Drones are popular little toys, but they're not the easiest things to control. While hand gestures may not change that too much, donning a HoloLens and flying a physical object with a wave of your hand at least makes the process feel a lot more like a telekinesis.

Considering how much smartphones cost in the first place, we're understandably reluctant to throw them out when we've bought a newer model. And this is probably the best practice, too, as there are many great uses for an old Android device.

The Oculus Rift is finally shipping to customers in more than 20 countries, and we're getting a good idea of how the device holds up from the initial reviews. You'll see some common threads throughout: along with an impressive virtual reality experience, the device is very comfortable with a solid design.

In the tech world, it's all too common to slap a fake label and packaging on a lower quality product, especially SD cards. If you've ever bought an SD card on the cheap from a slightly-less-than-reputable source (or even a reputable source, in some cases), how do you know if it's the real deal?

Want the next level security? Well then take a read here because this is some next level stuff. Heard of It?

Windows 10 has proved to be immensely popular (free upgrades certainly don't hurt), and with back to school time, there's a good chance you have a new computer running Microsoft's latest OS. You maybe you decided to go with a clean installation rather than an upgrade, or just haven't used your computer for much more than surfing the web and watching Netflix.

In my last how-to, we built a man-in-the-middle tool. The aforementioned script only established a man-in-the-middle. Today we'll be building a tool to utilize it. We'll be building a DNS packet sniffer. In a nutshell, this listens for DNS queries from the victim and shows them to us. This allows us to track the victims activity and perform some useful recon.

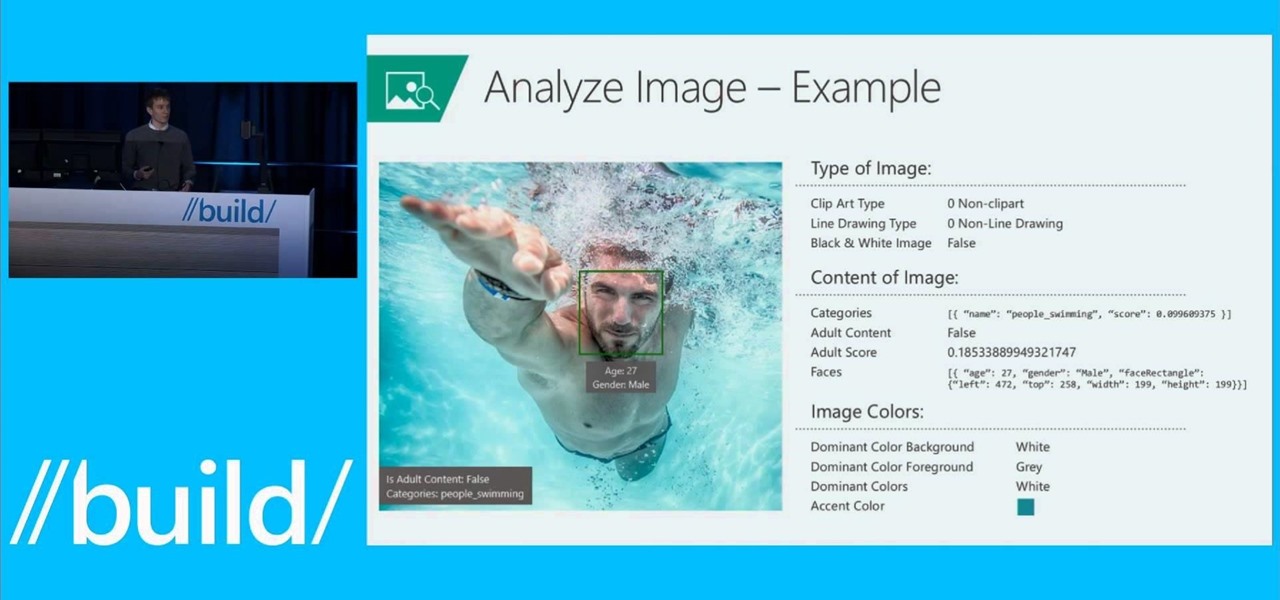
Microsoft is developing a new API project called poject "Oxford," and it includes face, speech, and more "smart" API technology. Despite being Microsoft, I actually found this to be very useful. ;)

Ad blocking on Android usually requires root access, but a pair of new browsers based on the open source Chromium and Firefox builds are looking to change this.

After you have registered to this site,sign in then to start missions. Basic Missions

Welcome back, my rookie hackers! In my ongoing attempts to familiarize aspiring hackers with Linux (nearly all hacking is done with Linux, and here's why every hacker should know and use it), I want to address a rather obscure, but powerful process. There is one super process that is called inetd or xinetd or rlinetd. I know, I know... that's confusing, but bear with me.

With over a billion monthly active users, it seems that Facebook is nowhere close to being dethroned as the most popular social media service in the world (sorry, Ello). While their stats may be impressive, it doesn't mean that Facebook is as good as it can be.

The internet is forever. When you put something out there, it can easily be re-shared, floating from server to server indefinitely with no way of taking it back. It's a scary thought when you consider that a young adult's grandchildren will one day have access to their drunken party pics.

AllCast, from renowned developer Koushik Dutta (better known as Koush), allows users to stream personal media, such as movies, photos, and music from mobile devices to Chromecast and other streaming devices.

Apple's iPhone 6 packs a powerful 4.7-inch Retina HD display with 1334-by-750 resolution, and it's so incredible in person that it almost looks fake. However, as awesome at this display is, it can always be better.

Before Apple jumped into the phablet game with their iPhone 6 Plus, there was the Samsung Galaxy Note series. Initially knocked for their size, the Notes slowly but surely gained popularity, thanks to powerful hardware, incredible displays, extensive features, great battery life, and a surprisingly-useful stylus.

Welcome back, my novice hackers! Before we try to attack a website, it's worthwhile understanding the structure, directories, and files that the website uses. In this way, we can begin to map an attack strategy that will be most effective.

I hate to break it to you, but you're probably here because you were trolled. Thanks to a Photoshopped image making rounds across Twitter, Apple fans were tricked into believing that iOS 8 allowed them to lock individual apps, accessible only through a passcode or fingerprint ID. While that's not technically true, we've got the solution for you.

In 2012, VideoLan published a beta release of their wildly popular desktop media player, VLC, for the Android platform. However, because the non-profit development team did not have access to popular North American Android devices, they opted to exclude the USA and Canada from their initial release. That is, until now.

If you're using iOS 10 or lower, there is no built-in way to record an iPad, iPhone, or iPod touch screen, and Apple doesn't allow any third-party apps to screen record either. If malicious, an app could theoretically continue recording even after you think it's off, allowing it to capture account and password information that you enter on your device. This changes in iOS 11, which introduces native screen recording, but what do you do if you're still running iOS 10 or lower?

Amazon released the Kindle Fire HDX back in late-2013, and if you picked one up or received one as a gift, you've probably had a good amount of time to get to know your tablet.

Of the sixty or so "must-have" apps that are installed on my Samsung Galaxy Note 3, there's only one that I need to use and hate with a passion. Skype. Whenever using it, I'm consumed by dropped calls, mic issues, poor quality, and random crashes, among other things—and I'm not the only one.

Safari has some cool new features in iOS 8, but the app that seems to have gotten the biggest update so far is Messages. A lot of the new Messages features were discussed during Apple's developers conference, but we found many others and picked out our favorite hidden ones below.

Welcome back, my greenhorn hackers! Lately, much of the discussion here on Null Byte has revolved around evading detection and not getting caught hacking. Several of you have written me asking for a series on evading detection and forensics, and while I began a series 5 months ago on just that, we have changed hacking platforms from BackTrack to Kali, which has a much more highly developed forensic toolset.

Google's new camera, aptly named Google Camera, has been all the rage since it was released onto Google Play last Friday. The main reason is the amazing Lens Blur feature that adds depth-of-field Lytro effects to photos, without the use of any expensive accessories or extra hardware, like on the new HTC One M8. The camera does this by utilizing a depth map through the processing of multiple images. Frame your photo, move the camera (phone) in an upward tilt or motion, and the software capture...

While rooting your Galaxy Note 2 certainly has its advantages—everything from increasing security to relieving the Power button of its duties—it's definitely not for everyone.

This video tutorial shows How to make a Macrame Bracelet with fish symbol in another way. Historical explanation: The origin of this acronym is something else again. It is not in the Bible. No one really knows who first came up with the acronym ICHTHYS, ( in Greek, it is an acronym for Jesus Christ, the Son of God, our Savior ) used by early Christians as a secret Christian symbol and now known colloquially as the "sign of the fish" or the "Jesus fish".

Welcome back, my hacker novitiates! Recently, I demonstrated a hack where you could redirect traffic intended for one site, such as bankofamerica.com, to your fake website. Of course, to really make this work, you would need to make a replica of the site you were spoofing, or better yet, you could simply simply make a copy of the original site and host it on your own server!

This Square knot design feature picots, which are small loops at the sides of the knot. Picots are simply loops along the edges. Picot Designs are vintage Macrame techniques. They are often used to make the edges of craft items to look like as flower petals. This is a good project for children and beginners to learn one of the basic knots frequently used in Macrame. To this pattern you can add pearls and have an interesting look.

The Samsung Galaxy S5 was just officially announced at Mobile World Congress. The new flagship device will be available worldwide beginning April 11, 2014, including all major U.S. and international carriers. With over 200 million Galaxy devices sold to date, the S5 doesn't stray too far from the trend, at least not aesthetically. We've still got a high-grade plastic shell with perforated back covers, and four color choices at launch. Our highlights of the release event are as follows.

The Xperia Z1, Sony's flagship device, has been extremely popular overseas, so much so that it has made its way into the U.S. market as the Xperia Z1S, a modified version of the original. Known more commonly as the "waterproof smartphone," the Xperia Z1 packs one of the most powerful cameras on the market, with an impressive 20.7 megapixels. Since the device is only available for T-Mobile here in the States, unless you currently have that carrier, the chances of you getting your hands on Sony...

When you were younger, you probably had your parents bugging you not to have your cassette player headphones up too loud. For all you younger readers out there, it was probably a CD player. The even younger readers likely had an iPod or other MP3 player. Either way, your parents didn't want you to mess up your hearing, blasting that Limp Bizkit in your ears (wow, I'm showing my age here).

Ever since the early days of their existence, cell phones have been reducing the common wristwatch to nothing more than a fashion accessory. I'm not exactly a watch aficionado, but I do own a few that I wear on a daily basis. Since I have family in different parts of the world, I love my watches that have a second time zone, allowing me to see what time it is where they are.

WhatsApp is one of the most well-known and most utilized cross-platform chat applications available today. It's free for one year, and only $0.99 a year after, which is chump change when you realize there are no hidden costs like international charges. Basically, it creates an easy to use forum for you and your friends to chat, regardless if they're an Android or iPhone user.

Twitter's video-sharing app, Vine, had some very stiff competition once Instagram added video sharing to its repertoire. Recent figures show Instagram at 130 million followers compared to Vine's 40 million. Many think that Vine is on its way out, but on the contrary, I think it's here to stay.

Whenever the word "popup" pops up, I immediately cringe because all I can think about are those obnoxious ads that ruin my everyday browsing experience. But, not all popups are evil.

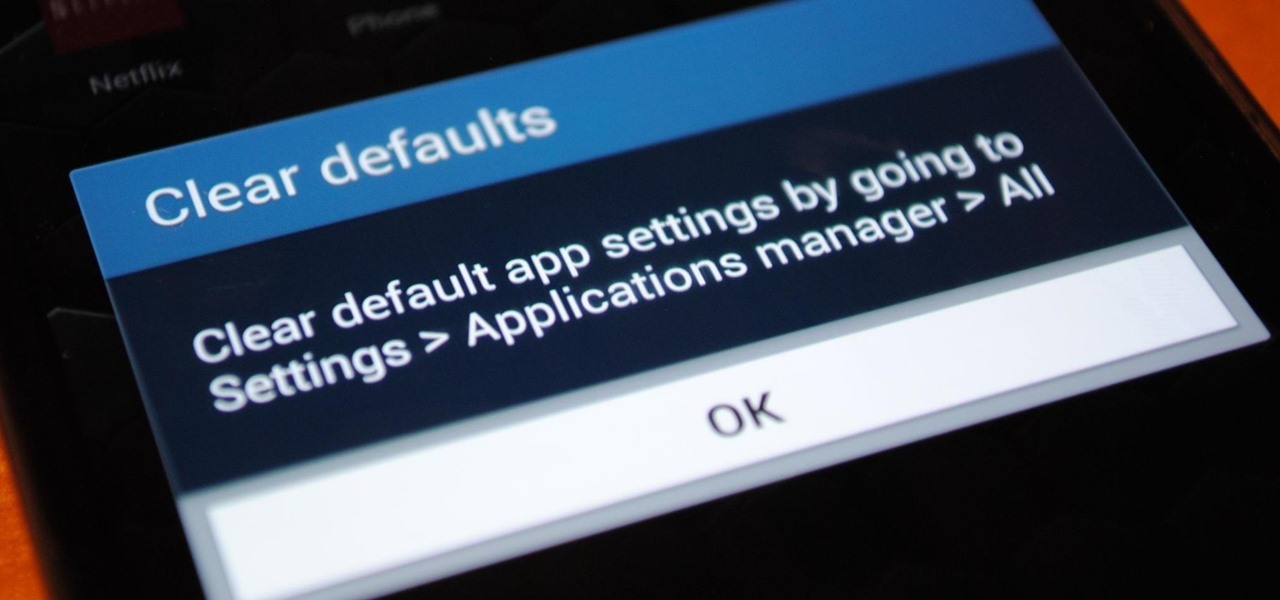
Customization is one of Android's popular selling points, and going hand-in-hand with that is being able to set default apps for different actions. Whether you want to play a song, navigate somewhere, or send a text, you can set a go-to app for each of those tasks.

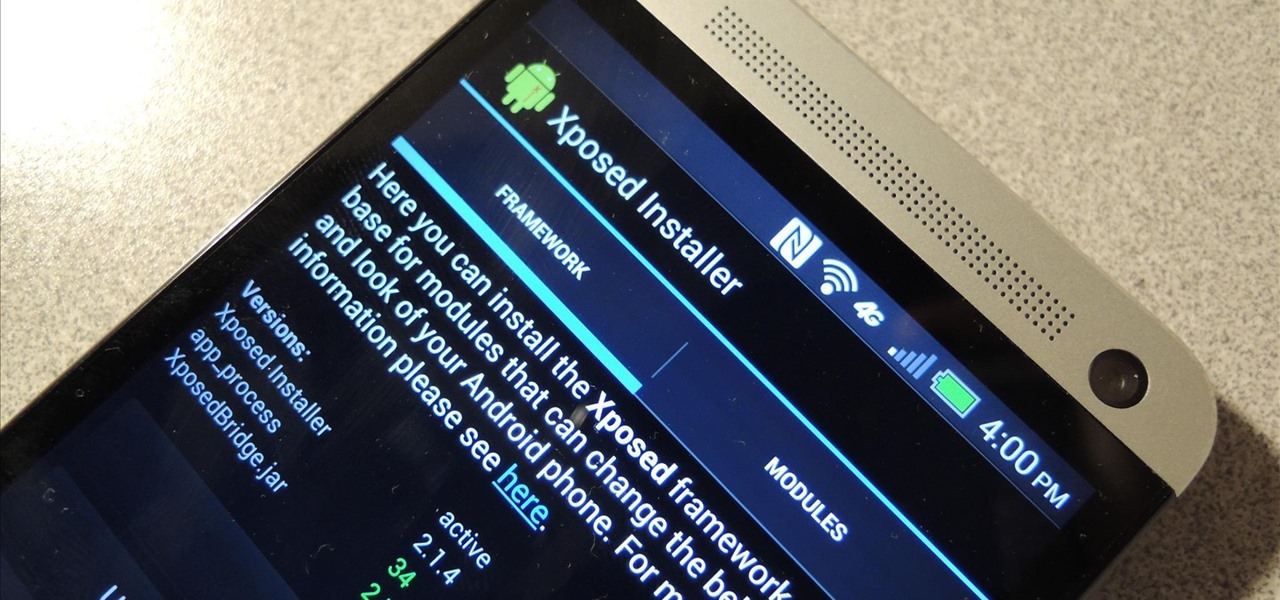
Update: The installation process for Xposed Installer is now dead simple—check out our updated guide!