Did you know you can help protect yourself when traveling with a gun? No, not like that; and not in any way that's going to land you in prison. Simply by packing a gun, you can ensure that not only will your luggage be safer, but that the airline will make certain that it reaches its destination. Photo by Alamy

The only things that will get you into a good college is persistence, a will to learn, and of course… grades. If your grades are lacking that oomph they need to impress the schools and your parents, there's a few ways to aid in improving your scores. With a little effort and focus, your next report card will sport better grades.

If you think that card counting is only a thing in the movies then think again. You too can try a couple of methods to help you count cards. Like anything, the more you work on it the better you will be.

There're plenty of great ways to get traffic, especially this off-site optimization technique using classified ads to point website traffic back into your site itself.

Is a Bridezilla driving you crazy? Whether the bride gone wild is your sister, daughter, or BFF, you can stop the insanity. Here are some tips offered on how to deal with an out-of-her-mind bride.
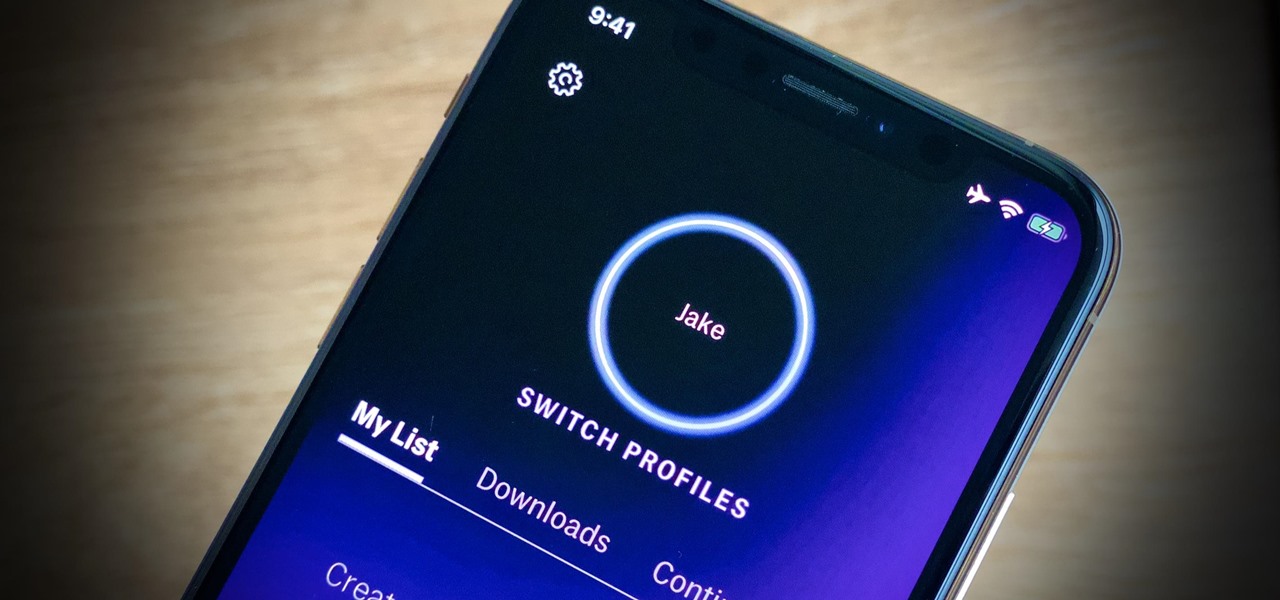
Many streaming services offer user profiles for different people in your household, some of which also include profile images. In most cases, you can set a custom profile image to better differentiate and personalize your account from the others, and HBO Max lets you do the same, albeit, with limited options.

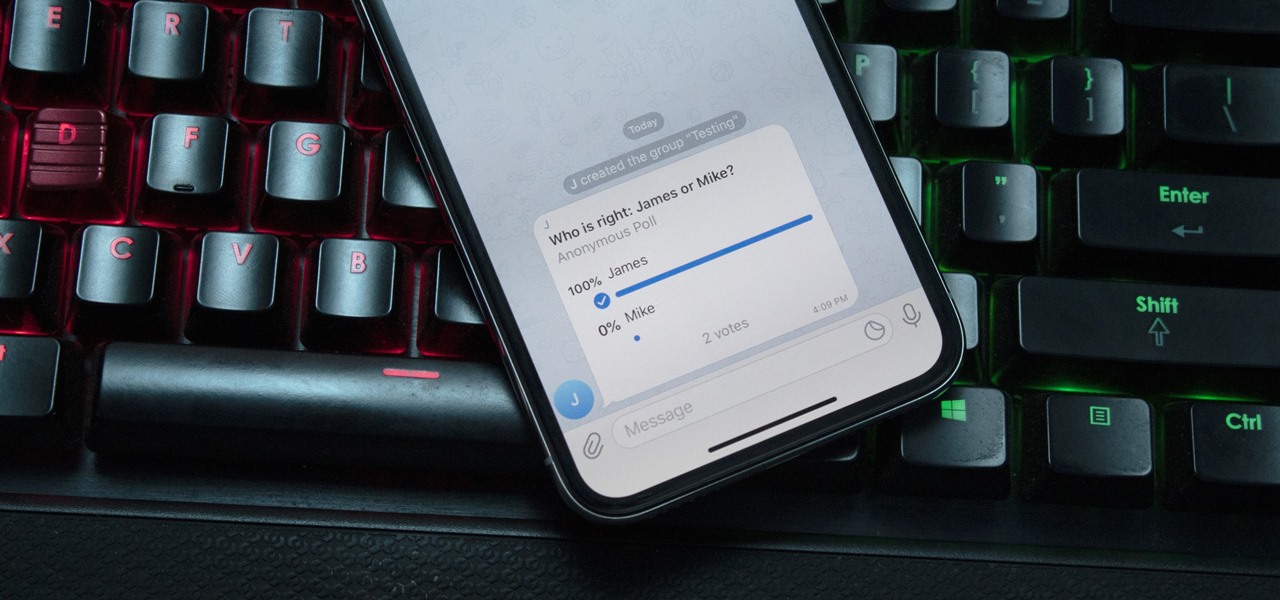
With group chats, arguments tend to devolve from a dispute between two people to a giant debate amongst all members. But before things get out of control, Telegram has a feature that can help.

The Alt-Tab keyboard shortcut makes switching between apps and programs a breeze on your Windows PC. Just like your computer, your Android phone has the same feature baked in to make switching between recent apps just as hassle-free.

The rise and fall of Meta, the Silicon Valley-based augmented reality startup that looked to challenge the likes of Microsoft's HoloLens, and others, took just six years.

Samsung's version of Android Pie has landed on Galaxy handsets like the Note 9, S9, and S8, though we've known what to expect thanks to leaked beta versions of the software a few months back. The newly dubbed One UI has plenty of new features and improvements, but some of the first you might notice are the visual improvements to the default messaging app.

Microsoft has informed HoloLens users that the company will begin rolling out a mandatory update for HoloLens as part of its Windows 10 October 2018 release that brings a number of new features and quality-of-life improvements to the headset.

Don't think because your MacBook is using FileVault disk encryption your device is secure or immune to hackers. Here's how to find out if that FileVault password is strong enough to withstand an attack from a motivated attacker.

Location services company Mapbox has added new capabilities to its location-based gaming tool to fend off Google's challenge for the same mobile app category.

When it comes to augmented reality apps, visually immersive experiences are plentiful, but audio experiences are somewhat underrepresented. A new app for iPhones and iPads seeks to shift the AR paradigm toward the latter.

PowerShell Empire is an amazing framework that is widely used by penetration testers for exploiting Microsoft Windows hosts. In our previous guide, we discussed why and when it's important to use, as well as some general info on listeners, stagers, agents, and modules. Now, we will actually explore setting up listeners and generating a stager.

When we are building programs that communicate over a network, how can we keep our data private? The last thing we want is some other lousy hacker sniffing our packets, so how do we stop them? The easy answer: encryption. However, this is a very wide-ranging answer. Today we're going to look specifically at how to encrypt data in Python with dynamically generated encryption keys using what is known as the Diffie-Hellman key exchange.

Your iPhone might have a great camera, but it can be irritating to get things like exposure and focus right when your fingers are all over the 'viewfinder.' The Pictar aims to change that by making your iPhone as much like a DLSR as it can, keeping your fingers from obstructing your next great photo.

Yes, they're called volume keys, but they can do much more than adjust your volume. With minimal effort, you can do some amazing things with these physical buttons, like secretly record videos, toggle on your flashlight, scroll through pages, control your music, and much more. And while using them to wake your screen is useful, let's take it a step further and show you how to use them to completely unlock your device, even if the screen is off.

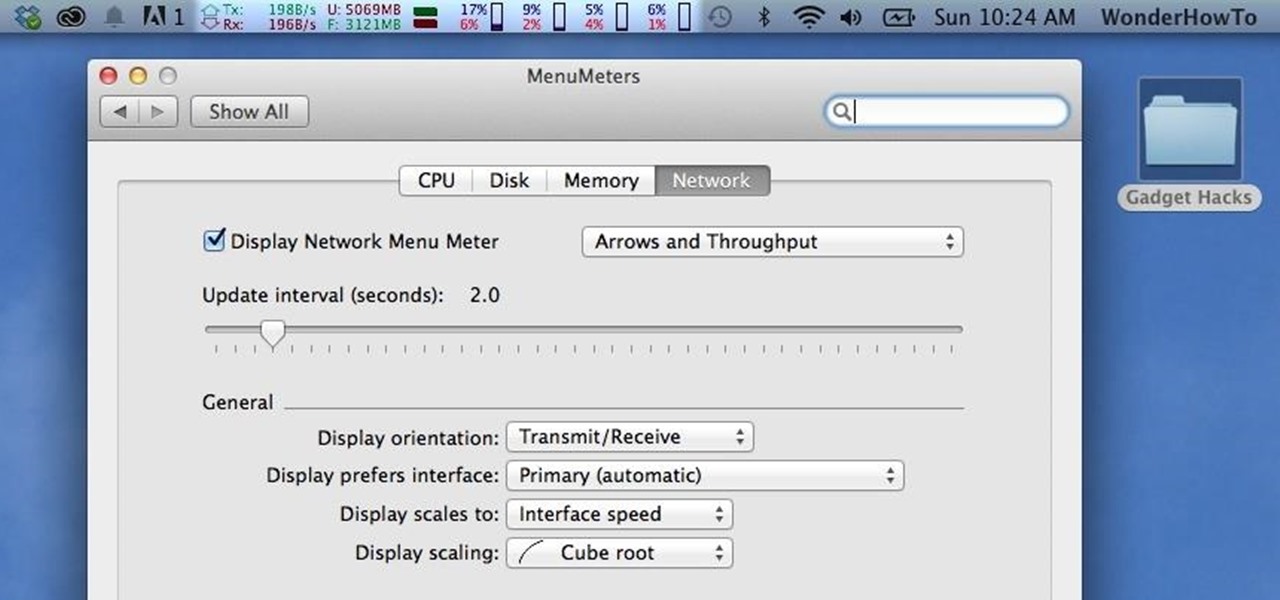
Like a car, your Mac needs to be monitored and cared for to keep it running as smoothly as possible. While your vehicle comes with a ton of gauges to keep track of your oil, temperature, and in some cases, even tire pressure, your Mac has no easy way to watch for low memory or high disk usage. Normally you would have to open up Activity Monitor to take a look at your usage stats, but now there is something better.

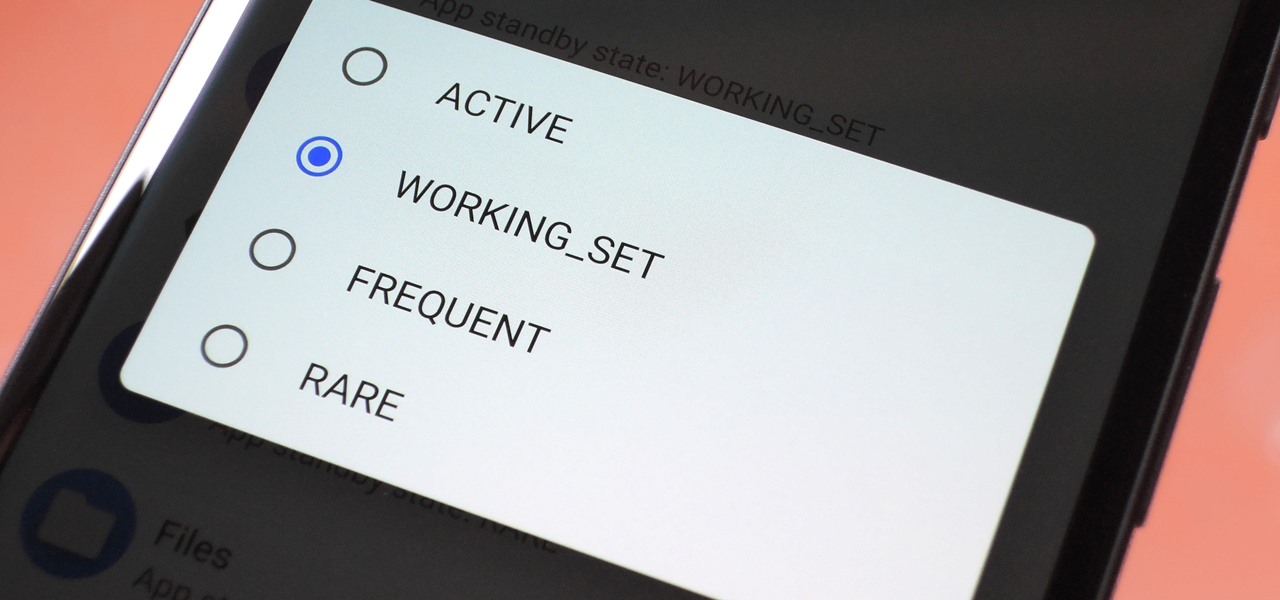
Even though there are over 1.3 million apps available for Android, we normally confine ourselves to a select few for day-to-day usage. With an average of 41 apps installed per user, most apps on our smartphones lay idle for the majority of the time we spend using them. Instead, we find ourselves constantly coming back to that small set of apps that meet almost all of our needs.

Taking pictures, sharing your location, and making calls are easy enough to do with an Android device, but for the most part, they all require your screen to be on with some sort of swiping and pressing actions. Dedicated shortcut keys are virtually non-existent on any modern day phone, but their utility is something that can be very useful.

Configuring user accounts is extremely important for those with a family shared computer or anyone using a work computer. Assigning different accounts with their own distinctive accessibility, customizations, and applications is the best way to manage a computer with multiple users.

Windows 8 the biggest update to Windows yet. The new gesture-friendly version replaces the aging start menu with a dynamic new Start Screen, complete with live tiles that give you a glimpse into your apps before you launch them, not unlike the new Windows phones. With such a radical departure from the past, some familiar features have been moved around, which will take some getting used to. It's worth noting that the new Windows 8 does not abandon the old desktop model completely; it still ha...

An isomorphic (or self-transposing) keyboard is "a musical device where a grid of notes is displayed to the user and the interval change between notes in constant for any given direction." For those of you who didn't grow up playing the piano like I did, that basically means that it lets you move between keys easily without having to learn new patterns because the keys are laid out so that a chord is the same pattern in every musical key.

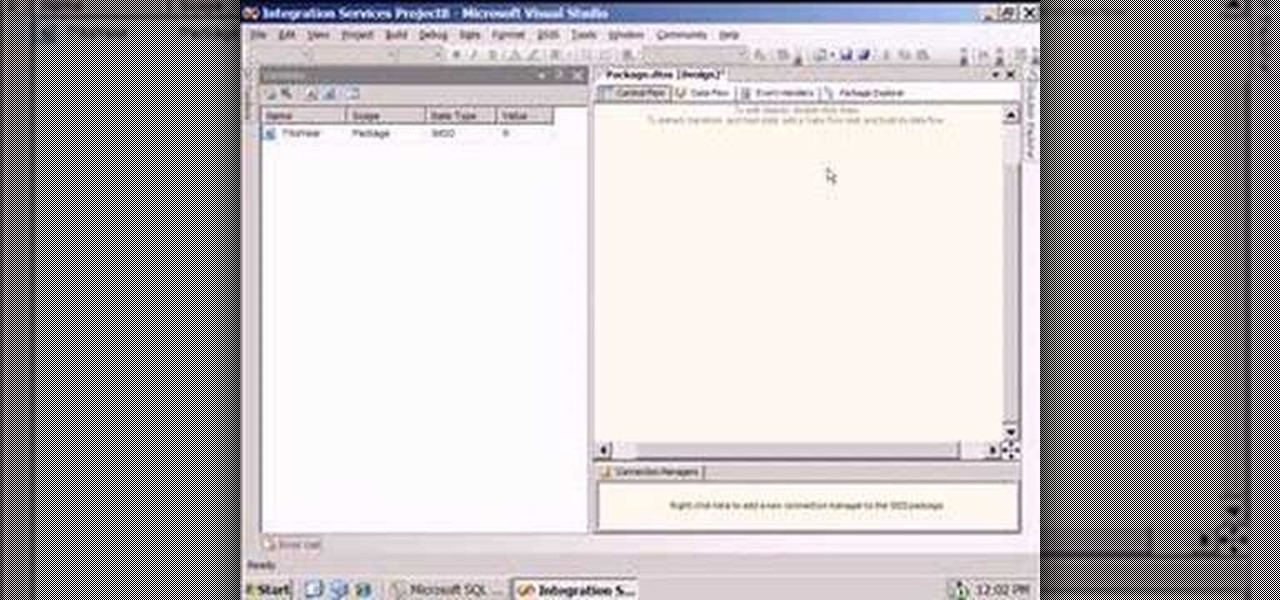
Expressions are new in SSIS (meaning that they were not in DTS) but they allow you to create extremely flexible packages. Expressions can be used to assign values to variables, help you determine whether to execute a task, and to assign properties. If you ever found yourself writing ActiveX code (VBScript) in DTS to determine which task to execute based on a variable's value, then you probably can forego the scripting all together in favor of expressions! They are very powerful in SSIS and yo...

The yoga cactus arm movement helps establish stability underneath the shoulders and upper arm area for inversions and back bends. This yoga how-to video demonstrates how to use the cactus arm movement to transition into cigarette girl action. Cigarette girl action is a name that Kira Ryder, our yoga host, has assigned to a movement she uses in her yoga classes. Watch and learn how to transition from cactus arms into cigarette girl movements in yoga.

You don't need flying broomsticks or magic balls to play this version of the game – it's tailor-made for muggles like us.

When joining a new network, computers use the Address Resolution Protocol to discover the MAC address of other devices on the same network. A hacker can take advantage of ARP messages to silently discover the MAC and IP address of network devices or actively scan the network with spoofed ARP requests.

With a simple social engineering trick, sudo passwords can be captured in seconds without the target's knowledge. The passwords can then be saved to a file or exfiltrated to another computer on the network.

Until very recently, Apple apps were among the only ones that would play nicely with Siri on iPhones. If you wanted to take advantage of the digital assistant to, say, compose an email, you would need to go with Apple Mail instead of the email client you actually use. As of iOS 12, this is no longer the case.

Battery drain is a major pain point for Android users, though that promises to change thanks to Android Pie's new Adaptive Battery feature. But Google hasn't said much about the inner workings of this feature, only publicly stating that it uses AI to boost battery life. So we dug in to find out what's really going on under the hood.

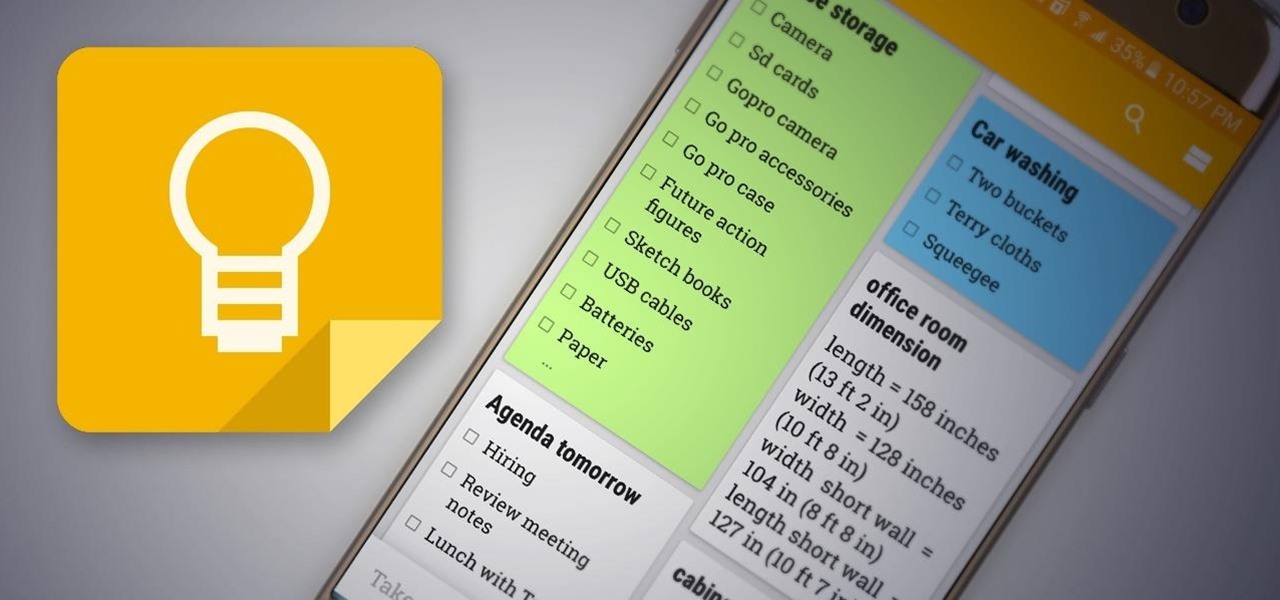
When it comes to note-taking, Google Keep is one of the most diverse and functional applications on the Android platform. Sure, there are a plethora of other note-taking apps to choose from, such as ever popular OneNote and Evernote, but Google Keep differentiates itself from the crowd with its user-friendly interface and Google Now integration.

If your iPhone has a Home button, such as either iPhone SE model, old or new, then it has a secret triple-click gesture to activate a suite of shortcuts. These options, dubbed accessibility shortcuts, can work wonders for folks that are hearing impaired, have limited use of their hands, or have vision problems. Still, the shortcuts have plenty of everyday applications that everyone should know.

Hey guys, in this tutorial, we are going to learn about the heap segment and how to use it for storing data in our programs. We will also go into the details of its use in conjunction with the char pointer and struct data types.

Welcome back, my greenhorn hackers! As expected with Null Byte's dramatic growth over the last year, we have added many new aspiring hackers who are still lacking in the basics of networking. In addition, with the new "White Hat" certifications coming out shortly, the exam will require some basic networking skills and knowledge to pass.

In the last iteration of how to train your python, we covered if/else and conditional statements. We're going to diverge a little today and cover lists. Lists are simply that, lists. It is a set of values located under one variable. Now that we know the definition of a list, let's learn about them! List Basics

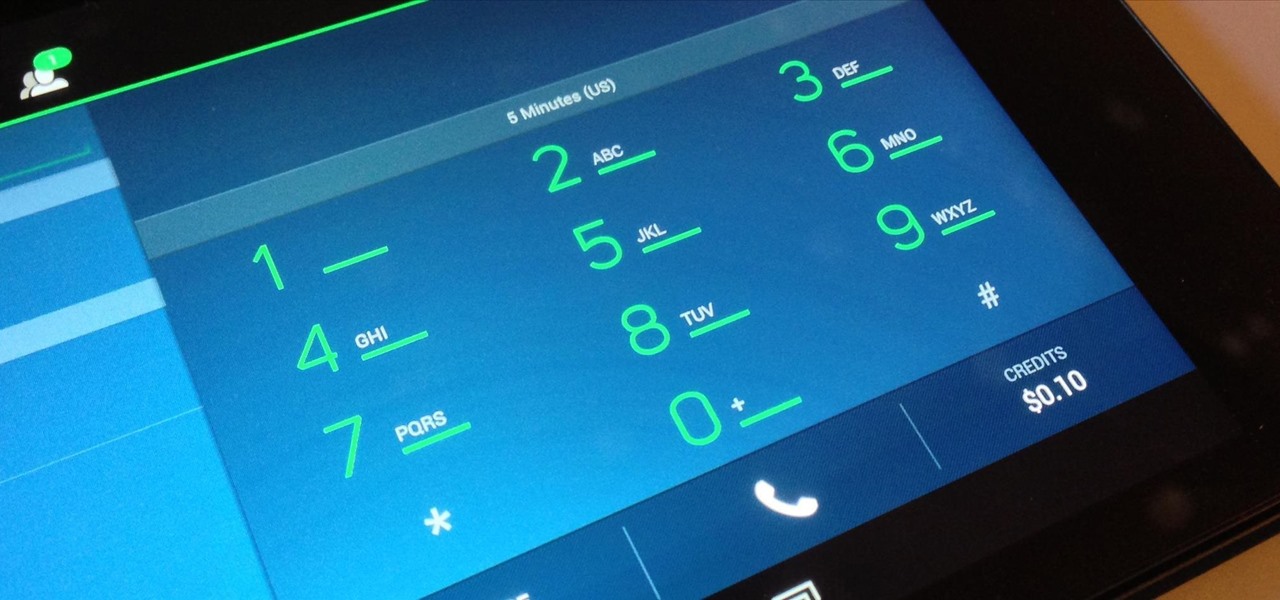
Your Nexus 7 may be a tablet, but it can also be used as a phone, thanks to the continued upswing of VoIP applications, which send voice and media messages over the Internet—not over a cellular network.

So, you're browsing the web on your iPhone using Safari, and you come across a picture you really want to keep forever and ever… what do you do? You can save it directly to your phone! But how do you download that web image? Best Buy has answers. The Best Buy Mobile team explains how simple it is to save web images from Safari on your Apple iPhone.

Impress your friends by actually knowing what to do with those darts—other than winging them toward the wall—next time you're at a bar.

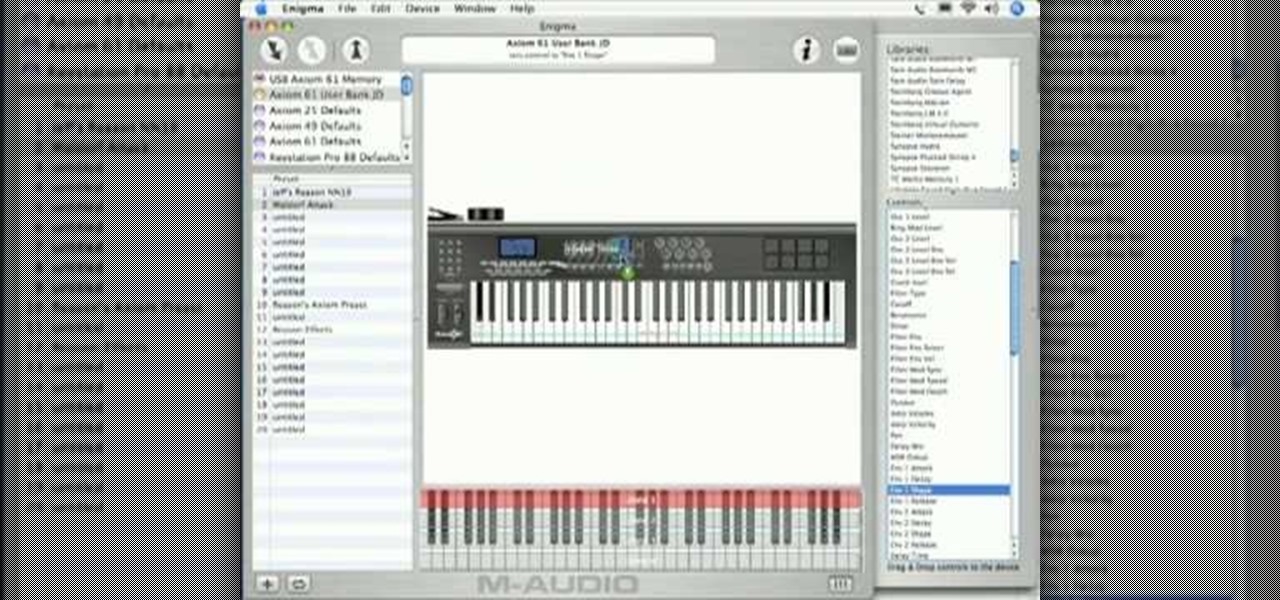
In this tutorial, Jeff Dykhouse demonstrates how to use the powerful Enigma Editing Software to assign MIDI message to all the different controllers that the Axiom 61 keyboard has at its disposal. Jeff covers: Downloading Presets, Creating User Banks and Loading and Creating Presets. You can use the Axiom 61 with Reason, Ableton Live, Pro Tools and even GarageBand.