To play in the World Cup, soccer's ultimate tournament, you have to be among the best players on the planet. For the rest of us, Google has a hidden game to simulate the thrill of scoring goals for your favorite team.

We all want to be healthy, but in practice, it can be tricky, especially from the fitness angle. Our lives seem busier and busier, which makes hitting the gym quite the challenge. What if we told you there was a real way to work on your fitness in the comfort of your own home — in just seven minutes a day? All you need is a chair, a wall, and a 7-minute workout app.
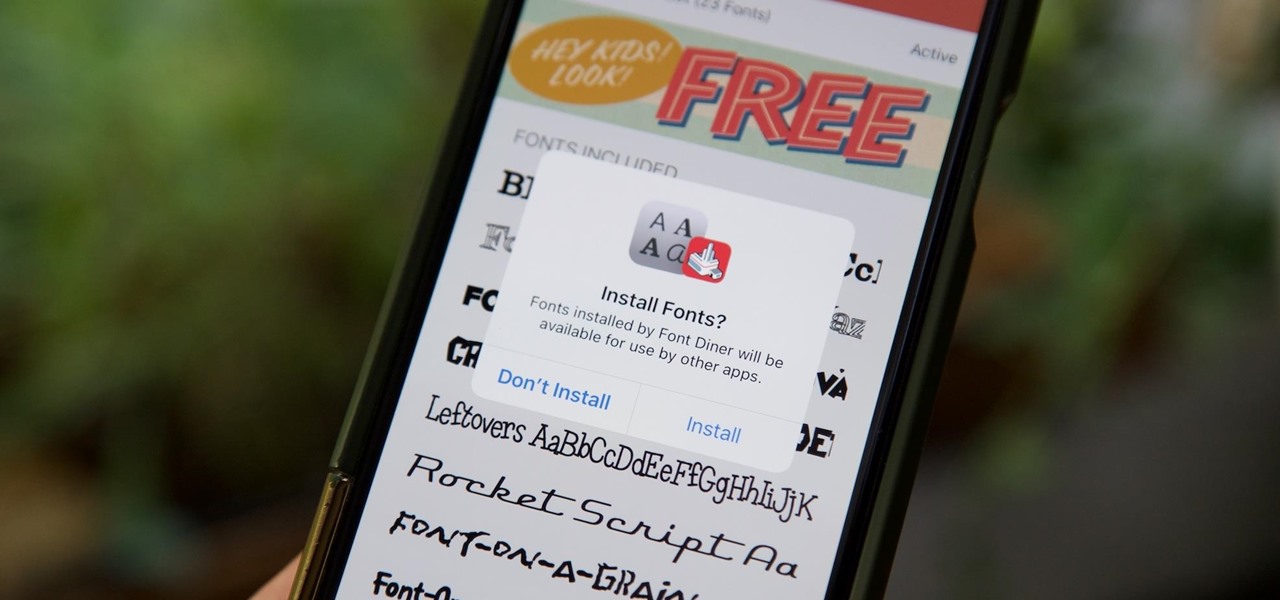
Apple added the option to install custom fonts and use them in different apps on iOS 13. The rollout has been a bit confusing, with Apple announcing partnerships with vendors such as Adobe, but also limiting the feature to work with only certain apps. Nonetheless, you can now download and install custom fonts on your iPhone.

It's finally out. After months of testing, iOS 13 is available to install on your iPhone, which means over 200+ new features you can use right now. The update, released on Sept. 19, can be installed over the air or from a restore image using iTunes in macOS Mojave and older or Finder in macOS Catalina. Ditto for the 13.1 update issued on Sept. 24.

The worlds of augmented reality and virtual reality are closely linked in many ways. That means it's smart for AR insiders to keep a close on new developments in VR. If you have been paying attention, you know that Oculus CTO John Carmack is one one of the most important thinkers in the VR space.

Many of our online accounts now come with an added two-factor authentication (2FA) functionality to help keep our data safe. This essentially means no one would be able to access the account until a specific set of requirements were met. It could be a combination of a password with a security key or even a passcode with some form of biometrics, like a fingerprint or face scan.

WhatsApp is the go-to messaging app for millions worldwide and its easy to see why. The app can be considered the Swiss Army Knife of texting thanks to numerous features like Group Chats and Status Stories, in addition to striking a great balance between ease of access and overall security.

Before you go ahead and delete your Facebook — don't lie, you've been thinking about it — consider this. Facebook offers users a wide variety of privacy options to mess with, which can help you find a little control over your information. We're not saying this solves Facebook's privacy crisis, but it might be a more reasonable option than throwing in the towel entirely.

Dating websites allow you to see a person in a very intimate context, framing their successes and accomplishments in life to an important audience. The information contained in these profiles often can't be found elsewhere, offering a unique look into the personal life of the user.

As smartphones become more accessible, billions of people have come to depend on their features for daily life. One of the most important aspects these days is the camera. OEMs have been working for years to improve camera quality, and they seem to have finally figured it out — the best way to achieve DSLR-quality photos wasn't just with better sensors, but with better intelligence.

PowerShell Empire is an amazing framework that is widely used by penetration testers for exploiting Microsoft Windows hosts. In our previous guide, we discussed why and when it's important to use, as well as some general info on listeners, stagers, agents, and modules. Now, we will actually explore setting up listeners and generating a stager.

Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.

It's no secret that devices leak data, but sometimes they do so in ways you may not expect. Your phone, laptop, printer, and IOT devices leak Wi-Fi information that can (and is) used to track you.

With some of the groundwork out of the way in getting a Mac set up for hacking, it's time to start looking at toolboxes. Our first toolbox is Git, which will be used throughout future tutorials.

Hello people again, I wrote my last post about crypto about 10 months ago, now I will introduce something not fresh for the science, but fresh for the people who wants to learn. In my http://null-byte.wonderhowto.com/forum/cryptography-0161538/ post of crypto concepts, there is just basics, today we will see something that targets wide concepts like Symmetric crypto, Public Key Cryptography, Hashing, Keys etc...

Update (February 2019): The methods below will help on older Android versions, but we've recently revisited this topic. So if you have a newer Android phone and you want to get rid of Google, head here.

Welcome back, my novice hackers! Reconnaissance is one of the most important preparatory steps to hacking. As I have emphasized many times before here on Null Byte, you must know the operating system, the ports, the services, the applications, and sometimes even the language of the target to be effective. If you haven't taken the time to gather this info, then you are likely wasting your time.

Anyone who has rooted their Android device has likely used a tool called Android Debug Bridge, better known as ADB, at some point during the process. For most, that is their only interaction with the ADB, but to be a true Android power user, you need to really know the tools at your disposal.

In my last article, I explained why text adventure games are some of the most Steampunk computer games out there. I even shared a free Steampunk text adventure game that I'd made myself!

It's a trick that never fails to amaze. You're placed in handcuffs, but with a flick of the wrist, you're free! Kick off your career as a daring escape artist with these simple tips.

Learn how to insert a reusable menstrual cup with this feminine hygiene tutorial. The menstrual cup is a great alternative to disposable tampons and pads. It is very cost effective and friendly for the environment. With regular sanitizing, the menstrual cup can last years. This video is specific to the Mooncup menstrual cup, although most menstraul cups are inserted in the same fashion. Watch this how to video and maybe you will decide to use a menstrual cup during your next period.

From Smart Web Printing to recyclable HP inkjet cartridges, it's never been easier to be environmentally conscious.

Here's a basic walk-through I put together explaining how to bring out the overtones. I ran by each step really quickly so if you have specific questions feel free to email me.

In this video clip series you will not only learn tips and information about the shofar but you will also learn how to play it and special notes specific to the instrument. Because there are no valves or fingerholes in the shofar it is its size that changes the tone and sound of the instrument. The larger the shofar the deeper and fuller the tone. This is just a piece of what you will learn through this series!

In this series of online video tutorials you'll learn how to use Reason 3.0 music recording software. Expert Jerus Arte demonstrates how to use the program, from installing it on your computer and setting it up with the right preferences, how to control the master volume, and how to use features like the NN-19, the NN-XT, the Dr, Rex loop player, and the Redrum machine. He shows you how to use effects like the compressor and reverb, and how to mix down your song into a format that can be burn...

Professional gymnast Hayley Holmes demonstrates how to become a contortionist with several stretching exercises, handstands, splits and basic moves borrowed from yoga and ballet. She tells you how and why she became interested in contortion ism and suggests career options should you become interested as well. And best of all, she twists into some truly amazing positions right before your eyes.

There are now more emoji on your iPhone's keyboard that you can send as reactions or stickers or insert wherever else you use emoji — and it's about time. It's been nearly a year since the last emoji update for iOS, and we only received support for 31 new ones then. The new iOS 17 software update brings almost four times as many.

Accessibility features — such as spoken content, reduced motion, and voice control — help those who might have hearing, vision, learning, or physical and motor disabilities better use their iPhone devices. These features are very welcome, but when enabled they work system-wide, which can be a problem if you need these settings enabled only in certain situations.

Your iPhone keeps track of every single place you go, especially those you frequent most often, and syncs those locations across all your iCloud-connected devices. People who gain access or already have access to your iPhone, iPad, iPod touch, or Mac may be able to view all of these locations to see where you've been and where you might be. If this worries you, there are things you can do.

These days, the only thing your eyes view more than your phone's home screen is the backside of your eyelids. So it goes without saying that whatever picture you have as your background gets old pretty fast.

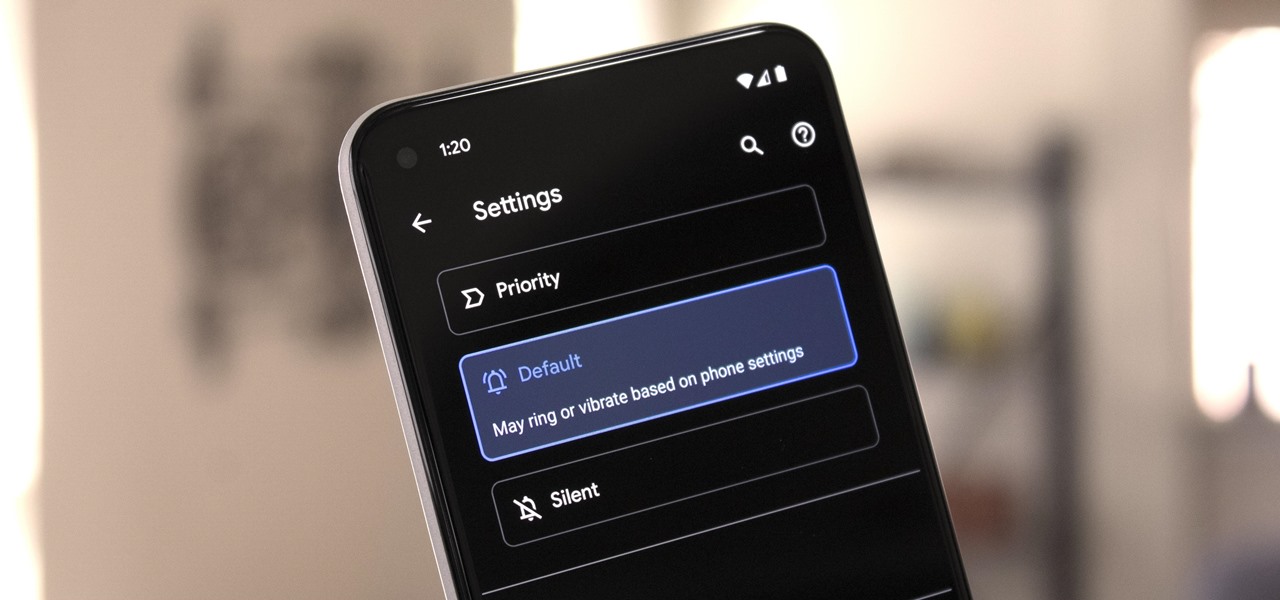
Things tend to get noisy when you're in a big group chat, which is why the notification sound for that thread shouldn't be your standard, attention-grabbing ringtone. But you don't want to set the default notification sound to something too subtle, otherwise you'd miss messages that actually matter.

Apple always finds a way to sneak in tiny, inconspicuous features that improve the iPhone experience. And with iOS 14, there's a hidden, unannounced gesture that makes it possible to navigate apps and menus faster than ever before.

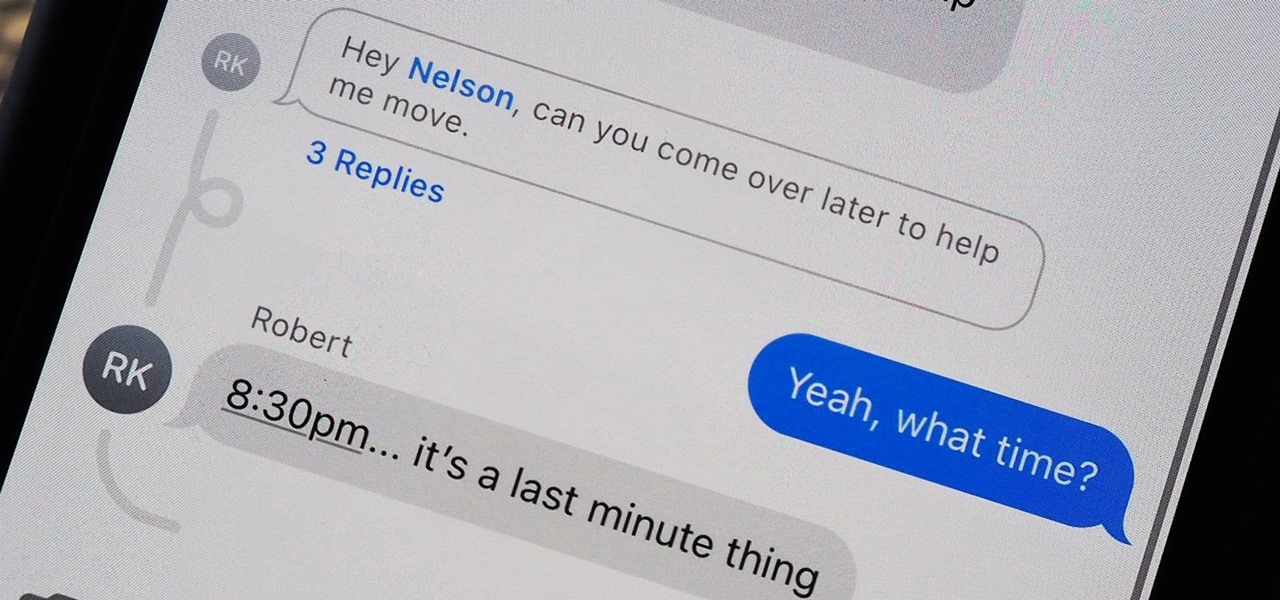
A group conversation can be a chaotic place. Even with a small number of people, you still may get more messages than you can keep track of on your iPhone. What makes it even worse is trying to sort through all of the conversations within conversations. Apple, however, wants to make things easier on all of us, which is why iOS 14 allows you to respond to specific iMessages using inline replies.

Folders are a neat way to keep your home screen apps organized in your own specific categories, but what about your personal contacts? You can actually populate a folder with all of your favorite contacts for one-tap instant access.

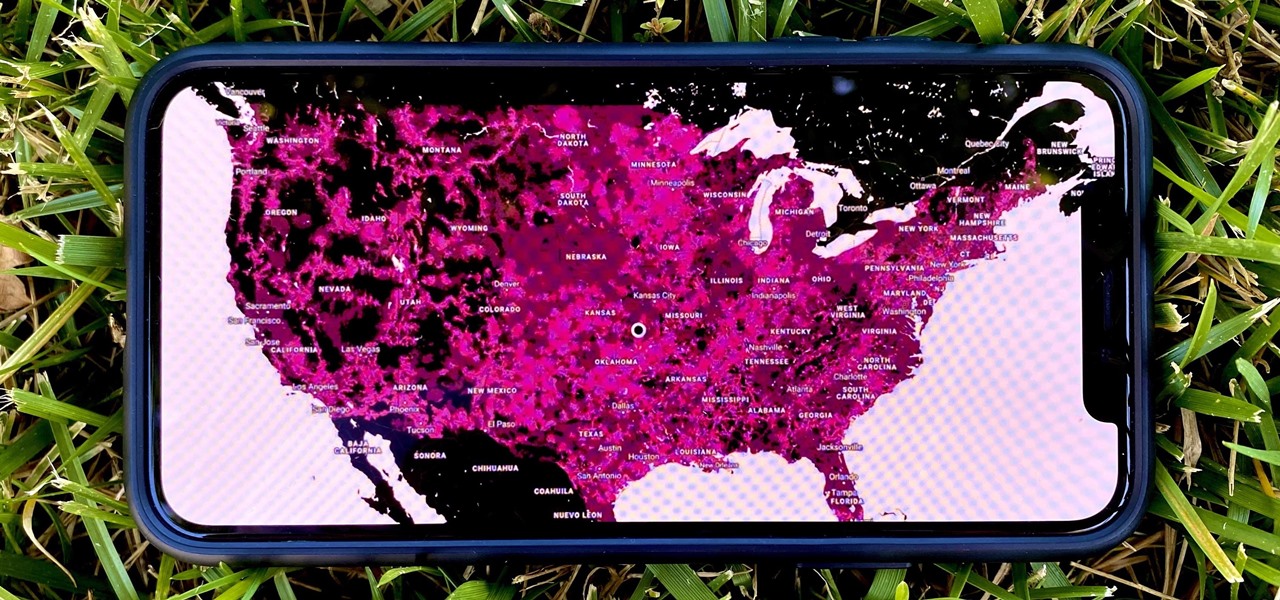
In 2009, 4G LTE networks rolled out in Stockholm and Oslo, replacing 3G as a better upgrade to the mobile data technology that gives us the broadband speeds we have on our mobile devices. Over a decade later, and we have the latest, next-generation wireless network technology among us, 5G, but can you even use it?

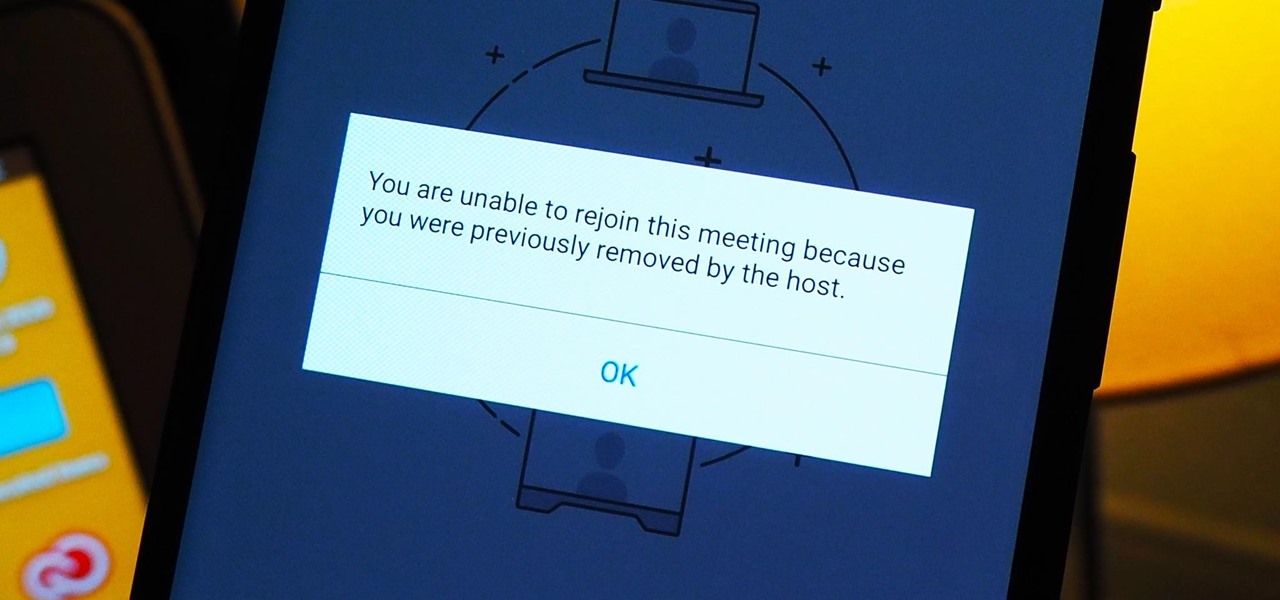
As more and more people use the video conferencing service Zoom, the chances of trolling behavior and attacks only increase. But it's not just "Zoombombers" you need to worry about. A heated discussion between family, friends, or colleagues could turn sideways real quick, and sometimes the best course of action is to remove the participant from the group video meeting altogether.

The response to the COVID-19 pandemic means that social distancing has become the new normal. It also means that more Americans are using video conferencing to connect with colleagues working from home or friends and family in quarantine because of the new coronavirus.

Computer vision is a key component in enabling augmented reality experiences, but now it can help give sight to the blind as well. In this case, that assistance comes from Envision, developers of mobile apps for iOS and Android that use optical character recognition (OCR) and object detection to provide an audio description of the user's surroundings.

When it comes to iOS beta updates, developers get their updates first, and once they do, public testers play the waiting game. Sometimes Apple releases the public version three hours later. Other times it waits 24 hours. It's a roll of the dice almost every time. As for iOS 13.4 public beta 2, it's the latter case, coming exactly one after developer beta 2.

The camera system on the iPhone has never been better. Apple's iPhone 11, 11 Pro, and 11 Pro Max sport some of the best shooters on the market. But no level of quality makes up for the fact that shady apps can access your cameras for nefarious reasons. You can take control of the situation, however, and block any app you want from using your rear and front-facing cameras.