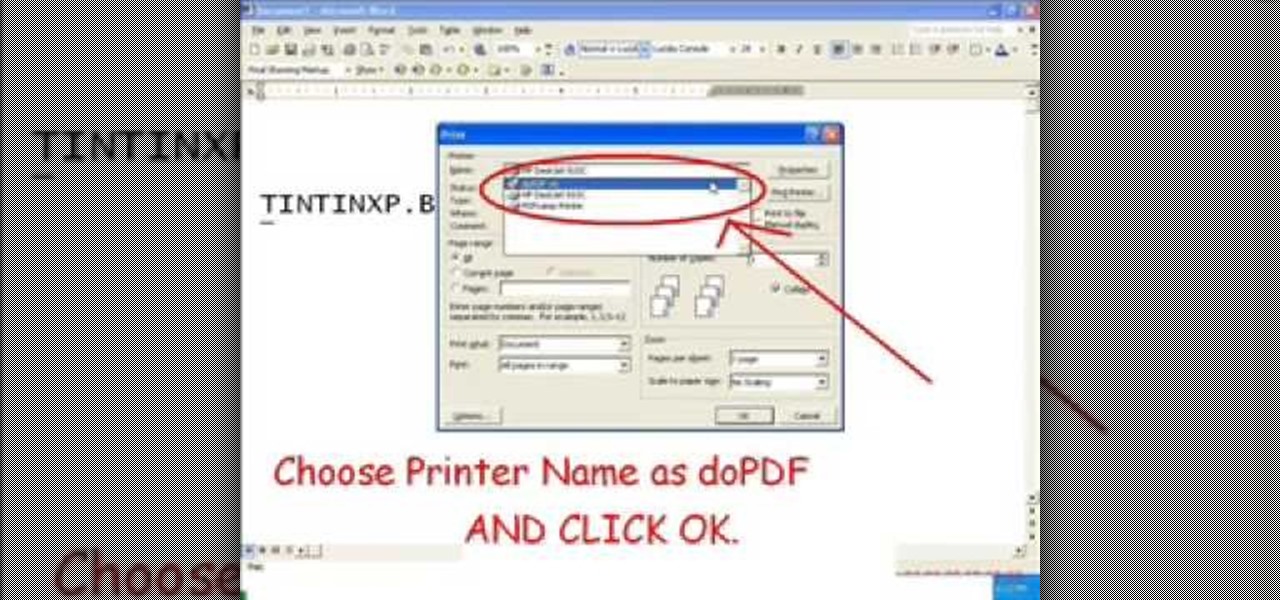
In this video tutorial, viewers learn how to convert word documents to PDF format. This task is very easy, simple and fast to do. Users will need to download a program from this site: DoPDF. Once downloaded and installed, open the program and open the file that you want to convert. Then click on File and select Print. Choose the printer name as "doPDF" and click OK. When a window pops up, select the location where you want to save the file. This video will benefit those viewers who have a tex...

The video is about making a ISO file or a disc.To enable this you must have ISO installed on your system.The video begins by opening the Image burn setup wizard file.Once you have opened it , keep clicking next until you are finished with the installation. Then you have to insert a blank CD into the drive. Once you have done that a window will pop open displaying options for the CD.Click on the mode option in the window and select ec mode and then click on the first option displayed which is ...

In this video tutorial, viewers learn how to fix an iPod with corrupted files on a Windows PC. To fix the corrupted files on an iPod, users will be resetting their iPod. Begin by holding the center and Menu button for about 10 seconds until the screen on the iPod turns black. Then immediately hold the center and Play/Pause button until a check mark appears on the screen. To prevent an iPod from getting corrupted files, do not disconnect an iPod when it is connected to the computer. This video...

In this how to video, you will learn how to convert an AVI file to a DVD with Xilisoft. First, you will need to download the Xilisoft AVI to DVD Converter. Next, click the add video files icon on the left and select the AVI file that you want to convert. Select it and click open. Next, change the destination so that it is saved as an ISO file. Enter the new name of the file and click save. Click start burn on the right side. Now your AVI will be converted to DVD format. Once it is finished, y...
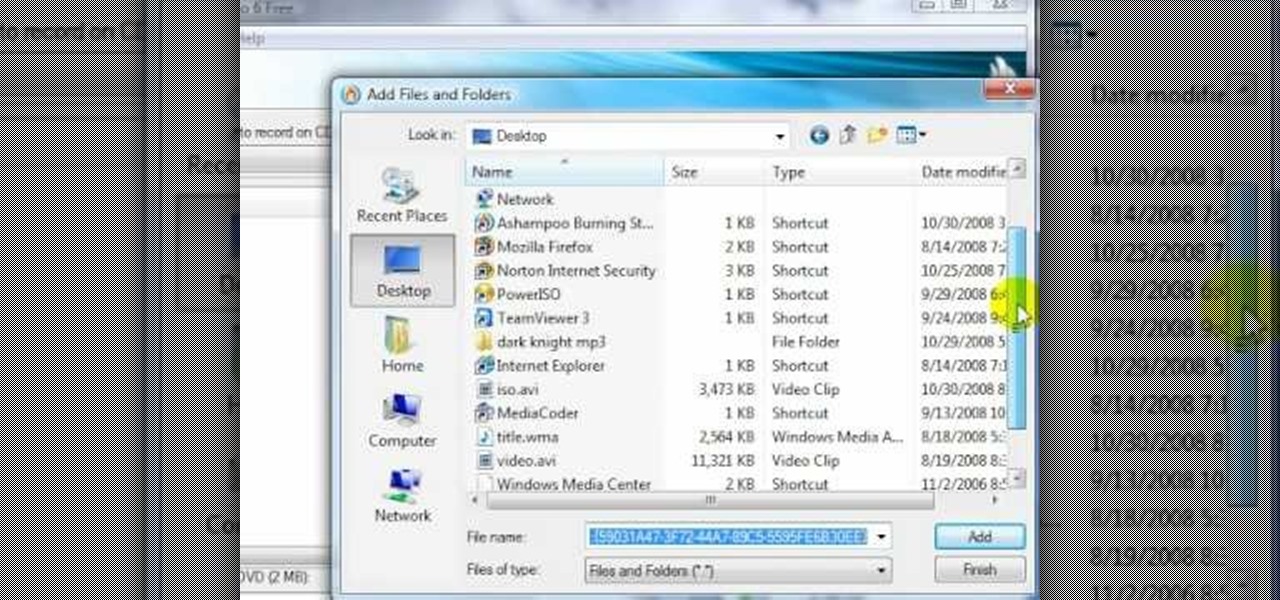
In this video tutorial, viewers learn how to create an ISO image. Users will need to download the program, Ashampoo Burning Studio 6. Begin by going to the Google search engine and search for the program. Select the result from download.com. Click on Download Now and save the file. Double-click on the file and follow the instructions to install it. Then open the program and select Create/Burn Disc Images. Select the type of disc image that you would like. Then click on Add and select the file...
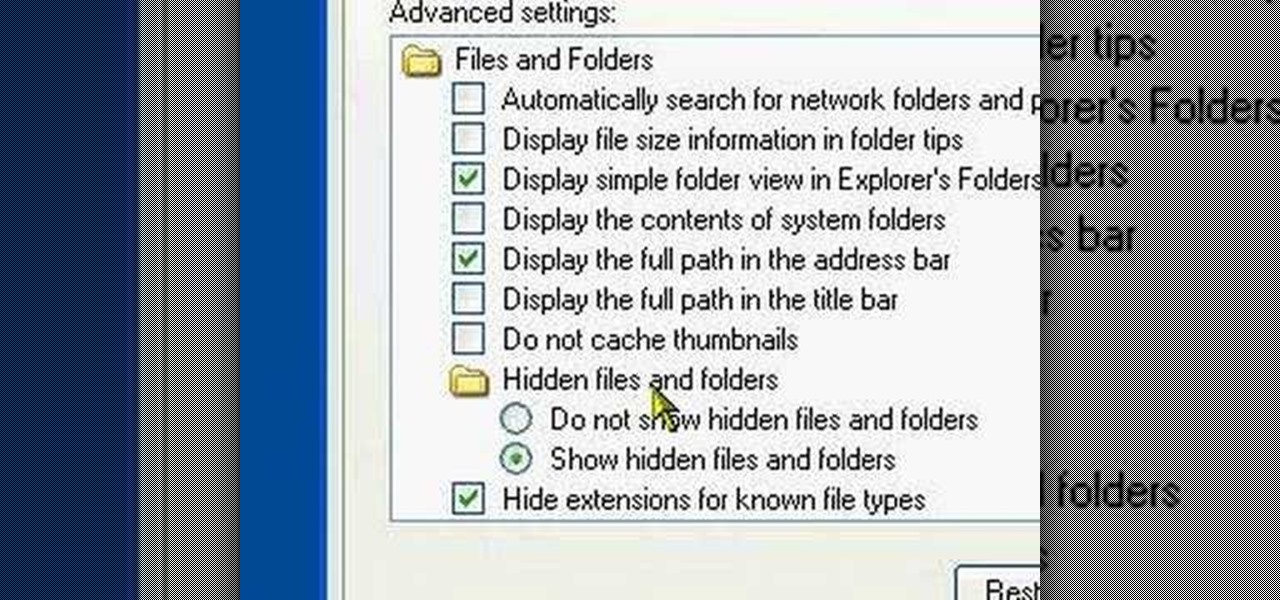
In this video tutorial, viewers learn how to view hidden files and folders in a Microsoft Windows XP or Vista computer. Begin by clicking on the Start menu and select Control Panel. Double-click on Folder Options and click on the View tab of the Folder Options window. Under Hidden files and folders, check the option that reads, Show hidden files and folders. Then click on Apply and OK. This video will benefit those viewers who use a Windows XP or Vista computer, and would like to learn how to...

Just because you are using Linux, doesn't mean you have to be cut off from file sharing with those using a regular Windows PC. In this tutorial, learn how to share files between Ubuntu and Windows using a Samba local network. Samba is simple to use and can be obtained through your Synaptic package manager.

In this video tutorial, viewers learn how to unzip a file in a Microsoft Windows 7 computer. Begin by going to a website that you would like to download the file from. Right-click the link and select Save Link As. Selection the Desktop as the save destination and click Save. On the desktop, right-click the on the zipped file and click Extract All. Now click Extract. A new folder with the same folder name is now created. Inside the folder is the desired file. This video will benefit those view...

If you do not like the QuickTime video but would still like to view your .mov video files, follow these simple instructions to have your file play in any media player.

Changing computers or switching to a different type of web browser? If you have been using Firefox for a while, you most likely have some good bookmarks saved. Check out this tutorial and learn how to export your bookmarks from your old browser and take them along with you, wherever you go.

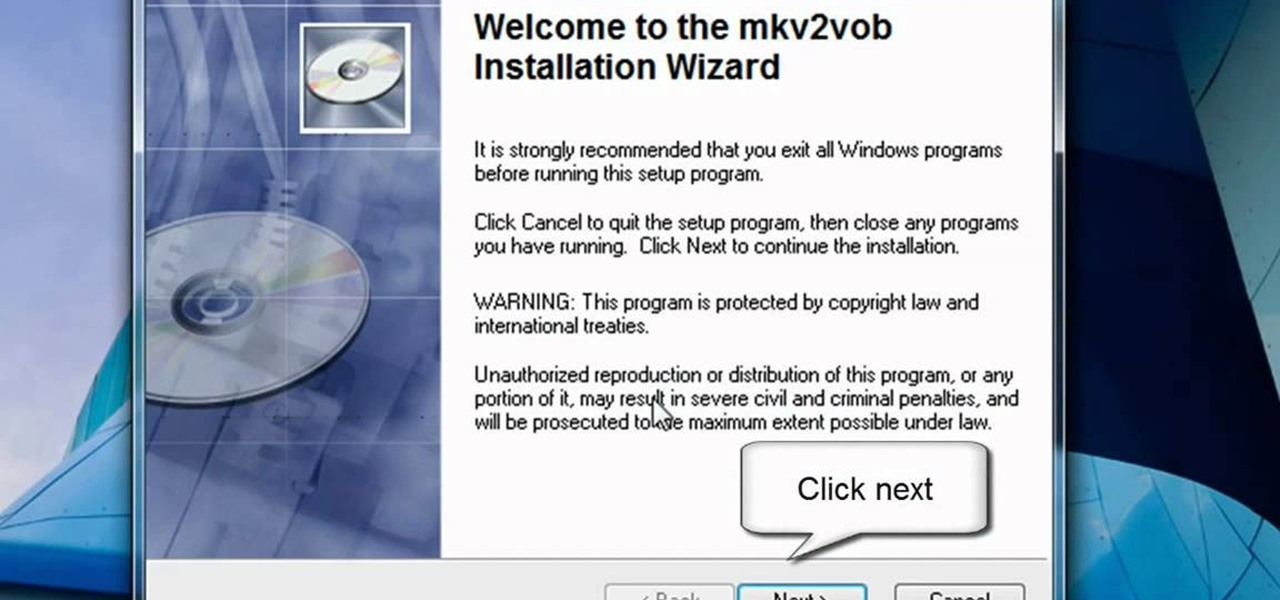
In this video tutorial, viewers learn how to play MKV videos on the PS3 using the MKV2VOB software. Begin by downloading the MKV2VOB programs from the link in the video description. Once downloaded, install it on your computer. Now open the program. Go the Configuration tab and change the setting to the same as the video. Then click on the Add File tab and select Browse under Source File. Find your MKV file and select Open. Then under Destination Directory, select where you want your file to ...

In this video the instructor shows how to choose options on a batch file. In a batch file if you write the command '@ echo off', the person running the batch file cannot see the commands being executed. You can use the 'if' condition to make the program execute either of two commands depending on the condition. While writing the if statements make sure that there is space between the 'if' and the '%' sign. If you write 'shutdown -t 30' command in your batch file, then the batch program when r...

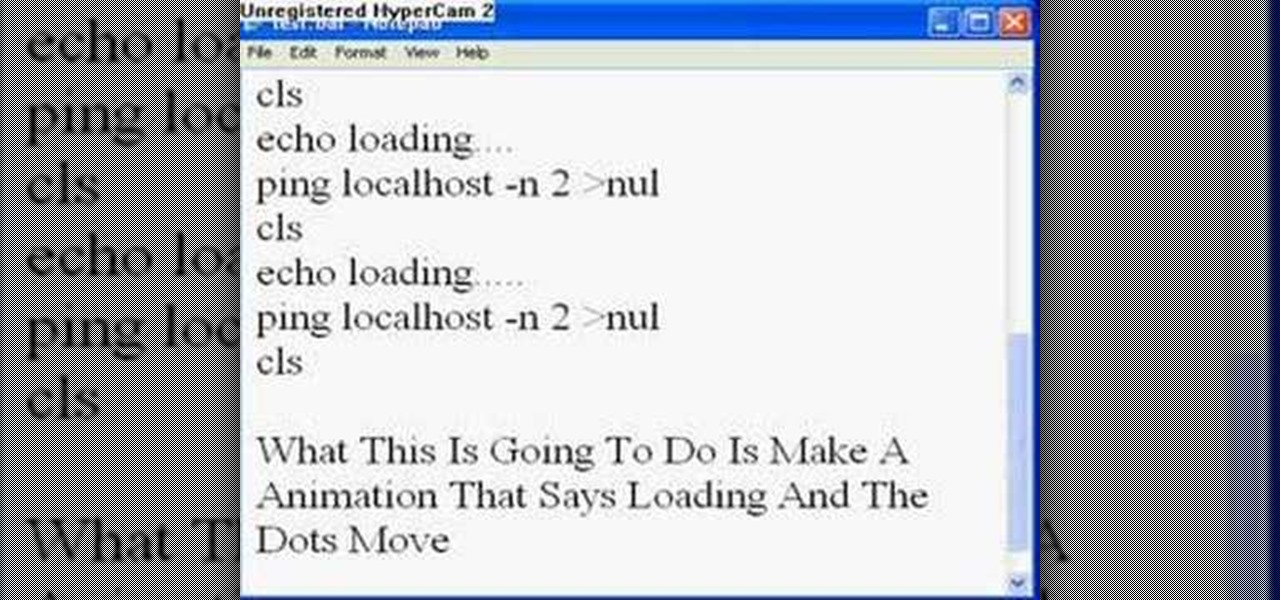
CtrlFormula teaches you how to make an animation with a batch file. Before you begin you must know that sending batch files over the internet is risky, so keep that in mind. You create a new .txt file and type in: @echo off. Hit Enter twice and type in: echo loading. Then hit Enter once and type: ping localhost -n 2 >null. Hit Enter once and type in: cls. Copy and paste this structure three times. For each loading you see you have to add another dot at the end, so the animation will slowly go...

This video teaches you how to open .zip files with a just few easy steps. First, you need to download a program Winrar. The download can be found at http://www.rarlab.com/download.html and the download should start immediately. Once the download is complete, open the program.

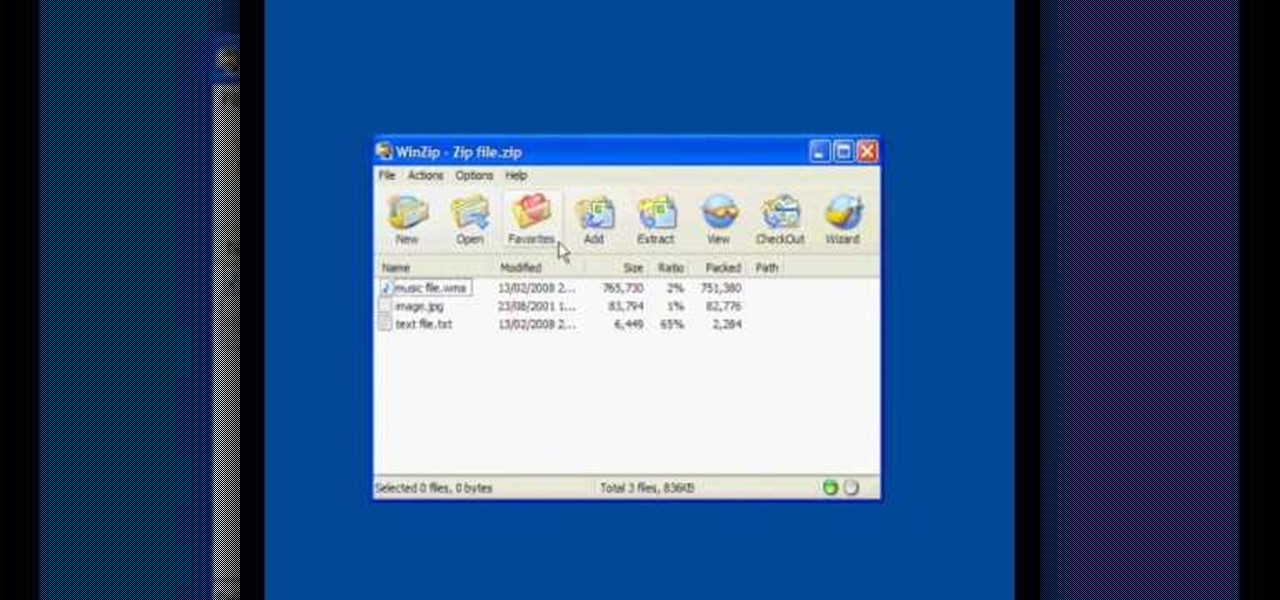
Do you have a hard time extracting/unzipping files using WinZip? If you follow along we will be shown a couple simple steps on how to unzip files using WinZip.

This is a tutorial video demonstrating how to make your own gameboot for PSP. The video recommends starting with part 1 and proceeding through to part 2, 3, and 4 in order. It is important to look at the video description for vital information and links. A cintro is a custom intro created to start first thing as the game boots up. In the first step you will need a video in mp4 format to use as the intro. Next install and save. The converted file will show up in the same folder of the video. O...

Stan shows an easy way to see and clean the files that are hogging hard drive space in the computer using a free software called "windirtstat". Now enter the following address in the web browser "windirtstat.info" and scroll down the page until you get the downloading and installing section. Click on the link "windirtstat1.1.2Setup(Ansi&Unicode)" which will be right after the "for all flavors of windows" this will direct you to "SOURCEFORGE.NET" download creations. This will ask you to save t...

Have some files you don’t want anyone to see? Or maybe it’s just been a while since you’ve emptied your trash bin. The trash bin function is not a permanent delete but you can erase files off your Mac with this tutorial.

This video tutorial is all about recovering the deleted files in Windows Vista. If you are using the Windows Vista and you have unknowingly deleted a file and emptied the recycle bin, then you can recover it. This can be done by using the Shadow Explorer. Shadow Explorer is a Vista program that accesses the Vista Volume Shadow Copy Service. In Vista, the shadow copy service is turned on by default. It creates backups of files on a regular basis. Shadow Explorer provides access to these backup...

Check out this cool hack from The Emo Lab. This video tutorial will show you how to do a few Windows registry hacks!

This software tutorial will show you how to email GarageBand files. Learn how to zip the GarageBand file and create an archive so you can email your GarageBand music files.

The built-in Files app on your iPhone has only gotten better since it was introduced in iOS 11, with small improvements after each new iOS version. You can manage files on your internal storage as well as in iCloud Drive, but one of the best features is being able to manage media and documents from all of your cloud storage accounts in one place.

Getting files from an Android device to a Mac or iOS device is not always easy or convenient, and the same goes for transferring content from a Mac or iOS device to an Android device. But we're here to tell you there is a better way than using USB cables, email, and cloud storage, and it gives you the look and feel of AirDrop.

OnePlus phones are easy to root, but that also means they're easy to brick if you get trigger happy with your superuser privileges. If you find yourself in this situation, you'll quickly realize the OnePlus firmware download page doesn't provide files you can flash in Fastboot mode.

When you export an image from the Photos app in macOS, you may not be getting the whole deal. In the export menu, you need to select either JPEG, TIFF, or PNG, and if you don't make any adjustments to the quality settings, it'll likely be compressed. If you need the original full-resolution file or want to get the video that's attached to a Live Photo, there's a simple way to do it.

The week in AR business news started out with a bang with two bombshell reports that cast a shadow on the AR industry as a whole.

It is said that the best way to avoid detection when hacking is to leave no trace, and often that means not touching the filesystem at all. But realistically, in most cases, it's impossible not to interact with the filesystem in one way or another. The next best thing to do to throw off any investigators is to change the file attributes to hide activity. We can do this with Metasploit's Timestomp.

Directory traversal, or path traversal, is an HTTP attack which allows attackers to access restricted directories by using the ../ characters to backtrack into files or directories outside the root folder. If a web app is vulnerable to this, an attacker can potentially access restricted files that contain info about all registered users on the system, their permissions, and encrypted passwords.

When we reviewed the best file managers on Android, MiXplorer easily topped our list with its abundance of features, including tabbed browsing, support for up to 19 different cloud services, file and folder encryption, and much more. The only major complaint we had was the fact it couldn't be installed from the Play Store, but now, that is no longer the case.

A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website defacement to full-on code execution. For this reason, RFI can be a promising path to obtaining a shell.

It's not uncommon for hackers to attempt to move laterally between devices in proximity of a compromised device to maintain a prolonged presence in the network. Malware utilizing USB flash sticks to self-replicate and compromise air-gapped machines isn't a new concept.

Think back to when you last wanted to transfer some music or videos to your friend's smartphone and how difficult and slow it was. As powerful as our phones are, the default file sharing options are limited. There are, fortunately, some better options which make moving files easy, secure, and painless.

In most macOS hacks, a non-root terminal is used to create a backdoor into the device. A lot of damage can be done as a low-privileged user, but it has its limitations. Think twice before granting a file permission to execute — an attacker might be able to convert your harmless scripts into persistent root backdoors.

With the macOS stager created and the attacker's system hosting the Empire listener, the malicious AppleScript can be designed and disguised to appear as a legitimate PDF using a few Unicode and icon manipulation tricks.

Deleted bank statements and private photos are still within an attacker's grasp, so don't think that emptying your recycling bin is enough to keep your files from coming back to life. It's possible for a hacker to recover compromising files and images from a backdoored computer completely without the victim's knowledge.

The Galaxy S9 was announced February 25, and it's jam-packed with features like AR Emojis and and a Dual Aperture camera. You really love the cut of its jib, but maybe you don't have the means to get your hands on one. Well now, you can get the Galaxy S9's notification sounds and ringtones, to help you feel like you own one.

Apple's codec for photos and videos in iOS 11, HEVC (High-Efficiency Video Coding), as well as the container, HEIF (High-Efficiency Image File Format), result in a reduction in size for pictures and movies without sacrificing quality. Seems like a win-win situation, but Windows-users can't open the .heic extension that these files use. In order to open HEIC files on a Microsoft Windows PC, you'll have to turn to third-party apps and tools. One of these tools, CopyTrans HEIC for Windows, essen...

File inclusion can allow an attacker to view files on a remote host they shouldn't be able to see, and it can even allow the attacker to run code on a target.

Any internet user will need to download files eventually, and most simply have faith that what they are downloading is trustworthy. This doesn't give much clarity into the contents of the file, but if the file's author published the original checksum, comparing it to the SHA-256 hash of the downloaded file can ensure nothing was tampered with.

An attacker with shell access to a Linux server can manipulate, or perhaps even ruin, anything they have access to. While many more subtle attacks could provide significant value to a hacker, most attacks also leave traces. These traces, of course, can also be manipulated and avoided through methods such as shell scripting.