
How To: Hack WiFi Using a WPS Pixie Dust Attack
Long time reader, first time 'How To' poster. This tutorial has been highly requested. Here are the steps to perform a Pixie Dust attack to crack a WiFi password that has WPS enabled.


Long time reader, first time 'How To' poster. This tutorial has been highly requested. Here are the steps to perform a Pixie Dust attack to crack a WiFi password that has WPS enabled.
Well Welcome Back My Fellow Hackers. What is Slowhttptest? You may be asking. Slowhttptest is a Application Layer Denial of Service attack aka an attack on HTTP. You can read more about it here and also download it if you don't have Kali Linux. slowhttptest - Application Layer DoS attack simulator - Google Project Hosting.

Welcome back, my rookie hackers! Many newbie hackers focus upon the technical aspects of hacking and fail to give enough attention to social engineering. In fact, I would say that technical hacks should ONLY be attempted if social engineering attacks fail. Why bother spending hours or days trying to hack a password if someone will simply give it to you?
The mysterious, still unidentified missile that was seen yesterday off the coast of Southern California is stilling boggling Los Angeles residents. The projectile was seen on November 8th, shooting straight up into the sky, just north of Catalina Island.
In this video tutorial, you'll learn how to use Cheat Engine 5.5 to hack Penguins Attack TD 2! It's easy. So easy, in fact, that this clip can present a complete overview of the process in about five minutes' time. For more information, including detailed, step-by-step instructions, take a look.

Big predators pose a big threat unless you know what to do under attack. HOW TO SURVIVE advises making lots of noise, freezing when confronted, and playing defense in order to survive. Watch this video outdoor safety tutorial and learn how to survive an attack from a large predator, like bears or cougars.

In this chess lesson, you'll learn how to do Greco's Attack in the Giuoco Piano, in an Italian Game. Everyone chess master should learn this, because you're middle game isn't getting any stronger.

Do you know what a "double attack" is in a chess game? Well, the "knight fork" is basically the same thing; a simultaneous attack of one piece against two opponent pieces. Don't let your opponent win! Use this.

In this episode of Full Disclosure we are explaining the website attack known as Cross-Site Scripting (XSS). Cross-Site Scripting is a type of security vulnerability that affects web applications that do not sanitize user input properly. This kind of vulnerability allows an "attacker" to inject HTML or client side script like JavaScript into the website. Cross-Site Scripting is most commonly used to steal cookies. Cookies are used for authenticating, tracking, and maintaining specific informa...

This tutorial shows you how to execute the first two sets of primary moves with the bo: group 1 (attacks) and group 2 (blocks). It also shows how to change grips.

This tutorial for Devil May Cry 3 covers the basics of jump canceling and the overall advantages it will provide the player once mastered. The whole concept of a Jump Cancel (JC/JCing for short) is the cancellation of an aerial technique with a jump.

Design flaws in many routers can allow hackers to steal Wi-Fi credentials, even if WPA or WPA2 encryption is used with a strong password. While this tactic used to take up to 8 hours, the newer WPS Pixie-Dust attack can crack networks in seconds. To do this, a modern wireless attack framework called Airgeddon is used to find vulnerable networks, and then Bully is used to crack them.

Good day people, today we will examine some basic, for some people well-known attacks, also we will take a look at some advanced attacks.

Recently the newly famous ProtonMail service was under attack by DDoS attack. This attack was believed to be the hacking group Armada Collective.

So you've mastered the basics of using a shield and going up against an opponent who also wields a sword and shield. This tutorial shows you how to both stage an effective side attack, and how to defend against an opponent making the same attack on you.

Geoff and Jack from Achievement Hunter, show you how to deny a sword lunge with a well-timed melee attack. The tip is to time your block just right because if you get hit with the sword, you're dead, so if you get the timing right it'll still cause you to lose your shield but you could get some shots in between blocking, especially if you're out of other weapons.

Battle in verses 1-12, killing Fairness and Angels, in the Xbox 360 game Bayonetta. In Chapter 3 - Burning Ground, you have to make sure you know what you're doing. In verse 4, the creature is called Fairness. A soon as it appears it will shoot a fireball at you, be sure to dodge it. Fairness has several attacks it uses. It can shoot fireballs, which move faster than other fireballs you've encountered. It has a charge attack that you can dodge or you can jump over it. It also has a sonic atta...

You can’t always get rid of panic attacks completely, but you can learn to live with them. Watch this video for helpful tips on controlling the situation.

Your family and estates have come under attack, and you must defend them! This walkthrough for Assassin's Creed: Brotherhood shows you how to get through this part of the game, in large part by manning the cannons against your enemies.

In MMA nearly every part of the body is fair game for attacks and attacking, even the toes. In this video Joanne and Risha of MMA Girls will teach you how to use a toe hold to submission an opponent.

If your arm is tingling all fuzzy-like the way it does when you've slept on it wrong all night but you've been up for more than a few hours, then you may have a case of the stroke rather than sleep-induced wonky arm.

In this Sports video tutorial you will learn how to play midfield in soccer. Adrian Heath, Head Coach of Austin Aztex, explains the role of the midfield player in this video. Midfield player is the engine room of the team. He moves forward and feeds the ball to the strikers for attacking the opponent's goal and falls back in to his own half when defending. Two midfield players combine to pass the ball from the defending half to the attacking half past the opposing midfielders. There are many ...

In this video pest control specialist Mark Govan of ABC pest control shows you how to fight the war on fleas. Protect your home and animal from getting attacked by these blood suckers.Follow the advice in this video and make sure you prevent an invasion or attack on these annoying little creatures.
Learn everything you could possibly want to know about the internet, multiplayer game Evony with help from alexstewart2. Watch this video tutorial to learn how to farm rose, lion, cross, and nation medals in Evony.
COD4 Pro Nade Tutorial See how to do a pro nade attack in Vacant on COD4. For this grenade throwing tutorial, you need to be in Multiplayer mode, Search and Destroy, on Call Of Duty 4: Modern Warfare.

COD4 Pro Nade Tutorial See how to do a pro nade attack in Crossfire on COD4. For this grenade throwing tutorial, you need to be in Multiplayer mode, Search and Destroy, on Call Of Duty 4: Modern Warfare.

Cary Kolat demonstrates wrestling technique - collegiate offense - single leg series - shoulder roll attack below hips. Check out this coaching video from Kolat.com archive of wrestling drills and moves.
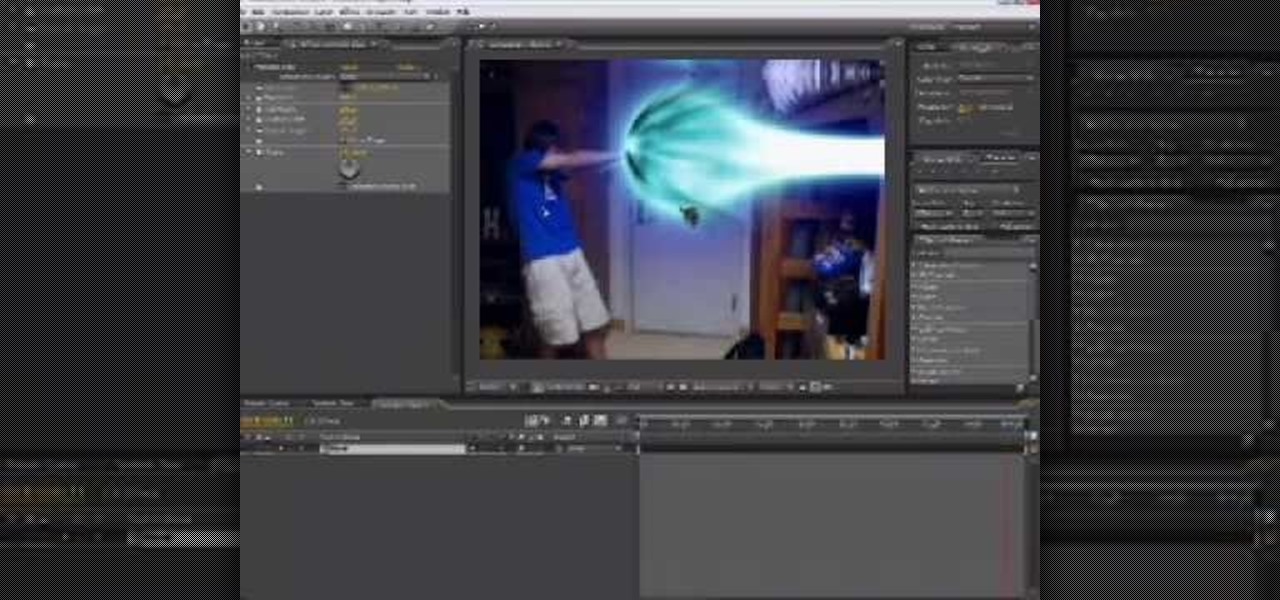
No, the Kamehameha is not the famous Hawaiian king who united all the islands under his rule from 1795 to 1819. Nope. However, it is named after him. But in this case, Kamehameha is an energy blast attack shown in the Dragon Ball Z series. And with this After Effects tutorial, you're going to learn how to recreate this energy attack.

Jarret Waldman explains why Imi the founder of Krav Maga uses a single handed defense instead two in other systems for gun from the front attack.

What makes you better than your opponent in Jiu Jitsu? The ability to chain attacks, one right after the other.

How to attack from someone's guard (you in the mount position) in Jiu Jitsu using the heel hook technique.

Brute-forcing is an easy way of discovering weak login credentials and is often one of the first steps when a hacker finds network services running on a network they gain access to. For beginners and experienced hackers alike, it's useful to have access to the right tools to discover, classify, and then launch customized brute-force attacks against a target. BruteDum does it all from a single framework.

There are many ways to attack a Wi-Fi network. The type of encryption, manufacturer settings, and the number of clients connected all dictate how easy a target is to attack and what method would work best. Wifite2 is a powerful tool that automates Wi-Fi hacking, allowing you to select targets in range and let the script choose the best strategy for each network.

Cracking the password for WPA2 networks has been roughly the same for many years, but a newer attack requires less interaction and info than previous techniques and has the added advantage of being able to target access points with no one connected. The latest attack against the PMKID uses Hashcat to crack WPA passwords and allows hackers to find networks with weak passwords more easily.


In this video you will learn how to complete the "Finish Him" achievement in GTA IV. In order to do that just follow these steps. First you will need to go in a crowded place. You will need to get 10 melee counters in 4 minutes. To complete a counter attack you will have to press the A button when the enemy tries to hit you. After you dodge the attack you will have to press the B button in order to punch him back. Just repeat this process for 10 times and you will successfully get the "Finish...

In these two videos, Matt discusses 1.d4 d5 2.e3 Bf5, preventing White's Stonewall setup by beating White to the d3-h7 diagonal. The only way White can play for an advantage is to play 3.c4 with the goal of an early attack on b7. Some of these positions can also be reached via the Slav Defense.

ARP spoofing is an attack against an Ethernet or Wi-Fi network to get between the router and the target user. In an ARP-spoofing attack, messages meant for the target are sent to the attacker instead, allowing the attacker to spy on, deny service to, or man-in-the-middle a target. One of the most popular tools for performing this attack is Ettercap, which comes preinstalled on Kali Linux.

While Wi-Fi networks can be set up by smart IT people, that doesn't mean the users of the system are similarly tech-savvy. We'll demonstrate how an evil twin attack can steal Wi-Fi passwords by kicking a user off their trusted network while creating a nearly identical fake one. This forces the victim to connect to the fake network and supply the Wi-Fi password to regain internet access.

Welcome back, my fledgling hackers! Over the years, we have examined multiple ways to own, exploit, or compromise a system. On the other hand, we have not spent a lot of time on denial-of-service (DoS) attacks.