A deadly type of brain tumor and Zika-related brain damage in developing fetuses are devastating brain conditions that, at first glance, may seem unrelated. However, thanks to new research, their paths seem to cross in a way that could benefit patients. A new study has shown that Zika kills brain cancer stem cells, the kind of cells most resistant to treatment in patients with glioblastoma, a deadly brain tumor diagnosed in about 12,000 people in the US each year.

During the millions of years they've been on earth horseshoe crabs have developed a trick that can save our lives even now — and may be especially useful in the fight against healthcare-associated infections.

Despite longer live spans, almost half a million people die of healthcare-associated infections (HAIs) each year, many of them preventable.

Bed bugs are parasites not yet known to spread disease — but they cause plenty of irritation. As scientists and landlords search for new ways to deal with the pests, a new study examines how we can deter bed bugs without so many chemicals.
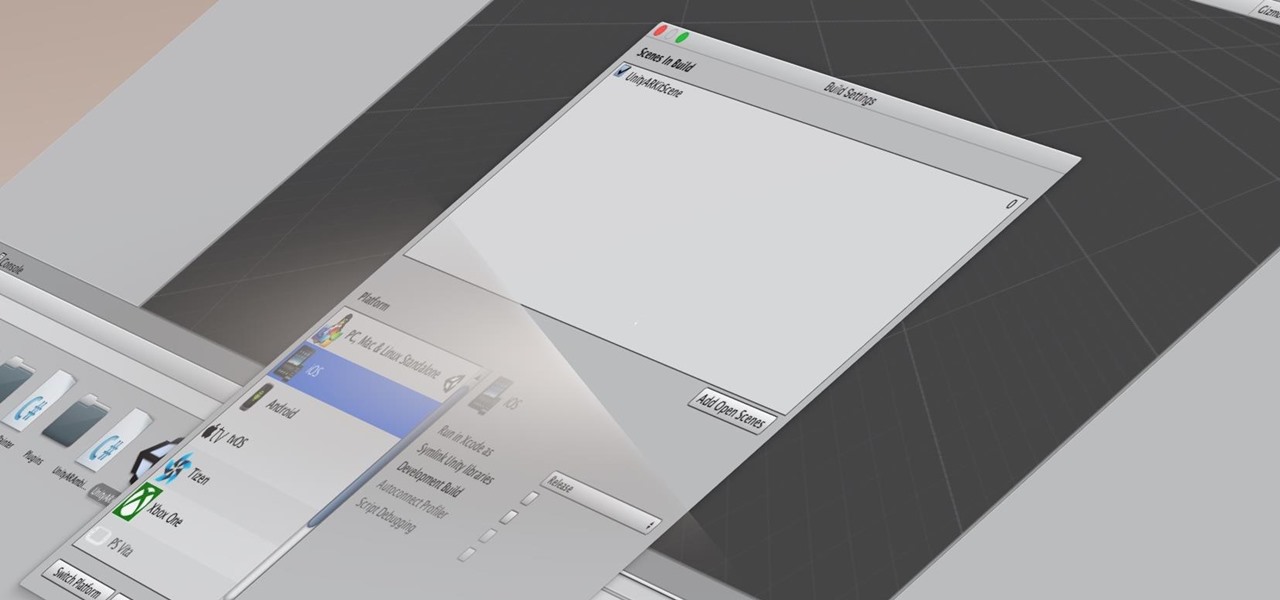
Many developers, myself included, use Unity for 3D application development as well as making games. There are many that mistakenly believe Unity to be a game engine. And that, of course, is how it started. But we now live in a world where our applications have a new level of depth.

Move over whole wheat — white bread may be back in style after a new study shows that it may be your gut microbes that decide what kind of bread is best for you.

The Galaxy S8's AMOLED display is prone to screen burn-in, particularly with the navigation and status bars. But hiding these bars would make it hard to navigate your phone — that's where Pie Controls come into play.

Sometimes it's impossible to concentrate — let alone direct your personal assistant Siri — when someone is blasting music on their phone or talking to thin air. I mean I'm loud, but not that loud.

Think of the coolest, most unique way to create art that you can. Got it? Now think about creating that art out of living things.

In a disturbing turn of events, Uber has been tracking oblivious iPhone users even after they removed the application from their phone. Two years ago, the situation escalated to such an extent that CEO Travis Kalanick earned a slap on the wrist from Apple mogul Tim Cook.

In the past, infection with human immunodeficiency virus (HIV) commonly led to dementia as the virus made its way to the brain. Even in effectively treated people, HIV can hide out and replicate in places like the brain, where it's tough to detect. That's why it's very concerning that half of all HIV-infected patients still report cognitive problems.

The modern age of techno-dating has made an interesting landscape for social interactions when there is some modicum of romance (or lust). For those of us born before the internet evolved into the prolific monster it has become, we first met our love interests face to face. Today, however, apps like Tinder have changed the introductory stage, for better or worse.

At this point in our series on creating a customized hacking container, you should be able to use Docker to save and retrieve customized instances of Ubuntu from your own machine. Make sure to revisit part one and part two if you need a refresher.

In Pokémon GO, having an in-depth understanding of your Pokémon's stats and abilities is crucially important to becoming a better player. Not all Pokémon are created equal; as such, it's critical that you look at each of your Pokémon—even duplicates—with a keen eye.

Fast food is a guilty pleasure in which we all indulge. When you're short on time and long on hunger, being able to whiz through the drive-thru or run 'in and out' of a fast food joint can be a real lifesaver.

Welcome back, my rookie hackers! The Golden Fleece of hackers is to develop a zero-day exploit, an exploit that has not been seen by antivirus (AV) software or and intrusion detection system (IDS). A zero-day exploit is capable of skating right past these defenses as they do not contain a signature or another way of detecting them.

Welcome to a tutorial on XOR encryption. We'll be looking at what XOR is and how we can use it to encrypt or decrypt data.

This is my first How-To on Null-Byte, so I hope it's not too complicated written, because I am not a native english speaker. I don't use pictures, but this Tutorial is a good supplement for my updated Tutorial here.

Welcome back! In the last training session, we covered logical and membership operators. We're going to switch gears and expand our knowledge of lists.

Not many people use their phone exclusively for making calls or sending messages today. If you're an Android user, the chances are high that you're using your phone or tablet for work-related activities. However, the basic set of apps and services your device was shipped with won't satisfy most users. The good thing is that Google Play Store has a nice selection of productivity apps for every task. Below you'll find a list of apps that will help you gradually optimize and organize your digita...

I think it was 1986 when I first discovered my love for making computers say stupid things out loud. My older brother got a Commodore 64 for his birthday, which came bundled with software that would speak out any term you typed in—and boy, that computer sure made a fool of itself after my five-year-old imagination got a hold of the keyboard.

As many of you know, processor's clock frequency improvement got stuck in about 2003, causing the origin of multicore CPU (and other technologies). In this article I'll introduce you on how to run code simultaneously in various processors (I suppose that all of you have a multicore CPU). When you write code without any parallel directive, it only executes in one CPU at the same time (see it below). OpenMP make simple to work with various cores (if not with all of them) , without so much heada...

In the last iteration of how to train your python, we covered the concept of control flow and covered the booleans associated with it. Today, we'll be putting those to use as we discuss how to use if, else, and how to make conditional statements. So, Let's get started!

WPA Enterprise is widely used in large corporations as it offers individual and centralized control through a server that authenticate the users (RADIUS server). In this tutorial I will show you how to break the barrier and obtain the user credentials.

Reddit, the self-proclaimed "front page of the internet," continues to take a big bite of my free time each and every day, as well as millions of its other users'. The clicking and scrolling through page after page never gets old, but you could speed things up with a few browser extensions and double your Reddit knowledge in half the time. Here are my favorite extensions you can try out for the Chrome, Firefox, and Safari web browsers.

Only three things in life are certain: death, taxes, and getting a dent in your car or truck. Even if you're as careful as possible, you can't always account for runaway shopping carts, wrongly thrown footballs, out-of-nowhere light posts, and other real-life annoyances.

Hi nullbytes! I've been recently reading the whole Linux Basics for the Aspiring Hacker series and felt like it was missing some stuff I know, so I felt like sharing it with anyone who might find it useful too.

Welcome back, my rookie hackers! "How can I travel and communicate over the Internet without being tracked or spied on by anyone?" It's a question many Null Byteans have asked me, so I have decided to write a comprehensive article addressing this issue.

Welcome to the first chapter of Excel is Simple, a place where we will burst all myths around excel and try to make it simpler and fun to use.

There's a never-ending selection of app launchers that want a permanent spot on your Android device. While some keep the stock-Android look with beefed-up versions of Google's launcher, Blur is relatively new on the scene, with a unique approach to app management that sets it apart.

Security is a priority for many when they first set up their mobile devices. Nobody wants to have a stranger or nosey friend go through their phone and discover risqué photos or embarrassing text messages. These days, the closet is gone—everyone keeps their skeletons in their phones.

It's the biggest day of the year for all things Google. Their developer conference, dubbed Google I/O, gives us a peak at what the guys at Mountain View have been working on over the course of the past year, and this year, Android was center stage.

Safari has some cool new features in iOS 8, but the app that seems to have gotten the biggest update so far is Messages. A lot of the new Messages features were discussed during Apple's developers conference, but we found many others and picked out our favorite hidden ones below.

Like Costco's price codes or the tags on your bread, the numerical codes printed on those sticky little fruit and vegetable labels can reveal a lot of information to us consumers. Once you understand the codes, you can look at that little label (also known as PLU, or "price look up" label) and know whether the produce you're about to buy or eat was treated with pesticides, genetically modified, both, or neither. Before we go any further with deciphering the codes on these labels, let's take a...

Phantom phone vibrations. You might feel them in the pocket of your jeans, or when your handbag is on your shoulder—even when you're holding your phone in your hand. When you do, you immediately wake it up to see who texted or what app just had an update—but there are no alerts.

The point of ice in your cocktail is to make it cold, right? Yes and no.

It's easy to take the food we eat for granted, but the truth is, there are a lot of bizarre, wonderful, and just plain weird things about what we eat and drink, the effects it has on our bodies, and vice-versa. Read on to learn how bugs provide food dye, the Japanese grow square watermelons, and more.

In today's dog-eat-dog world, every minute matters. Whether you're in school or working for the Man, a huge amount of your day is consumed by tasks, assignments, and other kinds of work. Then there's the time you spend playing video games, watching TV, or screwing around on your Samsung Galaxy S3.

Welcome back, my hacker apprentices! Several of you have written asking me how you can check on whether your boyfriend, girlfriend, or spouse is cheating on you, so I dedicate this tutorial to all of you with doubts about the fidelity of your spouse, girlfriend, or boyfriend.

Recently, there have been some questions regarding networking popping up and we have decided to put together this series to try and cover this gap.