If you want to appreciate the value of microbes, look no further than a chunk of cheese. Because cheese roughly traces back to the Neolithic Era, we might say the earliest cheesemakers were the first humans to manipulate microbes—without even knowing it. Now, thanks to microbiologists and the long tradition of cheesemaking, we know a lot more about the microbes that make our favorite types of cheese possible.

Avian flu is making the news again with new human cases in China reported in January. What does "avian flu" mean to you—and how dangerous is it?

"Necessity, not novelty," is a phrase I use often when it comes to HoloLens development. It would be fair to call it my mantra, or mission statement, as I prototype and explore software creation on this new frontier of mixed reality.

Transmitted by a sandfly one-third the size of a mosquito, parasitic Leishmania protozoa are responsible for a flesh-destroying disease that kills an estimated 20,000 people per year. Two new studies offer understanding of how the parasite provides immunity through persistence and why some people suffer more virulent forms of the disease.

As fun as it is to see Fido's face light up when you feed him table scraps, American dogs are getting fat. The good news is that research is homing in on nutritional strategies to boost canine capabilities to maintain a healthy weight.

Lighthouses and signal fires may have been the first social media. Without the ability to share language, a distant light meant "humans here." A new study from the University of California, San Diego, finds that bacteria can also send out a universal sign to attract the attention of their own, and other bacterial species.

A recent pathogen outbreak in Illinois is just one of many outbreaks of an underappreciated, but serious, viral infection passed from rodents to humans. These hantaviruses have been cropping up more frequently in the last decade or so, giving us more reason to clean out our dusty attics, basements, and garages.

Specialized cells in the lining of the gut may provide a key to preventing an infectious brain disease caused by misfolded proteins.

At this point in our series on creating a customized hacking container, you should be able to use Docker to save and retrieve customized instances of Ubuntu from your own machine. Make sure to revisit part one and part two if you need a refresher.

Alphabet's moonshot factory, X (formerly "Google X"), is a secretive place, but it seems that when they are close to graduating a project, then they need to staff it up quickly. Watching for these job ads is one easy way to know they're close to budding off a baby.

True innovation tends to come from the places we least expect as developers. The Microsoft HoloLens is still a very new product, and some of the other headsets are still just ideas, so the rules for mixed reality are not set in stone. That means all the real problems to be solved are yet to come.

When it comes to modifying Android, the single, most powerful tool available is TWRP custom recovery. It's even more capable than simple root access when it comes to changing the look and feel of your software, and you can even use TWRP to root your device in a few simple steps.

An app from the development team at ts-apps has the potential to make your Android device smarter than it's ever been. At first glance, you'd think it's just an ordinary home screen folder—but depending on what you're doing at a given time, the folder can show a completely different set of apps.

Paranoid Android has always been one of the most popular custom ROMs because of the inventive features its developers add to Android. Two of the biggest draws in particular have to be the "Halo" notification bubble, and the "Pie" navigation buttons, which can both fundamentally change the way you interact with your device.

When it comes to modding an Android device, a custom kernel can take you farther than almost anything else. Most offer the ability to overclock your processor for performance gains, change your CPU governor, or even under-volt to increase battery life, among other features.

There are two types of Halloween lovers: Those who like culturally-relevant costumes and serving precious ghost cupcakes, and those who live to freak their friends the hell out in the most disgusting way possible.

A few months ago, LlabTooFeR leaked a full system dump from Google's then-unreleased Pixel and Pixel XL smartphones. That may not seem like a big deal at first glance, but the system dump contained all of the preinstalled apps and services from Google's new flagships—including the much-anticipated Google Assistant.

Passwords are everywhere. We use them to unlock phones, computers, websites, encrypted disks, encrypted files... the list just goes on and on. Savvy users will already have a password manager of some sort that can generate a very strong password on a per site basis. However, these password managers also require a password. Not only that, it has to be something memorable.

Now that Google has announced its new Pixel smartphones, folks who rushed to buy an iPhone 7 might be experiencing a bit of buyer's remorse. The new Pixel and Pixel XL are packed to the brim with cutting-edge features and top-notch hardware, and Google seems to be taking direct aim at the iPhone 7 with its Pixel marketing (and their groan-worthy jokes during the keynote).

While you can't turn art into a formula, the film industry has managed to come stupidly close. While many storytelling principles still stand across mediums, successfully crafting a compelling, immersive narrative in virtual reality requires a brand new rulebook. Through trial, error, and success, writer/director/editor Adam Cosco figured out the right rules to follow (and break) in "KNIVES"—his latest 360-degree short film. The film tells an old-fashioned tale of a woman, Kelsey Frye, strugg...

While it hasn't gotten as much attention as iOS 10, Apple's big 10.12 update to their Mac operating system is finally out for all to enjoy—and you can download it for free from the Mac App Store right now.

There's a lot of great things to be excited about with iOS 10 on your device. You can remove annoying stock apps, search emails better, remember where you parked, and much, much more. Seriously, there's actually more outstanding features in iOS 10 than in Apple's latest iPhone 7 models.

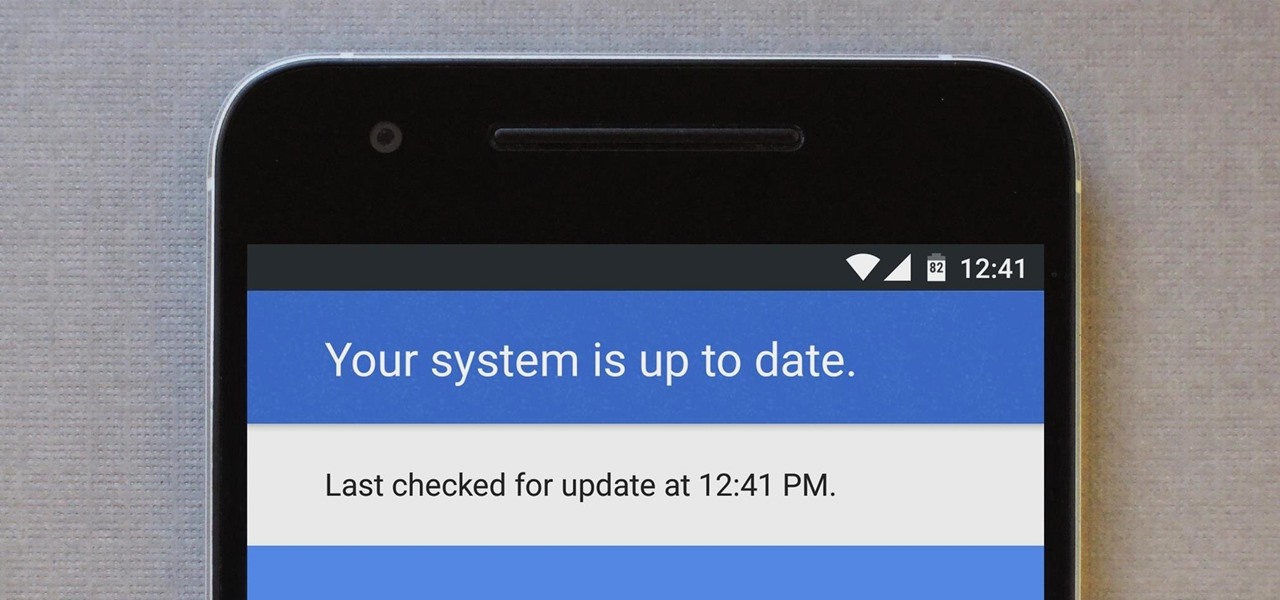
Android 7.0 Nougat has finally arrived—well, technically, it's in the process of arriving on Nexus devices across the globe. Google uses a staged rollout system to prevent excessive server load when issuing Android updates, which means even though Nougat has made its official debut already, you might not get that "Update available" notification for another few weeks.

The reality of tomorrow will not be static. We're here to bring you a daily look into the cutting edge innovations poised to merge the impossible worlds of our imagination with real life. We're NextReality.

When the Samsung Galaxy S7 and S7 Edge came to market in 2016, they were universally praised as being the pinnacle of Android smartphone design, even topping Consumer Reports' smartphone ratings.

Why, for the love of God, do people keep inventing ridiculous devices that make the simplest things more complicated in the name of convenience? This may be a rhetorical question that will forever go unanswered—because these crazy gadgets just keep rolling out, one after the other.

Greetings fellow students! I'm currently reading a book called "Violent Python: A Cookbook for Hackers, Forensic Analysts, Penetration Testers and Security Engineers"

Counter-Strike is one of the most popular first-person shooters of all time, and deservedly so. What originally started out as a third-party Half-Life mod garnered such a cult following that Valve had to hire the developers and purchase the intellectual property to make it an official standalone release.

The Galaxy S7 edge comes with a feature called Edge Apps that lets you quickly launch your favorite apps by swiping in from the edge of your screen. It's a natural and intuitive gesture, and as a result, we've seen a recent influx of apps that look to emulate this feature.

Fresh herbs are a surefire way to enhance a dish, but buying them at the store each time you need them is costly. Luckily, growing your own herbs is a lot easier than it seems: You can even using cuttings from the herbs you already buy to start your own little herb garden.

Ever since the Google Play Store removed its "Designed for tablets" section, it's been a lot harder to find good, tablet-optimized Android apps. Not that it was all that great to begin with considering that they used to list apps like Facebook and Twitter, which only have oversized phone UIs on tablets, not actual customized UIs.

Nothing about living in a snowy climate is easy, but life with a snowy, frozen car doesn't have to be the worst part of your day. With a few clever hacks and some anti-weather tactics, you can fight off frozen windshields, icy locks, and even stubborn car doors, while keeping your car running smooth all winter. 1. Deice Your Car Locks in Seconds

For many people, the two main advantages of buying a Nexus device are prompt updates and the ability to root without much hassle. But in a cruel twist of fate, these two features are almost mutually exclusive, since OTA updates will refuse to run on rooted devices.

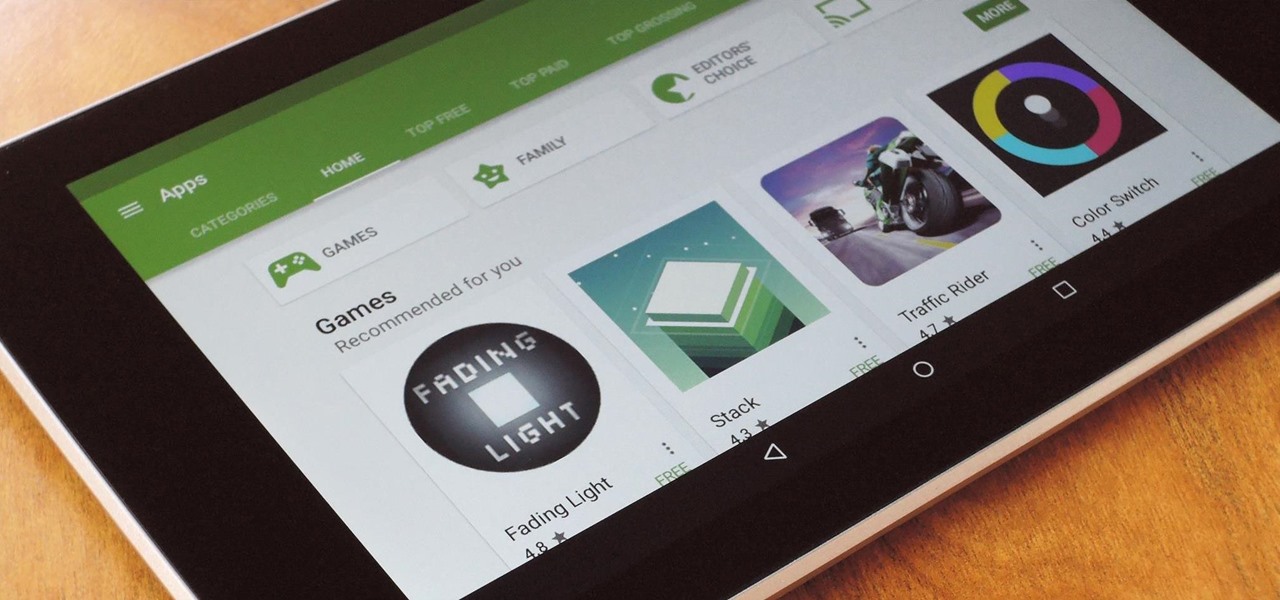
The Google Play Store hosts the largest collection of mobile apps on the planet, and it's the default app store for almost all Android devices. Ironically, though, while Google made its name with a powerful search engine, it can sometimes be difficult to find what you're looking for on the Google Play Store.

Macs are generally highly power efficient due to, in part, the optimized sleeping schedule with OS X. Yet in certain scenarios, you might not want your Mac to go to sleep: downloading a huge file, reading a book, reviewing a spreadsheet, analyzing some content on the screen... the list goes on. To resolve this, you can go to System Preferences and mess with the settings, but this can be an annoying process if you need to do it often.

Welcome back, my tenderfoot hackers! Web apps are often the best vector to an organization's server/database, an entry point to their entire internal network. By definition, the web app is designed to take an input from the user and send that input back to the server or database. In this way, the attacker can send their malicious input back to the servers and network if the web app is not properly secured.

If you're experiencing issues with an app or custom ROM and would like to report your problem to the developer, there's no better way to do it than by capturing a logcat. Android keeps track of all the commands that have been executed by various apps and services, which means that when something goes wrong, the error is clearly shown in this so-called logcat.

Managing hard drives in Linux is crucial to understanding your system and its operation as well as understanding the system you are exploiting or conducting a forensic analysis on. Linux has numerous commands that can provide us with information, control, and management of hard drives, and in this tutorial, we will examine a number of the most important ones.

In previous tutorials we have encountered these things called pointers and addresses but we still don't know what they really are. Let's learn a bit more to clear things up.

Welcome to another C tutorial. We will be looking at arrays, discussing what they are, when they are used and their special relationship with the char variable. Let's begin.