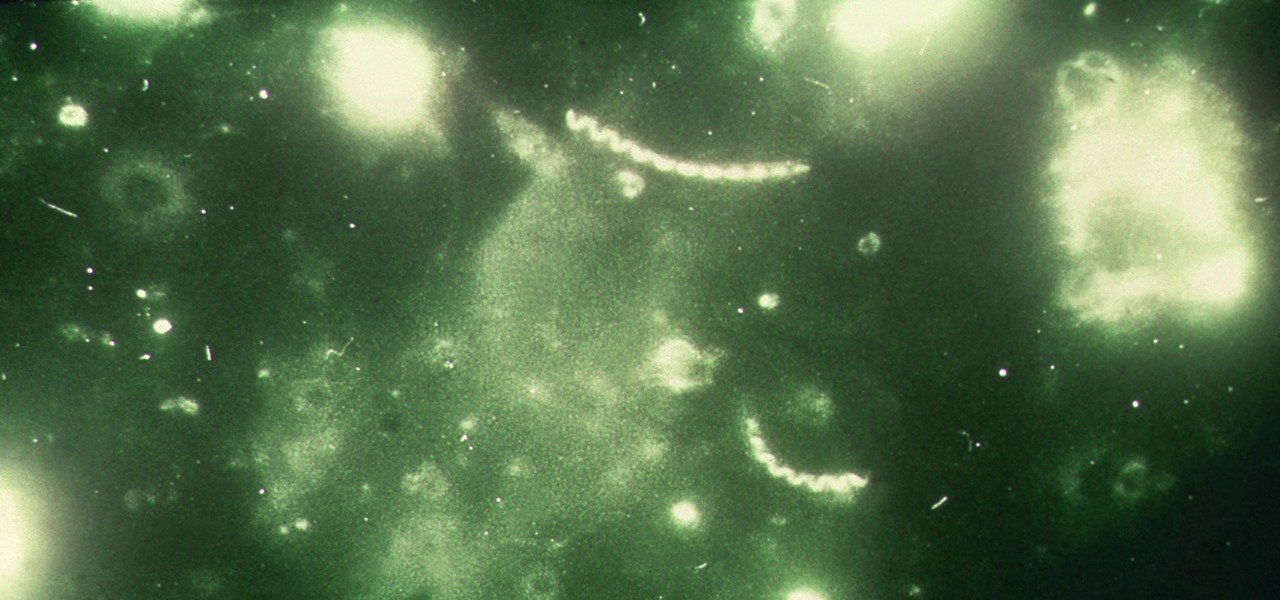
Look no further than Flint, Michigan, to discover the serious consequences of contaminated drinking water. Around the world, water polluted by pathogens and toxins sickens people or cuts them off from safe drinking water. Looking for a solution, researchers created tiny, swimming robots that pack a powerful punch against waterborne pathogens.

Citrus greening disease — caused by a bacteria spread by psyllid insects — is threatening to wipe out Florida's citrus crop. Researchers have identified a small protein found in a second bacteria living in the insects that helps bacteria causing citrus greening disease survive and spread. They believe the discovery could result in a spray that could potentially help save the trees from the bacterial invasion.

Move over whole wheat — white bread may be back in style after a new study shows that it may be your gut microbes that decide what kind of bread is best for you.

Stakeholders in the driverless industry are anxiously awaiting changes the US Department of Transportation (DOT) is making to self-driving vehicle guidelines.

Ford's appointment of Jim Hackett as its new president and CEO reflects how the company is largely pinning its long-term survival hopes on its driverless business. Following his previous role as head of Ford's Smart Mobility division, which overseas Ford's autonomous driving activity, Hackett will help the company take a more self-driving direction as a whole.
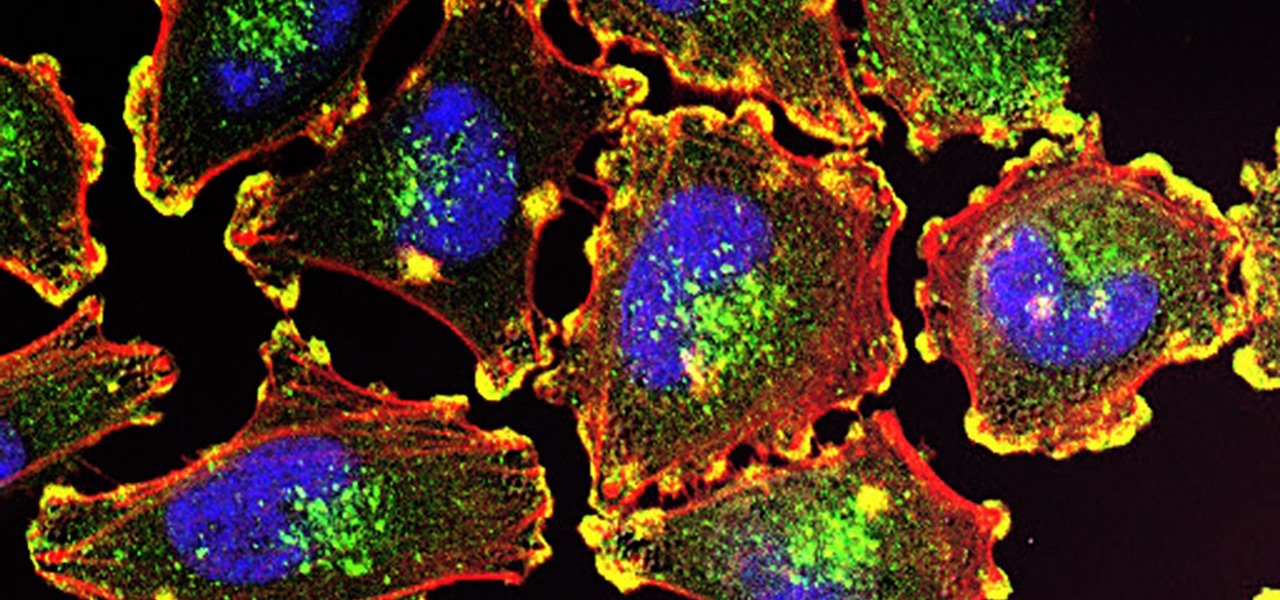
Activating the body's own immune system to fight cancer is the goal of immunotherapy. It's less toxic than chemotherapy and works with our body's natural defenses. The trouble is, it doesn't work for most patients — only about 40% of cancer patients get a good response from immunotherapy. But coupling it with another type of cancer therapy just might deliver the punch that's needed to knock out cancer.

Drug-resistant bacteria have made curing some infections challenging, if not nearly impossible. By 2050, it's estimated that 10 million people will be dying annually from infections with antibiotic-resistant organisms.

Even though the Ebola virus was discovered as recently as 1976, over 30,000 people have been infected since, and half have died a horrible death. Since there's no way to cure the infection, the world desperately needs a way to prevent it — and the five similar viruses in its family, the ebolaviruses.

We've worked hard to reduce the flow of toxic chemicals into our waterways, which means no more DDT and other bad actors to pollute or destroy wildlife and our health. But one observation has been plaguing scientists for decades: Why are large quantities of one toxic chemical still found in the world's oceans?

Colorado State University scientists have developed new tech that quickly identifies the presence of Zika virus in mosquito populations — and in human body fluid.

In order for software developers to do their jobs as new hardware reaches the market, they will need the right tools to get their projects off the ground and into augmented and mixed reality devices. There have been completely new approaches to development when it comes to AR and MR, and these are some of the faces behind them.

Devastating and deadly, land mines are a persistent threat in many areas of the world. Funding to clear regions of land mines has been decreasing, but new research may offer a less dangerous method of locating hidden, underground explosives by using glowing bacteria.

Every Friday, Next Reality reviews the latest headlines from the financial side of augmented and mixed reality. This Market Reality column covers funding announcements, mergers and acquisitions, market analysis, and the like. This week's column is led by two companies cashing in on visual inputs.

Phase 2 of a Zika vaccine trial began in the United States this week, along with Central and South America.

There could be a fresh outbreak of the Zika virus in the Americas as the weather heats up and the mosquito population blooms.

The search for a cancer treatment that selectively finds and kills only the cancerous cells has just made a giant leap forward.

A new study just out reveals that HIV takes hold in the human body with the help of cells that usually work to heal, not kill.

A tiny louse is responsible for decimating the citrus industry. Diaphorina citri, the louse in question, better known as the Asian citrus psyllid, harbors and spreads the "Candidatus Liberibacter asiaticus" bacteria that causes citrus greening disease.

The pathogen referred to as a "nightmare bacteria" is quietly adapting and spreading faster than anticipated.

As fun as it is to see Fido's face light up when you feed him table scraps, American dogs are getting fat. The good news is that research is homing in on nutritional strategies to boost canine capabilities to maintain a healthy weight.

Lighthouses and signal fires may have been the first social media. Without the ability to share language, a distant light meant "humans here." A new study from the University of California, San Diego, finds that bacteria can also send out a universal sign to attract the attention of their own, and other bacterial species.

You might feel the bite, you might not, but an infected mosquito has injected you with a parasite named Plasmodium falciparum, a single-cell protozoa that quickly takes up residence in your body.

The presence of certain bacteria can indicate whether the vaginal tract is healthy or not. It could also impact the likelihood of acquiring certain sexually transmitted diseases, like HIV, a new study suggests.

What do Leo Tolstoy (writer), Beethoven (composer), Paul Gaugin (artist), and Adolf Hitler (politician) have in common? They are all considered to have suffered from the sexually transmitted disease syphilis.

The Snapdragon 820 and 821 were met with praise last year, receiving almost no complaints compared to their overheating predecessor, the Snapdragon 810. But now, all eyes are on Qualcomm to see what goodies they have in store for us this year, as their new SoC, the Snapdragon 835, will be revealed this week at CES 2017.

Super Mario Run has been one of the most insidiously addicting iOS games to come out in recent years for iPhone. And now, as of March 22, Android users can get in on the fun, too.

Months before London-based Jonathan Moon would turn 30, he started musing over how to celebrate. While he had rung in past birthdays at home, he wanted to do something out of the ordinary as a farewell kiss to his twenties. A short ski vacation with friends felt like the perfect idea.

The story of Helicobacter pylori is a real testament to the tenacity of medical researchers to prove their hypothesis. It took decades before the scientific world would accept that the bacteria H. pylori caused ulcers.

Findings from a mouse study suggest that the Zika virus infection may have serious reproductive consequences for men.

New weapons are needed to combat antibiotic-resistant bacteria. Instead of drugs, scientists have discovered in an animal study that they may be able to harness vampire bacteria to vanquish pneumonia.

In this first part of my series on getting started with Windows Holographic, we are going to cover everything you need to get set up for developing HoloLens apps. There are many pieces coming together to make one single application, but once you get used to them all, you won't even notice. Now there are different approaches you can take to make applications for HoloLens, but this way is simply the fastest.

Smartphones have been around for nearly a decade now, so we've had plenty of time to develop preconceptions and bias. People that have never owned an iPhone will tell you that Apple devices are restrictive and bland, while others might say that stock Android is boring compared to manufacturer skins like HTC's Sense, despite never having owned a Nexus or Pixel.

When it comes to Android automation apps, Tasker has never had much competition. But considering how difficult it can be for a novice user to get the hang of things, and factoring in Tasker's drab and complicated interface, there's definitely room for another developer to step in with a Tasker alternative.

Google Photos is one of the best photo management services out there. It allows you to back up an unlimited amount of high-quality images without ever paying a dime, the photos and videos sync flawlessly across all of your devices, and its neural network-powered visual search feature seems like something that was pulled directly out of a Sci-Fi movie.

When it comes to security, Android generally takes an all-or-nothing approach—once someone has your PIN, they're free to do just about anything, up to and including wiping your device. This is why you have to be extra careful to ensure that neither strangers nor friends are looking over your shoulder while you're entering your PIN.
Most of you lot would be aware what WPA/WPA2 is so I won't bang on about the encryption or protocols a great deal. In short WPA and WPA2 both have a maximum of 256bit encrypted with a maximum of 64 characters in the password. The encryption is really only 64bit but x 4 because of the way the authentication functions as a 4 way handshake.

Greetings, fellow NBers! Welcome to my sixth iteration of my sorting series. Today, we'll be discussing a personal favorite: Quicksort, or Quick Sort.

Everyone has their own reality, and in that same vein, everyone has their own guidelines for what makes the "perfect fried chicken." Now, I'm not saying that my version is the ultimate for everyone, but it's definitely a crowd pleaser in my experience.

Welcome back, my tenderfoot hackers! Web apps are often the best vector to an organization's server/database, an entry point to their entire internal network. By definition, the web app is designed to take an input from the user and send that input back to the server or database. In this way, the attacker can send their malicious input back to the servers and network if the web app is not properly secured.

Welcome back, my greenhorn hackers! Over the years, I have written many articles here on Null Byte chronicling the many the hacks of the NSA, including the recent hack of the Juniper Networks VPN. (By the way, my speculation in that article has proven to be correct. The NSA did embed a backdoor on those devices.)