them to learn from.

Though under a lot of the average consumer's radar, the CISPA is now making rounds again with a coalition of advocacy rights groups. The act, known as the Cyber Intelligence Sharing and Protection Act, forces companies to ignore existing privacy laws and share information with the Federal Government. This short article will bring you up to date on this bill. The CISPA is another bill 'designed' to help prevent thefts and prevent them in cyberspace. But again, like all the previous bill before...

Big brother is watching when you're playing around on another system—and big brother is that system. Everything from operating systems to intrusion detection systems to database services are maintaining logs. Sometimes, these are error logs that can show attackers trying various SQL injection vectors over and over. This is especially so if they are using an automated framework like sqlmap that can spam a ton of requests in a short time. More often than not, the access logs are what most amate...

There's a time in everyone's life when they need to become immortalized and reprographed in a full-blown comic spread, complete with halftone dots and speech bubbles—or squares, if you're a square. With our favorite program Photoshop, you can quickly turn any hyperbolic celebrity into a comical farce. Even normal people can become vintage villains with a little pixelation.

In many ways, we center a large portion of our lives around festivals. They provide us days off from work, allow us time to be content with our families and loved ones, and a give us a chance to eat as much as we want without Aunt Carol saying something about our necks (it's thyroidal, Carol). However, some festivals are determined to push the needle to crazy. Here, for your consideration, are those offenders.

Last week, we had a great contribution from Christopher Voute, who introduced us all on some of the basic moves in Python. Now, who else will share their knowledge and tackle some of the topics below?

There was a huge ban wave recently on Xbox Live. In the unfortunate event that you decided to do something against Microsoft policy, and have consequently gotten yourself banned from Xbox Live, you may have come to the realization that doing whatever got you banned from Xbox Live in the first place was not worth the risk.

Washing a car is a simple task. However, many people damage their paint by scratching it or making swirl marks when washing. If you are going to take the time to wash your car, make sure you follow these simple tips to prevent paint damage.