This video production was released in coordination with the 2009 job posting for Army National Guard “Internment Specialists” that Kurt Nimmo reported on at the time. (The original post has been conspicuously removed since then). Notice that the job description, title and duties all seem to match the terminology used in the leaked document FM 3-39.40: INTERNMENT AND RESETTLEMENT OPERATIONS (at Army p/w protected link) outlining the plan to set up camps both globally and domestically (Yes, the...

In this video you will learn an easy trick that will make it much easier for American English speakers to understand you! Brought to you by Accent Master, accent reduction specialists. This video is best for people learning to reduce their accent or students learning English as a second language (ESL).

If you've tossed around the idea of turning your interest in white hat hacking into a career in cybersecurity or IT, now's as good as time as ever to invest some time and energy into improving your skill set.

Using Netcat to backdoor a macOS device has its short-comings. If the compromised Mac goes to sleep, the Netcat background process will occasionally fail to terminate correctly; This leaves Netcat running infinitely in the background and the attacker with no new way into the device. As an alternative, we'll use the lesser-known Tcl shell which can handle abrupt backdoor disconnections.

Rumors are what Apple dreams are made, so most of the time it's best to ignore the juicy ones -- but some Apple rumors demand a least a little attention.

In the wake of Google Glass' failure, we can expect other companies to fill the void in due time. Perhaps unsurprisingly, Snapchat may be one of the first.

While websites may run smoothly without any noticeable vulnerabilities, there's always the looming threat that any background weakness in the site can be exploited by hackers. Once a site is compromised, it can be difficult to get it fixed without the proper help. Google has recently launched a new series entitled "Webmasters help for hacked sites”, which teaches web developers and site owners how to avoid getting hacked and how to recover their website if it gets compromised in any way.

You just brought a brand new Pixel 3 from the Google Store, and you insert your SIM card only to find the phone won't recognize it at all. No matter what you do, the SIM card won't register and your Pixel won't connect to your carrier network. That's what happened to me and several other Pixel 3 owners. The good news is a fix is coming, the bad news is Google doesn't have a date for that fix.

The ride-sharing firm Lyft and Faraday Future, a troubled electric carmaker and potential Tesla competitor, have quietly appointed new top executives, but like the rest of the industry, they struggle to find talent for their driverless programs.

BMW seeks to hire 2,000 engineers for its driverless program ahead of the launch of its iNext Level 3 model in 2021, a source close to the company told Driverless.

Months after Next Reality broke the story surrounding the financial troubles at Meta Company, there's a new update in the company's ongoing patent lawsuit.

At its annual MAX event kicking off on Monday in Los Angeles, Adobe gave the audience a new preview of its forthcoming Project Aero augmented reality authoring tool during the keynote presentation.

Escape rooms, those real world puzzle games that challenge teams to solve a mystery and gain their freedom from a locked room, are all the rage right now. But augmented reality games such as The Lockdown could make them obsolete.

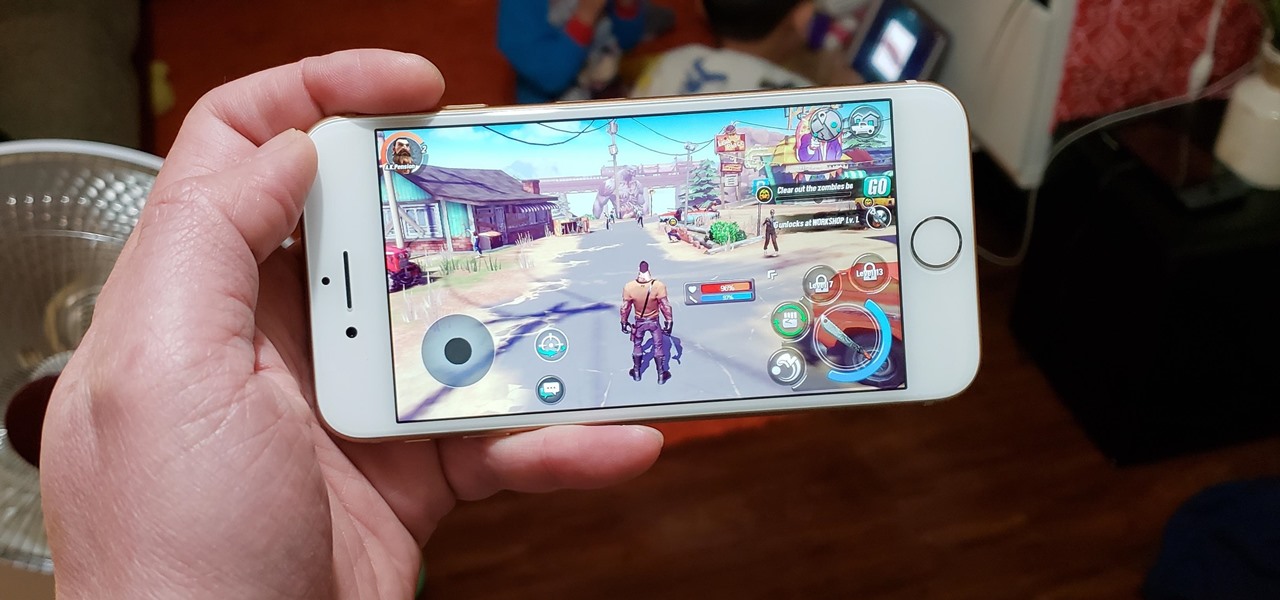
Mobile gamers are well aware of this, but zombie shooters have become pretty stagnant and unimaginative in recent years. Too many entries in this genre feature the same cookie-cutter gameplay, but thankfully, Gameloft aims to change this. The company has soft-launched Dead Rivals in a few countries, and with a little work, you can try the game yourself right now.

A recent TED Talk makes a strong case for the healthcare industry to adopt augmented reality as a means to expanding access to surgical care across the globe.

The HoloLens has become a frequent sight in medical facilities around the world, but a new demonstration shows just how seamlessly it can be integrated into traditional medical procedures to improve the experience for physicians and patients alike.

While the long-awaited HoloLens 2 officially arrived this week, details leaked about another, arguably longer-awaited AR headset, the fabled wearable from Apple, and a previously undisclosed partner assisting the Cupertino-based company with the hardware.

Hundreds of Windows 10, macOS, and Linux vulnerabilities are disclosed every single week, many of which elude mainstream attention. Most users aren't even aware that newly found exploits and vulnerabilities exist, nor that CVEs can be located by anyone in just a few clicks from a selection of websites online.

For a company more associated with debugging computer programs, Google's parent company, Alphabet, is making a name for itself by taking on the real thing — mosquitoes.

Despite longer live spans, almost half a million people die of healthcare-associated infections (HAIs) each year, many of them preventable.

No longer strictly relegated to the realm of science fiction shows and novels, artificial intelligence can be found behind important technologies that are driving innovation throughout the world. From space exploration and self-driving cars to data science and marketing algorithms, AI is the driving force behind many technologies that are moving humanity forward.

If the interconnected worlds of blockchain, Bitcoin, and cryptocurrencies scare you a bit, you're not alone. Thanks in part to the extreme and seemingly random fluctuations in the value of Bitcoin over the past three years, more than a few developers and investors are wary of the cryptocurrency revolution and its ties to blockchain development.

A few long-awaited iOS 11 features that Apple had promised way back in June 2017 have finally made their way to iPhones with the iOS 11.4 update. Aside from finally delivering on those, there's not a whole lot new in iOS 11.4 as a whole, though, there are a few things you'll definitely want to know about.

There is a reason the Amanita phalloides mushroom is called the "Death Cap." It can kill you. Mushrooms are a type of fungi, an organism that produces thread-like mycelia that often produce spores. Spores allow the fungi to reproduce. Molds, lichens, and yeast are all fungi, but the most visible fungi are mushrooms. Some fungi are delicious, but others can cause disease or, and still others, like Penicillium, can cure it.

The office of your physician, or your local hospital, is where you go when you need medical care. But it could also be where you could pick up a life-threatening infection.

Six people have died from fungal infections in Pittsburgh hospitals since 2014—that fact is indisputable. The rest of the situation is much vaguer. A lawsuit has been filed against the hospitals on behalf of some of the deceased patients, alleging that moldy hospital linens are to blame. While the lawyers argue over who's at fault, let's look at how this could have happened.

Not only has there been difficulty finding consensus on a name for driverless, autonomous, self-driving, or automated vehicles, there is also the issue of what we actually mean when we say a vehicle is self-driving, automated, and so on.

Ask anyone that works on the development of driverless vehicle technology and there is a very good chance that AutonomouStuff will have supplied something to their project.

When a dead body is discovered, finding out when the person died is just as important as finding out how the person died. Determining the time of death has always involved lots of complicated scientific detective work and less-than-reliable methods. However, a study by Nathan H. Lents, a molecular biologist at the John Jay College of Criminal Justice in New York, is the first of its kind to show how microbes colonize a body's ears and nose after death.

With the countless daytime talk shows starring and featuring doctors, nurses, and other medical specialists, discovering new ways to live a healthy life is just a remote click away. Although their shows might draw you in with incredible facts and mind-blowing secrets to weight loss success, it's important to take each televised recommendation with a bit of suspicion—most of these familiar faces aren't exactly telling the truth.

YouTube is the third most popular website in the world, after Google and Facebook. Millions of subscriptions happen each day on YouTube, with over 800 million unique users visiting each month. In that timespan, roughly 4 billion hours of video are watched, with 72 hours of video uploaded every single minute.

Don't think because your MacBook is using FileVault disk encryption your device is secure or immune to hackers. Here's how to find out if that FileVault password is strong enough to withstand an attack from a motivated attacker.

After a hacker has configured Metasploit on a remote private server, created a resource script for automation, and created a simple payload, he or she can begin the process of remotely controlling someone's Windows 10 computer with just a few moments of physical access — even if the computer is off.

If you have a HoloLens, you can now control the lighting throughout your home or office via holographic controls using the free Hue Lights app in the Windows Store. The app, made by California-based AfterNow, works with the Philips Hue colored lighting system and is much more polished than the prototype we saw in January.

Kali Linux is established as the go-to operating system for penetration testing, but in its default configuration, it's less than ideal for regular desktop use. While in many scenarios, a live boot or virtual environment can resolve these issues, in some situations, a full installation is better. A few simple changes can be made to a Kali Linux desktop to make it safer to use in this environment.

As was mentioned by the great OTW last week, TOR, aka The Onion Router, has had its integrity attacked by the NSA. In an attempt to reduce the anonymity granted by the service, the NSA has opened a great many nodes of their own. The purpose is presumably to trace the origin of a communication by compromising some entrance and exit nodes. Once both are compromised, it is much easier to correlate traffic with a particular individual.

Lidar, a technology first used by meteorologists and aerospace engineers and then adopted in self-driving vehicles, has slowly crept into consumer electronics over the last five years. If you have a Pro model iPhone or iPad, there's a good chance it has a lidar sensor, and you're likely using it whether you know it or not.

Dave consults with Dave Ropes of Tree Specialists, Inc., about the best way to trim trees that are uncomfortably close to houses or other buildings.

Choosing a nanny or au pair for your children is a process that should be organized and performed carefully, to ensure you find someone who can be trusted, will contribute significantly to the development of your child and integrate well into your family.

In recent years, Russian marine biologist Alexander Semenov has built a stunningly beautiful collection of deep sea photography, capturing alien creatures only locatable in the hostile, icy depths of the far northern sea off the coast of Russia.