In this video tutorial, you'll be taught a method for installing software packages within the Ubuntu Linux distribution in the simplest and most painless way available. There will be no web searching, downloading, or running, etc., of anything–just three clicks, and 2 minutes of your time! For a video walkthrough of the process, take a look!

Here is a demonstration of a custom designed brush for the TVPaint software. This pen is sensitive to a realistic method of gestural drawing. Watch this instructional video to use this software brush to make several types of digital drawing strokes.

Picasa 2 is a free image editing software from google. This software tutorial shows you how to use the basics of Picasa 2 for photo shorting, fixing and sharing. Learn how to navigate the interface and use the basic editing controls of Picasa 2.
This photo editing software tutorial shows you how to use this free software FastStone Photo Resizer 2.5 for Windows to batch rename and resize your images. Make life easier and resize and rename your photos all at once with the batch functions in FastStone Photo Resizer 2.5.
This photography software tutorial shows you how to use Kodak EasyShare free software from Kodak to organize your photos, make small fixes and access online services, from a UK perspective.

This software tutorial shows you how to use the video editing software Wax 2.0 to clone someone in a video. Learn to make multiple versions of yourself interact in one video in this Wax 2.0 cloning tutorial.

This software tutorial will show you how to track a laptop if it gets stolen using free tracking software Adeona. Of course, it's a good idea to figure out how to keep your laptop from getting stolen, but if you lose it, you can use Adeona to find the location of your laptop.

Everyone and their moms are into Guitar Hero nowadays. If you can't afford this great game, check out this tutorial and learn how to create your own Guitar Hero clone using free software and a controller that you can make using parts that total around $22. The free software used in this instructional video is called Frets on Fire.

In this software tutorial you will see how to create a polaroid picture and make it look like it is pinned up on a wall using Inkscape. All you need for this creative pinned-up polaroid is a picture and the open source software Inkscape.

If you do any amount of graphic design or layout design, then you know the importance of using kerning when working with typeface. This Inkscape software tutorial shows you how to manually kern text within Inkscape. This isn't the best graphic design software, but it is open source and if you are using it for layout you may need to use text kerning and will find this video helpful.

In this software tutorial you will learn how to make a simple paperclip from scratch using the curve tools in Inkscape. Inkscape is an open source freeware software so it's easy to get ahold of and start using for your graphic design needs.

This software tutorial shows you how to build a luma track matte in Cinema 4D 3D modeling software and then help speed-up your compositing of the track matte in After Effects. Creating a spinning logo with video footage inside the logo, as shown in this tutorial is a great way to learn to use Cinema 4D and After Effects together.

Controllerism is a lot like turn table-ism, except through its exclusive use of controllers and music software. Take a look at this instructional video and learn how to turn a simple and inexpensive MIDI keyboard into a custom audio controller. First, you'll want to rearrange the keys to line up with the knobs. Then, cut up an old DVD case and a bicycle tube to glue the rubber onto the keys to make it more tactile. Lastly, you'll need to set up the software to assign the keys with controls on...

Check out this video tutorial for building a Bart PE CD with Part PE Builder made by Runtime Software. Make sure that you have Internet access, a blank CD, and a copy of your Windows XP compact disk with at least Service Pack 1 on it. This will help you creat a bootable CD-ROM for your computer.

This video tutorial shows how to download .cut files onto Cricut software to design cards. Learn how to use this card making software, and get instructions for how to make a strawberry greeting card.

This is a terrible prank to pull on a friend. Destroy their iPhone software with a couple of quick hacks.

This shows you how to use the free software to unlock the iPhone, to work with any GSM Carrier. It is a very detailed, and quirky tutorial, so pay attention.

Learn how to use Inkscape (an opensource software) to design a logo for your website. This tutorial gives an overview of the software by running you through an example logo.

Are you the go-to guy/girl whenever your friends and family need tech support? You might want to consider installng LogMeIn - remote desktop software. The Lab Rats, Andy Walker and Sean Carruthers, will show you the benefits of LogmeIn software.

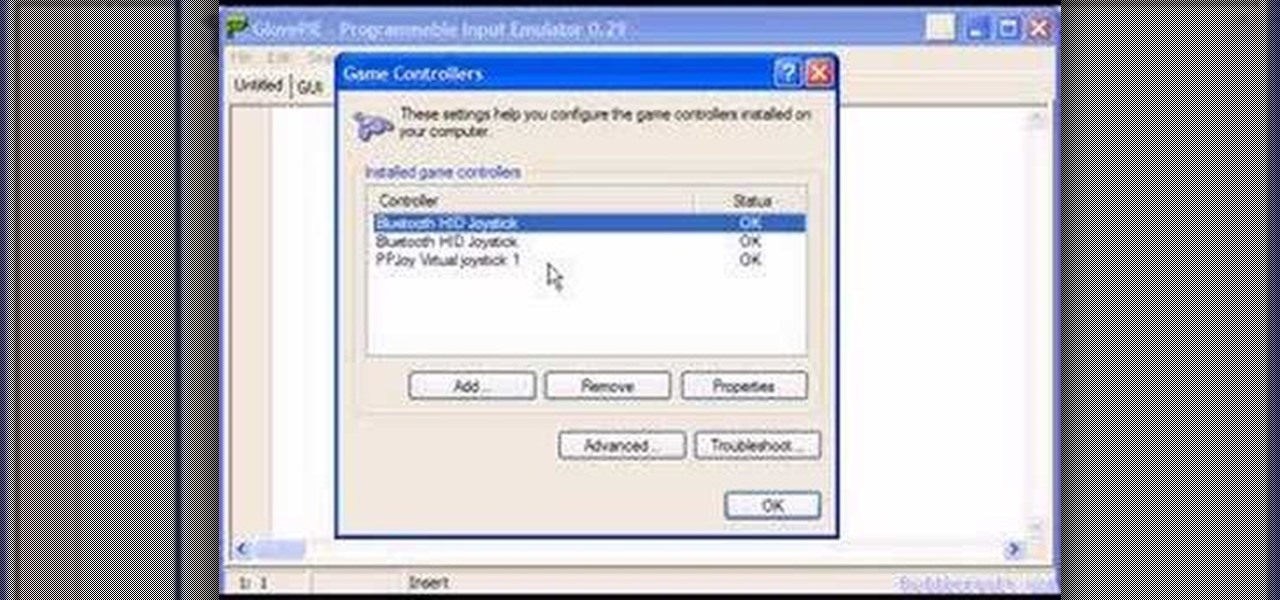
You can connect your Nintendo Wii Wiimote to your PC using GlovePie input emulation software and a bluetooth connection. Learn how to program your PC to recognize analog input or joystick/joypad input from a Wiimote using GlovePie and another piece of software called PPJOY

The fourth room in the Color software that's part of the Final Cut Studio of Apple, is the ColorFX tab. This section of the software allows you to create different looks by combining different effects nodes.

Here is a supernatural how-to for all you spirit lovers. This is a step-by-step guide to create a fake ghost video with free software. The initial technique is simple, but with a few more tweaks, you can get video that can fake at least your grandmother. Use this as inspiration for one of your April Fools Day pranks!

The automatic software update setting on your iPhone is nice, but you may not always want to install new iOS versions blindly. New updates could contain bugs and vulnerabilities, and your favorite features may even disappear. With the auto-update option turned off, you can manually download and install updates, but there are also hidden options to be more specific about how you want to do it.

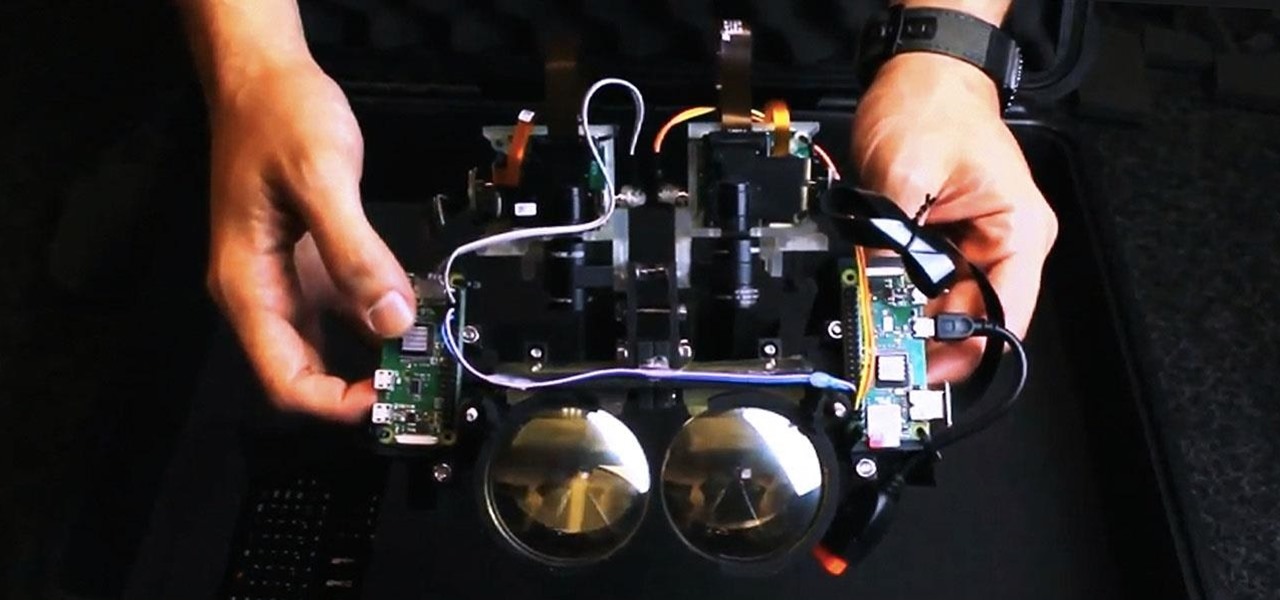
With all the hype around Magic Leap's recent launch, it's easy to forget that augmented reality hardware is still very much in its infancy. While we marvel at what is available now, researchers are still finding ways to design and produce more sophisticated components for next-generation wearables.

Now that ARCore is out of its developer preview, it's time to get cracking on building augmented reality apps for the supported selection of Android phones available. Since Google's ARCore 1.0 is fairly new, there's not a lot of information out there for developers yet — but we're about to alleviate that.

Smartglass maker ThirdEye Gen, Inc. has introduced an augmented reality solution for enterprises that includes their X1 Smartglass and a suite of software applications that enable completely hands-free computing.

Chairish, Inc. is the latest furniture retailer to bring augmented reality into its mobile stores, adding features for users to visualize products in their homes.

Welcome back, my tenderfoot hackers! One key area on the minds of all hackers is how to evade security devices such as an intrusion detection system (IDS) or antivirus (AV) software. This is not an issue if you create your own zero-day exploit, or capture someone else's zero-day. However, if you are using someone else's exploit or payload, such as one from Metasploit or Exploit-DB, the security devices are likely to detect it and spoil all your fun.

Hello Everyone! I wanted to share a free and open source note taking tool that I've been using for quite some time now.

Yesterday, April 7th, it was revealed that the United States White House had been hacked by allegedly Russian hackers. According to reports, the Russian hackers used social engineering/phishing to get a foothold in the U.S. State Department and then pivoted from that system/network to the White House. Although the White House said no confidential information was compromised, the President's appointment calendar and other information were. Attribution or "blame" for the hack was made more diff...

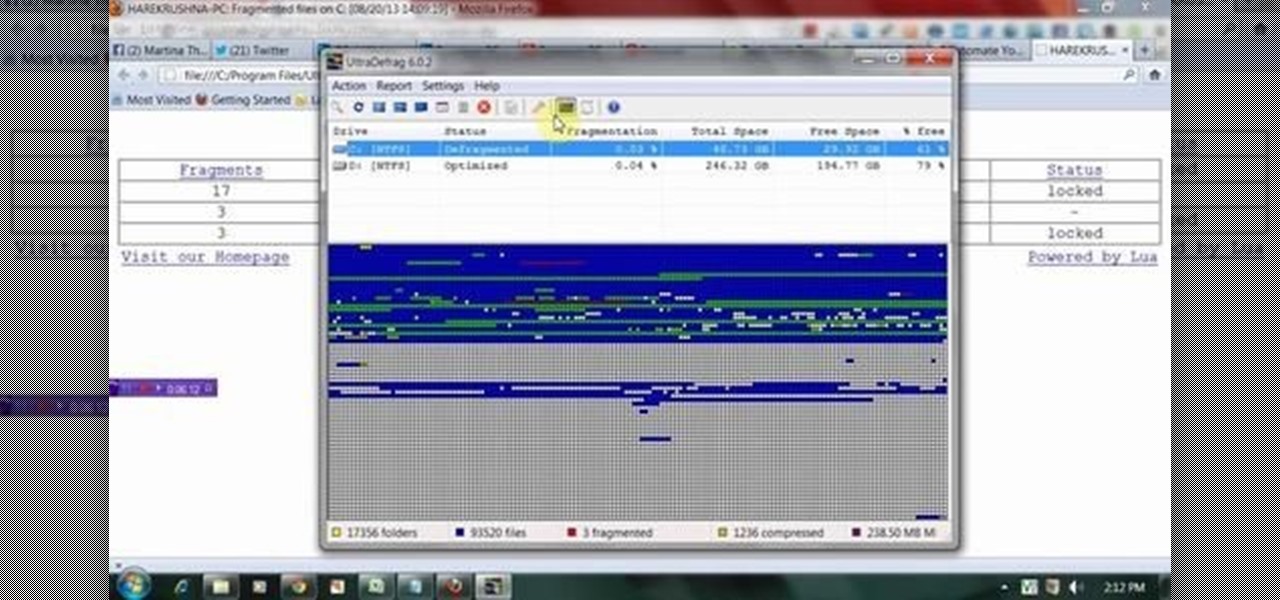
This Tutorial video will show you how to automate hard drive organization or defragmentation with ultradefrag software. UltraDefrag, PC utility software defrags your pc and speed up PC performance. So please watch the video and follow the steps to do it yourself.

Take a look at this new and contemporary Prom Bun Hair Style which is super cool and exclusive to adorn. Its over the top style has a unique and sophisticated appearance which appends a ritzy accent to your urbane persona. Try out this style following this simple tutorial. Step 1: Comb Your Hair to Make Them Smooth and Tangle Free. Once Done Gather All Your Hair in a

Welcome back, my budding hackers! I've written several listener guides on creating a malicious PDF or malicious Word document that would carry in it a payload with the Meterpreter, or reverse shell enabling you to own the system. One of the hurdles to using these techniques is the antivirus (AV) software on the target system. For instance, if you try to email a malicious PDF or Word doc, it's likely that the victim system will alert the victim that it contains a virus or other malware.

There is nothing more stunning than accentuating eyes with smokey makeup for a special occasion. Here's a tutorial for you on how to get smokey eyes for a stylish evening or a sophisticated day look in less time. Great for beginners.

Panolapse is a simple and easy way to add rotational panning motion to timelapse videos. Video: .

Ever since Sense 4, HTC phones have had no access to easy access setting toggles from the notification pane. CyanogenMod and other custom ROMs are an option, but even if your phone isn't rooted, you can still have clean, functional quick settings. Step 1: Install Power Toggles

I recently stumbled upon this lovely design created by Nichole, from nail polish wars, and was instantly inspired to ask for her permission to use her pictures to make a slideshow presentation of her wonder work! I like to call them mystical nails!!

Welcome back my fellow hackers! In my last few articles, I've concentrated on what is called a listener, which is basically the same thing as backdoor and rootkit, only "listener" sounds much less malevolent than the other two terms.

Drinking games just got a little more sophisticated (kind of). Startup SmartThings built this awesome Arduino-based machine that automatically pours a shot whenever the US wins a medal in the 2012 Summer Olympics. Goldschläger for gold, Cuervo for silver, and Jack Daniels for bronze.

Windows 8, the latest version of Microsoft's flagship software has introduced the new Metro UI screen as a replacement to the classic Start menu. If you want to get rid of the Metro UI, or you want to get the Start menu back, follow the directions detailed in this video