Remember the Rocketeer? The rocket jet pack that he wore? Jet packs are the coolest sci-fi props that haven't been perfected in "real life" yet. Almost, but not quite. For now, film rocket belts or rocket packs will do. Like in the Bond flick "Thunderball" and in the Star Wars movies "Attack of the Clones" and "Return of the Jedi". It's even in "Fahrenheit 451" and "Minority Report". But your homemade DIY jet pack might be the best of all. Watch this video tutorial to learn how to build a jet...
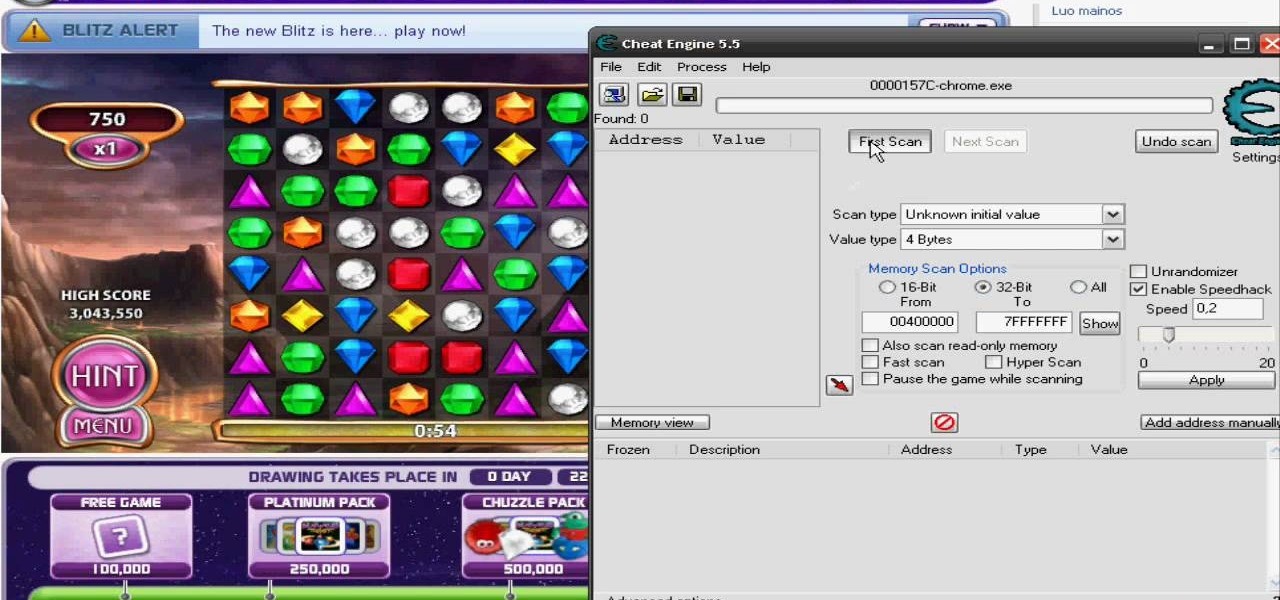
What's the one way to cheat on Bejeweled Blitz? Slowing down the time. If you can get the game to slow down a good amount, then maxing out your score isn't a problem. But you need something to help, like Cheat Engine...
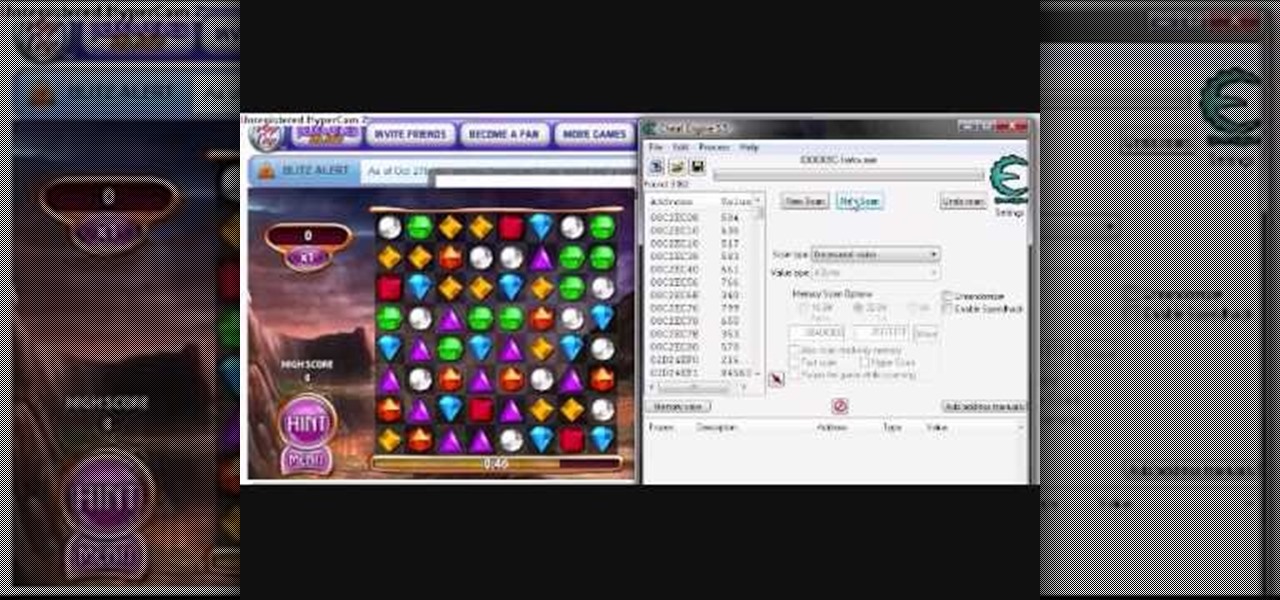
New to hacking? Hacking time in Bejeweled Blitz isn't all that complicated. You just need to be familiar with what you are doing, and the only way to do that is to watch this video tutorial to learn how to hack the Facebook game Bejeweled Blitz (10/27/09).
Many say that this hack for Bejeweled Blitz doesn't work, but it does. The key to getting it to work is merely clearing your cache and restarting your browser and computer. Then, cheat away...

Don't let Bejeweled Blitz get you down. It's not an easy game. Sometimes you just can't handle the degree of difficulty this notorious game imposes. But there are ways around this...

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast.

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast. Search Systm on WonderHowTo for more DIY episodes from this Revision3 show.

Daniel Martin, a magician and escape artist, explains his technique for getting out of thumbcuffs. Disclaimer: We're pretty sure it's not illegal to know HOW to escape from thumbcuffs... but we're 100% sure it's illegal to actually escape when detained by law enforcement (just sayin').

Watch this science video tutorial from Nurd Rage on how to make a complete refillable glow stick. You can make this complete and refillable glow stick with a steampunk-style to it.

Watch this science video tutorial from Nurd Rage on how to restore silver with electrochemistry. You can restore old silver with aluminum foil or a battery by simple electrochemistry.

Want to learn how you can make some awesome YouTube videos of your own? Maybe your own Internet show or maybe even a short indie film... well, one way to make things easy is a green screen. This two-part video tutorial will show you how to make your own green screen studio and key it out. With a green screen, a YouTube show with special effects is easy!

No more q-tips! No more alcohol! No more blowing in your cart! Did you know alcohol actually damages the carts? This is a much more effective, safe and long term way to restore the connection.

Watch to learn how to turn an ordinary photo into an interesting photo using special effects either created by you or provided by Photoshop.

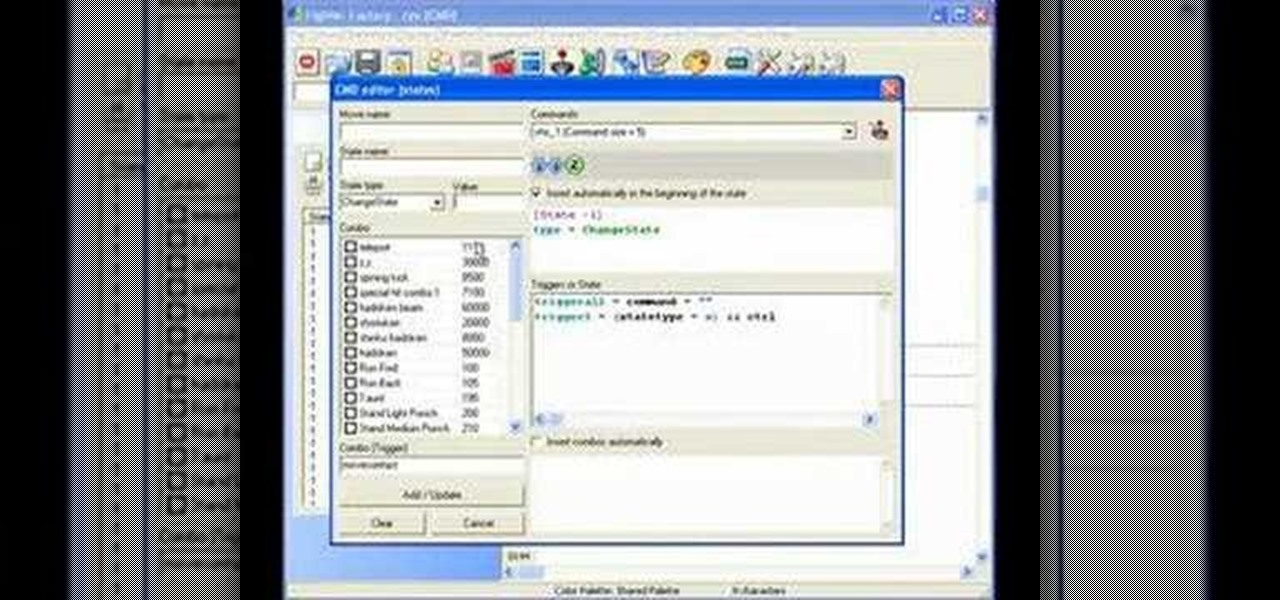
This tutorial tells you about most common variables and extra special effects and others to make your character better in Mugen - the custom PC game engine.

In many urban areas, GPS doesn't work well. Buildings reflect GPS signals on themselves to create a confusing mess for phones to sort out. As a result, most modern devices determine their location using a blend of techniques, including nearby Wi-Fi networks. By using SkyLift to create fake networks known to be in other areas, we can manipulate where a device thinks it is with an ESP8266 microcontroller.

Pyrit is one of the most powerful WPA/WPA2 cracking tools in a hacker's arsenal, with the ability to benchmark a computer's CPU speeds, analyze capture files for crackable handshakes, and even tap into GPU password-cracking power. To demonstrate how quickly it can hack a WPA/WPA2 password, we'll use it to play a Wi-Fi hacking CTF game anyone can practice for less than $10.

A powered-off MacBook can be compromised in less than three minutes. With just a few commands, it's possible for a hacker to extract a target's password hash and crack it without their knowledge.

I hate folder names, especially the one Apple shoves down our digital throats. On a computer, they make total sense, but on my iPhone, it's just more clutter on the home screen. You can tell what folder is what just by looking at the app icons within it, so why are we forced to label them? Technically, we're not, since there is a workaround in iOS 12 and iOS 13 to make those labels disappear for good.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

Design flaws in many routers can allow hackers to steal Wi-Fi credentials, even if WPA or WPA2 encryption is used with a strong password. While this tactic used to take up to 8 hours, the newer WPS Pixie-Dust attack can crack networks in seconds. To do this, a modern wireless attack framework called Airgeddon is used to find vulnerable networks, and then Bully is used to crack them.

It has not been a good year for Apple, as far as software scandals are concerned. From autocorrect nuisances to secret slowdowns of aging iPhones, Apple has had a lot to answer for. iOS users now have another issue to worry about — it's being called "chaiOS," and it's wrecking havoc on iPhones with just a simple URL.

If you used Touch ID on an iPhone before, all you had to do to install apps and games from the App Store was rest your fingertip on the Home button. On the iPhone X, there's Face ID instead, and Apple has included on-screen instructions to help everyone adjust to the lack of Home button. Still, those instructions may not be working for you, but the solution is as simple as a misinterpretation.

Ransomware is software that encrypts a victim's entire hard drive, blocking access to their files unless they pay a ransom to the attacker to get the decryption key. In this tutorial, you'll learn how easy it is to use the USB Rubber Ducky, which is disguised as an ordinary flash drive, to deploy ransomware on a victim's computer within seconds. With an attack that only takes a moment, you'll need to know how to defend yourself.

In the US, law enforcement officials can make you unlock your smartphone with a fingerprint, but they can't force you to input a password or PIN, which would violate your Fifth Amendment rights. To help you from ever being in a scenario where you're forced to put your finger on the Touch ID sensor, Apple has a built-in way for you to disable biometrics on your locked or unlocked iPhone in mere seconds.

Augmented reality sells, but who's buying? Over the past week, two companies made executive hires to capitalize on the growth of augmented reality as a service to sell to other businesses. Meanwhile, two companies joined forces to offer augmented reality tools to headset makers and content providers.

The LG V20 is a true audiophile's phone when it comes to playing music through headphones, but it only has a single bottom-firing mono speaker. So even though the V20 has received plenty of praise for its overall audio experience, that single built-in speaker ruins the fun by putting out some shoddy and cheap-sounding audio.

The LG V20 went on sale on September 29, 2016, and is the second flagship phone in the V series to be released by LG. Both the V20 and its predecessor, the V10, have been audio-oriented phones from the start, but the V20 has a much nicer Hi-Fi Quad 32-Bit DAC, which makes the output audio from the 3.5 mm headphone jack sound amazing. It's loud, it's crisp, it's full, and everything from the higher frequencies to the lower ones can be heard.

A new hack has reopened an 8-year-old iPhone security loophole that Apple thought it had fixed back with iPhone OS 2.2. This is not one of those times when a theoretical attack gets identified and blocked quickly by Apple. On the contrary, it's a hack that actually exists right now, and it can have some serious real-world repercussions, so this is something all iPhone users need to be aware of.

You may not know what HTTP is exactly, but you definitely know that every single website you visit starts with it. Without the Hypertext Transfer Protocol, there'd be no easy way to view all the text, media, and data that you're able to see online. However, all communication between your browser and a website are unencrypted, which means it can be eavesdropped on.

Cable TV providers were dealt a pretty significant blow on Thursday, February 18th, 2016, when the Federal Communications Commission decided that customers should have a choice in what type of device they use to watch cable, instead of being forced to rent a set-top box.

Having websites coded for mobile browsing is great for small screens, but if you have a Plus model iPhone or even the iPhone X, desktop versions of websites might show you more of what you want. Plus, there's the case of poorly designed mobile websites, where the desktop view is clearly the better option with more functionality and features. Luckily, asking for desktop sites in Safari is simple.

Summer cookouts and barbecues come with a lot of delicious foods, but to me, there's nothing better than dishes heaped with avocados. From guacamole to simply eating an avocado right out of its skin, I devour this fruit constantly—but it's one that can be tricky to find perfectly ripe.

Hangouts is a great cross-platform messaging service from Google that works with almost any device, making it one of the few messengers that can be installed on Mac, Windows, iOS, and Android gadgets alike. With its many useful features, one of the few debatable downsides is its not-so-attractive color scheme.

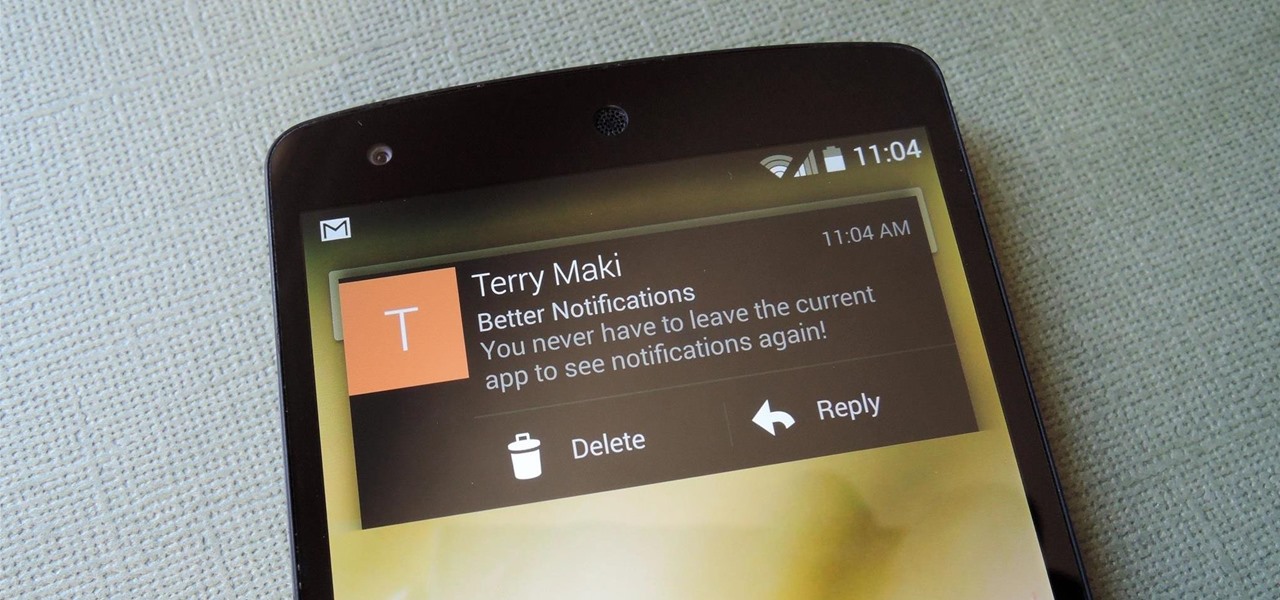
We got a fairly extensive look at the newest version of Android at Google I/O yesterday. The "L" version, which we're betting stands for "Lollipop", brings Google's new design philosophy to Android, and one of the main aspects of that design are new "heads up" notifications. Allowing you to continue using whatever app you're currently in without interuption, this new type of alert borrows from Apple's iOS, but does it the Android way. These notifications can be dismissed with a swipe away, ex...

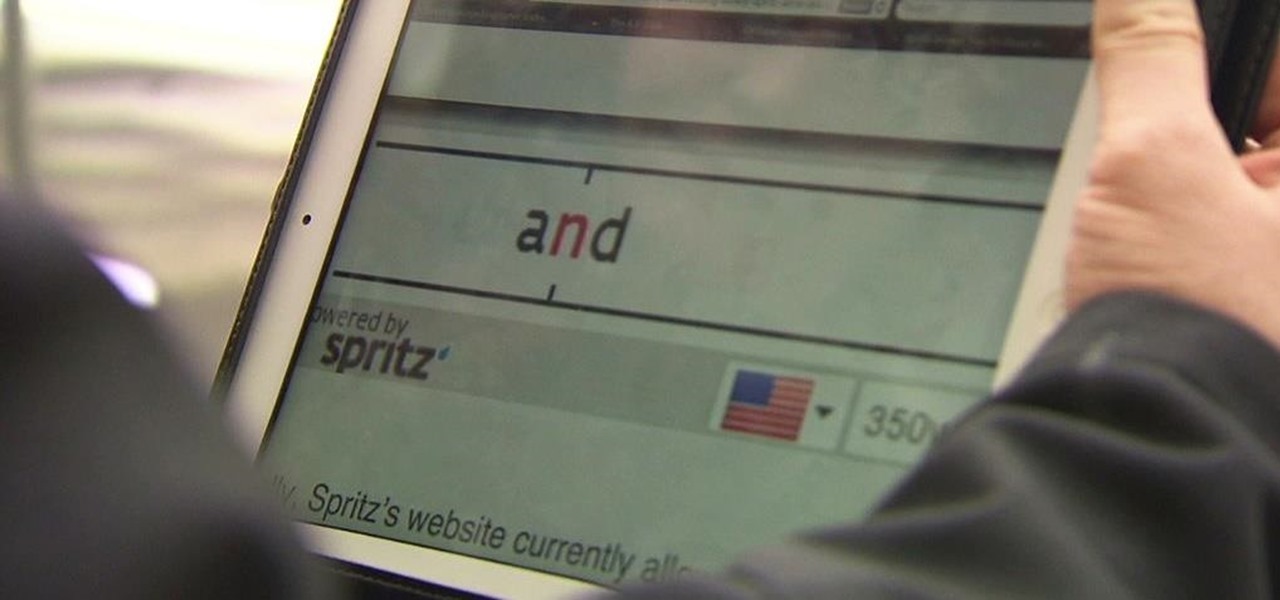
Reading is no longer a leisure activity—it's an on-the-go activity that requires speed and less attention. That's why speed reading apps are growing in popularity. As smartphones and tablets increasingly take over the traditional book market, reading skills need to be adjusted accordingly, so you can cram in 5 pages in-between texts and emails.

How many times have you heard someone utter the phrase, "Now, let's break into groups"? From classroom discussions to workplace think tanks, gathering into groups to generate ideas is common practice. These forced get-togethers are intended to encourage creativity and unique thought, but they can actually do the opposite. More often than not, group brainstorming is annoying rather than encouraging, and these group sessions can actually be detrimental to your productivity. Getting together har...

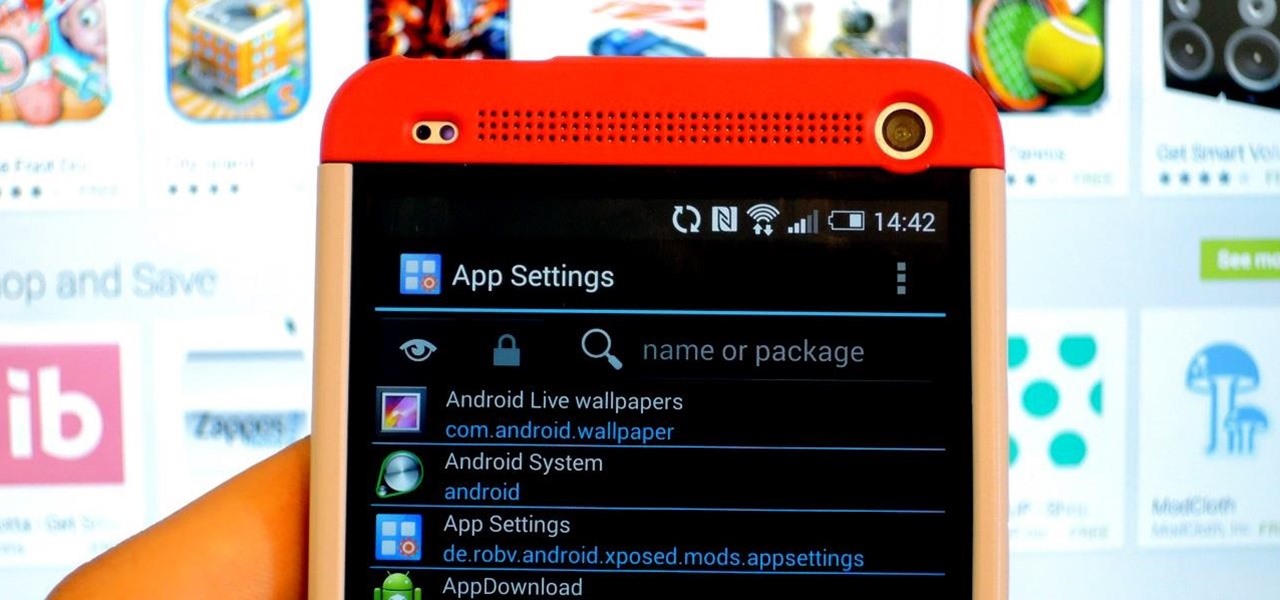
By this point, you've definitely come across an app or two that wasn't designed with the HTC One in mind. Either the resolution is too small, the status bar stays active when it shouldn't, or the font isn't the ideal size. There are ways out there to get that changed, but up until now it wouldn't just change one app—it would change all of them.

Cryptography is the science of keeping secrets, or more specifically, the science of disguising them. As a point of fact, cryptography has progressed quite a bit farther and now encompasses file and message integrity, sender authentication, and pseudo-random number generators.

Walking into a bar or crowded dinner party can be intimidating. Being surrounded by a bunch of people you're unfamiliar with or trying to impress the smokeshow at the bar is no easy task...for most of us.

How to cut Drywall, Sheetrock, Plasterboard. THE EASY WAY! G'day Knuckleheads, Uncle Knackers here and welcome to Video Two of my ten part series titled 'My Top Ten DIY Tips' as nominated by you..