Phishing is the easiest way to get your password stolen, as it only takes one mistake to log in to the wrong website. A convincing phishing site is key to a successful attempt, and tools to create them have become intuitive and more sophisticated. SocialFish allows a hacker to create a persuasive phishing page for nearly any website, offering a web interface with an Android app for remote control.

With a tiny computer, hackers can see every website you visit, exploit services on the network, and break into your Wi-Fi router's gateway to manipulate sensitive settings. These attacks can be performed from anywhere once the attacker's computer has been connected to the router via a network implant.
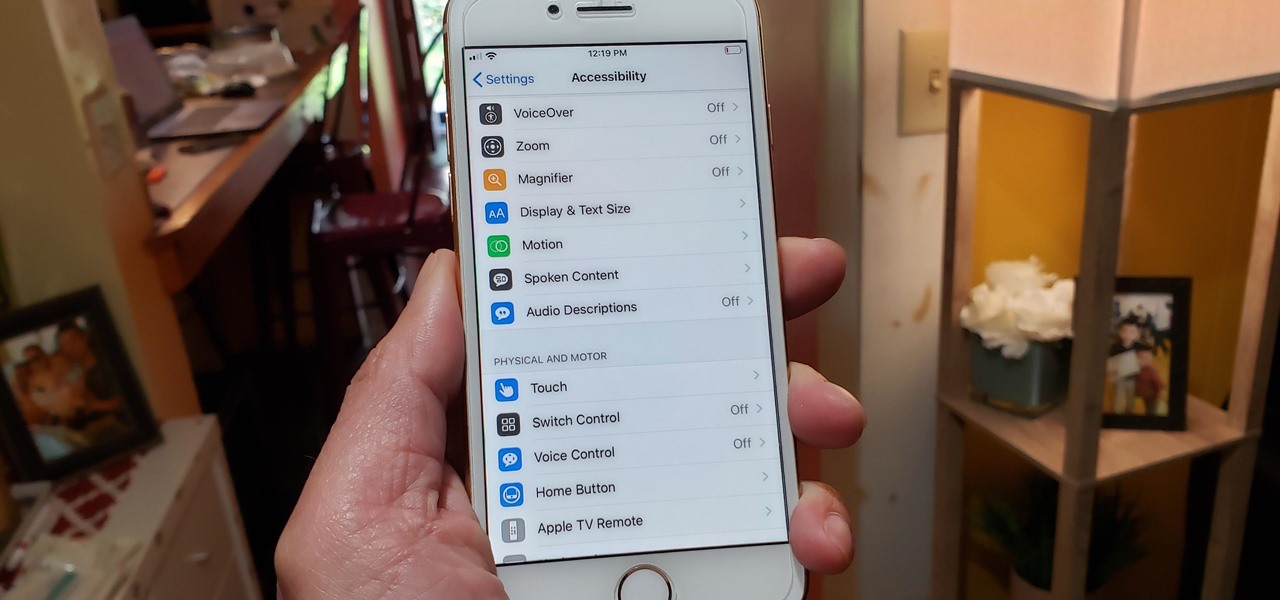
Beyond spotlight-grabbing features like Dark Mode and computer mice support that iOS 13 contains, Apple has also made its mobile platform more user-friendly for people that exhibit sensitivity to on-screen animations. If you've always found the transitional effects between app pages jarring, your iPhone now has a setting to help with that, preventing possible motion sickness and anxiety.
The Reader mode in Safari is a great way to view a webpage on your iPhone in a stripped-down manner, removing unnecessary images, videos, and advertisements for a streamlined experience free of distractions. Apple's iOS 13 improves upon Safari Reader when it comes to choosing which sites you want it to run automatically on, so everything is more accessible with more controls to work with.
For those with small hands, smartphones have gotten out of control as of late. Nearly every flagship phone is over six inches in length, so many are forced to use phones that are too big for them and hope they don't fall. Well, thanks to one developer, using these phones can be a lot easier.
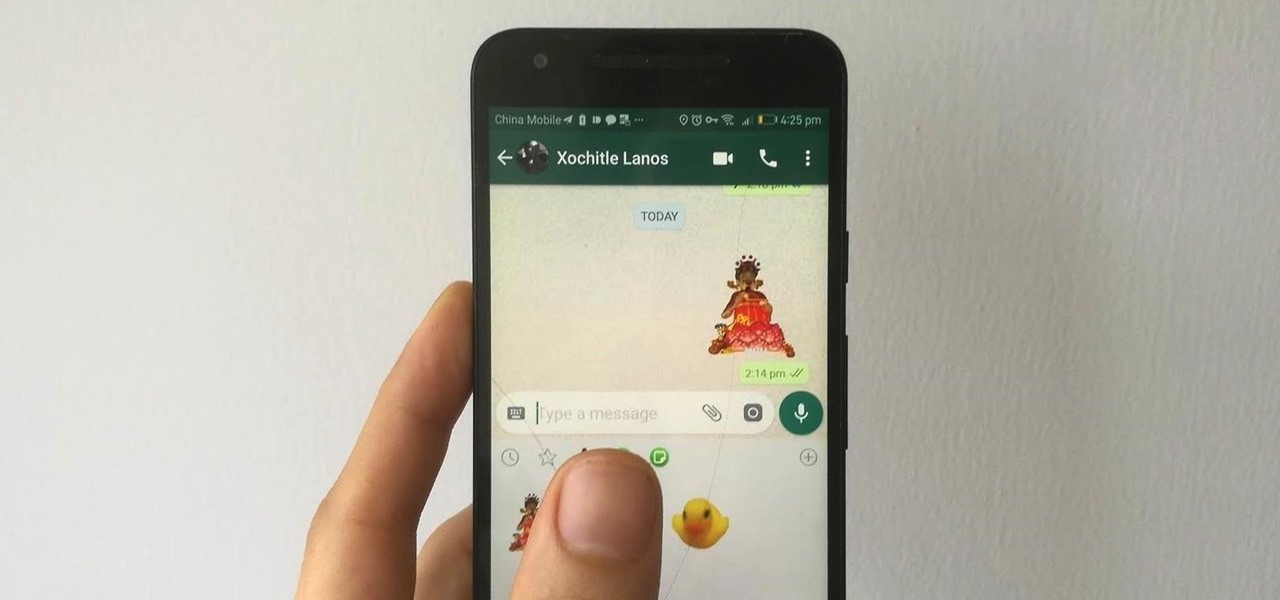
WhatsApp stickers can make your chat more fun. The stickers that come with WhatsApp are fine, but they're standard and accessible to everyone. What if you wanted to show off unique stickers that your friends haven't seen? To take things to the next level, you can create your own WhatsApp Stickers.

If you find yourself with a roommate hogging limited data bandwidth with video games or discover a neighbor has invited themselves into your Wi-Fi network, you can easily take back control of your internet access. Evil Limiter does this by letting you control the bit rate of any device on the same network as you, allowing you to slow or even stop data transfer speeds for them completely.

The next libSSH or OpenSSH exploit may be just around the corner. Keep your SSH service out of Shodan's database before hackers find new ways to bypass the password protecting the server.

Despite the recent gut punch of staff layoffs, Canada-based smartglasses startup North and its Focals are likely to be in the game for a while longer.

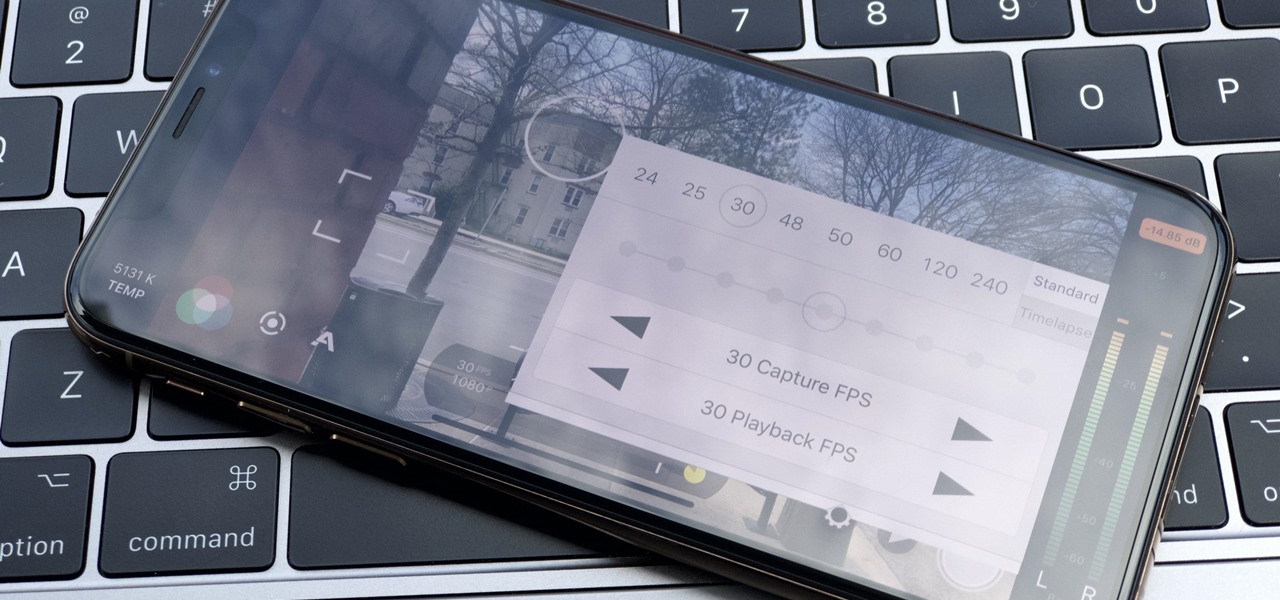
The days of bad smartphone videos are long gone. Your iPhone or Android phone is a capable video recorder, even offering different frame rate options in the native camera settings. Filmic Pro makes things a little simpler, however, and adds additional controls you wouldn't find on your device alone.

Over the past two years, Apple's Worldwide Developers Conference (WWDC) has become a showcase for new ARKit capabilities. This year, it could offer more information related to Apple's long rumored augmented reality wearable.

Tapping on your iPhone's display to pick up an incoming call can be annoying when your hands are wet or dirty. It might even fail to register and cause you to miss your call. If you have a jailbroken iPhone, however, you can get rid of this problem entirely, thanks to a free tweak that lets you instantly pick up calls without having to interact with your phone's screen.

Now that the dust has finally settled on Microsoft's big HoloLens 2 announcement, the company is circling back to offer more granular detail on some aspects of the device we still don't know about.

We're still weeks away from a probably HoloLens 2 release, but Microsoft's immersive computing team is still hard at work on other aspects of its "mixed reality" ecosystem.

The iPhone's notification system has drastically improved over the years, but it could still use some work. The notifications, while useful, are all monochrome, making it hard to distinguish which app posted each alert, and that's not even mentioning the drab overall look. This is where jailbreak tweaks can come in handy.

Though not as flashy as Face ID and other features, Low Power Mode has become one of the unsung heroes of iOS. When you're away from a charger, enabling this feature will dial back performance and networking to help you eke out up to three extra hours of battery life. If your device is jailbroken, you can even automate Low Power Mode to ensure your battery never dips to critical levels while out and about.

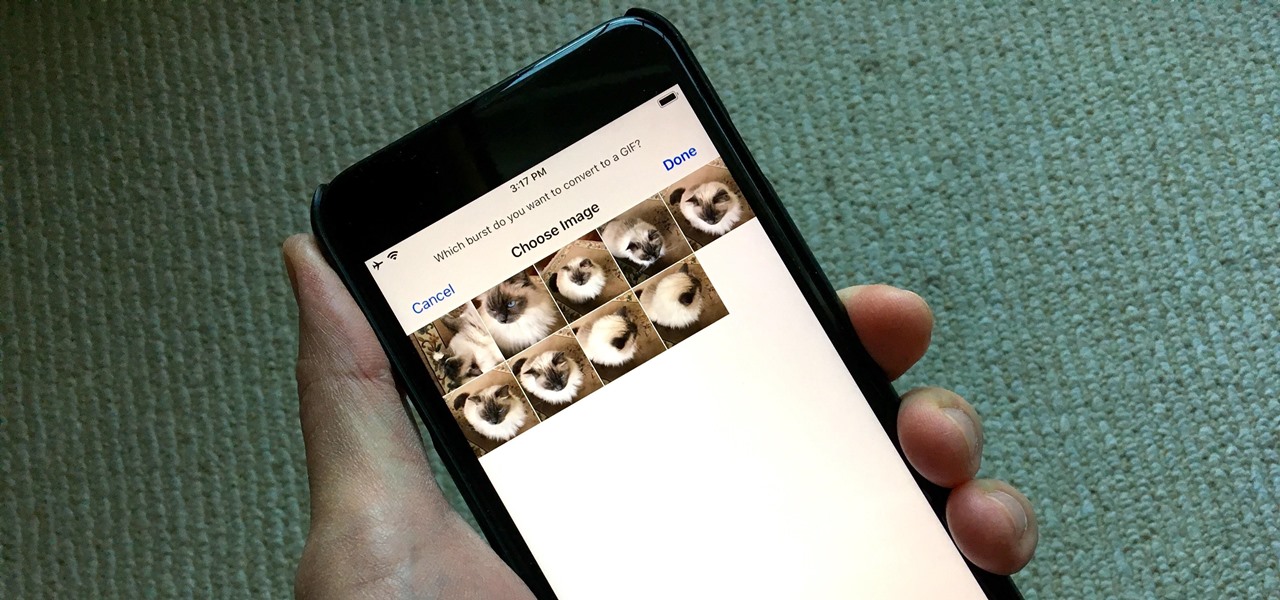
Creating GIFs of your own burst images has been possible for a while with third-party iOS apps, some of which cost money or include in-app purchases to utilize the full potential. Fortunately, with Shortcuts, Apple's automation workflow app, there's finally a native way to achieve this without spending any cash.

If you store important, sensitive information on your iPhone in Notes, you'll want to be more careful. When Notes syncs across your iPad and Mac via iCloud — devices that family members or coworkers may share — you run the risk of having your notes read, edited, and deleted by other people. Such a catastrophe is easily avoided.

Because timing is everything, the latest entry in the location-based augmented reality gaming sweepstakes, Ghostbusters World, has arrived just in time for Halloween.

For some Android users, this guide is sacrilege — but for others, iOS is just an attractive operating system that can be admired without feeling like you've betrayed your own phone. If you're one of those Galaxy Note 9 owners that have peeked across the aisle and desired an interface as clean as the one on the iPhone XS Max, you can configure your Note 9 to look like its rival with some tinkering.

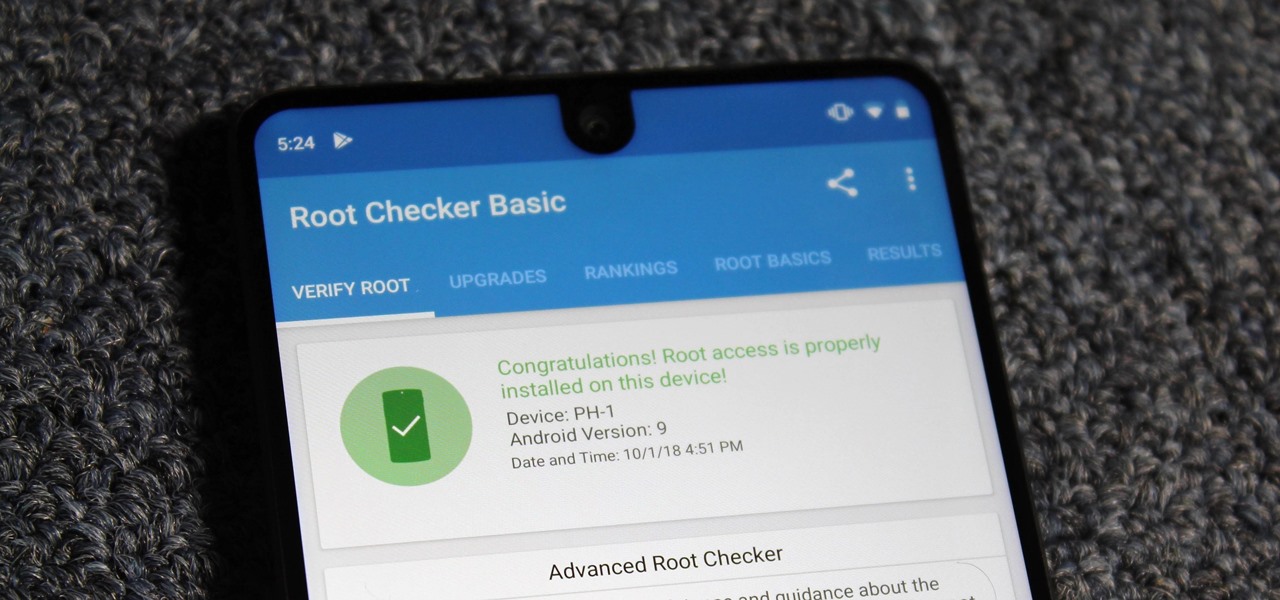
Despite its rocky start, the Essential PH-1 has a lot going for it. Not only does it get consistent security patches and system updates hours after the Pixels, but like the Google-developed lineup, it's also great for rooting. Not only is your warranty not void with rooting, but the process is pretty straightforward.

The newest version of macOS has arrived. While everyone's mind is being blown by Mojave's groundbreaking new Dark Mode, we'll be taking advantage of its insecure file permissions to establish a persistent backdoor with a self-destructing payload that leaves little evidence for forensics.

It's important to know who you're dealing with after hacking your target's MacBook. Getting remote access is simple, but covertly gathering information about the user and their system can be a challenge.

Xiaomi made a new phone with their sights set on picking up some ex OnePlus users. As a result, the Pocophone F1, or just Poco in some markets, is quite unlike most other Xiaomi phones. While you can't buy the F1 in stores in the US, you can get its home screen app on almost any phone right now.

Kali Linux, by default, probably doesn't have everything you need to get you through day-to-day penetration testing with ease. With a few tips, tricks, and applications, we can quickly get started using Kali like a professional white hat.

As penetration testers, we sometimes need to securely store customer data for prolonged periods. Bruteforce-resistant, vault-like containers can be created with just a few commands to protect ourselves from physical attacks and unintended data disclosures.

The Magic Leap One: Creator Edition has been teased for months now, and while we still don't know exactly when the sales will begin, it can't be long now because we've discovered a couple of new hints that the device's launch is imminent, hiding in plain sight on the company's website.

A new study published by American University demonstrates how Pokémon GO and other augmented reality games can help city governments bring communities closer together.

Soon, you'll be able to buy your OnePlus 6, but you can experience some of its apps today thanks to XDA user erayrafet, who ripped a few OxygenOS apps like Weather and this Gallery app. While Google Photos is a great service, this Gallery app should be your go-to app for locally-stored photos.

While hackers have taken advantage of numerous vulnerabilities in Adobe's products to deliver payloads to Windows users via PDF files, a malicious PDF file can also wreak havoc on a Mac that's using the default Preview app. So think twice before double-clicking a PDF open on your MacBook — it might just be a Trojan with a rootkit inside.

The OnePlus 6 is finally in customers' hands along with its top-of-the-line specs — and yes, a notch. But you can start getting some of their stock apps as early as today, thanks to XDA user erayrafet, who ported this Weather app directly from the source.

Earlier this year, we got our first taste of Android Pie in the form of Developer Preview 1. As with all past Android previews, DP1 was limited to Google devices — but at Google I/O 2018, Google announced that Developer Preview 2 would be accessible to other devices, including the Essential PH-1.

Its official: On May 8, T-Mobile finally released the Android Oreo update for the LG V30 and V30+. Now, every major US wireless carrier has pushed the update. For me, this update is a big deal. Not only does Android Oreo bring some new tools and features, but LG has also included a few additions as well.

Smartphones are still "phones," which means communicating with others is usually a primary use. Ranging from a simple "hi" to a more personal conversation and even sharing passwords, our messages should remain private so that only the intended recipient sees their content. While many apps tout end-to-end encryption, not all apps prioritize security and privacy.

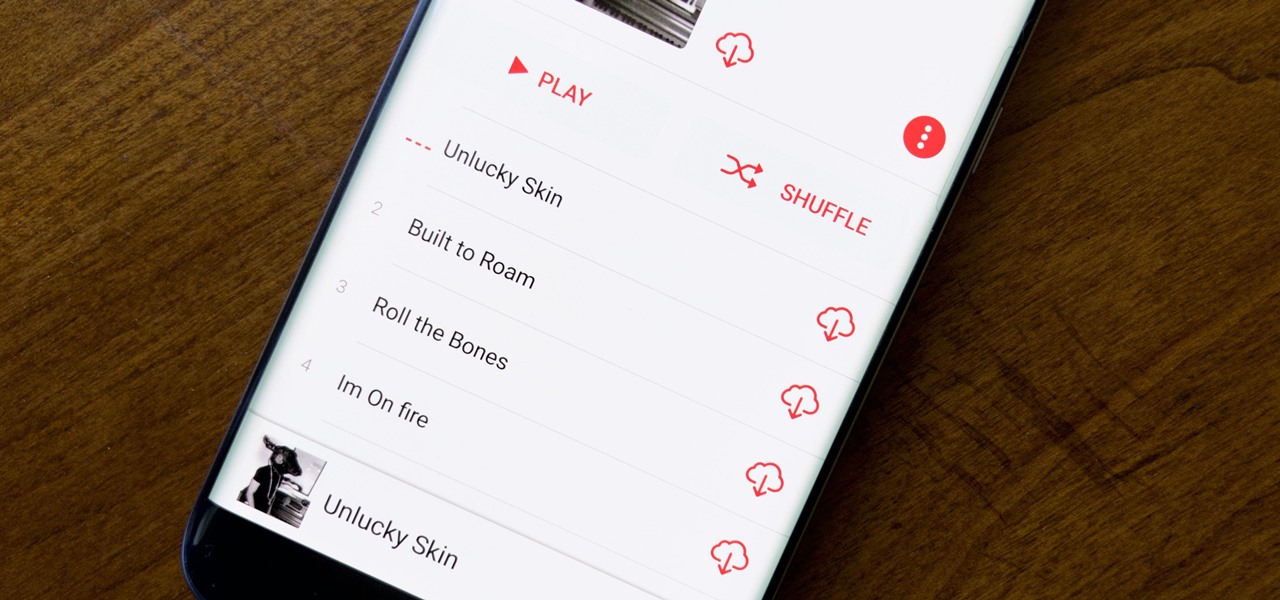
For most carriers, "unlimited" data plans aren't really unlimited, and they still cost more than data limited plans. So while subscribing to music streaming services and storing your own music library in the cloud may be more convenient, it may eat your data up like candy. To keep that from happening, try downloading tracks from Apple Music for offline playback.

The key to becoming a competent white hat is knowing how the technology that you are trying to exploit actually works. SQL injection is one of the most common methods of attack used today and also one of the easiest to learn. In order to understand how this attack works, you need to have a solid grasp of ... you've guessed it ... SQL.

Analysis of photographs and social connections can be a huge component of social engineering. Understanding who a person is, as well as who they know, can establish links within a company. This information could be used by hackers to execute elaborate social engineering attacks.

With over 1 billion downloads on the Play Store alone, Google Maps has become a staple for those traveling. Its popularity is the result of Google consistently improving its accuracy and adding new functionality. And this was only achieved with help of you — specifically, your data.

Before Google Chrome entered the scene and subsequently dominated the market, Firefox trailed only Internet Explorer as the most popular web browser. Now, Mozilla has its sights set on a new opportunity to revive its browser for immersive experiences.

With numerous insider reports, patent awards, acquisitions, and hires over the past few years, augmented reality smartglasses from Apple appear to be an inevitability.