Working in Photoshop and not sure how to save your files? What ARE all those extensions and what exactly are the differences. Well, this video breaks it down so you'll know just how to save your precious work.
File collaboration is one of the best integration features between Office 2003/Office 2007 and SharePoint. These task panes allow you to access and modify content in a SharePoint site from within Office without having to navigate to the site using your browser. The feature is available in the following Office 2003 and Office 2007 applications: Word, Excel, Microsoft Project, OneNote, PowerPoint, and Visio.

Is your hard drive filled to the brim but your not sure which files or file is hogging up all the space? Well check out jDisk for a visual representation of those space hogs.
How does Lightroom handle the process of going between itself and Photoshop? Where are the PSD files and what do we do with them? Check out this video and learn more about psds files and working with them in Lightroom.

Watch this video to learn an easy way to FTP (file transfer protocol) files using the Safari browser.

I show you a great way to take your beautiful .avi files and turn them into much smaller files that are great quality as well. And you don't have to buy extra software to do it!

Are you tired of having a bunch of files on your computer that you cannot get rid of? Find out how to use Windows notepad to remove unwanted files from your pc.

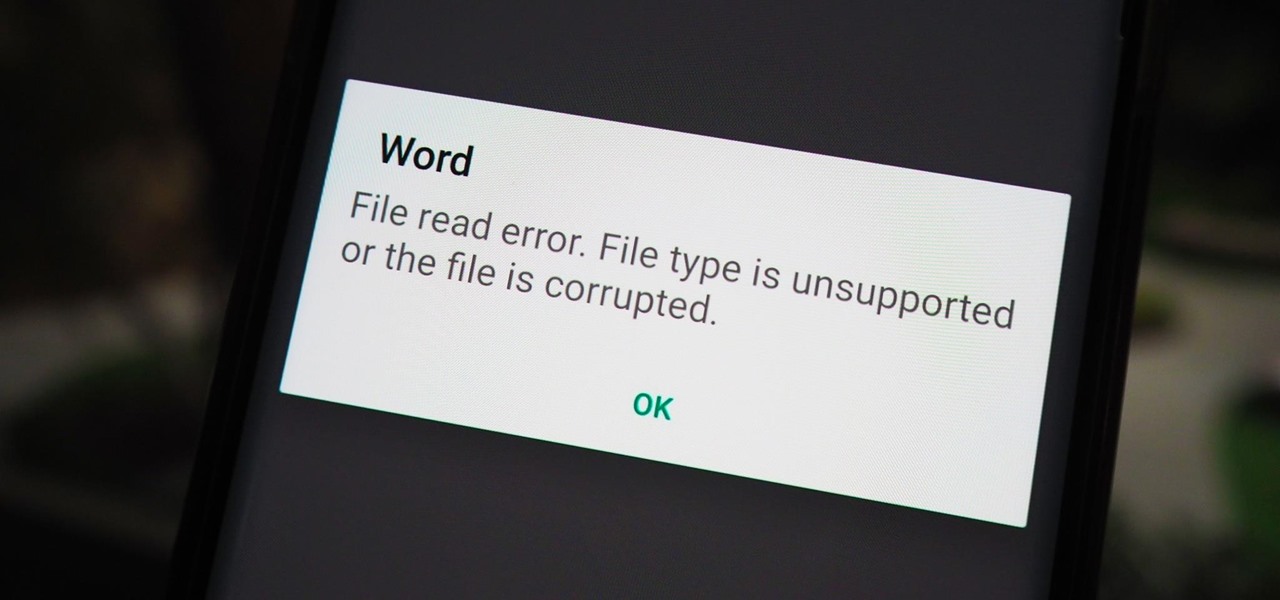
Have you ever seen a DOCX file, and don't know how to open it? Or you have a DOCX file, and want to convert it? Watch Chris' video to find out more about DOCX now.

If you need to share something online but don't want your personal information attached to the file, use an anonymous file hosting site. By uploading files anonymously, you keep your IP address safe and won't need to create any kind of account that could provide further logging. You can do this in a web browser, but it's much easier to do using a shortcut on your iPhone.

You have an assignment due, whether it's homework for school or a project for work, but you've only got a few hours left. There's no way you're going to finish in time and do a good job, and you don't want to turn in anything incomplete or half-assed. While it may seem you're out of luck, there's a simple way to buy yourself more time.

If you have an Android device that Netflix does not support, you can check the Play Store and it simply won't be there. But just because you're unable to download it through official means doesn't mean you have to live without Netflix since there's a way you can sideload it manually.

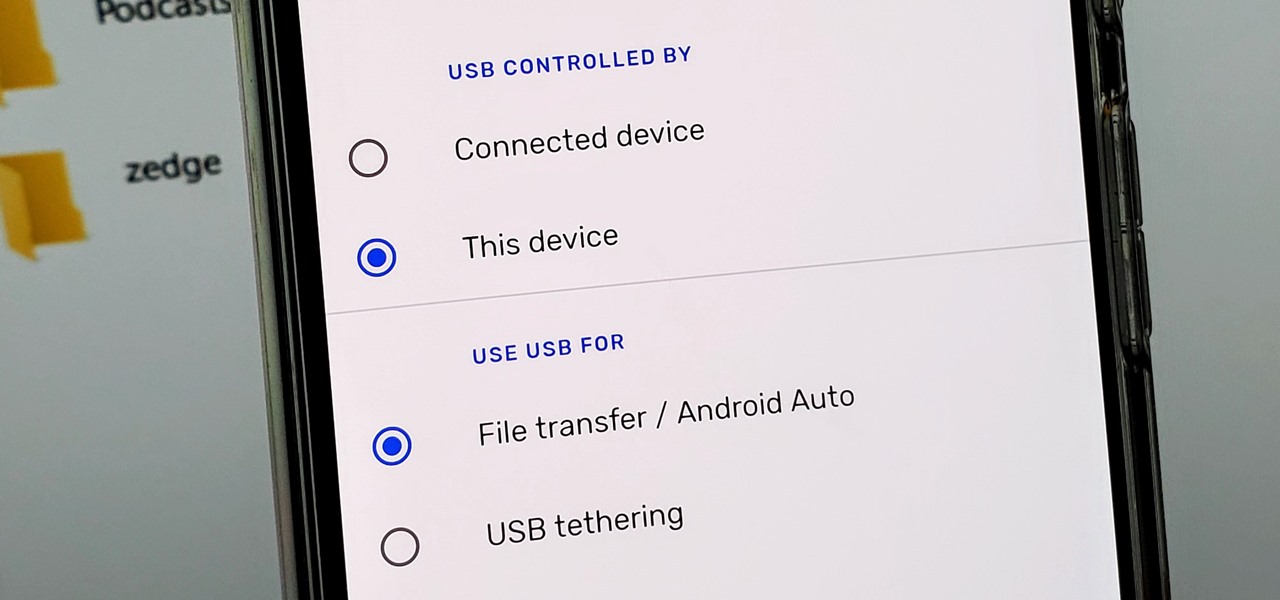
Back in the earlier days of Android, you were able to connect your phone to a computer, and it would mount automatically. This meant once the USB connection was made, your internal storage would pop up on the computer and you could go about your business. But recent versions of Android changed that to help increase security.

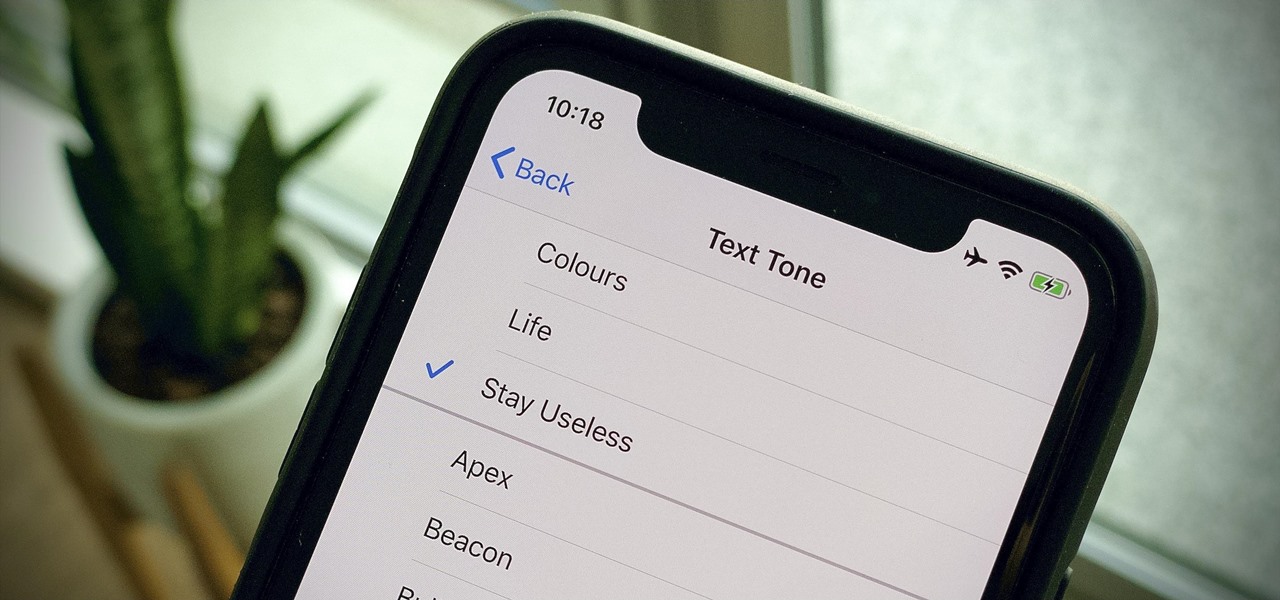
Apple hasn't refreshed its text tones on iPhones since iOS 7. That's six years of the same sounds. And while text tones like Bamboo and Hello have undoubtedly aged like fine wine, that's still too long to live with the same old sounds day after day. Let's take matters into our own hands — let's make our own text tones, right in Music on macOS 10.15 Catalina.

Your phone is loaded with contacts you've collected over the years. They're an asset, and you should use your library of connections outside the confines of your mobile device. Luckily, your Pixel uses a standardized medium to store contacts that can be used by the likes of LinkedIn, Outlook, Hubspot, iCloud, and more.

The Files app was first introduced to the iPhone with the release of iOS 11. In the two years since its unveiling, we've enjoyed a more desktop-class experience since there's finally a decent file manager for mobile devices. That said, there was always one major issue with the Files app, an issue iOS 13 solves for good.

TWRP is a name many are familiar with since it allows your Android device to install any custom file of your choosing. You can create a NANDroid backup to keep your data safe or even use Magisk to achieve full root access. In fact, TWRP is often seen as the gateway to modding your system for creating a unique user experience.

There once was a time in the Android rooting scene where we couldn't rely on using a custom recovery for all of our modding needs. Manual file flashing was very popular in the early days of Android before custom recoveries started taking over. With the rise of TWRP, it seemed like there was almost no need for manual file flashers; however, they appear to be making a welcomed return in a big way.

The newest version of macOS has arrived. While everyone's mind is being blown by Mojave's groundbreaking new Dark Mode, we'll be taking advantage of its insecure file permissions to establish a persistent backdoor with a self-destructing payload that leaves little evidence for forensics.

It's important to know who you're dealing with after hacking your target's MacBook. Getting remote access is simple, but covertly gathering information about the user and their system can be a challenge.

As penetration testers, we sometimes need to securely store customer data for prolonged periods. Bruteforce-resistant, vault-like containers can be created with just a few commands to protect ourselves from physical attacks and unintended data disclosures.

With all the web applications out on the internet today, and especially the ones built and configured by novices, it's easy to find vulnerabilities. Some are more perilous than others, but the consequences of even the slightest breach can be tremendous in the hands of a skilled hacker. Directory traversal is a relatively simple attack but can be used to expose sensitive information on a server.

Over the past month, we've spent significant time covering Samsung's Oreo Beta program, and the detailed list of features in Oreo is extensive for the Galaxy S8 and S8+. Many of you were upset when the Galaxy Note 8 was left out of the official Oreo beta program entirely, but we found a method to install a beta Oreo build right now on the unlocked and US variants if you'd like to give it a try.

Despite concerns with SafetyNet, Google actually cares about root. Every phone they sell has an unlockable bootloader, so you can toggle a setting and send a Fastboot command, then start flashing custom firmware right away. The Pixel 2 and Pixel 2 XL continue this tradition, and now they have an official root method.

Steganography is the art of hiding information in plain sight, and in this tutorial, I'll show you how to use Steghide — a very simple command line tool to do just that. In addition, I'll go over a bit of conceptual background to help you understand what's going on behind the scenes. This is a tool that's simple, configurable, and only takes a few seconds to hide information in many file types.

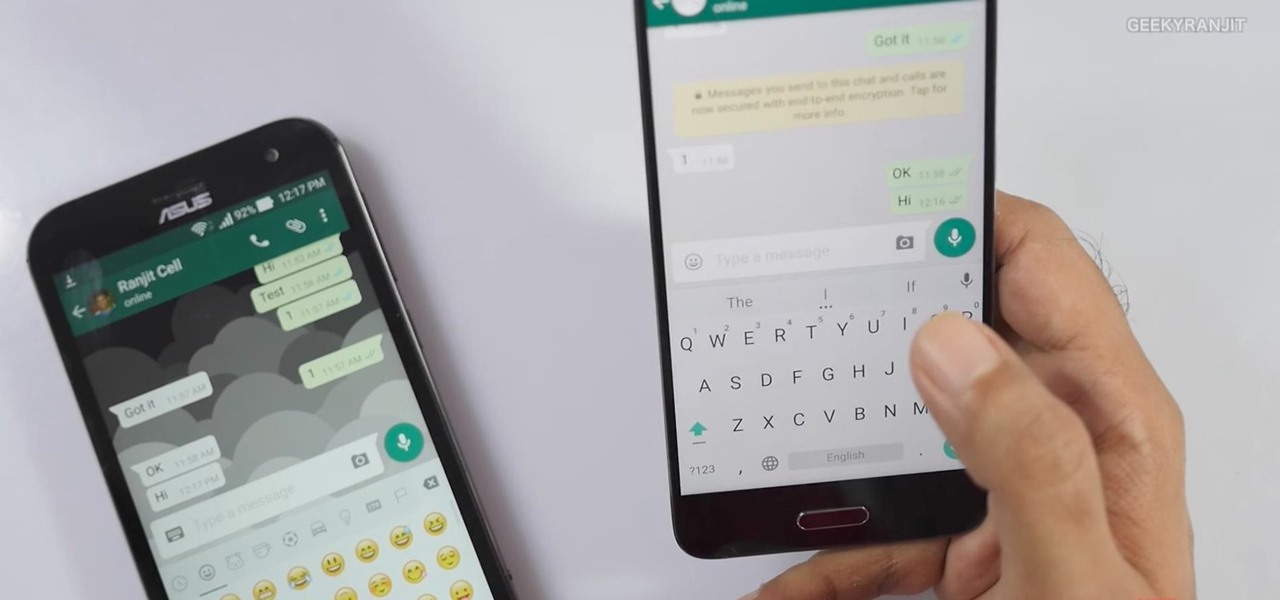
Cell phones have advanced rapidly since their inception. However, one frustrating aspect of our handheld computers is that we sometimes expect more than they can handle. We want smartphones to do all our PCs can do, but in many cases, that just isn't possible; especially when that comes to viewing and sending certain file types. WhatsApp is taking steps to bridge that gap now, by allowing users to send whatever kind of file they want, with one or two restrictions ...

Sometimes you need a password to gain access to an older running Windows system. Maybe it's a machine in your basement you forgot about or a locked machine that belonged to a disgruntled employee. Maybe you just want to try out your pentesting skills.

Backdoors are convenient to leave behind once you've already found a way into a server, and they can come in handy for a variety of reasons. They're good for developers who want a quick way into machines they're working on, or for systems administrators who want similar access. Of course, backdoors are also a hacker's best friend, and can be added in a variety of ways. One good tool for doing this is Weevely, which uses a snippet of PHP code.

How is it goin', fellow 1337 haXX0rZ! dtm here with another article, this time, we'll be looking at infecting PE files, executables in particular for this write-up. Obviously some prerequisite knowledge will be needed since this isn't really newbie-friendly. If you are still a beginner, fear not, it might still be interesting to read! Hopefully!

Welcome back, my budding hackers! In this series, I have been trying to familiarize you with the many features of the world's best framework for exploitation, hacking, and pentesting, Metasploit. There are so many features, and techniques for using those features, that few pentesters/hackers are aware of all of them.

This tutorial was written with Windows 7 in mind, but the principle applies to all versions starting from 7.

Hello partners, first of all I would like to thank all those who have sent me positive feedback about my posts, to say that I'm always willing to learn and teach. I'm also open to answer the appropriate questions.
This is for those using Kali Linux 2.0 that need to edit the CRDA values to get the increase in Txpower

Hello, everyone! If you haven't read the recent announcement on the official release of the Null Byte suite, I suggest you do so. This is going to be a quick tutorial on how to download and install the suite so you can see our communities genius. So, let's get started!

Not many people use their phone exclusively for making calls or sending messages today. If you're an Android user, the chances are high that you're using your phone or tablet for work-related activities. However, the basic set of apps and services your device was shipped with won't satisfy most users. The good thing is that Google Play Store has a nice selection of productivity apps for every task. Below you'll find a list of apps that will help you gradually optimize and organize your digita...

Microsoft's Windows 10 has proven to be a solid release by Microsoft, with faster adoption rates than its predecessor builds. The seamless integration of cloud services and tweaks both major and minor make using Windows easier than ever now. And it's almost enough to forget you ever used Windows Vista... almost.

Welcome back, my budding hackers! In this series, we are trying to understand how AV software works so that we can learn to evade it. To that end, we are working with the open-source AV software, ClamAV. I had previously introduced ClamAV in Part 2 of this series. If you have not installed it yet, go back to that and install it.

Android has a single text file named build.prop that determines tons of various system-wide settings on your device. You need root access to edit this file, since it's stored on the system partition—but the various lines of codes it contains are actually fairly easy to interpret and modify.

Hello fellows nullbyters, first of i will start saying that im addicted to this community, i feel the challenge growing up so fast, all the newbies, amateurs,advanced and professionals hackers around trying their best to help the community, badly but we got some script-kids too but anyway, today we are going to learn how to install and use clanAV in kali linux.. INTRODUCTION

Android Beam is one of those features that makes you look at technology in awe, wondering how exactly something like that works.

You always wanted to make an undetected payload and make it look legit, Well this is what this tutorial is about, You're going to learn how to backdoor any (Unfortunately only 32-Bit) software, Let's get into it