
How To: Get an upper body workout with power hang knee tucks
Learn how to do power hang knee tucks. Presented by Real Jock Gay Fitness Health & Life. enefits


Learn how to do power hang knee tucks. Presented by Real Jock Gay Fitness Health & Life. enefits

Learn how to do hang knee tucks. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do mock military pull ups on a squat rack with your feel on the floor. Presented by Real Jock Gay Fitness Health & Life.

Learn how to do diagonal down, side and diagonal up cable chops. Presented by Real Jock Gay Fitness Health & Life.

Good Housekeeping's Beauty Editor shows easy makeup tips to bring youth to any face.

Learn how to do seated V holds with twisting medicine ball floor bounces. Presented by Real Jock Gay Fitness Health & Life.

Learn how to hold a single arm plank. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to hold plank position while doing a cross kick under. Presented by Real Jock Gay Fitness Health & Life.

Learn how to do dumbbell skull crushers. Presented by Real Jock Gay Fitness Health & Life. Benefits

Ever wish you could bring your tabs with you from computer to computer? Now you can! Watch Tekzilla to find out all the details.

It's time to bring hot rollers back. If you want those sexy, soft curls and are sick of using your brush and hair dryer, try curling your hair with hot rollers. Andi Scarbrough of Byu-ti Salon shows Katherine Kendall a quick and easy way to curl your hair with many cool tips to achieve that "Hollywood Glam" in minutes.

You don't have to be Scooby Doo or Shaggy to enjoy this drink. Learn how to make a Scooby Snack cocktail brought to you by American Bartenders School. Bailey's, Midori and Malibu Rum are needed.

This is a discussion of a tricky line against the Stonewall, the Horowitz Defense (2...Nf6 3.Bd3 Nc6). White allows Black to spend three moves capturing the light squared Bishop and bringing White's pawn from c2 to d3, preventing a ...Ne4 invasion. This makes for very dynamic play.

Joanne and Lauren bring you a lesson from the MMA (Mixed Martial Arts) Girls series. In this video the sexy ladies demonstrate how to do the side control escape and maneuver to a single knee takedown.

Joanne and Lauren bring you a lesson from the MMA (Mixed Martial Arts) Girls series. In this video the sexy ladies demonstrate how to do a half guard technique by getting the underhook then go on your side.

Joanne and Lauren bring you a lesson from the MMA (Mixed Martial Arts) Girls series. In this video the sexy ladies demonstrate how to do the butterfly guard.

Joanne and Lauren bring you a lesson from the MMA (Mixed Martial Arts) Girls series. In this video the sexy ladies demonstrate the many ways to do the pass guard.

Joanne and Lauren bring you a lesson from the MMA (Mixed Martial Arts) Girls series. In this video the sexy ladies demonstrate the rear naked choke hold in mixed martial arts.

Joanne and Lauren bring you a lesson from the MMA (Mixed Martial Arts) Girls series. In this video the sexy ladies demonstrate how to do the rubber guard triangle choke in MMA.
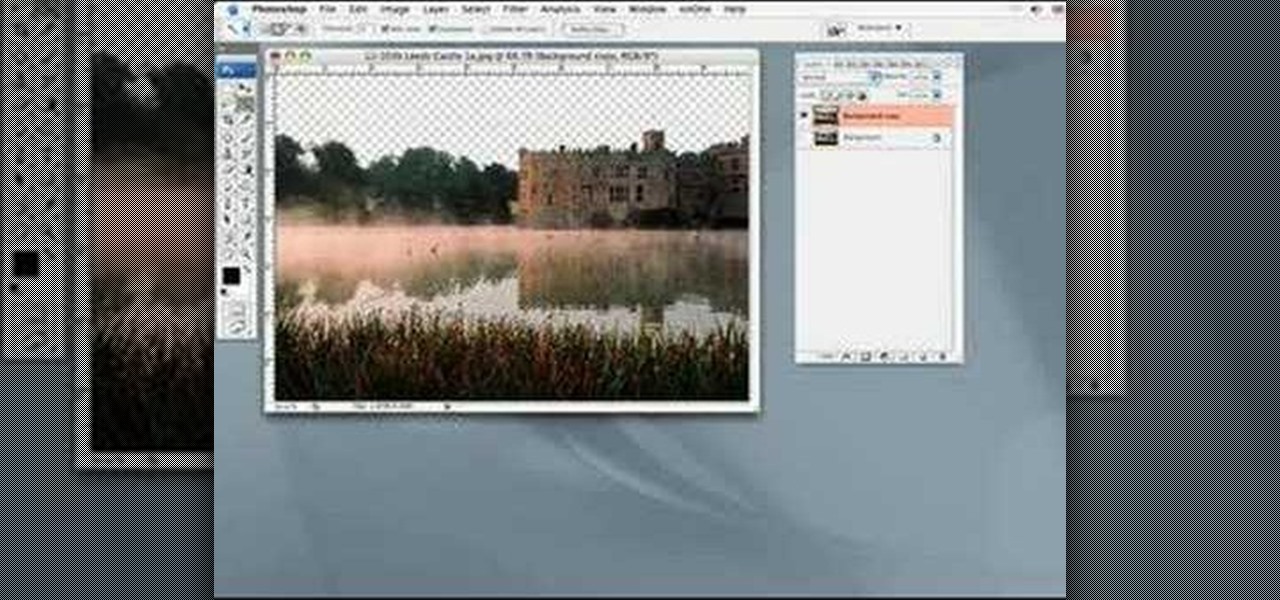
Depending on lighting conditions, you may need to overexpose the background to get a good shot of your subject. See how you can use Photoshop to bring the overexposed backgrounds back to life. This trick will work if you took a photo of the object and the sky, or if you just have another image of a background you want to use.

Time to bring in your indoor plants before the frost gets them. Here are some tips to get them ready for the transition.

Both the Germans and the Pennsylvania Dutch eat this dish on New Year's Day believing that it brings good luck. Ingredients needed are sauerkraut, onions, red-skin potatoes, bacon, McIntosh apples, garlic, paprika, pepper and pork ribs, country style or the cut of your choice.

Sammi demonstrates how to spin when you are ice skating. You can do two foot spins, one foot spins, and when you are doing a spin you have to bring your arms in to keep your balance. You have to try to focus your eyes on one spot.

If thinking about growing your own Bonsai, remember these are trees. Granted they're miniaturized and kept in small containers but they need to be kept outdoors. One wouldn't bring a Red Maple or Azalea inside, same here. They will require diligent care, they will need to be checked for over or under watering but need to remain outside most all of the year. If a tropical variety - a bright window or greenhouse would be perfect

Forgot to bring flowers to dinner for your date? This video will guide you through napkin selection and the folding necessary to make a paper rose!

A delicious macaroni salad recipe is something you will enjoy for years to come. Bring this tried and true northern-style version to your next cookout or picnic. You will need: elbow macaroni, green pepper, plum tomato, yellow onion and mayonnaise.

Going to the doctor can be an unsettling event for any child. This program is about preparing your toddler for a visit to the doctor.

As businesses flocked to Zoom, Microsoft Teams, Google Meet, and other video conferencing platforms to bridge the gap, we wondered aloud -- why aren't more companies leaning even more heavily on augmented reality?

Many popular apps automatically share your personal data. While I have accepted a certain amount of data collection from Google, to know companies such as Facebook perform this without my consent bothers me. After some researching, I've found a great solution, and it doesn't require root.

Now that Microsoft has squarely focused on the enterprise market with the HoloLens 2, it appears Lenovo is content to play follow-the-leader with its new augmented reality headset.

NetBIOS is a service that allows for communication over a network and is often used to join a domain and legacy applications. It is an older technology but still used in some environments today. Since it is an unsecured protocol, it can often be a good starting point when attacking a network. Scanning for NetBIOS shares with NBTScan and the Nmap Scripting Engine is a good way to begin.

Signaling a new direction forward for the company, Magic Leap shook up its executive suite by re-assigning to top leaders to new advisory roles. Meanwhile, a new startup backed by Hollywood executives, tech venture firms, and notable angel investors plans to bring new life to AR for marketing entertainment properties.

This week, inside sources divulged details of how Apple nearly acquired Leap Motion, twice. Otherwise, companies offering or working on augmented reality technology had more successes than failures to talk about.
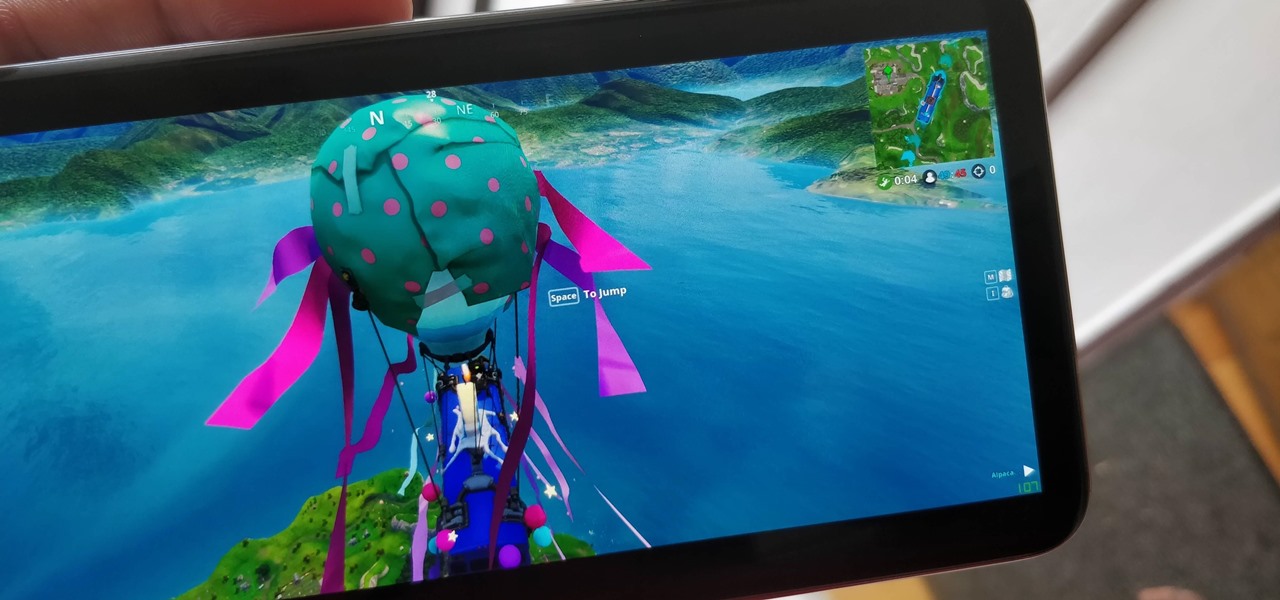
Since early March, iOS users have been able to enjoy the most popular video game sweeping the rounds. Android users have been left envious as they wait for a "few months," the only vague release date given by Epic Games. In the meantime, there are a few ways we can still satisfy our urge to play.

Arsenic occurs naturally in the environment, but it is also one of the most commonly found heavy metals in wastewater, deposited there by inappropriate disposal and arsenical pesticides, for example.

This is a how-to video on making "Spider Lollipops!" This would be a great treat for trick-or-treaters, or for your child to bring in as a treat for their classmates, or to just jazz up your basic lollipop! It is very simple to make and children will love the fact that they can customize their own lolli's.

When I tried to set up an eviltwin for a MitM-constelation in kali 2.0, I couldn't provide internet to the victim. The origin was the brctl bridging. I have read many tutorials but all of them where explained in backtrack and older versions of kali. So i was searching for a solution without using brctl and this solution will be explained now. This will just work on unencrypted wireless-environments.

Soup can be one of the most finicky dishes to make. While seemingly innocuous at first, the texture of this meal can change in an instant. For example, adding too many vegetables can result in soup that's too watery, such as tomatoes, which contain a lot of liquid.

If you're new to hamsters, or bringing your new little friend home for the first time, this video will show you what food to get, what food to buy, or what cage to buy, so that the transition from pet store to your home will be a little easier on the little guy.

If you accidentally deleted a few contacts in Gmail, don't worry. You could still restore or find those email ids. This video will show you how to recover those contacts and bring back to your contact list. The process of recovering those contacts is quite easy. So please watch the video and follow all the steps carefully.