Many operators use elevators to control access to particular floors, whether it be the penthouse at a hotel or a server room in an office building. However, the law requires them all to have a fire service mode, which gives emergency access to restricted floors, and a hacker can use that to bypass security altogether.

Analysis of photographs and social connections can be a huge component of social engineering. Understanding who a person is, as well as who they know, can establish links within a company. This information could be used by hackers to execute elaborate social engineering attacks.

Chrome is the browser of choice for millions of iPhone and Android users, largely thanks to its user-friendly interface and native Google support. But with concerns over sharing private information with massive companies growing, many people are starting to want a little less Google integration in Chrome.

As you're surely aware, your phone can be used against you. Thanks to our cameras and microphones, a clever hacker can obtain access to your device and invade your privacy. But spying isn't limited to just these two sensors — gyroscopes, proximity sensors, QR codes, and even ads can be used to paint a very clear picture about who you are and what you're currently doing.
If you're a console or PC gamer, you may be quick to ignore the mobile version of Fortnite Battle Royale. The lower graphics and the switch to touchscreen controls may be enough reason to dismiss this version of the game. But don't be so quick to judge — there are actually some clear advantages to playing on mobile.

Using just a small sticky note, we can trigger a chain of events that ultimately results in complete access to someone's entire digital and personal life.

Your dog is doing something charming, and you need to take a quick photo, but you don't have time to search in your app drawer for the camera app. The moment would have long passed by the time you find it. What if instead you could you open the camera or any other app simply by sliding your finger down on the home screen? Well with Nova Launcher and gestures, this is easy to accomplish.

Spotty cellular reception is a fact of life that we all have to deal with, especially when you're traveling. For those of us who rely on our smartphones for navigation, driving through areas with bad mobile data service can be a cause for major headaches.

Cancer cells do a pretty good job of flying under the radar of our immune system. They don't raise the alarm bells signaling they are a foreign invader the way viruses do. That might be something scientists can change, though.

Flu vaccines can help prevent us from getting or suffering the most severe effects of the flu. But, each vaccine only protects us from three different strains of the flu. If we don't have a vaccine against all types of flu, it leaves us open for an epidemic with a flu virus we didn't expect.

Bed bugs are brown and creepy. Could you spot one in your hotel room? A new study reveals most people are freaked out by bed bugs, but only about 35% could identify one.

This week's Market Reality covers a variety of business news from acquisitions and partnerships to competitive and technology assessments to quarterly financial results.

Most of us skip through documents like privacy policies and EULAs (end-user license agreements) because they're long and boring. But, as Congress just passed the SJR34 bill in early April, you're probably a little concerned about your personal data, so we summarized the privacy policies for major ISPs and mobile carriers in the US.

At the moment, it would be safe to say that demand for devices running Tango, Google's augmented reality smartphone platform, is relatively low among consumers. Kaon Interactive, a B2B software company who has built more than 5,000 interactive applications for use at trade shows, remote sales demonstrations, and other customer engagements, is betting that there is a market for the devices in sales and marketing.

Welcome back, my nascent hackers! In the conclusion of the Mr. Robot television series, Elliot and fsociety successfully completed their mission of encrypting all of Evil Corp's data with AES-128 encryption and destroying the key.

Greetings all. Before I get into the tutorial, I would like to mention that I am fairly new to Null Byte (been lurking for some time though), and what really appeals to me about this place is its tight, family-like community where everyone is always willing to help each other and the constant search for knowledge that inhabits this subdomain is a driving motivator for me to join in. I'm glad I arrived at the right time. Anyway, wipes tears (not really)...

Hello everybody Joe here. Today I will be demonstrating how you can find XSS vulnerabilities in a website and what you can do with them

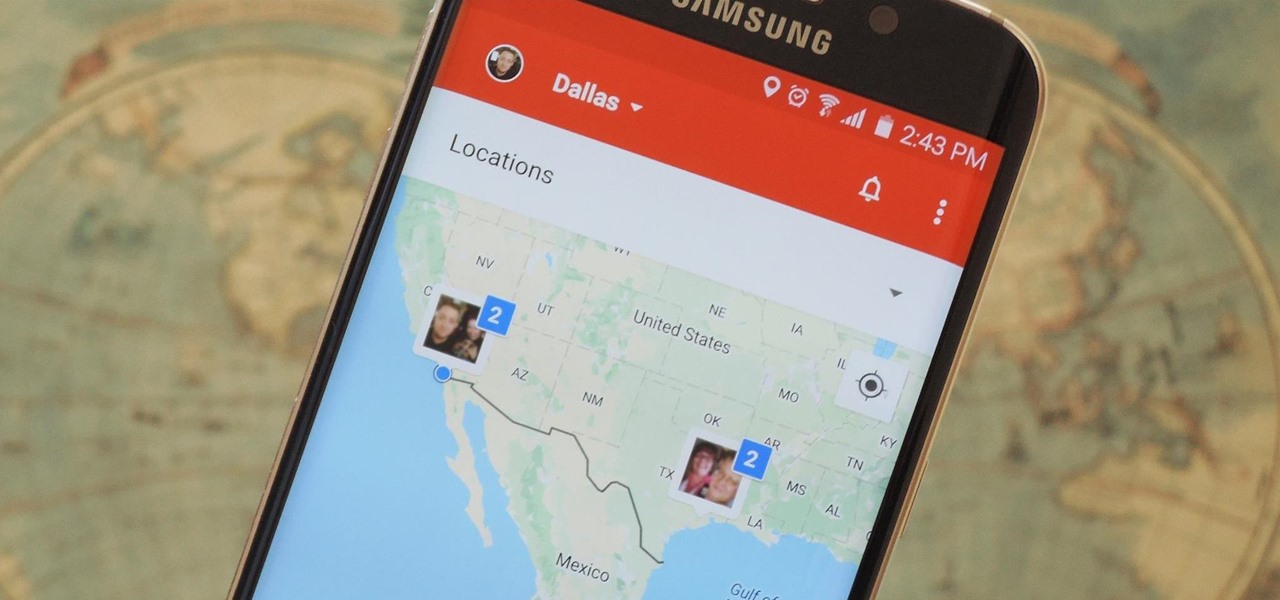
Instead of wasting time asking where your friends and family are at a given moment, then having them waste time by describing their location, there are several Android apps you can use that will automate this whole process. To top it off, it doesn't have to be about invading privacy or spying on someone, since most of these apps are offer two-way location sharing, or at least let you share locations only when you feel comfortable with it.

Welcome back, my budding hackers! When we are looking for ways to hack a system, we need a specific exploit to take advantage of a certain vulnerability in the operating system, service, or application. Although I have shown you multiple ways to exploit systems here in Null Byte, there are still many more exploits available that I have not yet shown you.

After many beta builds, Apple has finally released iOS 7.1 to the public. It includes bug fixes for the old iOS 7.0.6, along with UI enhancements and even some new features.

While Siri has never been my favorite, after using her in the new iOS 7, I have definitely become a fan. If you want to know why, check out the newest cool features that Siri has to offer!

Apple is widely known for keeping a tight grip on iOS, disallowing open-source and third-party downloads. While there are many reasons for this, the three most frequently referenced are quality control, malware prevention, and of course—money.

The new Samsung Galaxy S4 just received an update to Android 4.2.2, so why is it that my Galaxy Note 2 is still running an older version of Jelly Bean? It felt like yesterday that my device was finally updated to 4.1.2, but why even bother since 4.2 has been around since last November?

When someone says, "draw a box in Illustrator" you instinctively reach for the box tool and drag out a box on the page. However, if you need to create the box with a specific size then you need to know how to draw by the numbers. Use the drawing tools in Illustrator CS2 to draw shapes at specific sizes.

Kits are something your character might come across while playing Star Trek Online - special items which will augment or improve your character's specific skill set. This short video explains what kits do and how you find and use them.

In this tutorial, we learn how to change the engine oil in a Chevy truck. To start, you will want to place your car up on a secure jack so you can get underneath it with ease. Next, find the oil can and drain plug underneath the truck and use a wrench to remove the bolts around them. Now, place an oil pan underneath the drain plug and let the oil leak out into this until there is no more left. Next, clean off the bolt that is used for the drain plug and remove the filter from the underneath o...

If you just got a new Android mobile phone, then chances are, the first thing you're going to want to set up is your email account, so you have instant access to your emails all the time, everywhere and anywhere. Setting up your specific email account or accounts is actually not hard. Best Buy has answers. The Best Buy Mobile team explains how simple it is to set up an email account on an Android cell phone.

Learning the blues isn't an easy task, but this video helps make it a little easier. The song you'll be learning is "Coffee Blues" by Mississippi John Hurt. It's in the key of A and is a typical blues progression, in an alternating bass. It's the chords A, D, and E. If you're yearning to learn the delta blues, this is a great first step.

This is a tutorial on how to replace the screen on your ipod touch. This video is specific to the third generation ipod touch. You can tell if your ipod is a third generation because it only has two lines of writing on the back bottom. To begin use a safe open pry tool to open the ipod touch. Run the tool between the metal chrome frame and the glass digitizer. There are many clips on all sides and they all need to be released. Begin prying at the bottom and then work your way to the sides. Wh...

The video describes the making of Paper doll dress up and a Tin Purse to put the dolls inside. You can use the cartridge paper but regular paper should do. She was sticking to the princess themes in this tutorial. The tin comes from provocraft but creative imaginations also offers one. Instead of purchasing a tin you can find a old tin purse maybe once for a over sized set of playing cards. There is a tab feature you can use on the dolls but which children the might come off. She suggests usi...

This video teaches how to change Windows 7 accessibility options. Choose Start, Control panel. This opens the Control Panel window. Choose Ease of Access in the control panel window. This opens Ease of Access window. Inside the Ease of Access window, there are various links that allows you to set various accessibility options in windows 7. You can use these settings for options like "Optimizing Visual Display", "Replace sounds with visual cues" and you also have settings to choose how the way...

Dale Warner shows us how to get rid of PMS cramps in about 10 minutes. It's an easy, natural, effective and free approach.

Do you wonder if what you are seeing on your trees or plants is a problem, or simply natural? John White and Lois Pierce discuss various issues with Manzanitas, Red Buds, Viburnums, Mexican Buckeyes, and Cacti.

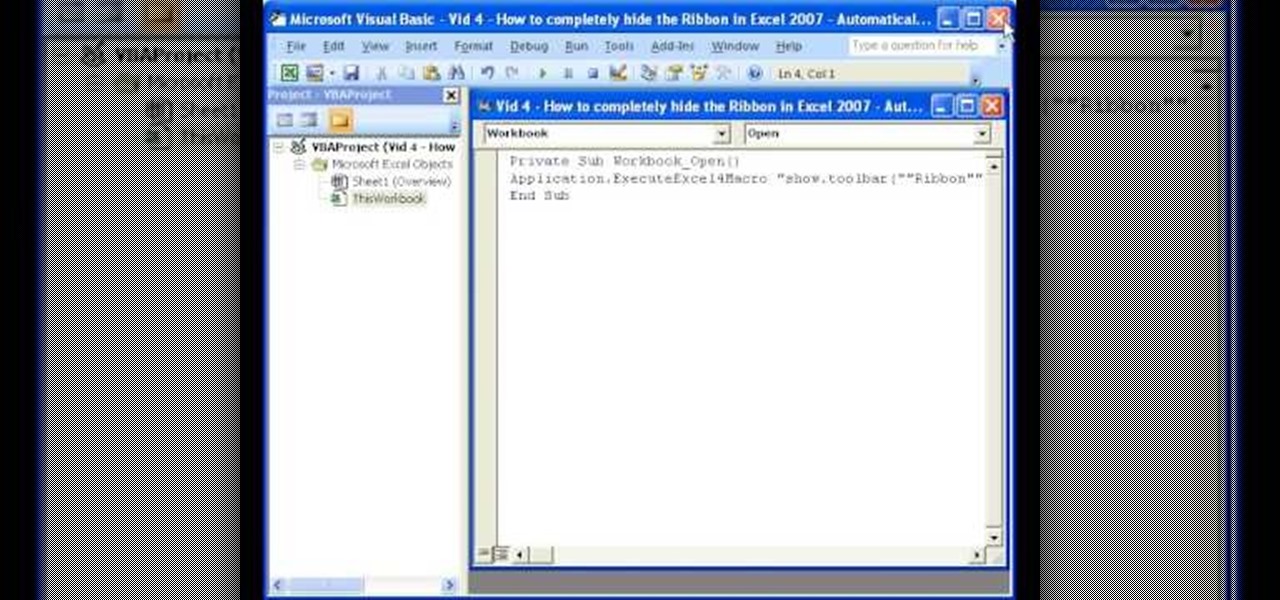
Teach Excel demonstrates how to completely hide the Ribbon menu system in Excel 2007 as soon as the workbook is opened. This will be done by writing a macro which hides the Ribbon only for the specific workbook in which the macro is implemented. Some helpful shortcuts are Ctrl+F1 which partially hides the ribbon, Alt+F11, which opens the Visual Basic screen, and Alt+F8, which opens the macros list. First, hit Alt+F11 to open the Visual Basic screen. Then double-click "This Workbook" on the le...

New to Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this Excel tutorial from ExcelIsFun, the 237th installment in their series of digital spreadsheet magic tricks, you'll learn how to

You don’t need to be in the gym to get super toned arms and legs. Stay outdoors and with only an exercise band you can get a difficult and muscle specific exercises that will turn any arm flab into defined muscle.

This video will go over how to insert a check box in Microsoft Word for printing or for electronic distribution. With just a few clicks you can get a check box. You can even add different symbols or styles for your check box.

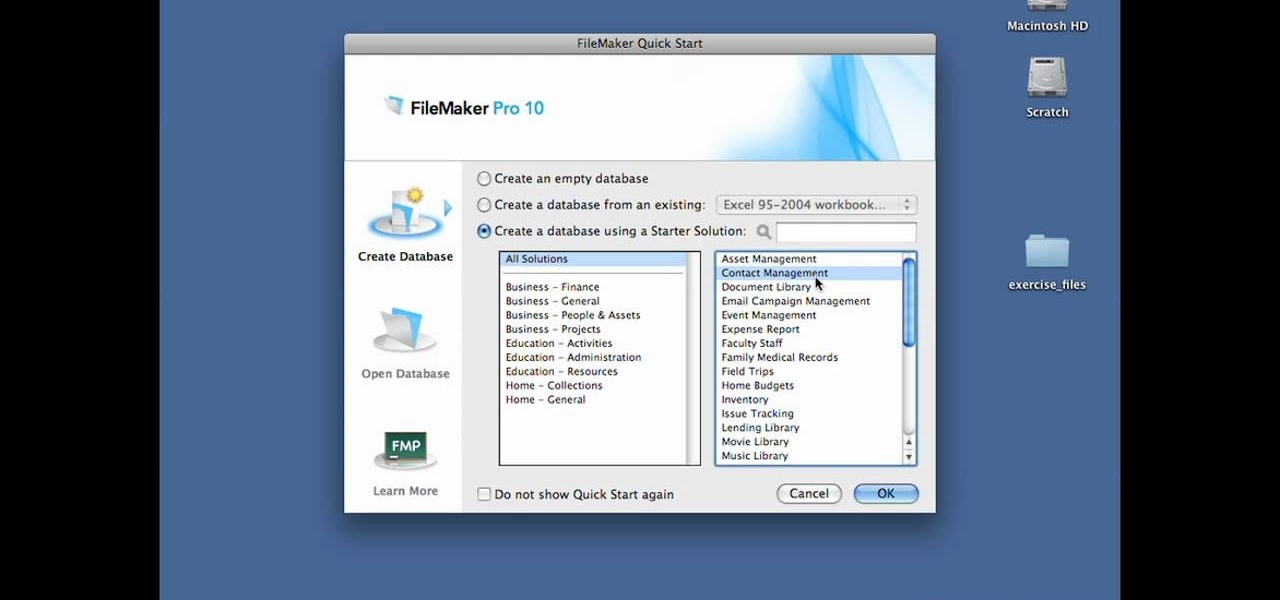
In this Lynda video tutorial, learn how to use FileMaker Pro 10 software to create databases with pre-made templates. FileMaker offers these templates in a package called Starter Solutions. To access these options, click open FileMaker. Then, go to New Database under the File menu. Click the option "Create a database using a Starter Solution." The templates are grouped according to the nature of their use. Some are for the home, while some are for business. All you do is open the template you...

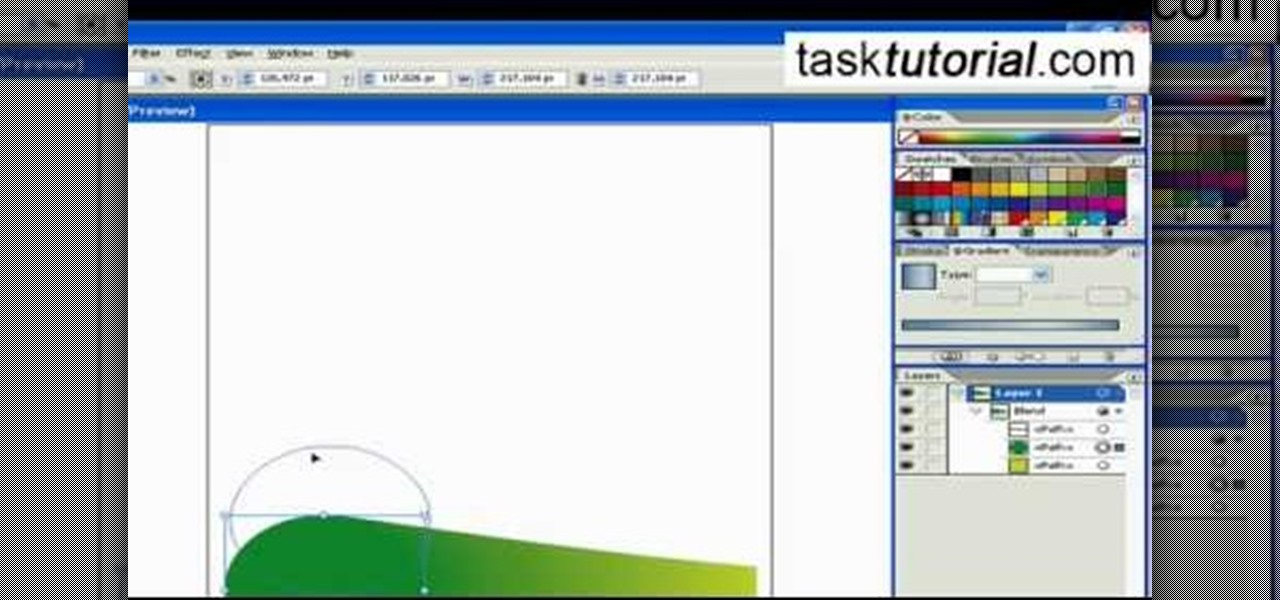
Learn how to blend shapes and colors in Illustrator with this tutorial. Open Illustrator and put the circle with color which you want. Put the square on the color you want. Select the object, go the title bar select the object and then select the blend. You will be shown the result on the screen. Select the square and circle where you place the object by click and drag method. Go to the object and select the blend and choose the blend options. Change in specific steps which you want in the sc...

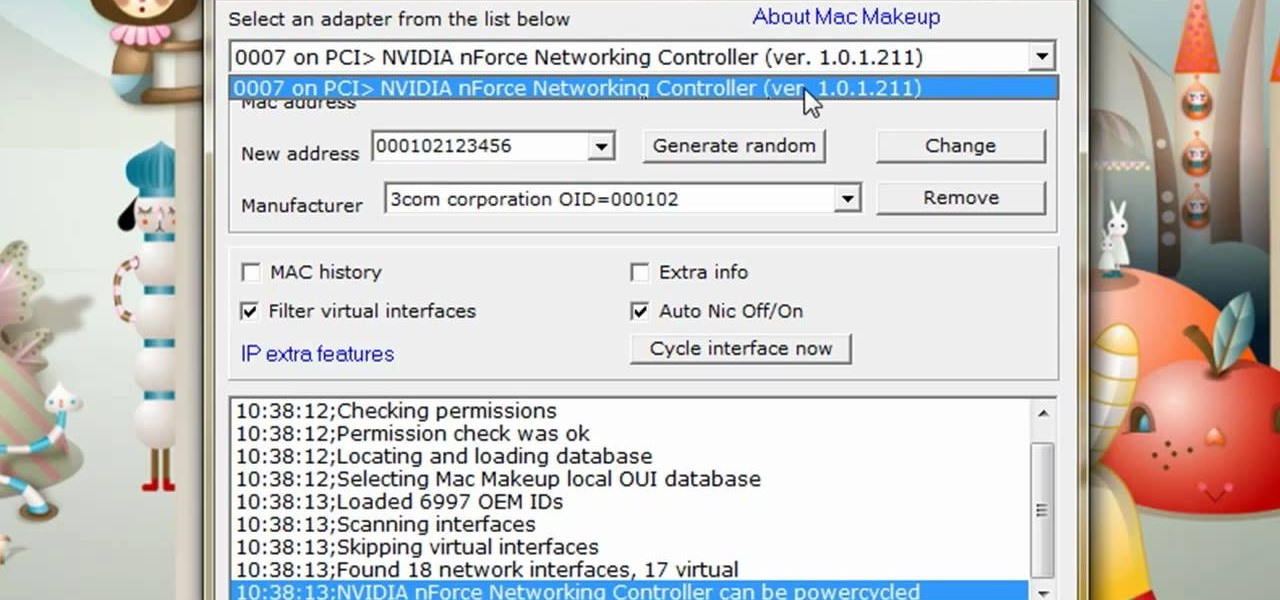
The video is about how to change the IP address. MAC address is the unique identifier a site of the most network adapters. MAC address is used to determine what IP address the computer will have and one way to change the IP address is by changing the MAC address. The method is only applicable for the windows systems and for the MAC systems you need to look at the link provided. In Windows in the start menu, type cmd in the run/search box, which will launch the command window. Type ipconfig/al...