This video focuses on strategies you can use to boost your metabolism--one-step needed in order to lose belly fat. Obtaining a faster metabolism will train your body to burn more calories throughout the day. The first step to boost your metabolism is through strength training, which means developing leaner muscle mass. This will result in long-term investment for caloric burning. The second step involves exercising in the morning; this will help you burn calories more easily throughout the da...
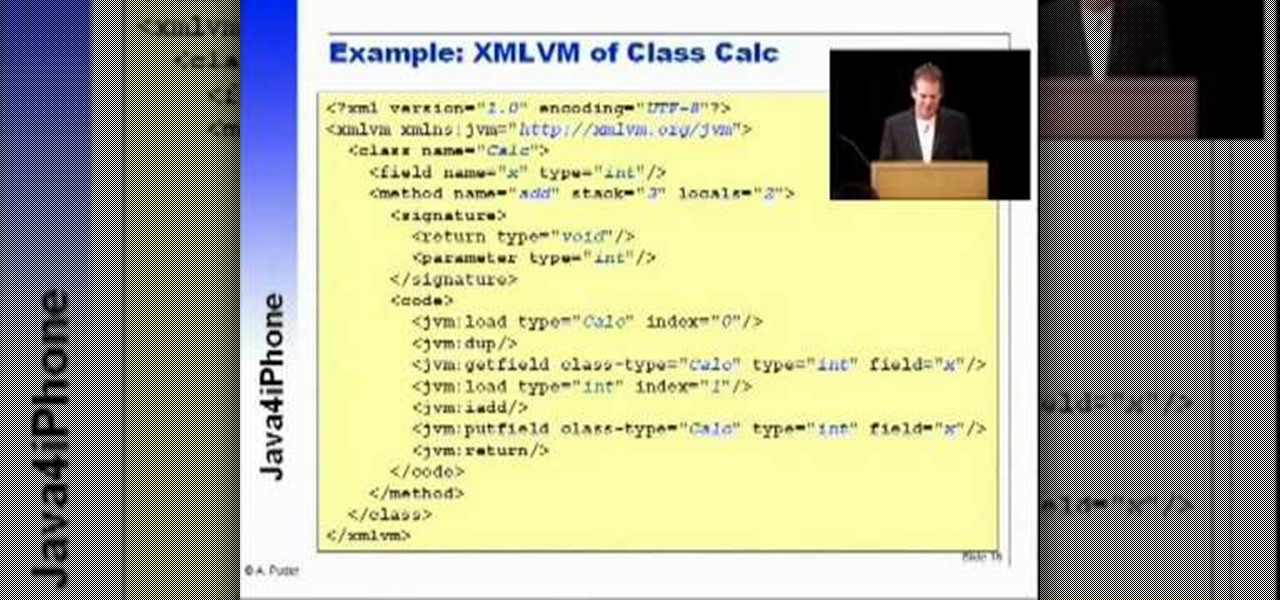
Arno Puder, a master of the XML coding field, gives a great rundown of Apple's new proprietary Java coding. This is especially helpful for Cocoa implementation

In this video, learn how to install Install0us 2.5 on your iPhone. This can only be installed on a jailbroken iPhone. Directions, tips, tricks, and tourbleshooting advice from videomaker, grandhustler are listed below.

Are you sick and tired of staring at that water damage on your ceiling? There’s no need to sleep staring at that annoying water spot on the ceiling when it's so easy to get rid of! Loose the spots with the easy steps listed in this video.

Are you a novice artist looking to up the ante in your drawings? Introduce depth and realism to your drawings with shadows. It all starts with “seeing the light.”

JusJerk has the Stick Figures, a jerk dance crew, show us how and what the "Dougie" looks like, a popular dance from Georgia that has spread out through out the United States. Watch and get inspired as several Stick Figure members show off their best Dougie moves.

Holidays such as Thanksgiving are doomsday for most garbage disposals due to clogs. If you're garbage disposal is clogged, check out this video to see some helpful tips on how to fix it.

Most people find the default SMS background for the iPhone fairly dull, so why not spice things up? Thanks to Cydia and some clever hackers, there is now a way to modify the background of your text messages!

If you've been using Cydia and you noticed that there's a lot of loading and waiting, check out this video to learn how to install Icy. Icy is very much like Cydia except less loading and waiting. It's much faster and you don't lose any of your sources you've added from Cydia or Installer; they are synced into icy.

This video drawing tutorial demonstrates an original fanart of Defective Reaper (meaning not "eyeballed", "copied" ,"pose-jacked", or "traced" from another existing source). For devotees of anime or hentai style, or those looking to get inspired by the Japanese manga type technique, this video will offer some inspiration. Check out this video drawing tutorial and learn how to sketch a hentai style Defective Reaper from Soul Chasers.

Spread the word: It's easy to reduce energy consumption! By sharing these tips, you'll help friends and family use less energy and save money.

Whether your plane made a crash landing or your ship got lost on a three-hour tour, now you're stranded on a remote island. Here's how to get help.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to build a motorcycle camera mount for under five bucks.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to build a free XMPP/Jabber server in ten minutes.

Check out this video tutorial to learn how to design a photorealistic tree with Blender. To make this tree with Blender, you will be using textures and mesh transparency. To start off, you'll first need to find a picture of a tree and save it as a transparent PGN file.

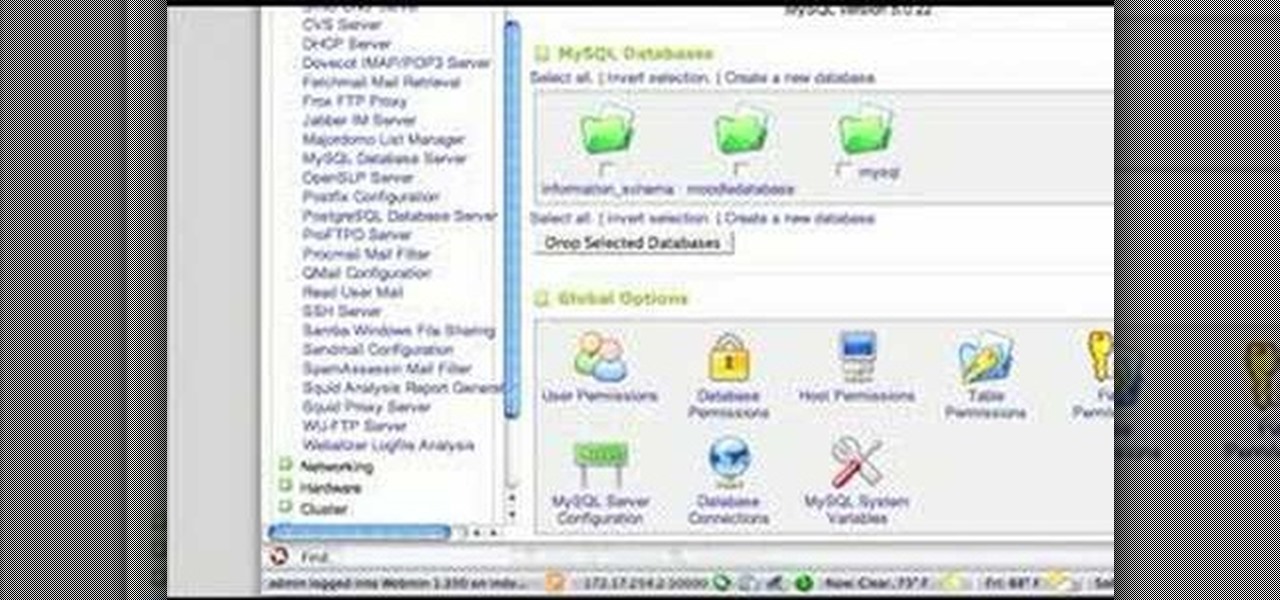
Interested in teaching an online course using your own server but can't quite figure out how to install everything you'll need? This video demonstrates how to setup a MySQL database for use with Moodle, the free, open source course management utility, which requires a MySQL database to run. For step-by-step instructions, take a look.

From brute force hardware-based solutions like pointing a camcorder at your monitor to more elegant, software-based solutions like (the free and open source) Xvidcap, there are no shortage of ways to create a screencast while running Linux. In this how-to from Linux Journal Online, Shawn Powers offers a comparative look at many of the most popular techniques employed by Linux users.

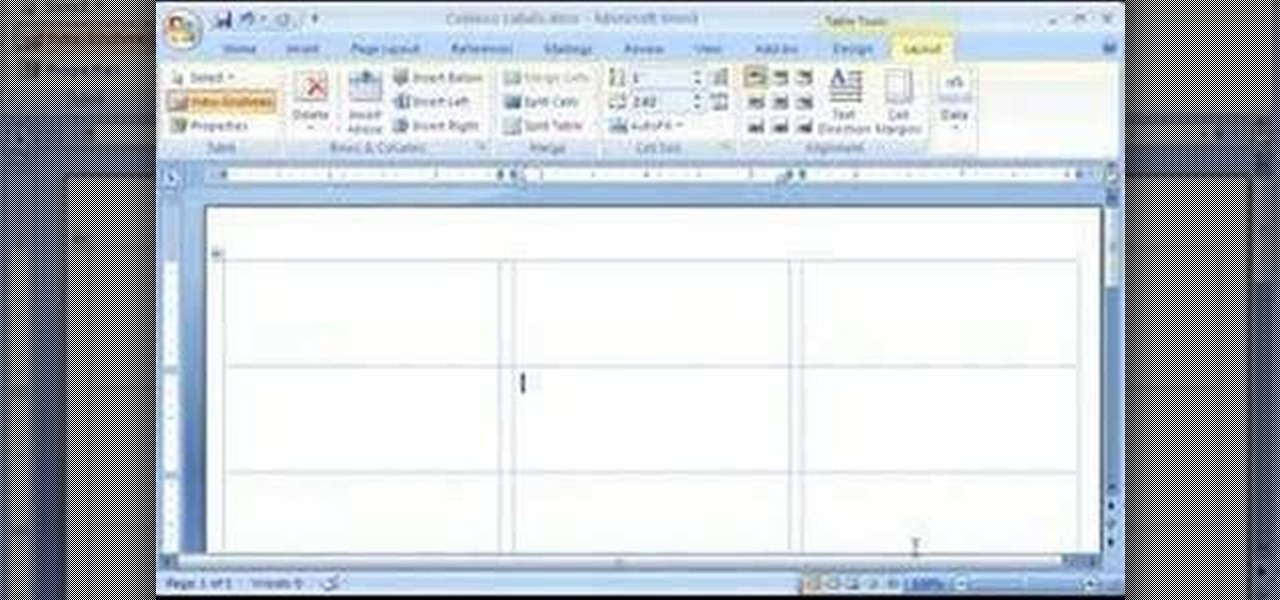
In this first demo of a 4-part series, learn how to set up labels for mass mailings using the Mail Merge feature in Word 2007.

Interested in pen spinning? Want to pick up a few moves? Pen spinning is the skilled movement of a writing instrument or pen with one's hands. It is used as a source of self entertainment (often for students), but there is a great deal of pen spinning culture (competitions, websites, etc.). Watch this pen spinning tutorial video and learn how to perform the "Continuous Middle Backaround 1.5" move.

This tutorial shows you how to creat a teeworld skin using the open source free software Inkscape.

If you are struggling with the paths tool and drawing vector art in GIMP, you can import other people's paths and manipulate them for your purposes! This tutorial will show you how to find sources at DeviantART.com and start using those in GIMP.

Check out this Blender video tutorial all you wannabe digital animators out there to see how to use paths and dupliframes in your 3D modeling.

This can only be done on a phone that has been Jailbroken. This is a video tutorial on how to copy and paste items in Safari for an iPhone or iPod touch.

The U.S. Centers for Disease Control estimates that 73,000 people contract E. coli O157:H7 each year. The primary source of these illnesses is ground beef that has been improperly handled and cooked. Watch this video to learn how you can avoid the spread of this bacteria.

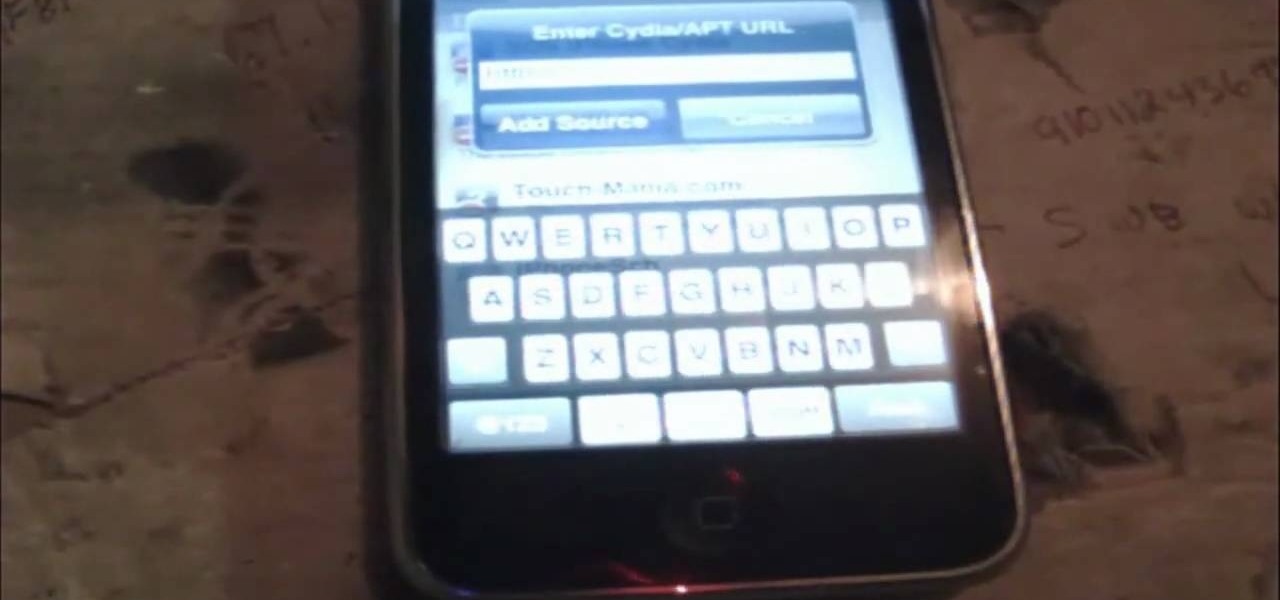
This is a new application that allows you to make movies into your wallpaper on your jailbroken iPhone or iPod Touch.

HD demo on how to set encoding parameters for proper Vimeo meady video at 720p resolution. This will give you crisp HD video ready for Vimeo upload right from iMovie 08.

This reaction is between metallic magnesium and carbon dioxide. Magnesium reacts with oxygen in the air to form magnesium oxide, but when the only source of oxygen is from CO2 the reaction becomes much more energetic. The products are white magnesium oxide and black carbon.

This video tutorial from OzLabs will show you how power the one-watt high powered LED using 120 volt source using a 12 volt adapter.

See a demonstration of decorative stitching with a variety of threads. Create your own sampler on your machine as a design source for future projects. Variegated machine quilting, polyester machine embroidery and metallic threads.

If you've ever wanted to quickly create a simple starfield (with a constellation) in Photoshop, here's how. This is part one, creating the source material for the After Effects project that follows in Part 2 ("Fish Star").

It is well documented that what you say and do online is tracked. Yes, private organizations do their best to protect your data from hackers, but those protections don't extend to themselves, advertisers, and law enforcement.

Compromised uTorrent clients can be abused to download a malicious torrent file. The malicious file is designed to embed a persistent backdoor and execute when Windows 10 reboots, granting the attacker remote access to the operating system at will.

While Apple and Google have paved the way for developers to create web-based AR experiences through their respective mobile toolkits, an open source option has entered the space.

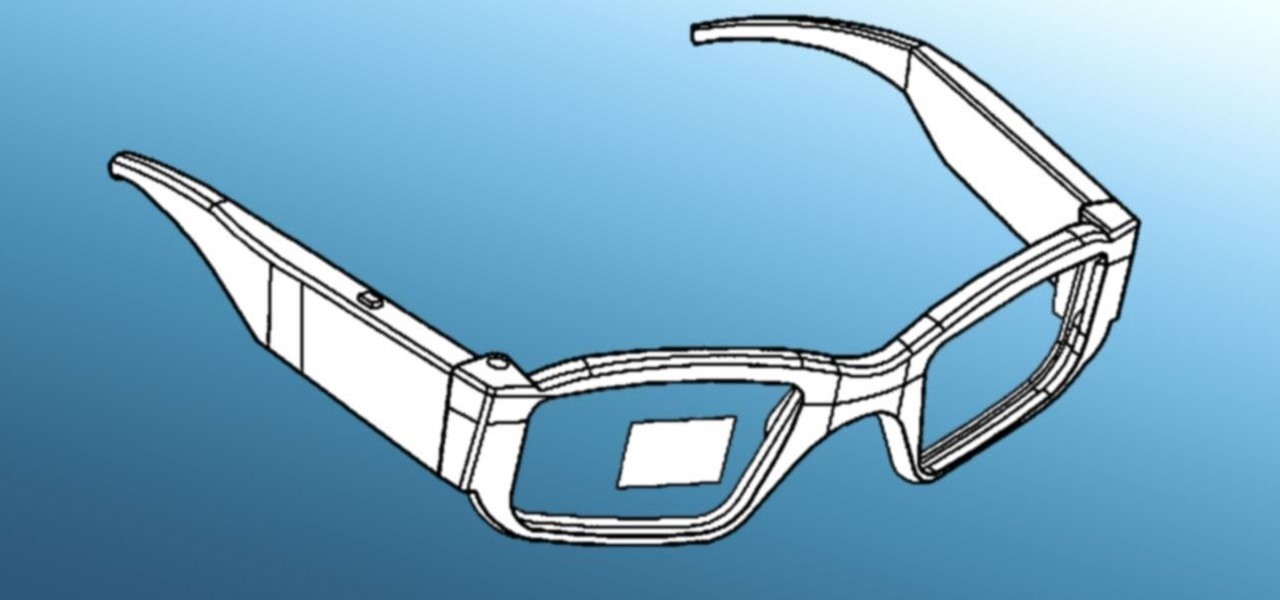
Historically, patents have never been a rock-solid source for uncovering the future of a company's product pipeline. However, sometimes, the images you find in the patent application search archives are so convincing you have to pay attention.

By using almost any packet-crafting tool, a hacker can perform denial-of-service (DoS) attacks. With the power to create just about any packet with any characteristics, a hacker can easily find one that will take down a host or network. Nmap and Hping are effective packet manipulation tools, but there's also Scapy, which is almost infinitely customizable.

Directory traversal, or path traversal, is an HTTP attack which allows attackers to access restricted directories by using the ../ characters to backtrack into files or directories outside the root folder. If a web app is vulnerable to this, an attacker can potentially access restricted files that contain info about all registered users on the system, their permissions, and encrypted passwords.

In the current state of the augmented reality space, Leap Motion is the only well known name in DIY AR headset kits with its Project North Star design, which gives makers the blueprints to build their own headsets.

In recent years, Apple has assembled its augmented reality team and supply chain through a series of acquisitions, high-profile hires, and strategic investments, but at least one potentially major deal was recently ditched.

Hand tracking technology company Leap Motion has built a stunningly fluid augmented reality ping-pong game that not only showcases the capabilities of its open source Project North Star augmented reality headset, but also demonstrates how artificial intelligence can elevate immersive experiences.

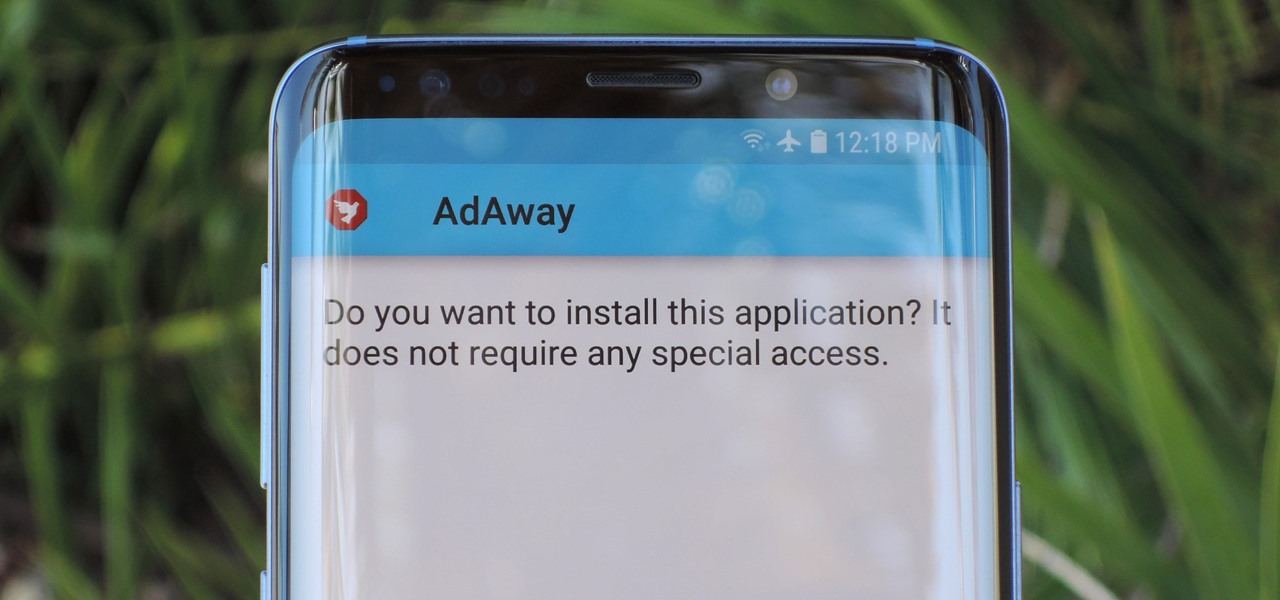
Starting with Android 8.0 Oreo, the process of sideloading apps has changed dramatically. Google removed the old "Unknown Sources" setting and replaced it with a permission that you have to grant to individual apps. It's really an interesting security feature.