Tor is an excellent obfuscation network for web traffic, and while instant messaging over the network is very useful, it can be relatively difficult to configure. In this guide, we'll look at two synchronous communications platforms (instant messengers) which can be routed over the Tor network, Ricochet and XMPP.
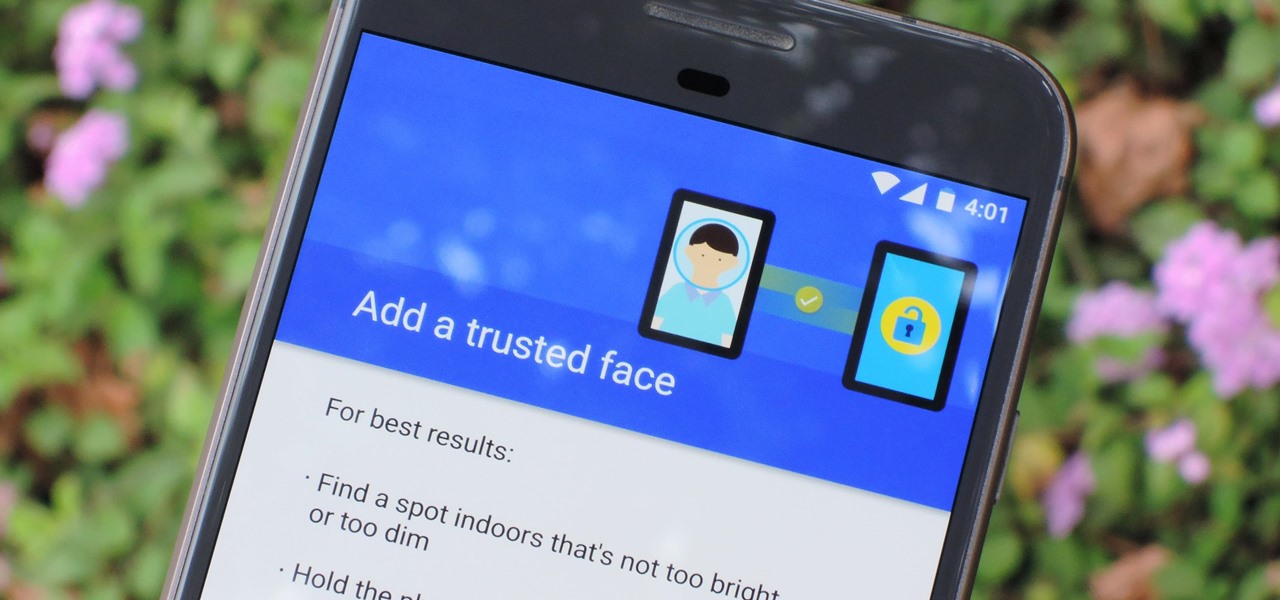
The iPhone X has a new unlocking mechanism called Face ID, which replaces the old Touch ID system since the phone no longer has a fingerprint sensor. The way it works is simple — you just look at the phone, it recognizes your face, then the system unlocks — so Apple deserves the praise they're getting for it. But did you know you can get almost this exact same feature on any Android device right now?

While Apple's tech used for Face ID on the iPhone is impressive, it's debatable whether it's more convenient than Touch ID. There are also concerns that your face could be used to track shopping patterns or be seen during mass surveillance by intelligence agencies. More importantly, it could be easier for law enforcement, and even thieves, to force you to unlock your iPhone.

The OnePlus 5 had been in the hands of the public for a meager twenty hours before developers on XDA released a custom recovery image for it, and the 5T had a similar trajectory. The installation process is simple enough, but it can be somewhat confusing if you're new to modding Android.

For those of us on the fast ring of the Windows Insider Program — Microsoft's continual beta program for the Windows operating system — the constant updates can be a bit of a pain. But there is a trade-off. We get to try the new features long before they come out to the public. So if you like to see the new shinies before everyone else, and don't mind the sometimes two or three major updates in a week, then this is definitely the option for you.

A case of West Nile virus recently confirmed in a person in Barton County, is the first human case of 2017 in Kansas. State health officials confirmed the appearance of West Nile this year in a press release on June 9th.

With the US Department of Homeland Security (DHS) banning laptops and tablets on flights originating from 10 international airports, and the United Kingdom taking similar precautions, international travelers are faced with hours of non-productive — or far less entertaining — flight time.

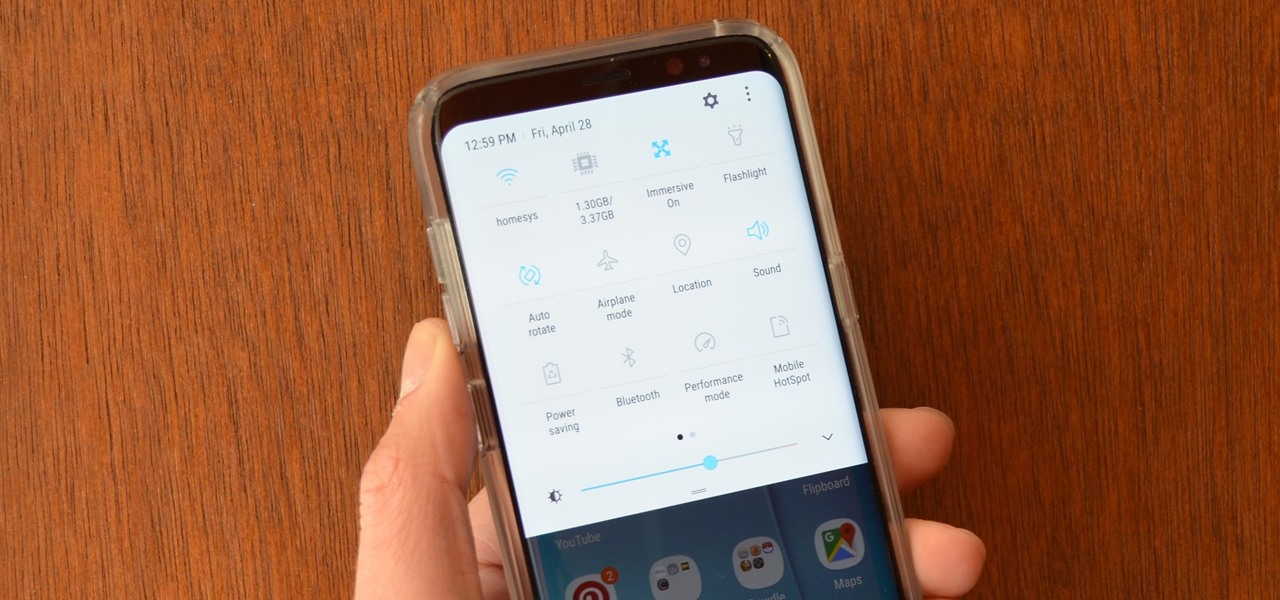
Up until now, enabling full-time Immersive Mode on an Android device has been a tedious task which required you to run individual ADB commands each time you wanted to toggle it on or off. This was a shame, too, since Immersive Mode helps reclaim lots of screen real estate by auto-hiding your navigation and status bars.

Despite a round of updates to Pokémon GO that patched and eliminated location spoofing, the game still has a difficult time dealing with the most hardcore cheaters. Like weeds on a grassy lawn, third-party bot makers still remain the biggest thorn in Niantic's side and continue to thrive despite the developer's best efforts to root them out. While the latest updates have blocked users from running modded versions of the game, like Pokemon GO++, that feature built-in joysticks to move your pla...

With the Game Developers Conference (GDC) in San Fransisco just a few weeks away, Microsoft Senior Program Manager Vlad Kolesnikov has announced via Channel9 (Microsoft's developer news outlet) that not only will new low-cost virtual reality headsets be coming in March to developers, but that they will be at GDC, too.

When temperatures drop and hit new lows during the cold, winter months, it's hard not to crank the heat up. That means increased energy bills each month, no matter if you rely on gas, electric, or another fuel for heating.

Welcome back, my novice hackers! In this series, we have been exploring how a forensic investigator can find evidence of illegal or illicit activity. Among other things, we have examined the registry and prefetch files for artifacts and have done some rudimentary forensic analysis. For those of you who are seeking career as a forensic investigator or security engineer, this can be invaluable training. For hackers, it might be life-saving.

The dock in Mac OS X is intuitive, customizable, and aesthetically pleasing, which is a stark difference from its clunky Windows alternative. In fact, in Windows, it takes both the Start menu and taskbar to accomplish what Apple's dock does—but it doesn't have to be like that. Below, I'll show you how to add an OS X-inspired dock on any PC running Windows XP or higher. Step 1: Install Aqua Dock

You need a good microphone on your computer in order to make audio recordings, voice chat, or use speech recognition. However, not every computer comes with a built-in mic, and not every built-in mic works great.

Welcome back, my tenderfoot hackers! Recently, Microsoft released a new patch (September 8, 2015) to close another vulnerability in their Windows Vista, 7, 8, and 8.1 operating systems. The vulnerability in question (MS15-100) enabled an attacker to gain remote access to any of these systems using a well-crafted Media Center link (MCL) file.

Task Manager got revamped quite a bit in modern versions of Windows. First introduced in Windows NT 4.0, it's become pretty popular among more advanced users. In Windows 10, Task Manager is not just a task manager anymore, it's also a system monitor, startup manager, history viewer, user controller, and the list goes on.

Cortana, Microsoft's personal assistant for its Windows Phones and Windows 10, will soon be released for Android. That is, officially released. It's hard to keep a good thing locked away, and to that end, Cortana for Android has been leaked, thanks to APK Mirror.

So, we all probably know that when you run a trojan made by Metasploit, nothing will appear to happen. This is a sign for me to immediately check my Task Manager, but for an unsuspecting victim, it will just seem like a broken file. It is likely that they will delete this "broken file" once they see that it "doesn't work." In order to prevent this, we need to disguise the trojan.

Presented by Apartments.com When looking for a new apartment, it's hard not to notice the improvements (on large and small scale) needed prior to moving in. While your landlord may be taking care of new carpeting, cleaning the central air vents, and fresh paint on the walls, there may be some additional improvements on your list that you can take care of on your own. Here are five quick improvements you can check off your list before the big move.

Back when CRT and plasma monitors were still a thing, screensavers served a purpose beyond just aesthetics: the moving images and patterns prevented static images from being burned into the display.

Google has already started to roll out the over-the-air update of Android 5.0 Lollipop to older Nexus series phones and tablets, but chances are it will take a long time for the OTA to hit your device.

Welcome back, my tenderfoot hackers! I recently began a new series on digital forensics to help tenderfoot hackers from being detected and ultimately, incarcerated. In this installment of that series, we will look at recovering deleted files. This is important to hackers because you need to know that even when you delete files on your computer or on the victim's computer, a forensic investigator can usually recover them.

Need to clear you cache? This guide details how on any web browser (Chrome, Internet Explorer, Firefox, Opera, Safari, Internet, and Dolphin) for any platform (Windows, Mac OS X, iOS, and Android). What Is the Cache Exactly?

Welcome back, my fledgling hackers! There's an evil dictator hellbent on destroying the world, and in one of our last hacks, we successfully compromised his computer and saved the world from nuclear annihilation. Then, we covered our tracks so no one would know what we did, and developed a hack to capture screenshots of his computer periodically so we could track of what he was up to next.

I rarely ever turn my desktop off. For starters, it takes a few minutes to boot up, which I hate, and secondly, putting the computer to sleep is perfectly adequate. You really only need to completely shut down your computer every once in a while.

Archive files are great for portability and saving space, but a lot of people don't know they can also be encrypted. There are a lot of archiver programs out there, but most of them can open a file that's been encrypted using other software, as long as you're using a recent version.

Since the release of iOS 6, there has been a bit of an uproar over some of the new features (the new Apple Maps replacing Google Maps) and certainly over the glitches that always come attached with new operating systems. Downgrading Your iOS

Have you ever had this happen? Your main OS is windows, and you just istalled a nux dualboot. But when you installed GRUB to the mbr, your windows loader got deleted! Hence you are not able to get into windows anymore... Sucks. But there's also a solution!

From a holiday window display in Paris, France last Thanksgiving.

At a windows partner conference in Taipei, Microsoft unveiled their Windows 8 tablet. First impressions: WOW! Looks like they are actually innovating for once.

Child Safety Window Treatments

Hotmail just isn't the same anymore— it's better! In the just-released Windows Live Essentials 2011 from Microsoft, Windows Live Hotmail 2011 is jam-packed full of new features.

In this clip, you'll learn how to add or remove a font on a desktop or laptop computer running the MS Windows Vista operating system. For more information, including a complete demonstration of the process and detailed, step-by-step instructions, watch this home-computing how-to. Add or remove a TrueType or OpenType font on a Microsoft Windows Vista PC.

In this clip, you'll learn how to make adjustments to default font size on a desktop or laptop computer running the MS Windows Vista operating system. For more information, including a complete demonstration of the process and detailed, step-by-step instructions, watch this home-computing how-to. Adjust the font size on a Microsoft Windows Vista PC.
Windows Live SkyDrive which is initially termed as Windows live folders is one of the parts of Microsoft Windows online service. It is a password protected service that allow users to store file and share them with others. Here the windows live id is required to access the users profile. Anyone can make his/her files private or public. Public share file are easy to access without requiring any Windows live id.Initially it was available only few states in United States. But nowadays it expande...

This tutorial shows you how to change the default window title name from osCommerce to whatever your store name is using cPanel X. Change the osCommerce default window title in cPanel X.

How to send pop-up messages to friends on a local Windows NT network. Send pop-up messages to friends on a Windows network.

De-clutter your desktop and learn how to get a minimal, but functional, look to your Windows XP desktop. Make a minimal Windows desktop.

Have you ever wondered how to create an invisible folder? I mean an invisible folder, not a hidden folder. Nowadays, we are facing lots and lots of problems requiring us to keep our data safe and secure. There are millions of hackers all around the world that are trying to steal our information whenever we get onto the internet. Even some of our friends are trying to lay their hands on our personal and confidential information.

Looking for some new ideas in facepainting? This video will show you how to paint a squirrel monkey face. The squirrel monkey has an adorable face, and this design is sure to be a hit with anyone getting their face painted. Perfect for kids' parties.