Hello everyone! How's subnetting going? Did you practice a lot? I hope you did, but even if you didn't we will go through some more examples so you can be feeling confident after reading this article. It's all about that bad boy binary!

While attempting to hack a web app, there may come a point where the attacker may have to escape the default directory in order to access unauthorized files. This is known as a directory traversal attack. Much as the name implies, this attack involved traversing the servers directories. But in order to move to an unauthorized directory, we need to know where those directories are. Today we'll be building a tool to brute force these directory locations based on HTTP response codes. Before we g...
If you're looking to customize your Android beyond its stock options, things can get confusing quickly. One of the best places to get into developer mode is the XDA forums.

Hello, this is my first post on Null-Byte. This is made for those who have an interest in writing into another processes memory. Why would you want to do this? Who knows, personally I just wanted to mess around with games on my computer(have unlimited health).

Hello again, folks! I'm back with another (final) guide on runtime crypters which is an extension on my previous runtime crypter guide. If you have not read it yet, I highly recommend that you do since the fundamental theory of the PE format. Again, this will be a Windows-specific guide, so I'll repeat this: If you're a hater and cringe at the slightest sound of Microsoft's grotesque baby, feel free to close this tab, delete your history, exit your browser, pour some oil onto your machine and...

Hello people again, I wrote my last post about crypto about 10 months ago, now I will introduce something not fresh for the science, but fresh for the people who wants to learn. In my http://null-byte.wonderhowto.com/forum/cryptography-0161538/ post of crypto concepts, there is just basics, today we will see something that targets wide concepts like Symmetric crypto, Public Key Cryptography, Hashing, Keys etc...

Welcome aboard my inquisitive comrades. I am starting a new series that nobody expected coming. It may not seem very exciting at first, but await the last few parts as many startling discoveries will be made. This is a series which I plan to continue after the completion of Nmap, unless you have major objections.

Researchers have discovered a "severe vulnerability" that allows attackers to use eBay to distribute malware, and the online auction company has no plans to fix the problem.

Welcome back, my novice hackers! In this series, we have been exploring how a forensic investigator can find evidence of illegal or illicit activity. Among other things, we have examined the registry and prefetch files for artifacts and have done some rudimentary forensic analysis. For those of you who are seeking career as a forensic investigator or security engineer, this can be invaluable training. For hackers, it might be life-saving.

While iPhone sales are expected to dip for the first year ever, Apple is reportedly planning to release a souped-up, 4-inch iPhone 5 in hopes of boosting sales for users who prefer a smaller handset.

It's looking more and more likely that rumors stating that the iPhone 7 will not include a 3.5 mm headphone jack are true. Chinese websites Wei Feng and Anzhuo.cn reported that anonymous sources on the supply chain confirmed that the controversial design choice is a reality.

I saw many people asking for a Tutorial about writing their own Remote Administration Tool, so I now introduce you in a basic kind of RAT. This program is not for real use, but for learning how you could write this kind of tool. It will be basicly coded and not very refined. I used Python 3, so you have to install it if you want to use this program unchanged. Also this RAT is for Windows and almost all features won't work under Linux.

I recently posted a Tutorial about setting up Dendroid: http://null-byte.wonderhowto.com/how-to/setup-dendroid-android-rat-0167299/. I have worked the last 5 days on getting the Dendroid Binder, given with the Dendroid Source, working. This solution only works on Windows systems!

I'm back. School's an ass. On my quest for knowledge, which started approximately 3 years ago, I can upon an interesting little artifact. It is called the Arduino.

Similar to the feature that lets you dim the light on your PS4's DualShock controller, your Playstation 4 is filled with useful tricks that you may not know about, especially when all you want to do is pick up and play. One of these useful tricks is the ability to turn your TV on using the PS4 controller.

If I could only eat one food for the rest of my life, it would definitely be potatoes. In fact, when I recently saw The Martian, I didn't feel that badly for Matt Damon. I mean, sure... he was stranded on a hostile planet, millions of miles from home. But he got to eat potatoes all the time! Pretty fair trade, if you ask me.

When using Linux, we often need to install new software, a script, or numerous large files. To make things easier on us, these files are usually compressed and combined together into a single file with a .tar extension, which makes them easier to download, since it's one smaller file.

Hello Everyone! I wanted to share a free and open source note taking tool that I've been using for quite some time now.

Hello fellow training hackers. I do not know if many of you are familiar with ruby, but since it is a useful scripting language, that hasn't been covered too much here on Null Byte, I thought why not do some How-tos about it now and then.

It would only make sense that Google is one of the most active app developers on the Android platform, particularly when you consider that they develop the platform itself. From my count, there are an astounding 117 unique apps that the search giant and its subsidiaries have published on the Google Play Store.

Google just announced a new and improved Chromecast at an event in San Francisco this morning, and debuted a new "Chromecast Audio" for streaming music directly to any speaker. I'm sure you rushed off to the Google Store to buy one of these promising and powerful devices, but while you wait on the new one to come in the mail, your old Chromecast just got a lot more functional by way of a simple app update.

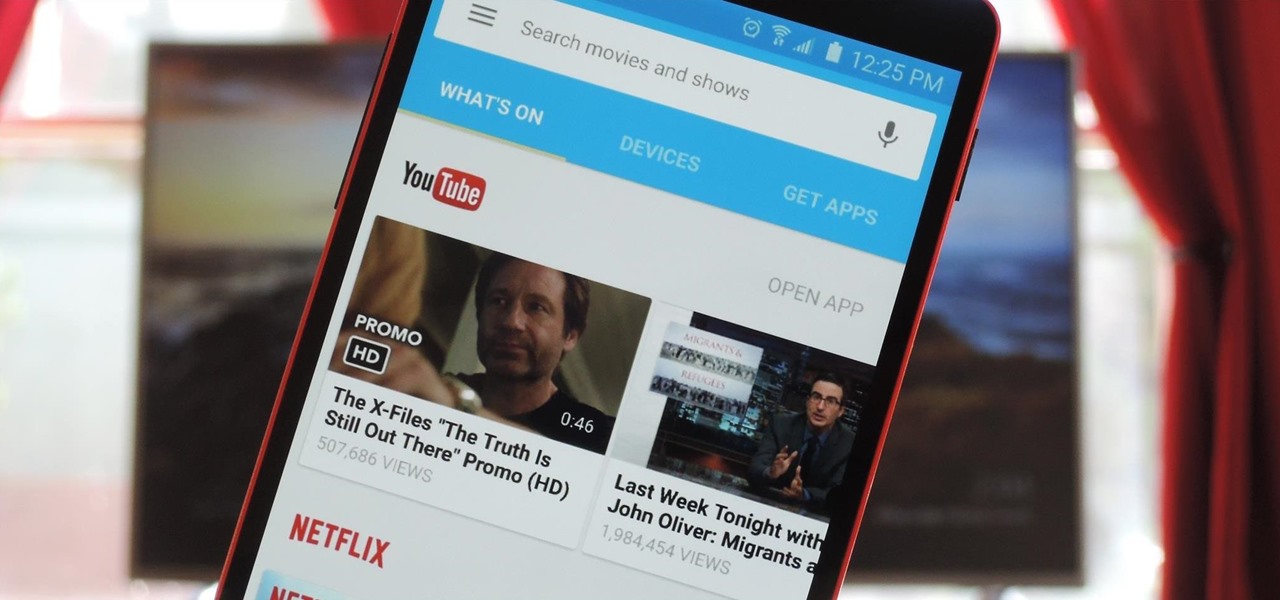
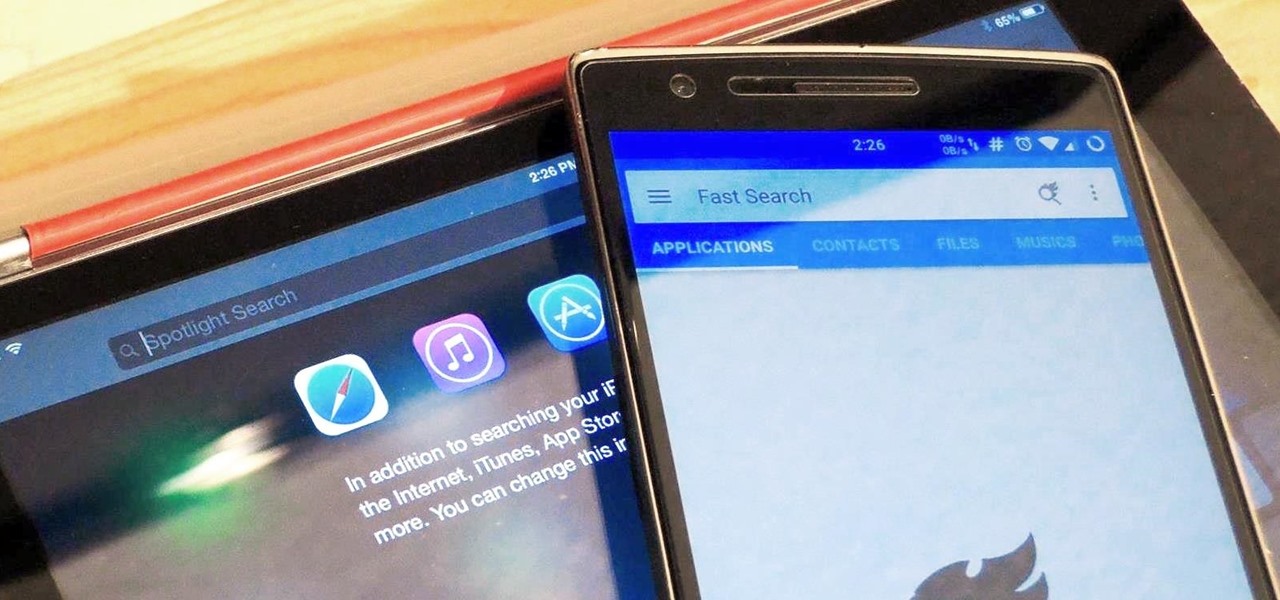
Google Now is great for looking up movie times or finding your parking spot, but if you need to track down a file you downloaded, you're relegated to using a file explorer and, depending on your organizational skills, this can either be extremely easy or a huge pain in the ass. Unfortunately I land in the latter category, which is why I started using Fast Search by developer Mohamad Amin.

Whether it's delivery drones or getting the U.S. Postal Service to ship packages on Sundays, Amazon continues to remain innovative and ahead of the game, as further evidenced with their mobile app, Amazon Underground.

There are a lot of great tutorials on Null Byte using Python to create backdoors, reverse shells etc, so I thought it might be worthwhile making a tutorial on how to convert these python scripts to exe files for Windows victim machines.

Google's Chromecast has been out for almost two years, and I can safely say it has changed the way I use my TV. At first it was a hassle to even get local media to play on it, but now casting has branched out to torrent streaming, which was a real game changer. Unfortunately, most apps only let you stream one video or song at a time, or you can't add magnet links or torrents to a playlist of local content.

I am very new to Null Byte but I find much of its content and community incredibly interesting. I spent quite a bit of time just chronologically going through the posts and I noticed a common theme in many of the beginner posts. Many people seem to want to know the 'secret' or a paragraph on "How to Hack" and become a hacker in a few minutes. I started off this post as a reply to a question from a beginner but thought it might be beneficial to have for those stumbling across this site.

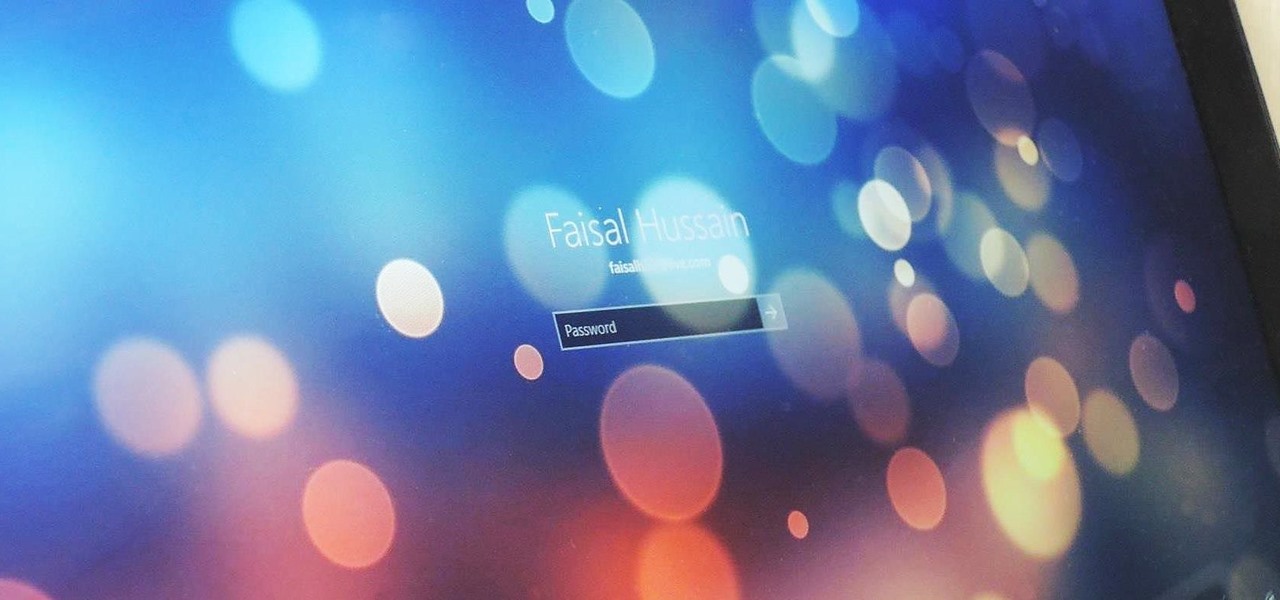
Windows 10 makes it a cinch to change the lock screen background: simply go to Setting -> Personalization -> Lock screen, then change the background to whatever you'd like. But, trying to change the login screen background—the screen where you enter your password—was a long, complicated, and possibly dangerous process. Luckily, developer Krutonium has published a tool that automates the entire process, and it's very easy to use.

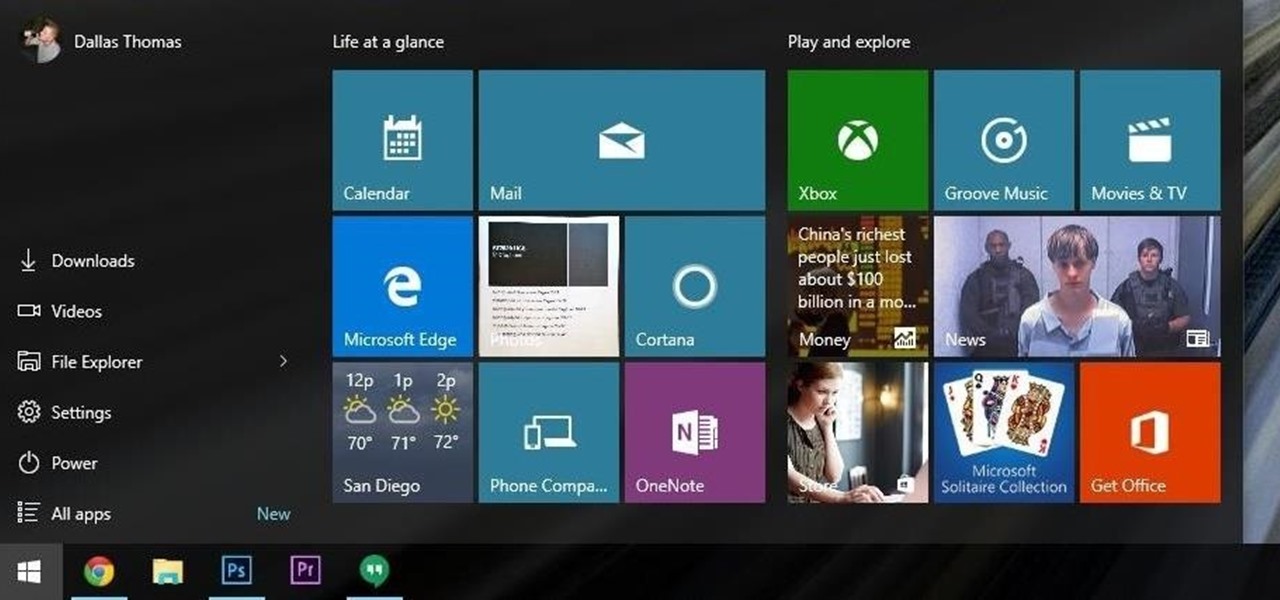
The desktop Start menu is finally back! After receiving a lot of negative user feedback, Microsoft ditched the touchscreen-first approach of Windows 8 and went with a more traditional setup for mouse-and-keyboard users in Windows 10.
Hello I have now asked for help a few times, so I figured I should contribute with what I can offer as of right now, which is many valuable sites if you need to look someone up.

Welcome back, my rookie hackers! So many readers come to Null Byte to learn how to hack Wi-Fi networks (this is the most popular hacking area on Null Byte) that I thought I should write a "how-to" on selecting a good Wi-Fi hacking strategy.

Welcome back, my greenhorn hackers! One of the most important issues any hacker must address is how to get past security devices and remain undetected. These can include antivirus software, intrusion detection systems, firewalls, web application firewalls, and numerous others. As nearly all of these devices employ a signature-based detection scheme where they maintain a database of known exploits and payload signatures, the key is to either:

Smartphones don't generally play nice with tripods, so videos taken with our handheld devices make terrible source material for time-lapse photography.

There's a recently discovered flaw by iDownloadBlog that lets thieves reset a stolen Apple Watch without a hitch, which is the result of Apple not including the Activation Lock feature that iPhones have had since iOS 7.

As with any software, Android apps can occasionally suffer from bugs. But finding the root cause of such issues can often be difficult, and reporting bugs is a cumbersome experience.

Exclusive to the Samsung Galaxy S6 Edge, "Information stream" is a screen feature that lets you see quick, at-a-glance information with a simple swipe while the screen is off. It also supports plug-ins, or additional streams of information that can come from third-party sources. So developers are starting to come up with nifty little add-ons for Information stream, and the team at 3C has some cool new system feeds that might come in handy.

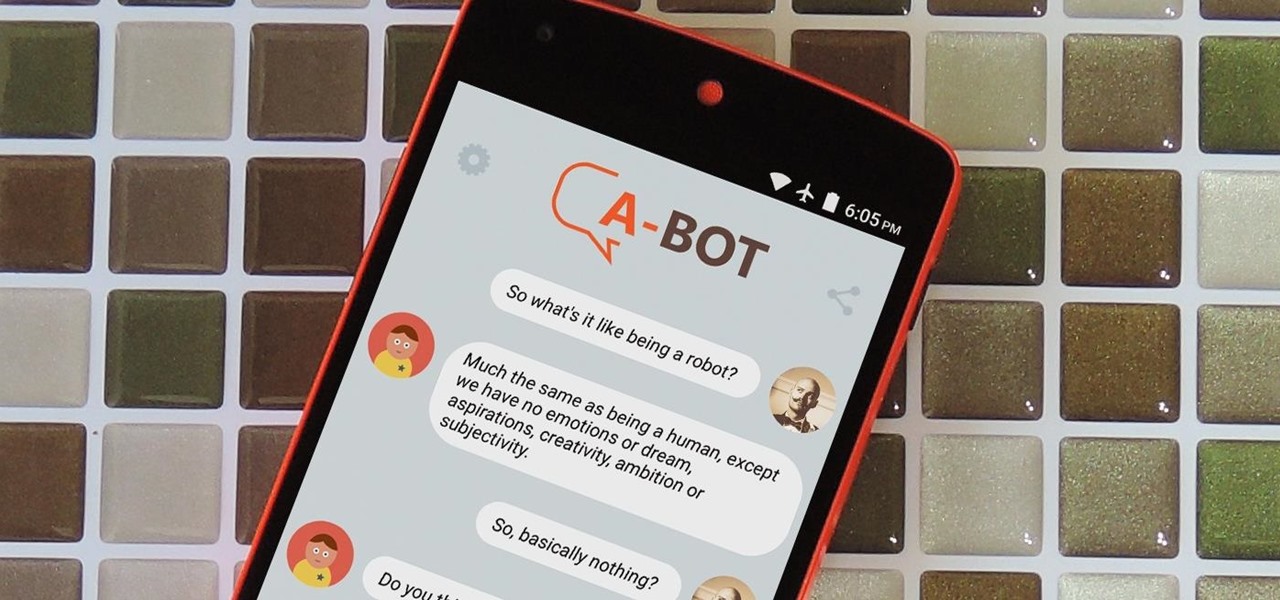
We all have those moments where we're bored or lonely, and in those times, just having anyone to talk to would be awesome. But maybe your friends are all busy, or everyone you know is at work and nobody's responding to your text messages.

If you have an Apple Watch, it's easier than ever to ask Siri for directions, send a quick text, or locate the nearest Chipotle—because you don't need to pull out your iPhone anymore. Luckily, Apple made it fairly painless to get Siri up and running on the Watch, so let's go over the two quick activation methods.

Samsung has a long-standing reputation for packing their devices with lots of added functionality, and the Galaxy S6 Edge is no exception. It comes with a nifty feature called "Information stream," which allows you to get quick, at-a-glance information by swiping the edge of your screen back and forth while the display is off.

Whether it's for handling your business's social media account or just for personal reasons, like trolling an ex-girlfriend's page (not that I've ever done that) or posting on behalf of your pup, there are instances where having two different Facebook accounts on one device is simply easier than switching back and forth.

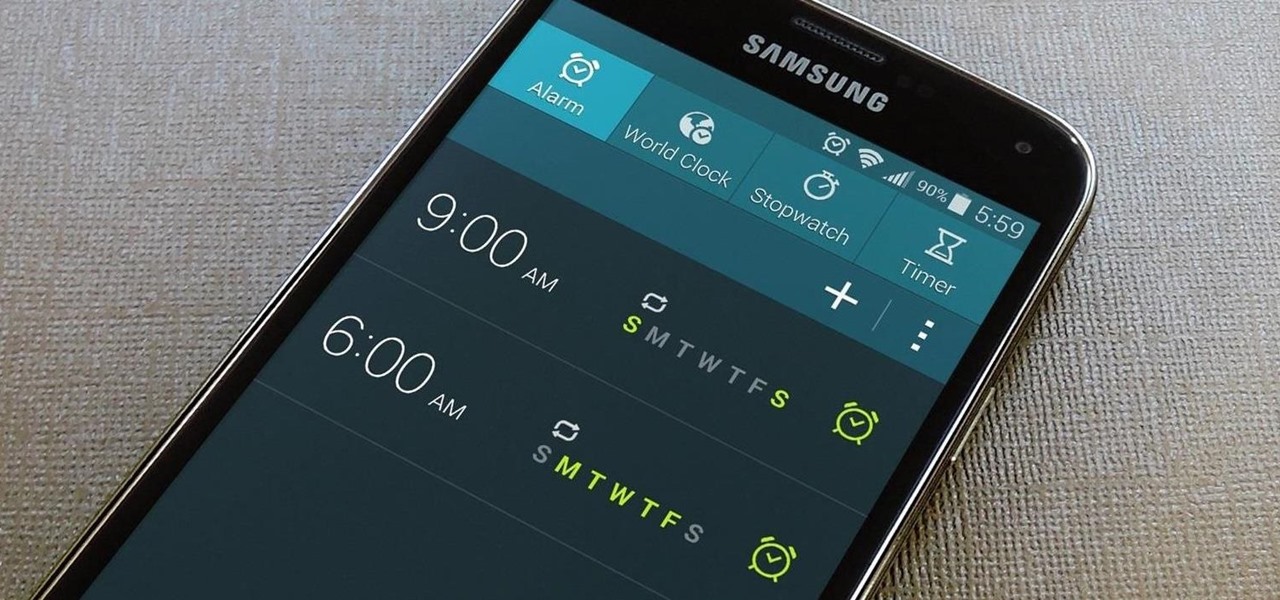
The basic clock app on Android devices is functional and has a few nice features. One of these is a "World Clock" view, which lets you see the current time in different cities across the world, and shows the time in your location at the top.