Even with today's high-powered devices, battery life is still an issue. We, as users, have to almost habitually check the current battery percentage, because otherwise, we might end up draining too much in the morning, then get stuck with a dead phone at night.

Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use in the 1990s, hacking went into hyperdrive.

Live wallpapers have dipped in popularity lately, with many users favoring a single, static image as their home screen background. But this is generally due to still photos offering a more sophisticated look, while traditional live wallpapers can sometimes seem a little less avant-garde.

There's a good chance that your iOS device has become unresponsive at least once. It's usually at this point that you start thinking your device can no longer pass muster. You could upgrade to a newer model, but that's not always feasible, and often times, unnecessary.

In this article, we will explore the basics of radare2, a powerful package that comes with Kali. We are going to write a simple program, and then disassemble it, to see what is really doing in the processor.

Those of you who have been a part of the Null Byte community for even a short while know that I sincerely and firmly believe that hacking is the most important skill set of the future.

Let me start by saying something controversial: I despise the gluten-free fad. I think gluten is delicious (I go through at least two loaves of bread a week, with a healthy dose of pretzels and pasta in there as well), and I think many of the health myths surrounding gluten are either fabricated or hyperbolic.

You can beef up the security on your Mac all you want, but all the firewalls and antivirus apps in the world mean nothing when that can of soda tips over on your Macbook, destroying your laptop and all its data forever.

Welcome back, my hacker novitiates!

Although this century is still young, with little fanfare we may have just witnessed the "Hack of the Century." AV software developer Kaspersky of Russia recently announced that they found that some hackers have stolen over $1 billion from banks around the world!

We are living in a golden age of craft beers. Originally invented by the ancient Egyptians, every culture now has its own tastes regarding beer. The process of making beer is so multi-faceted, it's a miracle that any gets made at all.

Welcome back, my amateur hackers! Over the course of the next year, we will be developing our own zero-day exploits. In my first article in this series, I introduced you to buffer overflows, which are the source of some of the most lethal exploits, particularly the "remote code execution," so we are focusing our exploit development here on a buffer overflow.

Investing is like exercise—we all know we should be doing more of it, but we often just can't find the time. I mean, really, who's got the hours, inclination, and skill to pour through volumes of data and put together a balanced yet sophisticated portfolio of investment vehicles tailored specifically to optimize their returns while mitigating potential risks. Not me, that's for sure.

Once you unlock your bootloader and root, you're left with one more hurdle to overcome, and that's getting S-Off.

In order to unleash the full potential of your Samsung Galaxy Note 3, you've got to root it. These days, it's easier than ever, and can be done by just plugging your device into a Windows computer and pressing one button. It's so easy, your grandmother could do it, so what's stopping you?

Okay, so you're rooted and need to return your Nexus 5 to its stock firmware. Whether it's because you need to send your phone in to the manufacturer to fix a defect or you just want to use the device's over-the-air updating feature, unrooting and returning your Nexus 5 back to its fresh-out-of-the-box state is a fairly simple process with the right tools.

Welcome back, my greenhorn hackers! Earlier in this series, I showed a you a couple of different ways of fingerprinting webservers. Probably the easiest way, is to use netcat and connect to port 80 and pull the webserver banner.

Fluorescein is a commonly used fluorescent dye that is quite hard to come by in a concentrated form. Fortunately, it's used in relatively large quantities in highlighter markers and can be extracted by a fairly simple process. Fluorescein makes spectacular explosions of color as it dissolves into water and can be used for many different purposes that are addressed in the video below.

Windows 8 and its new Windows Store have simplified the process for uninstalling and cleanly deleting applications from your computer. Removing applications in older versions of Windows required a few more steps: My Computer -> Control Panel -> Add or Remove Programs -> Find the Program -> Click Uninstall.

Are you feeling like you've got the hang of Google+? Or do you, as I do sometimes, feel like there are just a few too many quirks to keep track of? Here, I've given you 15 quick tips you should know about Google+ so you can maximize the way you want to use it.

Until recently, brainwave-reading devices have pretty much only existed in science fiction. Sure, electroencephalography (EEG), the technology that powers these devices, has been used in medicine and psychiatry since the late 1800s, but diagnosing people's brains and reading their minds are two totally different things. The first EEG headsets available to the public were used mostly in gaming and even in fashion, but in the last few years, they've gotten a little more sophisticated.

The Minecraft 1.9 prerelease beta has begun. This guide will help walk you through the process of downloading, installing, and upgrading your version of Minecraft to the 1.9 pre-release so that you can try out the new biomes and snow golems for yourself.

While many image sites allow you to hide image and video catalogs behind passwords, you can often gain access to these images by "guessing" the URL of the image. This process is called fuskering. Photobucket is one of the popular websites that can be fuskered and this tutorial will teach you how to use Nav.Net 4.2 to fusker private images

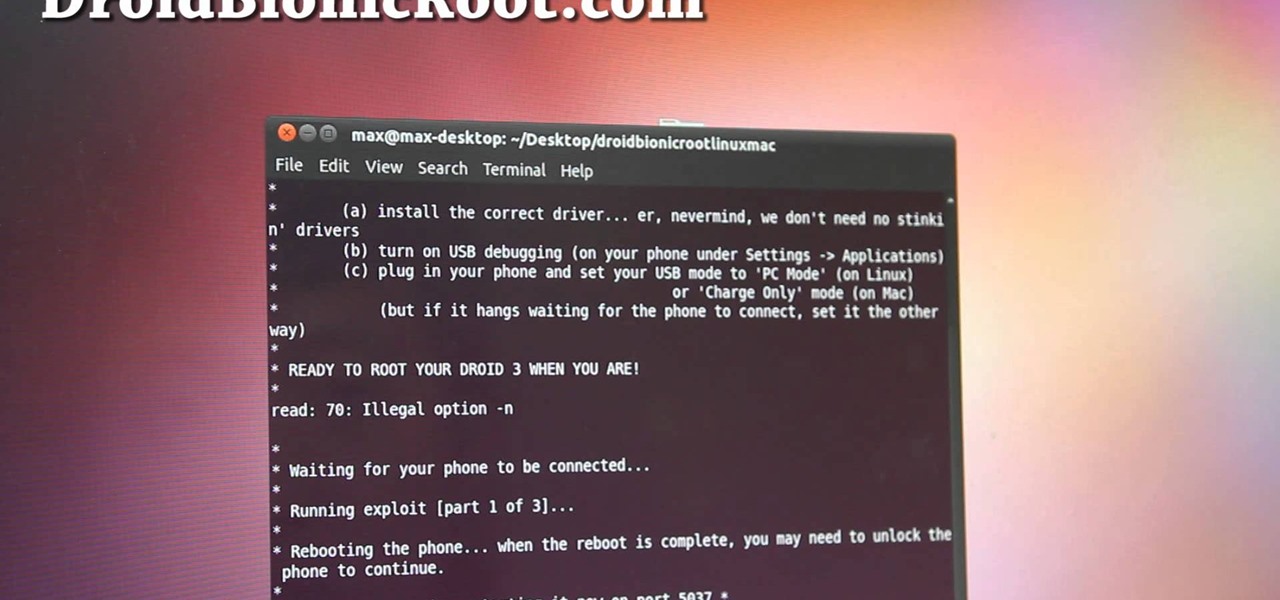
You have a brand new Droid Bionic smartphone, but you can only find guides on how to root it with a PC. Never fear, for this guide is here! This will walk you through the process of rooting your Motorola Android smartphone on a Mac or Linux computer.

The Zumocast app allows you to stream music, movies, or pictures directly from your work or home computer to your Droid Bionic smartphone. The Android device can also access documents or other files located on your PC using the program. This Motorola support video will walk you through the process.

This video will show the lowdown on knitting four-row stripes. Actually, this works with any knitting task requiring over 2 rows, where you want to change the colors of your yarn. Master knitter Judy Topaz walks you through the whole process.

If you're 3rd generation 8GB iPod Nano has frozen or broken in some other software-related fashion, you probably have to restore it to factory settings. DOH! Fortunately this isn't a hard process, and this video will teach you how to do it.

If you're interested in installing an application that you can't find in the Android Market, you'll need to use an apk (or Android packet) file. Don't know how to load an apk onto your phone? No problem: this Android owner's guide will walk you through the process. You'll find that, with a file manager application like Astro File Manager, it's a snap.

With unrEVOked, it's now easier than ever to root your HTC Evo mobile phone. So easy, in fact, that this hacker's how-to can present a complete, step-by-step overview of the process in just four minutes.

In this video, you'll be learning how to crochet a very beautiful lace pineapple pattern. Use this pattern as the base for an afghan blanket, a scarf, or anything your heart desires. Mikey takes you through the process step by step, so just watch the video!

In this home-science how-to from Household Hacker, we learn how to create an exothermic reaction by combining sulfur with iron, producing iron sulfide in the process. For all of the details, including step-by-step instructions, as well as to see what happens when these two elements meet, watch this video guide.

Need some help figuring out how to edit and apply effects to an audio track with iMovie 11 from Apple's iLife 11 software suite? It's easy! And this brief home-computing how-to from MacMost presents a complete, step-by-step overview of the process. Get started working with audio tracks in iMovie 11 with this video guide.

Looking for your next craft project? Why not a candy-stripe friendship bracelet? It's easy! So easy, in fact, that this video tutorial can present a complete overview of the process in just three minutes. For all of the details, and to get started making your own custom candy-stripe friendship bracelets, take a look.

In this video tutorial, you'll learn how to view multiple folders within a single window when using Ubuntu Linux 10.04 Nautilus. It's an easy process and this video presents a complete guide. For more information, including a full demonstration and detailed, step-by-step instructions, watch this helpful home-computing how-to.

In this clip, you'll learn how to breathe new life into an old router from its factory-default firmware to a custom third-party firmware like Tomato. For a complete demonstration of the process and detailed, step-by-step instructions, watch this handy home-computing how-to from the folks at CNET.

In this tutorial, we learn how to make adjustments to Mozilla Firefox's "Awesome Bar" search engine, a feature which first appeared in version 3 of the web browser. It's an easy process and this video presents a complete guide. For more information, including a full demonstration and detailed, step-by-step instructions, watch this helpful home-computing how-to.

In this tutorial, we learn how to toggle between the two graphics cards built into certain models of Apple's MacBook Pro laptop computer. It's an easy process and this video presents a complete guide. For more information, including a full demonstration and detailed, step-by-step instructions, watch this helpful home-computing how-to.

In this tutorial, we learn how to use an iPhone headset to remotely control a MacBook Pro. It's an easy process and this video presents a complete guide. For more information, including a full demonstration and detailed, step-by-step instructions, watch this helpful home-computing how-to.

In this tutorial, we learn how to set up and use custom key commands on an Apple computer running the Mac OS X operating sytem. It's an easy process and this video presents a complete guide. For more information, including a full demonstration and detailed, step-by-step instructions, watch this helpful home-computing how-to.

In this tutorial, you'll learn how to set up and use remote disc (DVD or CD) drive sharing for an Apple MacBook Air netbook. This can be done between Macs or between your MacBook and a Microsoft Windows PC. In any case, it's an easy process and this video presents a complete guide. For more information, including a full demonstration and detailed, step-by-step instructions, watch this helpful home-computing how-to.