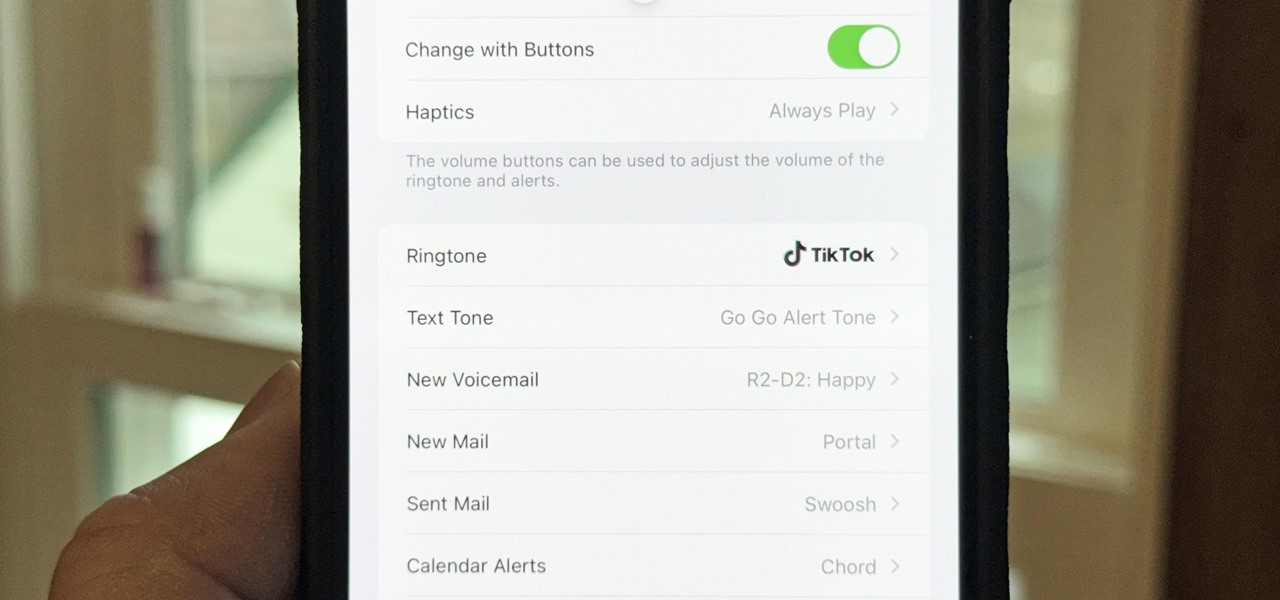
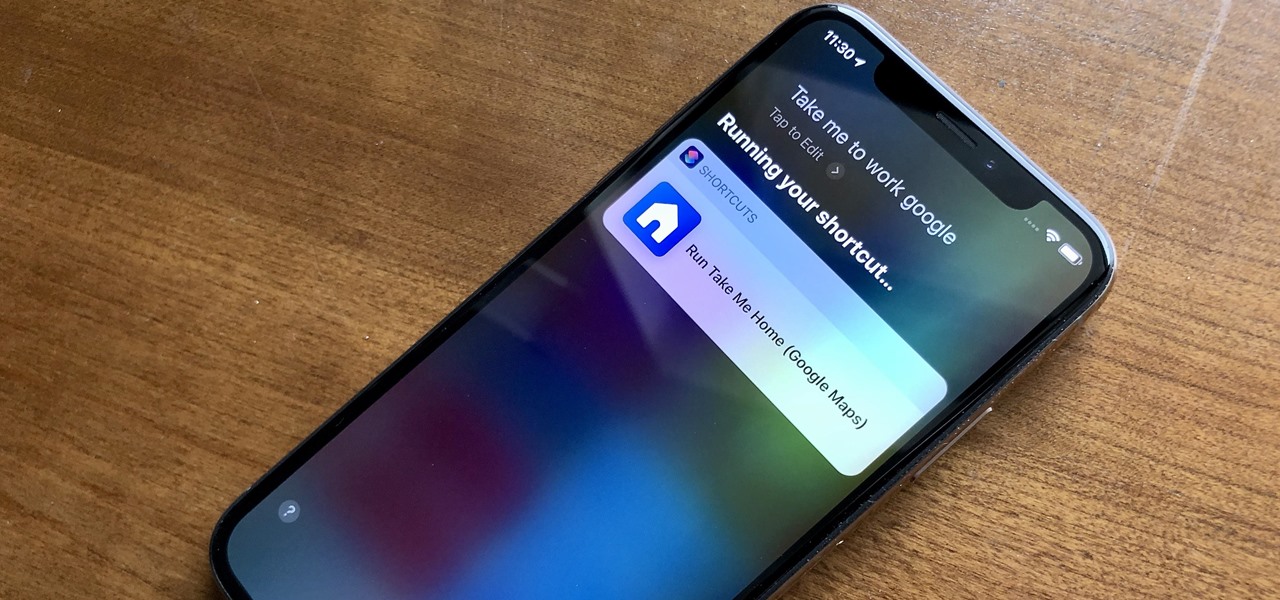
Your iPhone only has a few physical buttons, buttons with a set number of default actions assigned to them, like sleeping your display, controlling volume levels, and even taking pictures. But as much as these buttons can do for you, they can do more. You're not stuck with the out-of-the-box defaults. Every push button on your iPhone can be customized in one way or another.

Thousands of emoji are available on iPhone, iPad, and Mac, and you can use these in many of the apps you have installed on your Apple devices. But there's one emoji you'll likely never see on any of Apple's official emoji keyboards, and its absence may surprise you at first, considering it's embedded in virtually every Apple product. That emoji is, of course, the Apple logo icon.

The App Library is an excellent tool for browsing all the apps on your iPhone, especially since it includes every one of the home screen bookmarks you've made for websites and shortcuts. But it's all the way past your last home screen page. If you have a lot of visible home screen pages, that's a lot of swiping to open the App Library. Luckily, there is a trick to accessing it faster.

Some apps look great with Dark Mode, and some do not. So when you have system-wide Dark Mode enabled on your iPhone and are using an app that only looks good in Light Mode, you'd normally have to turn the dark appearance off manually, then switch it back on when you leave. But there's a workaround that can automate the process for you.
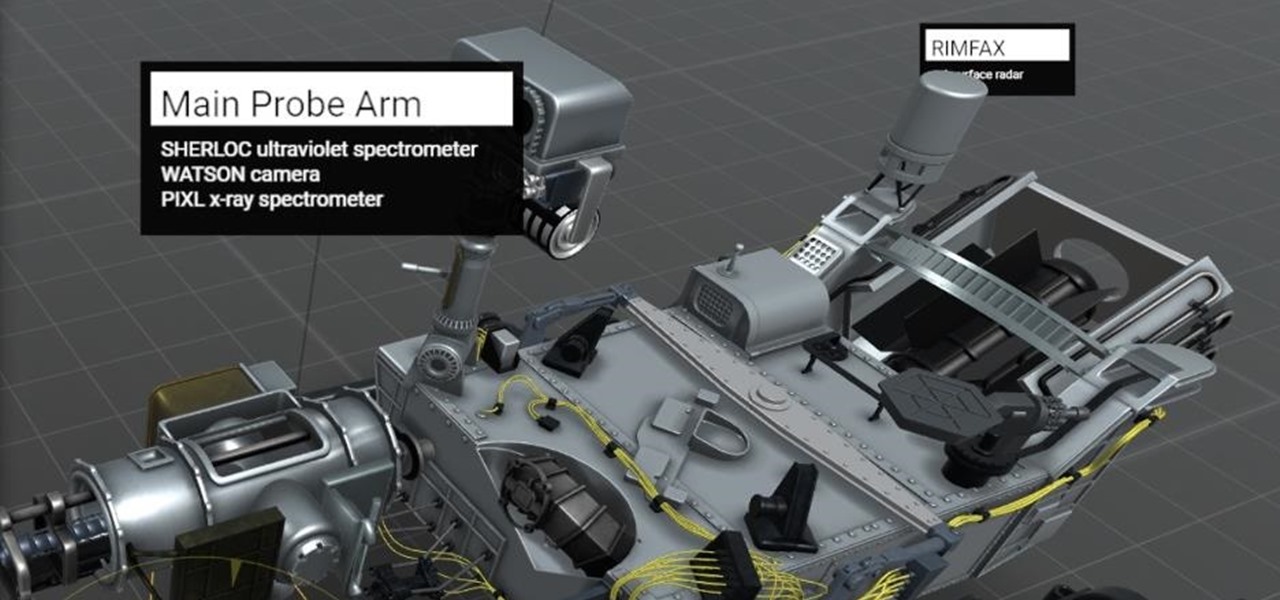
San Francisco-based augmented reality company Scope AR has made building AR instructional content for mobile devices and AR wearables as easy as throwing together a PowerPoint deck, primarily via its WorkLink platform.
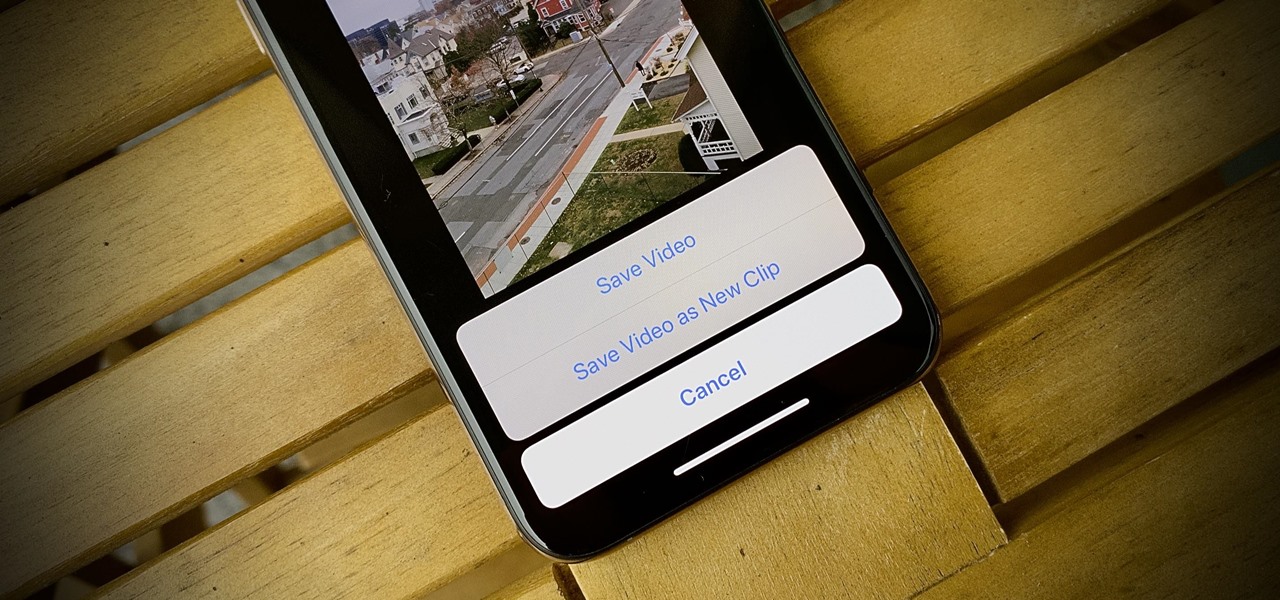
It wasn't long ago Apple released iOS 13.2 to the masses. The second major update to iOS 13 included 22 new features and changes that added a significant layer of depth to an already feature-filled experience. Apple isn't ready to stop the fun, however, as iOS 13.3, released Dec. 10, has a decent amount of new features too.

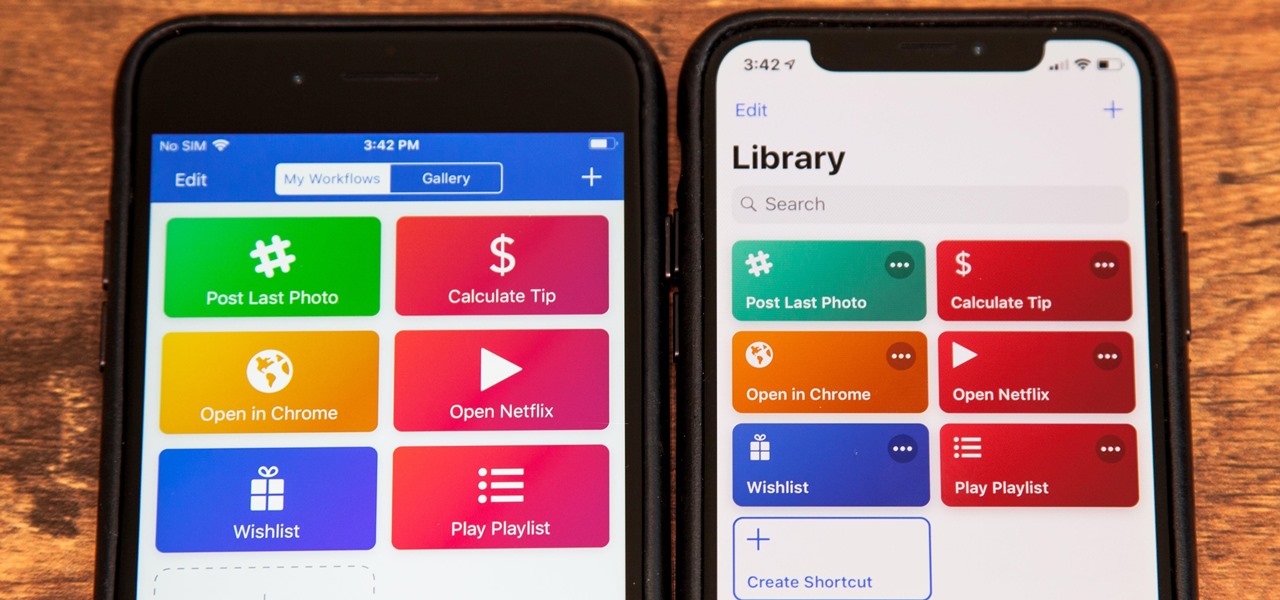
When Apple acquired the popular Workflow app in 2017, many were worried that it would either get replaced with something much worse, or just disappear entirely. Thankfully, Apple put these concerns to rest with the launch of Shortcuts. In iOS 13, Shortcuts is becoming more powerful than ever, providing functionality on the iPhone that the original Workflow team could only dream of.

For the first time, you can officially use a computer mouse with your iPhone, thanks to Apple's new Accessibility settings in iOS 13. It works for all types of Bluetooth mice, so if you have one, it'll already work. Plus, those with wireless receivers and even wired mice are supported by using a USB to Lightning adapter.

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.

Hackers rely on good data to be able to pull off an attack, and reconnaissance is the stage of the hack in which they must learn as much as they can to devise a plan of action. Technical details are a critical component of this picture, and with OSINT tools like Maltego, a single domain name is everything you need to fingerprint the tech details of an organization from IP address to AS number.

Connecting to your headless Raspberry Pi on the go typically requires a network connection or carrying around bulky peripheral hardware like a screen and keyboard. With the help of an old-school connecting standard, though, you can log into your Pi from any computer using a simple cable. If you don't have a power source, you can also power your Linux distro over the cable at the same time.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

An attacker with shell access to a Linux server can manipulate, or perhaps even ruin, anything they have access to. While many more subtle attacks could provide significant value to a hacker, most attacks also leave traces. These traces, of course, can also be manipulated and avoided through methods such as shell scripting.

Hello ladies and gentlemen, PySec here coming at you with another informative(hopefully) article for you all. In the last tutorial, we finally finished our discussion about IP Addressing and I intentionally didn't mention a really important concept with which IP Addressing wouldn't be feasible without it. What I'm talking about is how our network device gets the IP Address in order to communicate with other devices on the network/Internet. There are many different ways for that to be accompli...

For people that like to get things done, Android's home screen widgets are almost indispensable. Rather than packing your launcher with a bunch of icons, you can utilize widgets to get quick information in a beautiful package or provide one-tap access to a particular functionality within your apps.

As we're all aware, recon is vital to a successful hack. We need to know everything we can about the target in order to perform the best possible attack. Port scanning is a basic recon concept that is introduced very early in learning proper reconnoissance. The issue with port scanning is that is makes a lot of noise. Every connection to every port will be logged. This is where stealth scanning comes in. Also known as SYN or half-open scanning, stealth port scanning is a bit quieter, and is l...

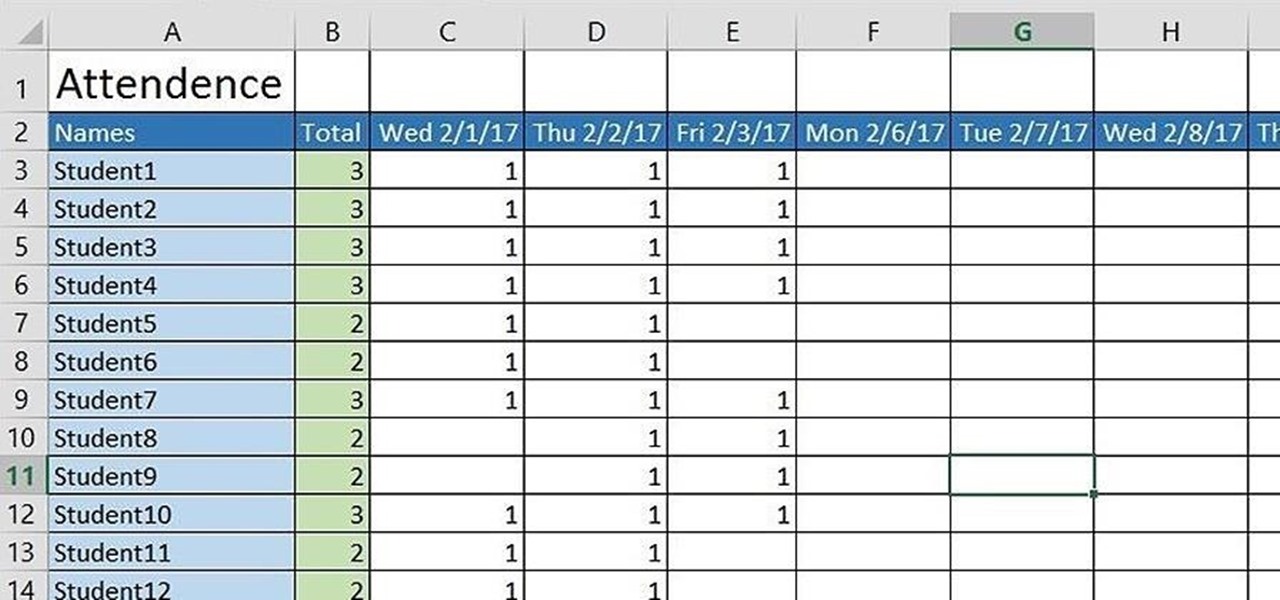
If you're a teacher in any type of school, whether it's high school, college, or middle school, it's imperative that you keep an attendance sheet. The paper and pen route can get pretty messy, and very disorganized, and that's where Microsoft Excel comes in. With this software, you can create a simple yet functional attendance sheet to keep track of your students.

There seems to be no end to all the viral TikTok sound bites and trending TikTok songs, and there's a good reason why they are ingrained in the fabric of our pop culture. TikTok's short audio clips can evoke laughter, tears, and a wide range of other emotions, and many of them just happen to be the perfect length to add to your iPhone's or iPad's arsenal of ringtones.

Google's feature drops for Pixel devices have added fun and useful new abilities, such as AR effects for Duo, Call Screen automation, scheduling Dark Mode, and Quick Access Wallet for Google Pay, that are exclusive to the company's line of smartphones.

Sending Christmas cards via snail mail is so passé. Why spend the time and money for a bougie photoshoot, saccharine card design, and postage when you can use augmented reality to instantly dress up photos and videos to send to friends and family instead?

It looks like Pokémon GO players may get a surprise gift from the game's developer, Niantic, this holiday season.

On iPhones, the share sheet is a powerful yet largely underestimated tool. For the uninitiated, the share sheet is the menu that opens whenever you tap the share button (the box with the up-arrow). This menu features sharing options to first and third-party apps, as well as extra functions like saving, copying, duplicating, and more. Best of all? It's surprisingly customizable.

Are you here yet? When will you arrive? How long until you get here? How far are you? Hurry up! When you're meeting up with someone or a group of people, you may get flooded with messages like that. Instead of trying to answer them mid-trip, you can send them your status from Apple Maps, so they know precisely when you'll arrive, and they'll even get updates if traffic is holding you back.

This time last year, Snap CEO Evan Spiegel and his company were faced with an erosion of its user base that cratered its stock price. This year, on the strength of Snapchat's AR camera effects, the company has reversed course. And that's why Spiegel tops the NR30, our annual list of the leaders in the AR industry.

Apple's latest updates to its operating systems add another security feature to its Find My service, so you have an even better chance at locating your lost iPhone, iPad, or Mac should it ever happen. As long as you have the option enabled, you can leverage other Apple users' devices to find yours on the map.

When driving, you can get directions hands-free by asking Siri. You can also make general map searches, show a location's details, call a query's phone number, and view traffic details. However, Siri defaults to Apple Maps for all those. If you prefer Google Maps, Waze, or another third-party navigation app, the map-based Siri commands won't work. But that doesn't mean you can't still use Siri.

Signaling a new direction forward for the company, Magic Leap shook up its executive suite by re-assigning to top leaders to new advisory roles. Meanwhile, a new startup backed by Hollywood executives, tech venture firms, and notable angel investors plans to bring new life to AR for marketing entertainment properties.

Hundreds of Windows 10, macOS, and Linux vulnerabilities are disclosed every single week, many of which elude mainstream attention. Most users aren't even aware that newly found exploits and vulnerabilities exist, nor that CVEs can be located by anyone in just a few clicks from a selection of websites online.

Augmented reality is becoming a slam dunk for sports entertainment, as leagues, their teams, and their broadcast partners have been quick to adopt AR.

Android does a great job at multitasking. Split-screen mode and picture-in-picture are terrific at letting you manage more than one app at a time. But there are some limitations. For instance, when you're playing a video and you open a second video in split-screen, the first one pauses. Thankfully, Samsung has a fix for this.

The road to becoming a skilled white hat is paved with many milestones, one of those being learning how to perform a simple Nmap scan. A little further down that road lies more advanced scanning, along with utilizing a powerful feature of Nmap called the Nmap Scripting Engine. Even further down the road is learning how to modify and write scripts for NSE, which is what we'll be doing today.

Apple's testing a new app for iOS 12 called Shortcuts, and it has a lot of overlap with their existing Workflow app. So much overlap, in fact, that Workflow won't be sticking around for much longer.

Extra hardware buttons have become a trend with smartphones lately. Often, these are unmodifiable buttons designed to launch a voice assistant. That isn't the case with the BlackBerry KEY2. Making a return from the KEYone is the Convenience Key, which also received an upgrade.

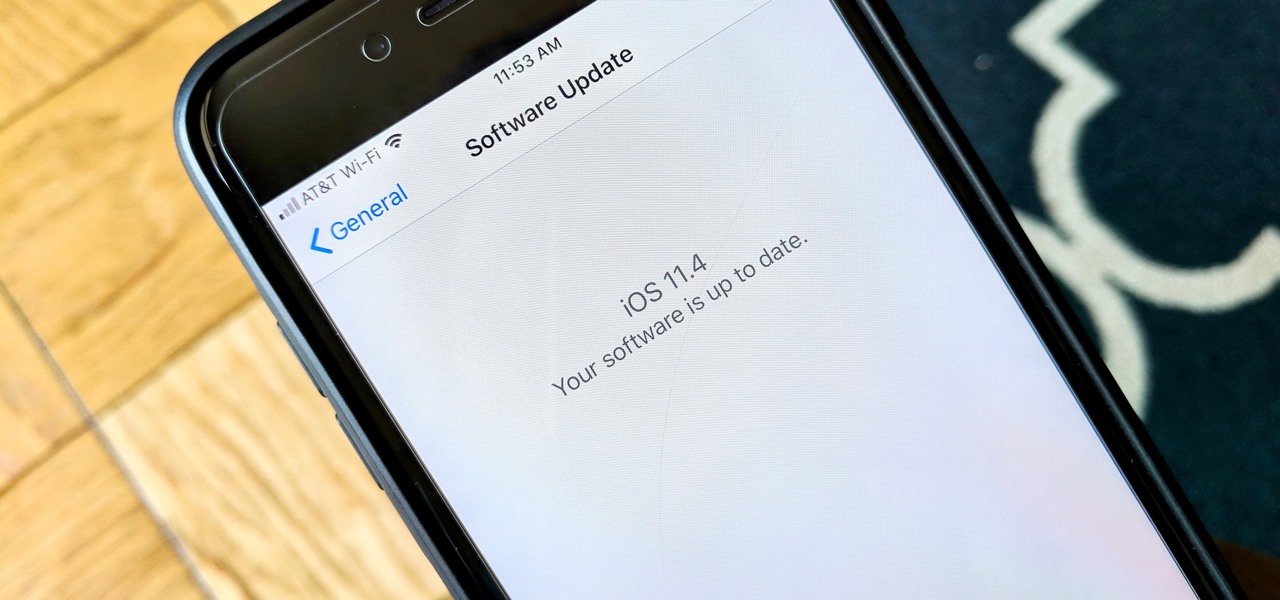
After six betas, iOS 11.4 was officially released to everyone with a compatible iPad, iPhone, and iPod touch. Some features are ones that Apple promised over eight months ago when iOS 11 was first pushed out. This update makes sense since iOS 12 will be announced at WWDC on June 4, and you can't announce a new version like that without first delivering on promises made for the one before it.

Before Google I/O 2018, the Google Assistant for Android and iOS had only two available voice options to choose from — a robotic female and male voice. But there are now six additional voices, and these ones sound way more natural than any other mobile voice assistant (plus, John Legend's voice is coming later this year).

Passwords stored in web browsers like Google Chrome and Mozilla Firefox are a gold mine for hackers. An attacker with backdoor access to a compromised computer can easily dump and decrypt data stored in web browsers. So, you'll want to think twice before hitting "Save" next time you enter a new password.

Since its introduction, the Bixby button has been a big point of contention among Galaxy fans. Many view the dedicated button as a wasted opportunity, which they argue could be put to better use if Samsung would let them use it for other commands. Thanks to an awesome app, you'll be able to remap the Bixby button on your Galaxy S9 to perform almost any function.

One of the standout features of Nova Launcher is its vast customization options. Not only does it includes numerous tweaks to alter the aesthetics of your home screen, but it even has plenty of features that reduce clutter. One area of our device that has a high potential for disarray is our home screen.

Most of us have never put much thought into this, but the question needs to be asked — what exactly happens to all of our online accounts when we die? No, the internet won't just know and delete accounts for you, so you need to plan for life's one guarantee. Because without a plan, things become a lot harder to sort out.

With the new iPhone X, Apple introduced a buttonless design for the first time. But without a home button, navigation within iOS 11 had to change to accommodate the new model. To solve this issue, Apple created gestures to perform the actions that the home button once executed. But while Apple users have to wait until November 3 to use these gestures, you can get these features right now on Android.