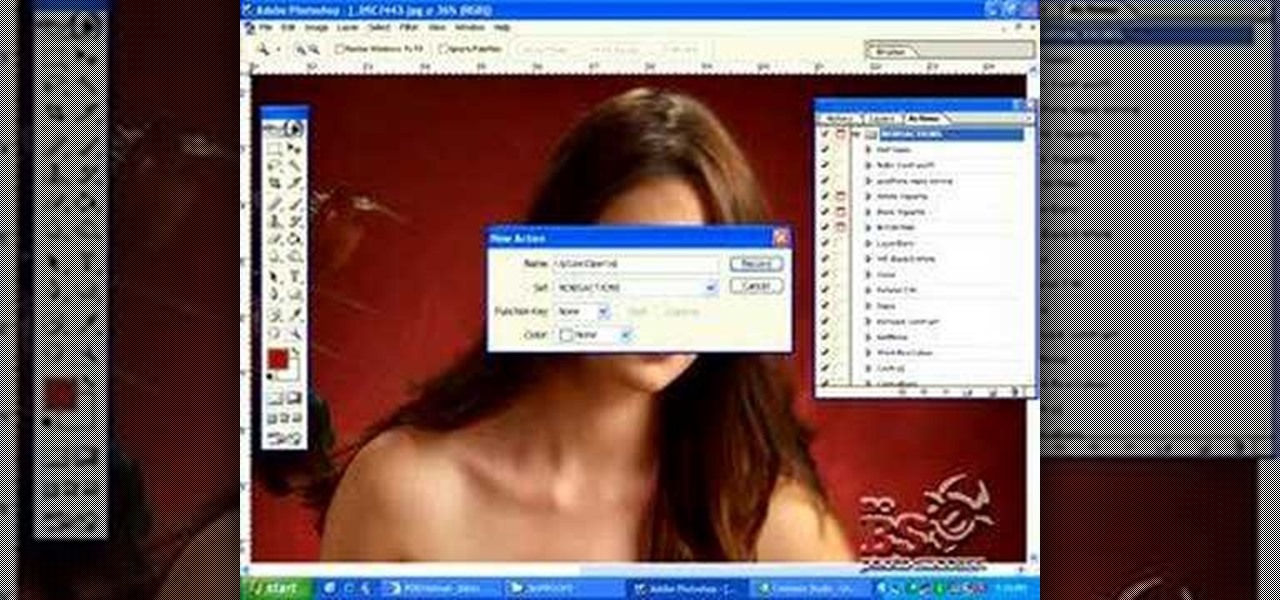
This video demonstrates the steps to restore your iPhone or iPod Touch to original factory settings. This is a way to undo or repair any damage to your phone caused by downloading unauthorized files or corrupt files. Be aware that this will delete all the files that are on your device including music, pictures, videos and contacts, so use this method when all others fail. First connect the device to a computer via USB and select the device in iTunes as shown. Go to the device's information pa...
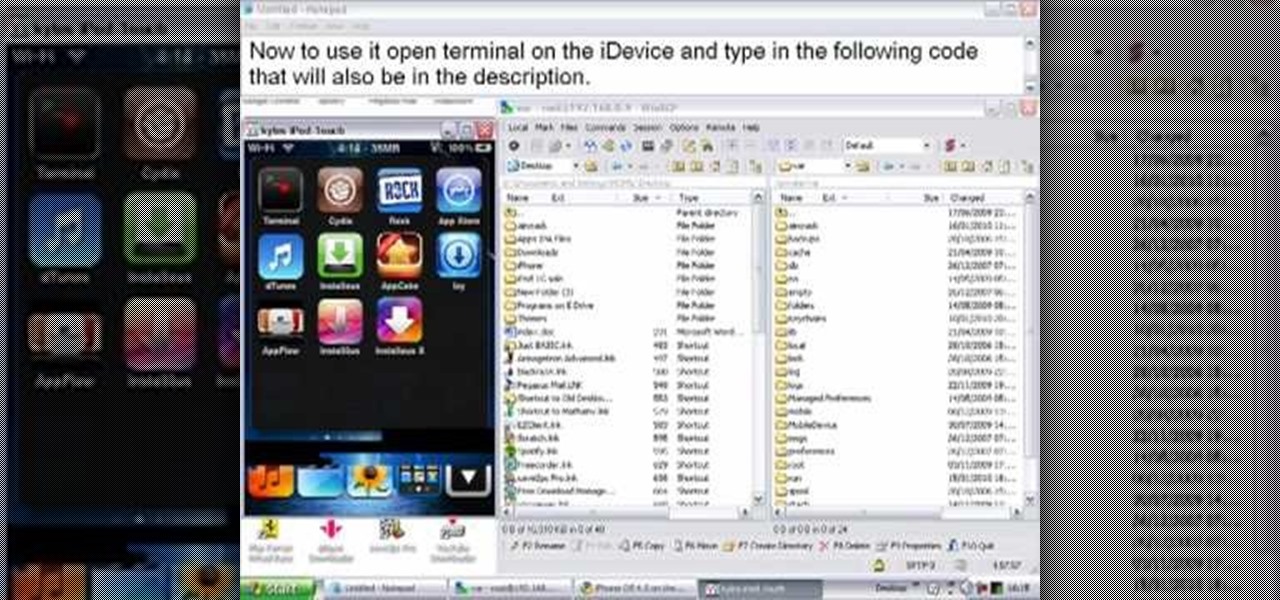
Learn how to install Aircrack on your iPhone to hack into almost any WiFi network. First download Aircrack from iHackMyi, then follow these steps:
The Wedge ROP is a render output driver, which can be used to change variables on the fly while rendering. This can be very useful when simulating, in that you can test out different parameters to see the different results. It's a relatively new feature in Houdini 9.5.

Check out these tips on the Adobe Bridge Center. Not only does the Bridge have excellent features for file browsing and file organization, but it also has the central area, consider it the hub, where you will find features that will further streamline your workflow. In this video tutorial, learn how to use the Adobe Bridge Center, which is a default favorite in the Favorites pane.
Here, see some tips on the collections and smart collections in the Adobe Bridge. Bridge has a lot to offer and is a great organization tool. Collections and smart collections are great workflow features available to you. In this video tutorial, learn about organizing your files without messing up your folder structure and automatically bringing files in that you want based on your settings you assign to that collection. Check them out and learn a great new feature of Adobe Bridge CS4.

Is your hatchet in need of a quick tuning? Doesn't quite get the job done anymore? It's time to sharpen it. This also applies to sharpening an axe.

New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to download files from FTP with Terminal on Ubuntu Linux.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

This software tutorial is an introduction to the tools found in pyro Audio Creator. Learn how to use pyro Audio Creator to manage your audio files by learning how to navigate the user interface and learn what each tool in pyro Audio Creator does.

Need to get songs on your computer into MP3 format so you can play them and store them more easily? Have too many songs to do them one at a time? This music editor software tutorial shows you how to batch convert WAV files to MP3 files using Music Morpher Gold. Put all your WMV songs in a Music Morpher Gold playlist then batch convert them to MP3 format all at once! This MMG tutorial shows you how.

Watch this software tutorial video to learn how to use the Quick Look feature on Mac OS X Leopard to preview files very quickly. Mac OS X Leopard's Quick Look feature will be easy to use after you've watched this how-to video.

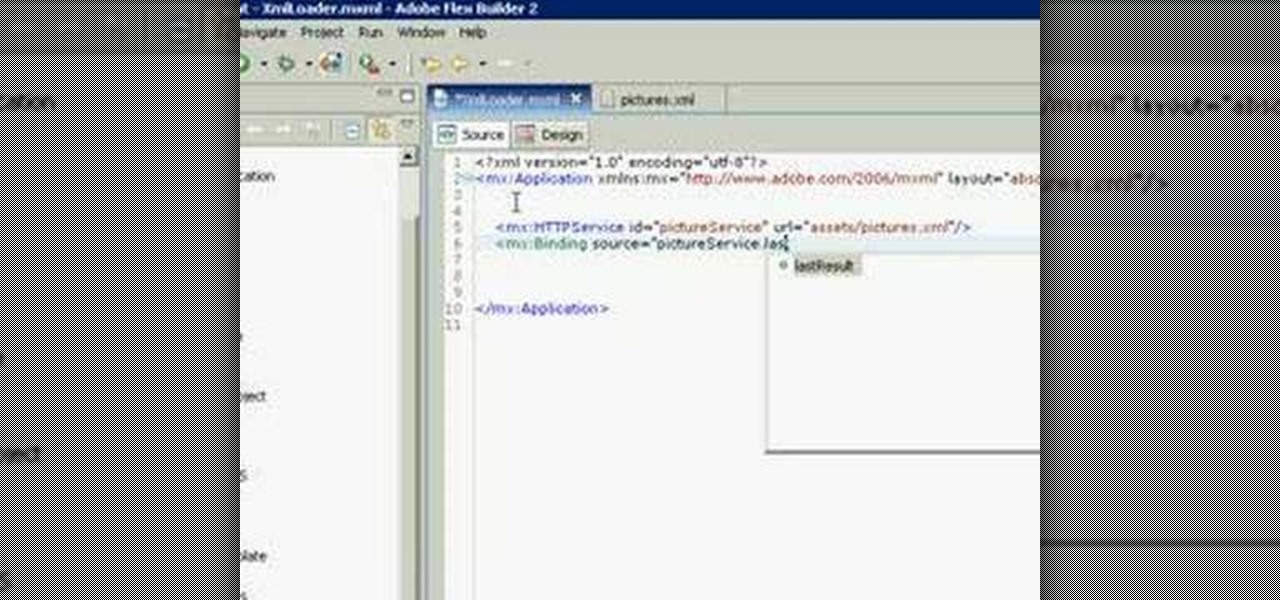
This XML video tutorial will show you how to bind an XML file in MXML in about ten lines. First you'll want to create a Flex project in Adobe Macromedia Flex Builder 2, then create an assets folder and a new XML file in MXML. Coding doesn't get any easier than this. Just watch and learn.

This video tutorial shows how to download .cut files onto Cricut software to design cards. Learn how to use this card making software, and get instructions for how to make a strawberry greeting card.

Learn how to get started in Photoshop Elements by importing digital photo files from your files and folders or off of CDs.

There's an easy way to get huge files with very little degradation to the file by using a little known secret in photoshop. Check it out in this video.

This walks you through how to create an animated GIF image file that can be used in websites, as avatar's, as icons, etc. You'll be using Microsoft Paint to create each frame of the animation, and an application called Unfreez (found here) to animate them together.

This is a tutorial on how to edit type in a layered file and a flattened file in Photoshop.

In this video, you'll discover how to upload files to your own website or blog using FTP.

How to easily fix the missing tags in your MP3 collection using free software called Fixtunes. The tags on an MP3 file identify things like the Song Title, Recording Artist, Album Name, Genre, Track Number, etc. When you buy songs from places like the iTunes Music Store or MP3.com these tags are complete. Some of the songs in your iTunes library may have incomplete tags. This is how you fix them.

In this video tutorial we will take a look at how to import files into DVD Studio Pro. Do note that it is recommended to render your movies into a compatible format before importing to DVD Studio Pro. The author suggests to use Compressor to do the job.

Google Meet might not have virtual backgrounds like Zoom, but it hits all of the other basics, from hosting many multiples of video participants to sharing your screen, that you'd expect from a robust video conferencing platform.

In the past, if you upgraded to a new Galaxy or if you had to factory reset your existing one to fix an issue, you had to restore your home screen layout manually. Your wallpaper, widgets, icon placement, and launcher settings were all dependent on you to be put back in their place. Thankfully, this isn't an issue anymore.

The biggest hurdle to rooting is that it usually requires a computer. Things get complicated when you're trying to use a desktop operating system to exploit a mobile OS, and the connection isn't always reliable. But with the help of Magisk, you can now use one Android phone to root another.

I recently picked up a Pixel Slate when Google had a deal going on. I'd been in the market for an Android tablet since the Nexus 7, and this was the closest thing to it. Unfortunately, I soon learned Chrome OS and Android aren't as integrated as I had hoped.

Compromised uTorrent clients can be abused to download a malicious torrent file. The malicious file is designed to embed a persistent backdoor and execute when Windows 10 reboots, granting the attacker remote access to the operating system at will.

Web applications are a prime target for hackers, but sometimes it's not just the web apps themselves that are vulnerable. Web management interfaces should be scrutinized just as hard as the apps they manage, especially when they contain some sort of upload functionality. By exploiting a vulnerability in Apache Tomcat, a hacker can upload a backdoor and get a shell.

If you're concerned about someone accessing your OneDrive files, you may want to upgrade your protection by enabling fingerprint or Face ID unlocking. Your sensitive information deserves to be protected, and now you can do so easily. Worry no longer — if you need to let someone else use your phone, with a password-protected OneDrive, sneaky file grabbers will be out of luck.

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

As part of the iOS 11 update, Apple added a document scanner function that creates high-quality digital copies of physical documents, but it was only available inside the Notes app. With iOS 13, Apple has built its scanner right into the Files app, enabling you to quickly create PDFs with your iPhone and do more with them.

The triple camera system on the OnePlus 7 Pro is the best setup they've ever done so far, but it could always be better. The primary sensor packs a whopping 48 megapixels, but as history has taught us, megapixels don't equal better photos by default. In fact, with where we are in terms of hardware right now, it's the software that determines a phone's camera performance.

Metadata contained in images and other files can give away a lot more information than the average user might think. By tricking a target into sending a photo containing GPS coordinates and additional information, a hacker can learn where a mark lives or works simply by extracting the Exif data hidden inside the image file.

The Pixel 3a came out of nowhere and flexed its muscles to show the industry that you can have a great phone without a hefty price tag. Since Pixel smartphones are first-party devices straight from Google, you can be sure you'll have root access one way or another. For right now the method used to get your Pixel 3a rooted will take a few steps, but they go by real quick.

Apple's Gatekeeper security software for macOS (Mac OS X) is vulnerable to remote attacks up to version 10.14.5. An attacker that's anywhere in the world can exploit MacBooks and other Mac computers by sharing a single ZIP file.

Every model iPhone since the 6s has boasted a 12-megapixel rear camera. You can take some pretty spectacular, professional-looking photos with it, especially on devices that have more than one rear lens. But the file size of each photo can become a problem when sending as an iMessage, which can eat up data.

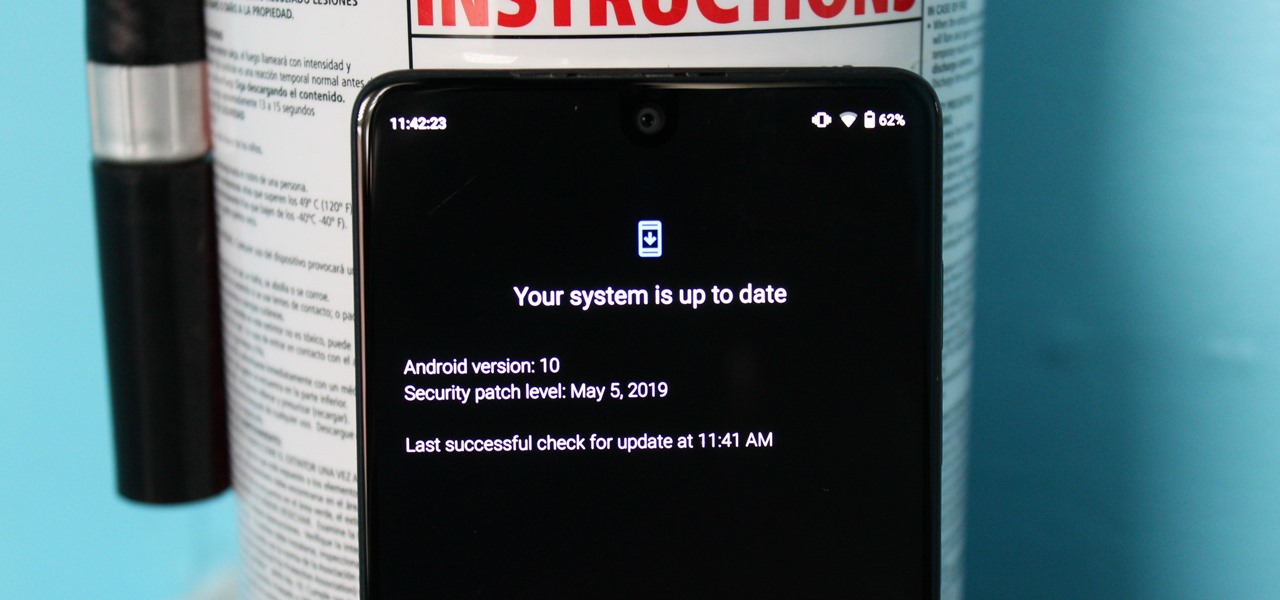
Like last year's beta release of Android Pie, Google has allowed the Android Q Developer Previews to support some non-Pixel devices. Announced at Google I/O 2019, there are 15 non-Pixel smartphones eligible for the Android 10 Beta, including 2017's Essential PH-1.

Samsung has stepped up its camera game with the Galaxy S10's dual- and triple-lens systems. But as impressive as the hardware is, the native Samsung Camera app still isn't as good with image processing and video stabilization as the Google Camera app for Pixel phones. Thankfully, you can get the best of both worlds.

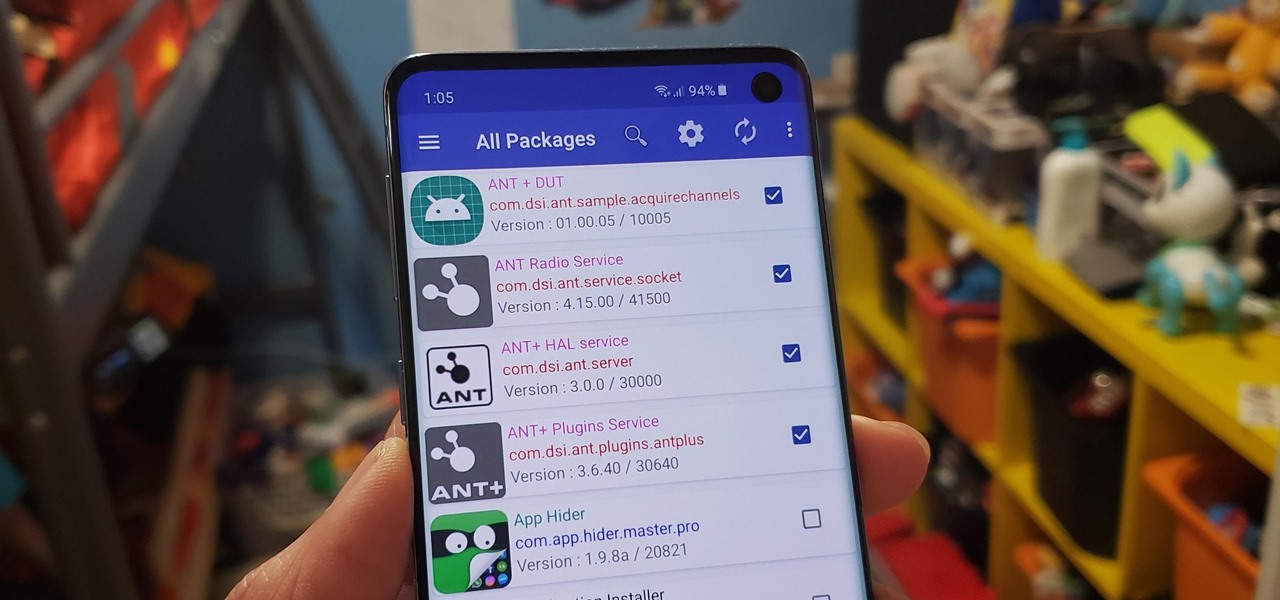
Bloatware remains one of the biggest problems with Android, especially when tied to a carrier. Removing bloatware usually requires you to take extreme measures like rooting. Unfortunately, the Galaxy S10 falls under this annoying umbrella, but there's an easy workaround.

Microsoft Office files can be password-protected in order to prevent tampering and ensure data integrity. But password-protected documents from earlier versions of Office are susceptible to having their hashes extracted with a simple program called office2john. Those extracted hashes can then be cracked using John the Ripper and Hashcat.

Switching phones has never been easier. Google backs up most of your app data on the cloud, which can then be restored onto your new phone. Sadly, Signal doesn't use this feature since it could compromise your security. Instead, Signal stores encrypted backups locally, requiring a bit of work to restore these messages.

Samsung isn't known for its timely rollout of major Android updates, and Android 9.0 Pie won't be an exception. If we go by their Oreo update timeline, we can expect Android Pie to officially touch down for the Galaxy S9 and S9+ sometime around November, with the final version rolling out the around the first quarter of 2019. But a leaked version of the beta has already hit the internet.