The HoloLens opens up new, digital locales within our physical world, so it was only natural for the HoloLens Challenge to ask developers to create a portal into one. One developer rose to the task and gave life to wall art, turning it into an interactive game called Future Boy.

Amazon is running a pre-sale deal on a few unlocked smartphones by BLU and Motorola, which will be released on July 12, 2016. The 8 GB BLU R1 HD is on sale for just $49.99, and the 16 GB version is available for $59.99, for a savings of $50 off either phone. You can also grab the 16 GB Motorola Moto G4 for $149.99, or the 32 GB variant for $179.99, again a $50 discount on each.
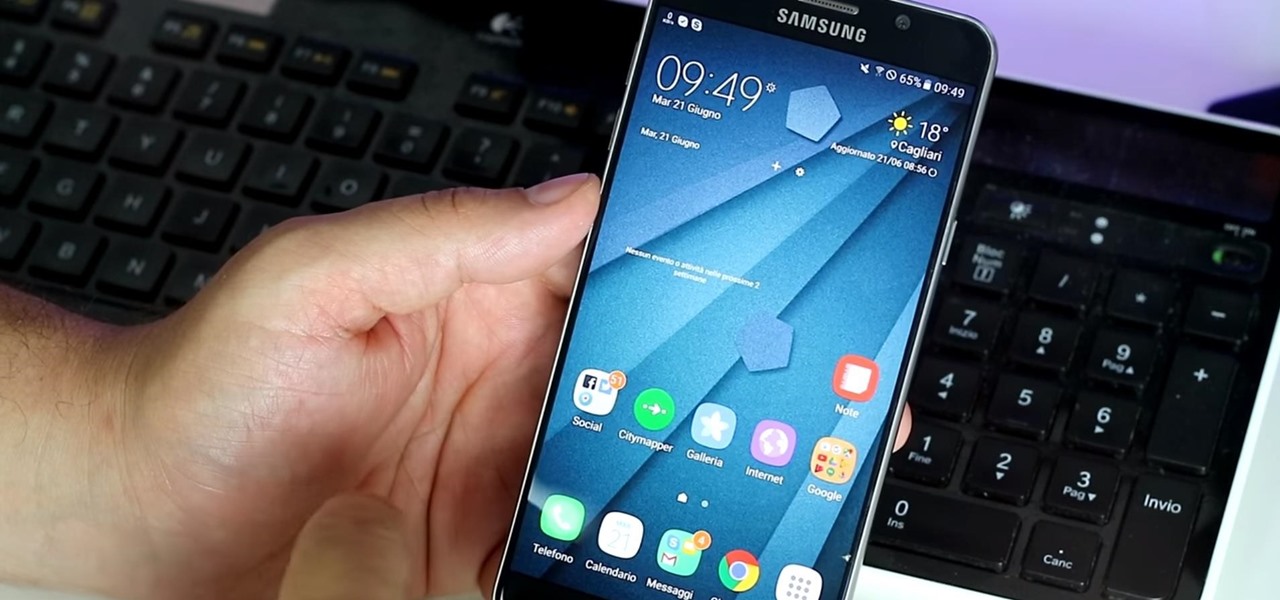
It looks as though Samsung will continue to tone down the look of TouchWiz, according to a leaked look at the newest "Grace" user interface for the upcoming Galaxy Note 7. HDblog, who acquired the leaked UI, shows off the beta version of the new skin in their video below.

The magic of an ice cold popsicle on a hot summer's day is undeniable, whether you're a child or a kid-at-heart. Neon-colored, store-bought popsicles may have a special place in your memory, but homemade popsicles are pretty hard to beat. Here's how to create delicious frozen treats that will both delight your inner child and tickle your adult taste buds!

Ever since iOS 8, you could add widgets on your iPhone using the "Edit" menu on the Today view page, but there's an easier and faster way to get widgets set up for viewing via a right swipe on the lock screen, a swipe right from the first home screen page, and a swipe down from center top everywhere else.
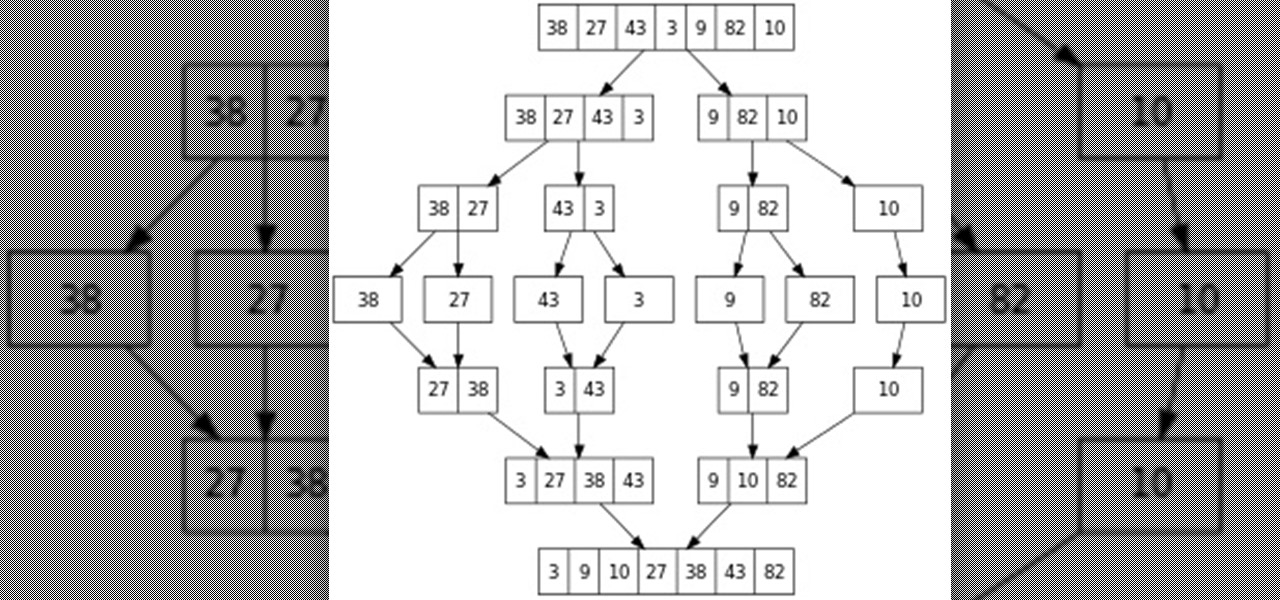
Hello everyone! This is part 7.0 of my Sorting series. I know, I said last time that there would be a 6.1, but not just yet!

Apple has finally addressed and issued a fix for Error 53, a "safety" mechanism that would prevent your iPhone from booting if you had certain repairs done outside of Apple's official channels.

YouTube announced last October some of the original programming it was producing for its YouTube Red subscription service, and the first four originals went live on Wednesday, February 10th.

The big day is nearly here... Super Bowl 50 kicks off this Sunday, February 7, at 3:30 p.m. PST (6:30 p.m. EST). And whether you're having a giant party or watching the game on your big-screen TV by yourself, there's one thing you probably won't be doing: cooking food in your kitchen.

Welcome back, my neophyte hackers! Metasploit is such a powerful tool that I can only scratch the surface of its capabilities here. As it has developed over the years, it is now possible to use Metasploit for nearly everything from recon to post exploitation to covering your tracks. Given its versatility, every aspiring hacker should have at least a tentative grasp of Metasploit.

Hi guys. Hope you all had a good Christmas , today i have a tutorial for you.

Welcome to another C tutorial. We will be looking at arrays, discussing what they are, when they are used and their special relationship with the char variable. Let's begin.

I loved the original Star Wars trilogy when I was a kid, but loathe all of the current DVD, Blu-ray, and streaming versions available today. Ever since 1997, every version of A New Hope, The Empire Strikes Back, and Return of the Jedi has had horrendous CGI effects added in that George Lucas deemed necessary to bring his "ideal" version to life.

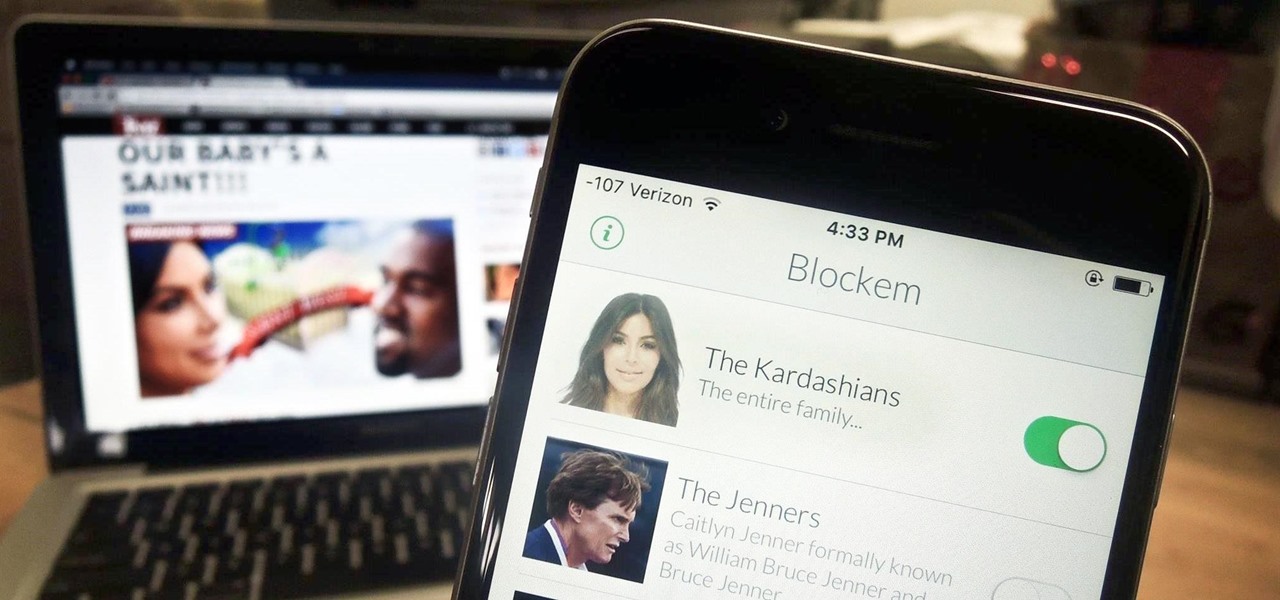
Kim Kardashian and Kanye West have fittingly named their second child "Saint," but I'm sure you don't care about that—and neither do I. Unfortunately, regardless of our pop culture interests, we're forced to know these types of stupid facts because the internet is so densely populated with Kardashian-related content that it's impossible to avoid. It's enough to make you puke.

I had the chance to play around with an iPhone 6s this past weekend, and I have to say, I found the new 3D Touch feature to be pretty intriguing. It's still only partially implemented, but when it does work, it works quite well—you simply press a bit harder on certain elements like image thumbnails, then instead of opening in a full-fledged view, you'll see a pop-up preview that fades away as soon as you let go of the screen.

Greetings all. Before I get into the tutorial, I would like to mention that I am fairly new to Null Byte (been lurking for some time though), and what really appeals to me about this place is its tight, family-like community where everyone is always willing to help each other and the constant search for knowledge that inhabits this subdomain is a driving motivator for me to join in. I'm glad I arrived at the right time. Anyway, wipes tears (not really)...

After a few months, I get so fed up with hearing the same ringtone go off alongside each new notification that I'm forced to switch things up—only to end up repeating this whole process when the new one gets played out. And I'm sure people around me are equally sick of listening to that tired old tone towards the end as well. I mean, a decade later, I'm convinced that Nokia tone is permanently implanted in my brain.

When we hack a web server, we usually want to be able to control it in order to download files or further exploit it. There are many websites that let you upload files such as avatar pictures that don't take the proper security measures. In this series, I will be showing you how to gain root access to such a web server.

Ahh, coffee. That first sip of hot goodness in the morning is glorious, isn't it? There are days when you need it straight up: No extras, please. But what about those moments when you need a little something else? When that flavored French vanilla, hazelnut mocha, blah blah blend just doesn't cut it and you want a truly special flavor in your morning joe?

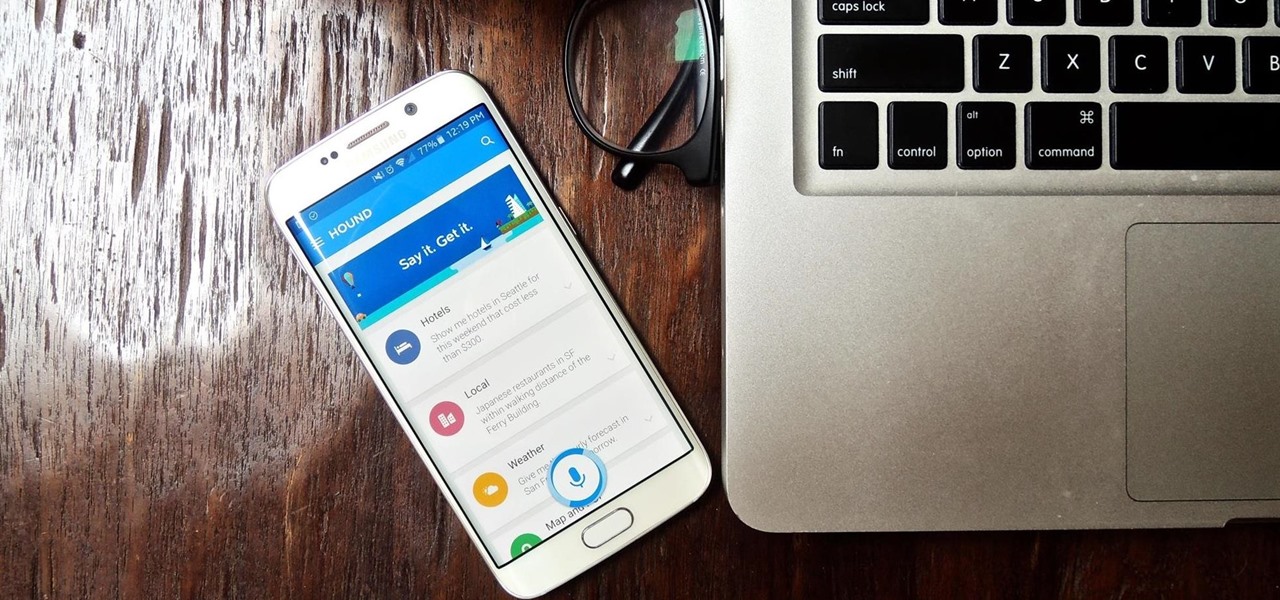
SoundHound's new virtual assistant application, Hound, is gaining a lot of buzz in the tech world—especially after a demo video showed just how awesome it works (it has amassed over 1.6 million views in under a week).

Google recently announced the beta release of a developer tool called ARC Welder for Chrome, which allows developers to run and test their Android apps on any computer with the Chrome browser installed.

Hi everyone! In the previous part of this series we introduced remote code arbitrary execution via buffer overflows using all of our past experiences.

A long time ago in a galaxy far, far away, a man by the name of George Lucas wrote an amazing trilogy about a new world and the power of the Force… and then subsequently ruined the franchise 22 years after the original release date.

The shooting of Walter Scott (who was unarmed) has been dominating the news these past few weeks. Scott, who ran away from police officer Michael Slager after a routine traffic stop, was shot in the back and pronounced dead shortly thereafter. Unlike similar cases where a cop shoots an unarmed person, the police officer involved in this particular shooting is currently in jail, facing a potential murder charge.

Thanks to the strenuous efforts of our Gadget Hacks development team here at WonderHowTo, the fortified barrier segregating Android from iOS has finally fallen down.

3D printing is getting closer and closer to becoming an everyday reality—which means revolutionary things are going to start happening for the home cook. Already there's a 3D printer that can produce edible tailored fruit and the Foodini, which can print full meals, including spaghetti and burgers. However, neither are available for purchase, and most likely won't be within reach of the average cook for years.

If you've ever used a custom ROM on one of your devices, chances are it had a built-in feature that allowed you to kill any app by long-pressing the back button. This function comes in handy quite often, especially in situations where an app is acting up, since it stops all associated processes and clears the app from memory.

When my girlfriend told be about a Trivia Crack cheat she discovered, I was a little dubious. Then, after witnessing her trick in action and trying it out myself, my faith in the popular trivia game was forever tainted.

Now that the Xposed Framework has finally been updated for Android Lollipop, we're starting to notice that some modules function properly, while others are a bit buggy or even worse—don't work at all. Most of this is a result of changes to elements of the Android system that KitKat modules relied upon, and such modules will need to be updated for 5.0 compatibility.

A messaging app that blows your mind doesn't come along very often. Yeah, there's WhatsApp and Facebook Messenger, which are both good for what they are (web-based messaging platforms), but when it comes to interesting or unique features, they're somewhat lacking.

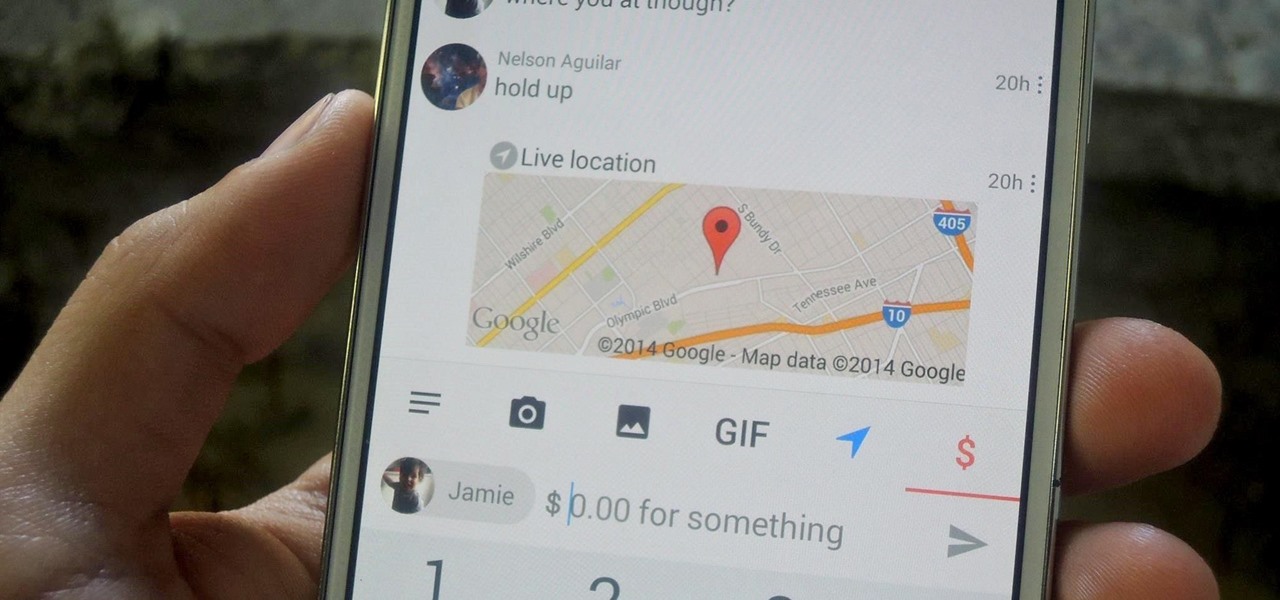
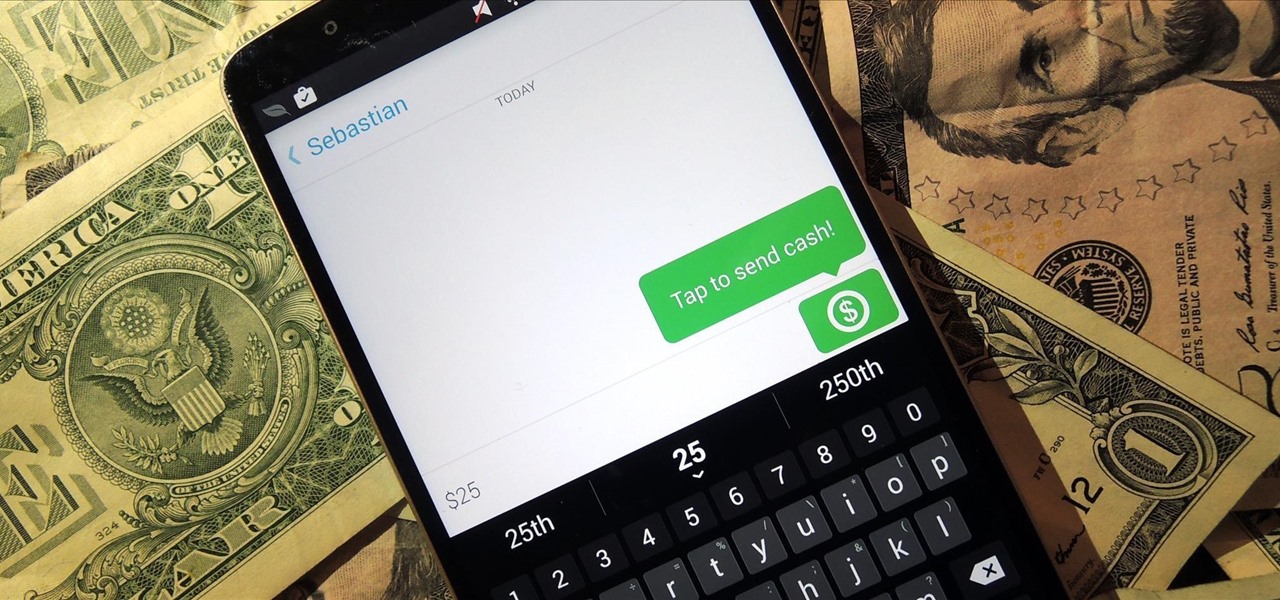
Snapchat is definitely not known for its stellar privacy or security features, but that hasn't stopped them from gaining millions of users. Now, those millions of users can do more than just share pictures and videos—they can share money.

Aside from being able to change the wallpaper and add shortcuts, the Galaxy S4's lock screen doesn't offer much in the department of personalization. The lock screen is efficient and practical, but it's also a little bland.

Welcome back, my nascent hackers! We have spent a lot of time in previous tutorials focused on hacking the ubiquitous Windows systems, but the vast majority of "heavy iron" around the world are Linux or Unix systems. Linux and Unix dominate the world of Internet web servers with over 60% of the market. In addition, Linux and Unix servers are the operating system of choice for major international corporations (including almost all the major banks) throughout the world.

Motorola changed the way users interact with their devices when they introduced their "always listening" feature on the Moto X. When I first saw it demoed, I couldn't wait to get the same functionality on one of my handsets, and now that has finally come to fruition.
This how-to is for everybody who faced the problem of intercepting personal data sending through the Internet and is looking for fast and secure method to protect his activity in the global network.

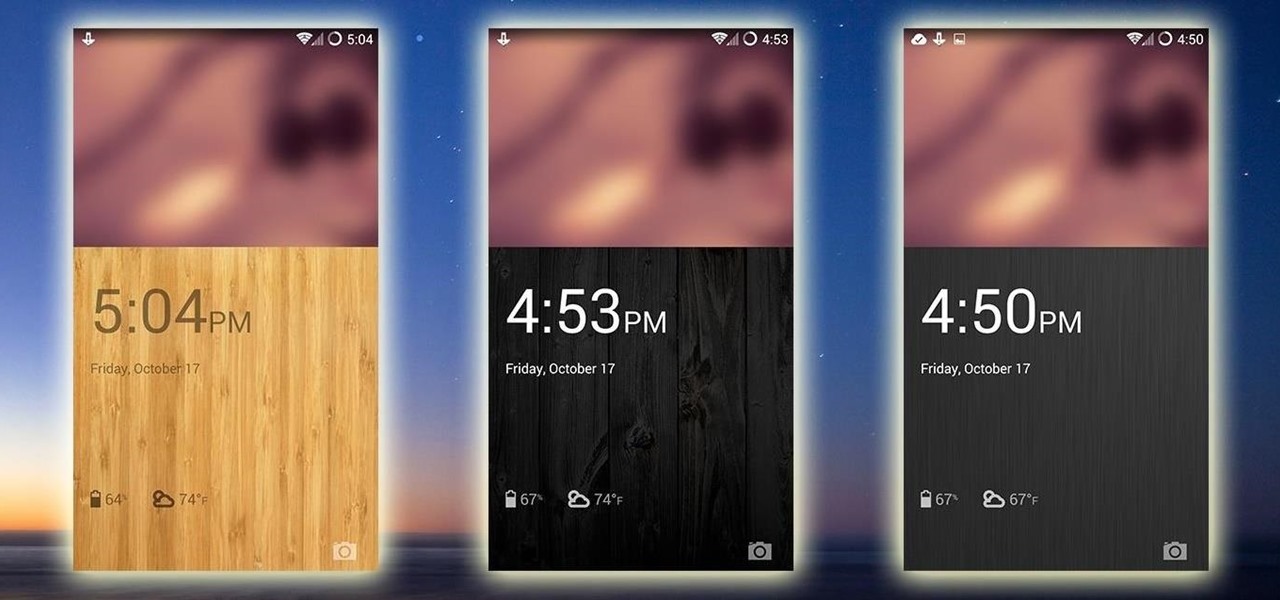
As much as it pained me to lose lock screen widget functionality, I just can't bare changing out the sleek-looking lock screen that's standard on the OnePlus One. The latest OTA introduced a new transparent theme, and while that's a welcomed improvement, I need more options!

Google has a practice known as dogfooding, where they use their employees to test new and upcoming features for their various services. Back in March, they accidentally released a dogfood version of YouTube on Google Play, and many Android users got their first behind-the-scenes glance at the internal testing features.

With root access, you're granted greater control over your device, allowing you to do things that your Android system wouldn't allow otherwise. Things like installing Xposed mods are made possible with root, but other advantages address performance and security, like stopping your Android logging, which is exactly what we'll be going over today.

Some apps have a nasty habit of ignoring your Android's auto-rotation settings and locking the display into either portrait or landscape orientation.

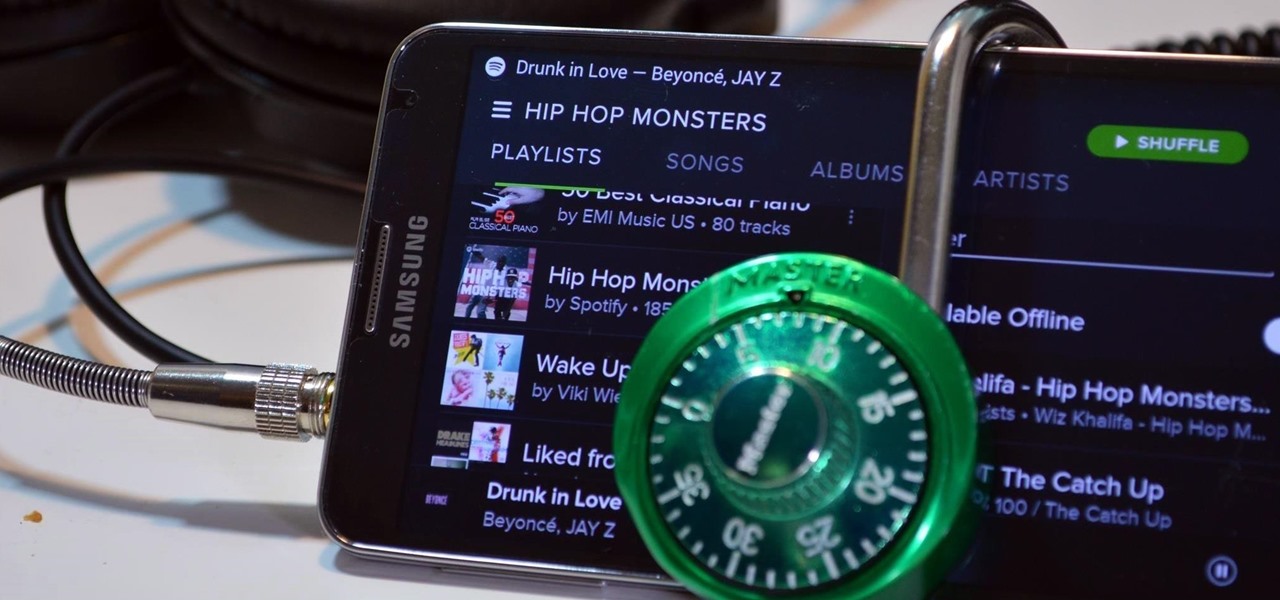
With over 20 million songs, Spotify has become my go-to source for music. I can stream tunes to my desktop or phone, without ever having to worry about storage space being eaten up.