It's no secret that devices leak data, but sometimes they do so in ways you may not expect. Your phone, laptop, printer, and IOT devices leak Wi-Fi information that can (and is) used to track you.

Whether you're a professional mechanic, a hobbyist, or someone who just wants to know why their check engine light came on, your Android device and an OBD-II adapter can provide insight as to what's going on with your car. Most adapters sell for less than $10, and once you plug it into your vehicle, you'll just need a good app to help you make sense of all the data it can gather.

We can add one more health effect of our gut bacteria to the growing list. Researchers from the UK have just reported that the gut microbiota plays a role, both directly and indirectly, on the toxicity and efficacy of chemotherapy. Their findings are published online in the journal Nature Reviews Gastroenterology & Hepatology.

As a former repair tech, I've heard the same reasons over and over as to why people opt not to purchase phone insurance. Some cite the cost—why pay extra every month for insurance when you're careful with your phone? Deductibles are expensive, so why not just spend that money on a repair instead of getting a refurbished phone as a replacement?

Black Mirror, Netflix's technology-horror anthology, never fails to provide thought-provoking entertainment centered around emerging and futuristic technologies, and the third season's second episode, "Playtest," delves deep into the worlds of mixed, augmented, and virtual reality. While designed to leave you haunted by the end, offering a more "evil" narrative than we'll likely see in our actual future, the episode explores possibilities that aren't as far off as one might think.

With some of the groundwork out of the way in getting a Mac set up for hacking, it's time to start looking at toolboxes. Our first toolbox is Git, which will be used throughout future tutorials.

Whether scheduling meetings, events, tasks, or even keeping tabs on the weather, a good digital calendar can help you stay on top of your game in ways that a normal calendar could never do. Indeed, there are many calendars to choose from, but Google Calendar is one of the best due to Google's excellent cloud service, feature-rich web-client, and their easy-to-use Android and iOS applications.

Hello people again, I wrote my last post about crypto about 10 months ago, now I will introduce something not fresh for the science, but fresh for the people who wants to learn. In my http://null-byte.wonderhowto.com/forum/cryptography-0161538/ post of crypto concepts, there is just basics, today we will see something that targets wide concepts like Symmetric crypto, Public Key Cryptography, Hashing, Keys etc...

So, you want to perform an exploit on a victim, but you're not on the same network as their machine. In this tutorial, I'll be showing you how to set up a meterpreter reverse_tcp attack to work over the internet.

My first ever post on here was 'Keeping your hacking identity secret' and it did very well, and its not something I see here on null byte. So read along.

Hello NullByte! This will be my first How To series.

If you're having a "Netflix and chill" night, the last thing you want to worry about is finding something to watch—after all, you have better things planned for the night.

hello my dear colleagues, I made a visit to nullbyte and found that there is not a complete tutorial about the google dorks, so I felt the need for this tutorial, and seeing that there are many newbies around, so here's a tutorial that will teach you how to use google to hack.

Locking your keys inside of your car is frustrating, to say the least, especially if you're in a hurry to get somewhere. You can always call AAA roadside assistance or a locksmith, but you'll probably have to fork over some money, as well as wait for them to get to you. You might even get towed.

Hi, everyone! Recently, I've been working on a pretty interesting and foolish project I had in mind, and here I'm bringing to all of you my findings. This guide's main aim is to document the process of building an Android kernel, specifically a CyanogenMod kernel and ROM, and modifying the kernel configuration to add special features, in this case, wireless adapter Alfa AWUS036H support, one of the most famous among Null Byters.

Update (February 2019): The methods below will help on older Android versions, but we've recently revisited this topic. So if you have a newer Android phone and you want to get rid of Google, head here.

Spotlight, Apple's selection-based search system, received a major facelift on Mac OS X Yosemite. Packed with dozens of new features, such as a central search window and increased app suggestions, the reworked Spotlight was a breath of fresh air.

The balanced and refreshing taste of a cocktail should always entice you into another sip. You'll know you're drinking something of quality when no specific ingredient, including booze, dominates its taste. A great cocktail can even mirror a great meal by exhibiting flavors like fruit, smoke, and herbs. And adding these flavors while making cocktails at home isn't hard at all.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

When you think of an online music service nowadays, Spotify is probably near the first that come to mind, and for good reason. Being able to create, share, and take all of your playlists anywhere, across all of your devices, is something that I couldn't live without. Unfortunately, nothing this good is free, and with Spotify Premium, users of their free service are left with very limited features when streaming on their mobile devices.

Welcome back, my hacker novitiates! A short while ago, I introduced you to regular expressions. Regular expressions are a language that is particularly useful for finding complex text patterns in streams of data.

Welcome back, my novice hackers! Reconnaissance is one of the most important preparatory steps to hacking. As I have emphasized many times before here on Null Byte, you must know the operating system, the ports, the services, the applications, and sometimes even the language of the target to be effective. If you haven't taken the time to gather this info, then you are likely wasting your time.

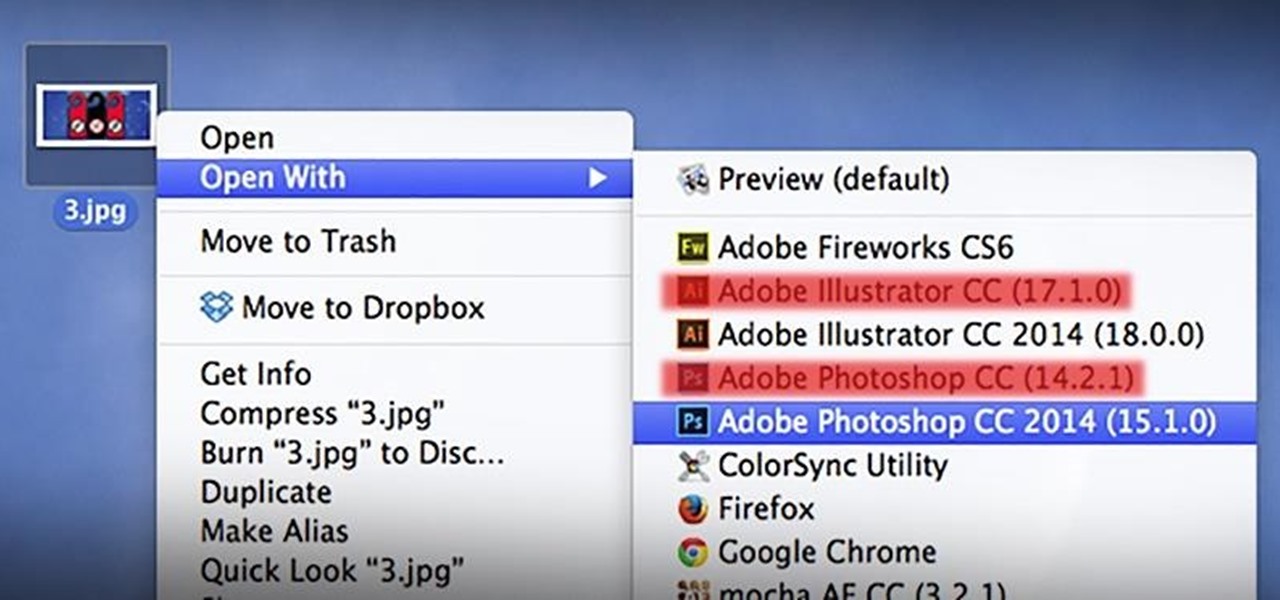
As a regular Mac OS X user, I have a love/hate relationship with the "Open With" contextual menu. Sometimes, it has just what I need. Other times, it's often packed with unnecessary or duplicate items, or missing the app I want to open the file up with the most.

Welcome back, my apprentice hackers! In this series on password cracking, I have been attempting to develop your skills in the age-old art of password cracking. Although it might seem like a simple and straightforward exercise, those of you who have attempted password cracking know that there are many subtleties to this art.

As we near the one-year anniversary of its release (and the inevitable unveiling of its successor), the Samsung Galaxy Note 3 remains a device that packs quite a punch when it comes to hardware. It boasts a 2.3Ghz CPU and was the first mobile phone ever to house 3GBs of RAM. Suffice it to say, it can handle any software you throw at it with no discernible lag. Even Samsung's notoriously bloated TouchWiz ROM seems lightning fast.

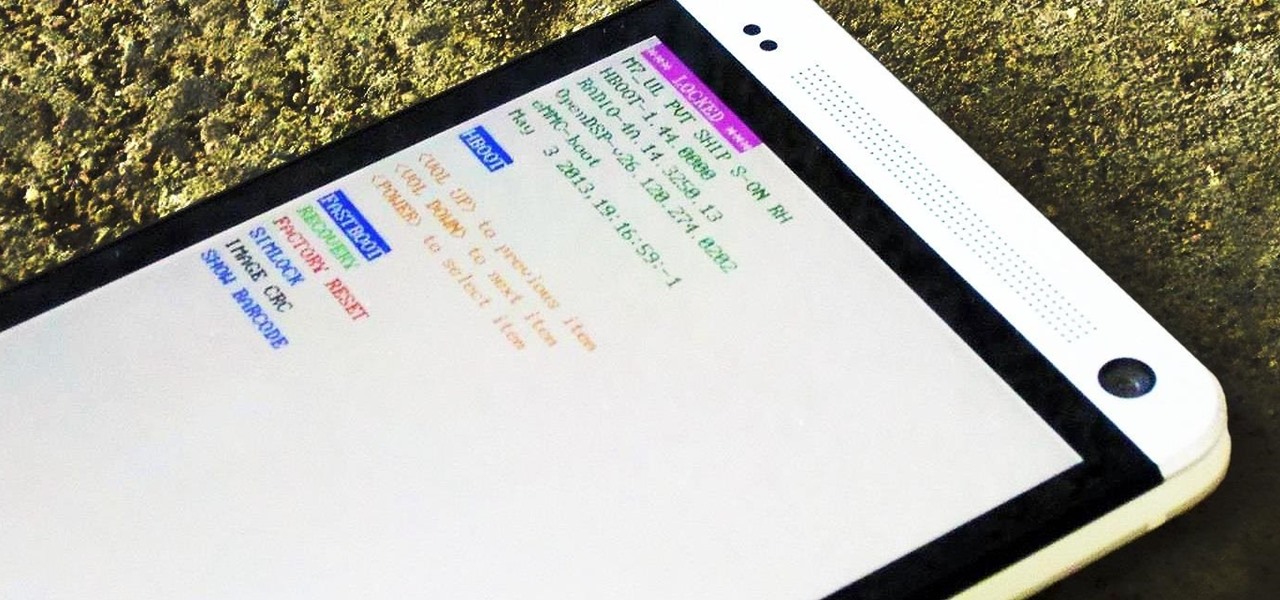
Anyone who has rooted their Android device has likely used a tool called Android Debug Bridge, better known as ADB, at some point during the process. For most, that is their only interaction with the ADB, but to be a true Android power user, you need to really know the tools at your disposal.

Welcome back, my fledgling hackers! A short while ago, I did a tutorial on conducting passive OS fingerprinting with p0f. As you remember, p0f is different from other operating system fingerprinting tools as it does not send any packets to the target, instead it simply takes packets off the wire and examines them to determine the operating system that sent them.

If you're reading this, chances are you're a softModder, someone who doesn't let anything stand in his or her way from ultimate customization.

Welcome back, my hacker apprentices! Although there is a multitude of different hacker types, the one target they all share is the database. I often refer to the database as the hacker's Holy Grail, or the ultimate prize for an effective hack.

The iPod changed the music and electronics industries when it was first introduced way back in 2001. It is credited with ushering in the age of "connected devices," and has held a huge market share of around 70% for years. At the height of its popularity, the iPod made up almost 50% of Apple's revenue. Now that the smartphones and tablets we use every day have the ability to store and play music, the iPod's glory days are over. Nevertheless, there are millions of people who still use them, an...

In my last article, I explained why text adventure games are some of the most Steampunk computer games out there. I even shared a free Steampunk text adventure game that I'd made myself!

If you've been to a convention of any sort before, you know that there are good and bad panels, and that their inherent goodness or badness often has little to do with the actual content being discussed. That's because giving a panel is a skill that not everyone has. However, it is a skill that everyone could have! In this article, I'll tell you how to give a good panel on practically any subject. Image by Shannon Cottrell

TouchDevelop is a browser-based programming tool that allows anyone to build your own Windows 8 apps directly from any touchscreen device, including iPad, iPhone, Windows Phone, Android, PC and Macs. Once the script is created and the app proves to work, it can be placed in the Windows Store for free or purchase.

I've tried my hand in the past at defining Steampunk, but as anyone else who has made a similar attempt will tell you, there's a significant backlash from the community against working to create a real definition of what Steampunk is. That may sound ridiculous to some, but it's a very serious matter to others. With the recent announcement that TeslaCon 4 will be called the Congress of Steam, I think it's appropriate to talk about why all of this stuff is worth it. In this article, I'm going t...

The director of 100 Musicians and Nurse/Fighter/Boy talked with us about old school filmmaking Charles Officer has directed shorts, music videos for K’naan, and the features Nurse/Fighter/Boy and Mighty Jerome, a documentary about Canadian track star Harry Jerome. His new short 100 Musicians, which screens Monday as part of Short Cuts Canada, is a small ode to civic optimism, concerning itself with a lovers’ argument over who exactly misheard a radio DJ reporting the plans of Toronto’s much m...

Okay, so you've decided to take the plunge, and participate in our Love. Earn program with a how-to article. But, for whatever reason, your article keeps getting rejected by WonderHowTo, and you're wondering, well, where's the love?

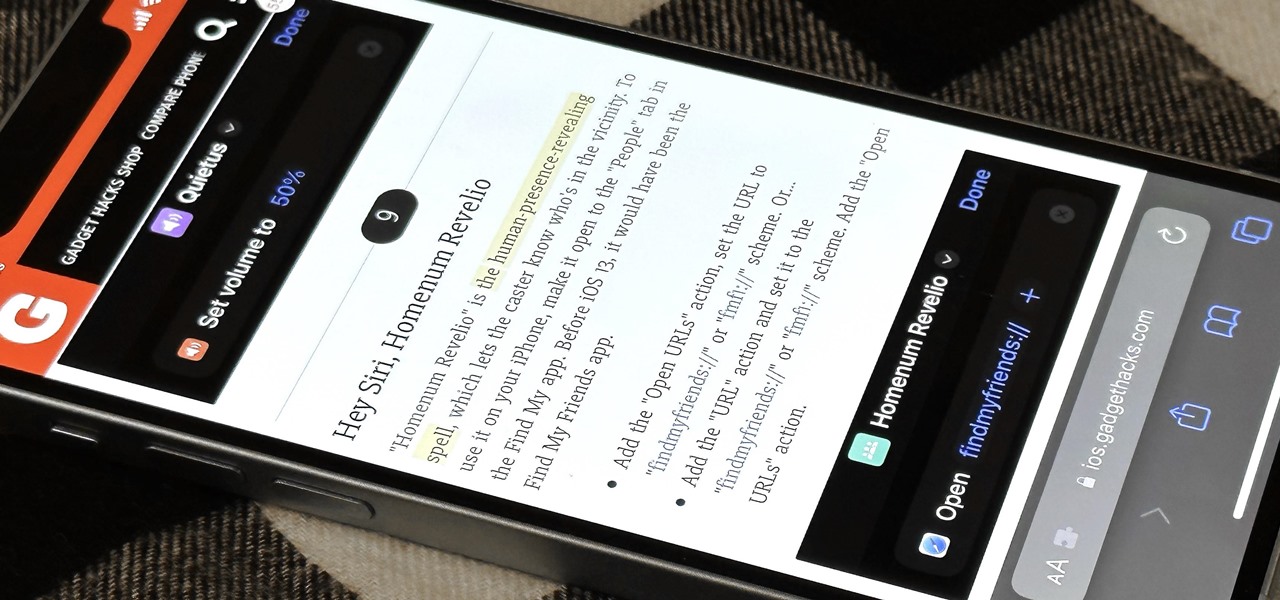
Safari has a major new feature for your iPhone, something that will change how you share, receive, and interact with links — and nobody is talking about it. The feature works on the latest iOS software, as well as the latest iPadOS and macOS versions. Still, you won't find any information about it in Safari's app or settings, so it's pretty hidden if you haven't seen it by accident yet.

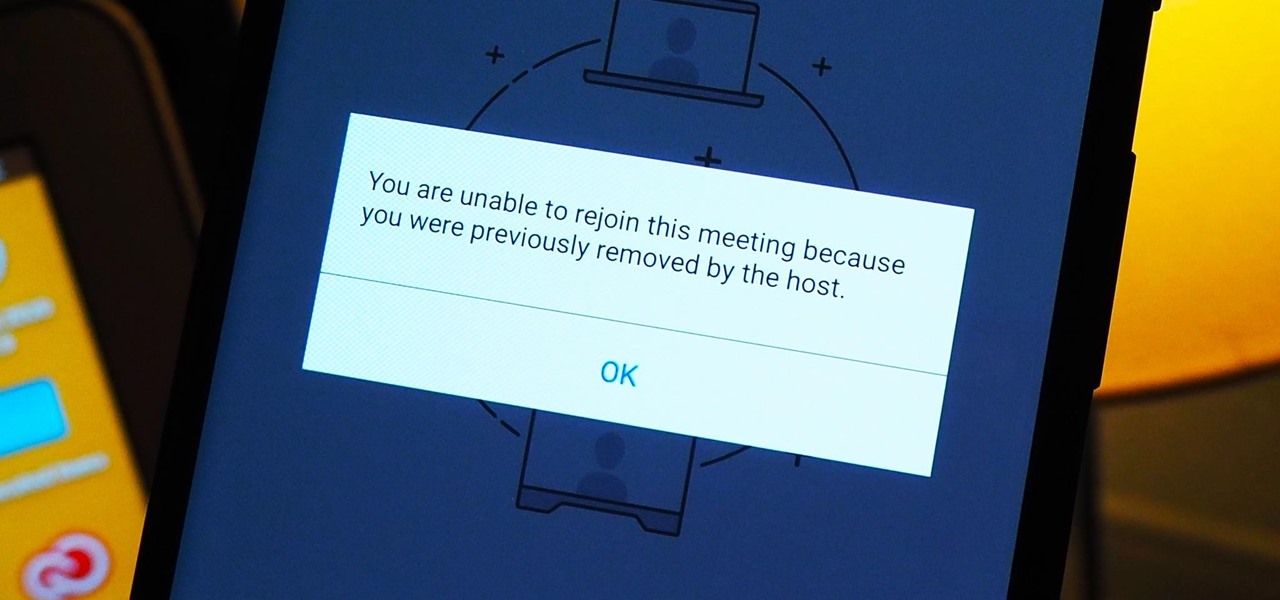
As more and more people use the video conferencing service Zoom, the chances of trolling behavior and attacks only increase. But it's not just "Zoombombers" you need to worry about. A heated discussion between family, friends, or colleagues could turn sideways real quick, and sometimes the best course of action is to remove the participant from the group video meeting altogether.

Computer vision is a key component in enabling augmented reality experiences, but now it can help give sight to the blind as well. In this case, that assistance comes from Envision, developers of mobile apps for iOS and Android that use optical character recognition (OCR) and object detection to provide an audio description of the user's surroundings.

The camera system on the iPhone has never been better. Apple's iPhone 11, 11 Pro, and 11 Pro Max sport some of the best shooters on the market. But no level of quality makes up for the fact that shady apps can access your cameras for nefarious reasons. You can take control of the situation, however, and block any app you want from using your rear and front-facing cameras.