The Pixel's "Flip to Shhh" feature may not be groundbreaking, but it is useful. Third-party apps are copying it for other phones because it's so convenient. But it's not enabled by default and it's fairly hidden in the settings. So to take full advantage of your Pixel's feature set, you should learn how to use Flip to Shhh.
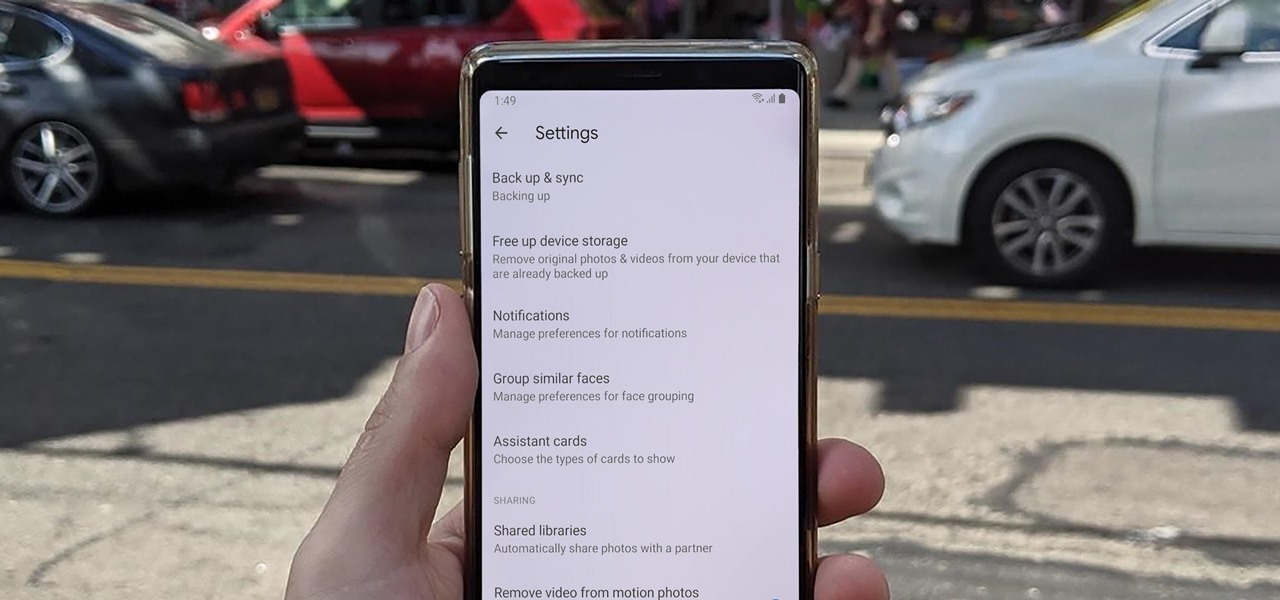
Sharing pictures from Google Photos by sending a link saves time because you don't have to download the image from Google, then reupload it somewhere else. But anyone who has your link can access your pictures, and baked into every file is metadata that you may not want prying eyes to know about.

I don't know about you, but I go to Pandora to listen to music. So when the music stops and an audio message from an artist starts updating me on their tour dates or some new product, I get pretty annoyed. The good thing is you can turn these off.

Some may find it annoying to get YouTube notifications randomly throughout the day. Every time a YouTube channel uploads a video, every time someone replies to your comments. But at the same time, you don't want to turn off those notifications so you don't miss out. Well thankfully, YouTube offers a happy medium where you can get important notifications, but only get them once a day at your desired time.

Did you know that the YouTube app can tell you how much time you've spent watching videos? If you're like me, you'll be surprised to know exactly how much of your life is spent inside the popular app. You can get a specific breakdown of how much you YouTube you consume.

Let me paint a picture for you. You're on a long flight home, and while listening to music on your Samsung Galaxy S10, a great song comes on. You want your friend to hear it too, who's also listening to music using a pair of Bluetooth headphones. Thanks to Dual Audio, you can easily share your experience.

Despite the recent gut punch of staff layoffs, Canada-based smartglasses startup North and its Focals are likely to be in the game for a while longer.

Smartphones have put an end to camcorders. If you want to capture memorable moments in high quality, look no further than that technological marvel in your pocket. Recent Galaxy phones are shining examples of how far we've come — but the more capable a camera gets, the more complicated things can be.

Every year, fans of Irish culture, as well as those looking to celebrate their own culture, come together on St. Patrick's Day, March 17.

We're still weeks away from a probably HoloLens 2 release, but Microsoft's immersive computing team is still hard at work on other aspects of its "mixed reality" ecosystem.

Samsung isn't set to reveal its latest and greatest — the Galaxy S10 line — until February 20, but that hasn't stopped leaks from giving us an early taste. While we already know what the rumored devices will probably look like, we now have access to their wallpapers as well. Apple fans don't need to be left out of the fun — someone has already cropped these images to fit your iPhone's display.

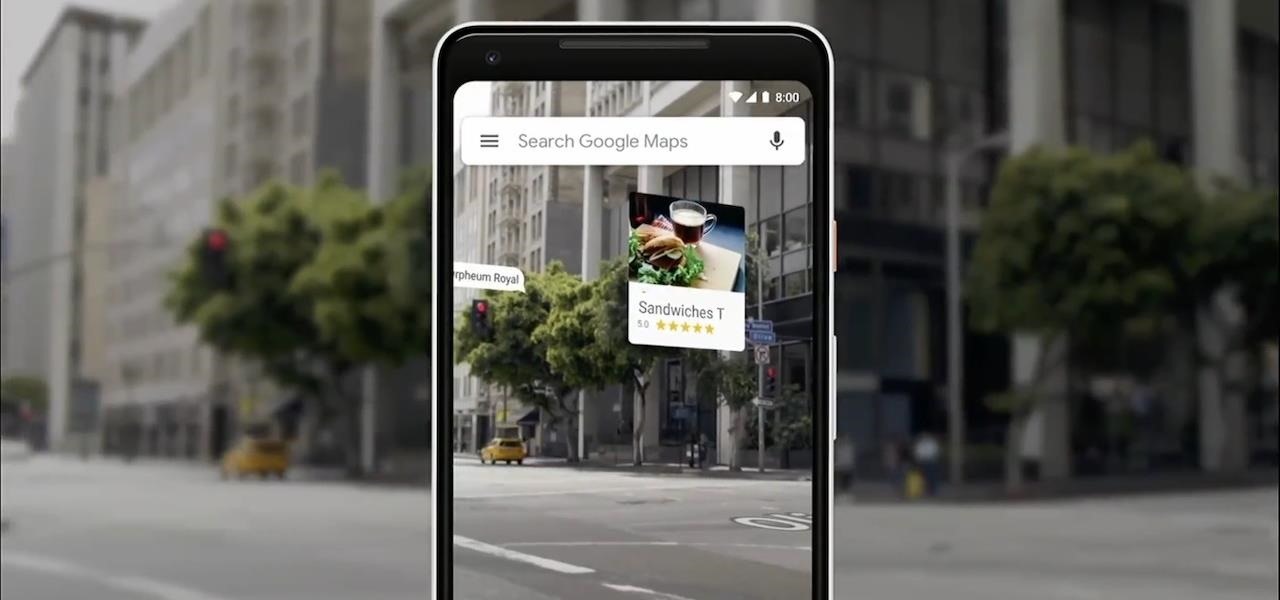
The augmented reality walking navigation mode for Google Maps appears to be closer to an upcoming release for the general public.

If there was a version of the Doomsday Clock for counting down the release of Microsoft's HoloLens 2, then the caretakers of that imaginary clock would move the minute hand to "one minute to midnight."

In a way, Twitter is the town square of our era, where people can share and discuss ideas on a wide variety of topics. While the tech giant has its own app for Android, it's pretty bare-bones when it comes to features. This has paved the way for third-party clients that are rich with customization options.

Whether it's for health reasons or just to look better, many of us want to get in shape. It's a long process that starts with nutrition, and dieting is never easy. Fortunately, there are some great food-tracking apps that will make it a lot easier to become a healthier version of yourself.

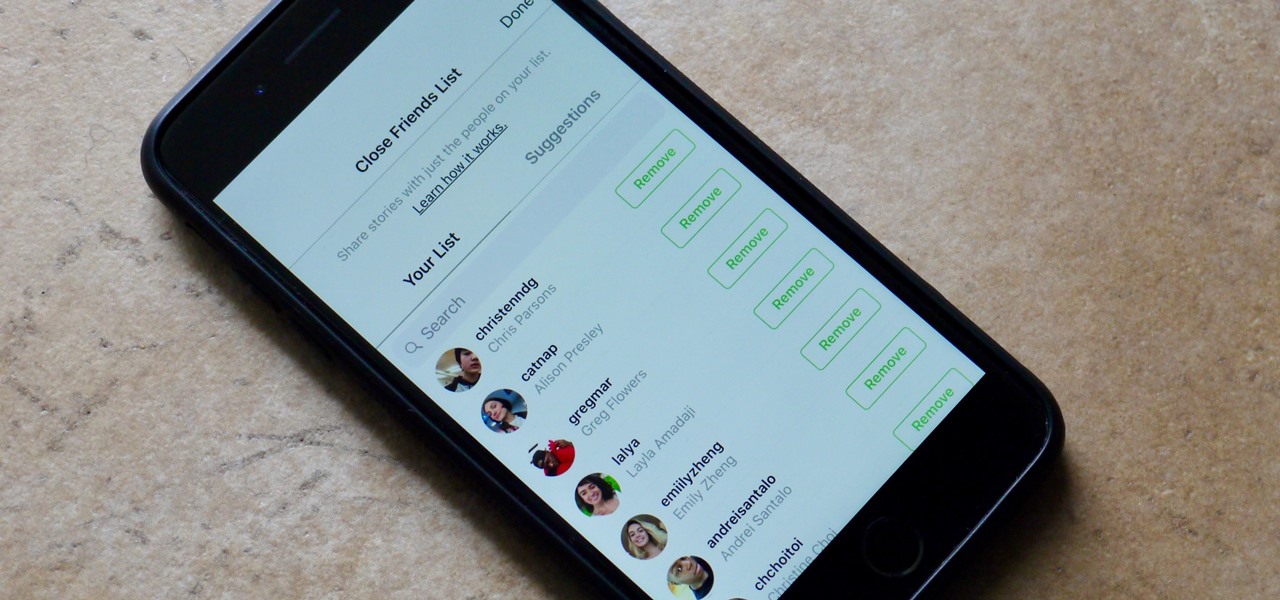
Stories make sharing your day-to-day highlights fun on Instagram. However, other than choosing who to hide stories from, by default, stories don't have much privacy control, especially if your Instagram account happens to be public. Instagram recognizes this flaw, which is what its "Close Friends List" is all about.

One of Apple's most touted (but seldom seen on social media) apps, Clips, got an update on Wednesday.

The Pixel 2 XL had what Google called a circular polarizer to ensure the screen would be visible from any orientation while wearing polarized sunglasses. They made a pretty big deal out of it at their 2017 event, but in 2018, there was no mention of whether or not this feature would return in the Pixel 3. It did.

While there were a ton of features added in iOS 12, one that Apple had been bragging about since June was nowhere to be seen. Until now. With the iOS 12.1 update, your iPhone gets a huge feature, as well as a few smaller ones to boot.

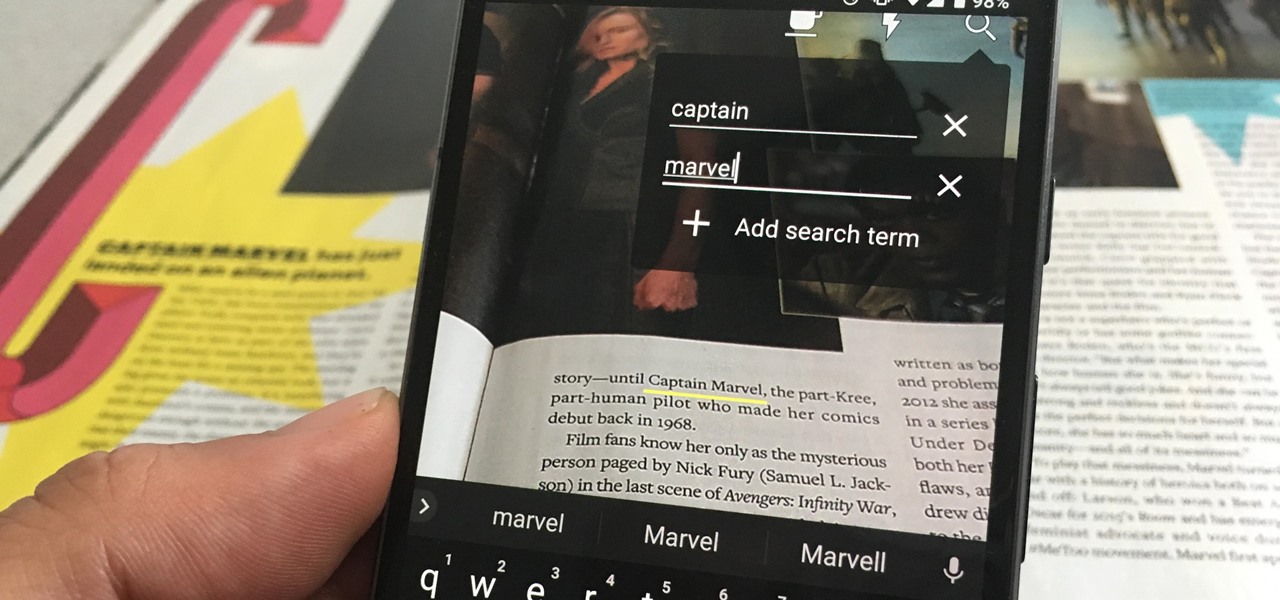
One of the neatest tricks available in Google Lens, an app that can identify and interpret real world information, is the ability to copy text from the app's camera view and paste it into a digital document.

From its introduction and all the way through iOS 11, FaceTime has been restricted to one-on-one calls. Apple will be changing that in a future iOS 12 update with Group FaceTime, which adds support for up to 32 people total in group audio and video calls. But that's not all we'll be getting in iOS 12 — there are more features that FaceTime has or will be getting soon that you should know about.

Magic Leap has been promising to launch a developer conference for years, and now the company is finally making good on that promise. On Wednesday, Magic Leap sent out the official announcement for its first L.E.A.P. conference, which will be held in Los Angeles in October.

If you're on the hunt for a profitable side-gig, or even a completely new way to to make money, you'll want to take a look at Upwork, a leading freelancing platform that connects skilled freelancers with clients from all over the world.

With Android Pie, Google added a genuinely useful feature for Pixels called App Suggestions, which uses AI to predict the apps you might want to use next. These show up at the top of your app drawer and in the new dock in the revamped multitasking UI for quick access. But here's the trouble: Muscle memory is a thing.

If you're a part of Generation X or a Millennial, there's a good chance that the first mobile game you played was Snake on an old school Nokia phone. Now, you can relive that nostalgia of monochrome and push buttons in augmented reality with the Facebook Camera.

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.

Apple's own Photos app received some pretty amazing updates in iOS 11, but does iOS 12 have what it takes to one-up last year's Photos improvements? We think so.

Netflix is branching out into the comic book business, and it's summoning augmented reality via Facebook to make the first issue more magical.

Location services company Mapbox has added new capabilities to its location-based gaming tool to fend off Google's challenge for the same mobile app category.

Backdooring a powered-off MacBook is easy when a few minutes of physical access is allowed. That attack works well if the hacker also shares a Wi-Fi network with the victim, but this time, I'll show how to remotely establish a connection to the backdoored MacBook as it moves between different Wi-Fi networks.

When it comes to augmented reality apps, visually immersive experiences are plentiful, but audio experiences are somewhat underrepresented. A new app for iPhones and iPads seeks to shift the AR paradigm toward the latter.

Google's Pixel smartphone had a decent head start as one of the first devices to offer ARCore, but that early exclusivity has been frustrating for some Android device owners. Some of that frustration was relieved when Google added more Android devices to the ARCore list in February.

It's not an official app, but for fans of Rick and Morty, it's a welcome piece of the series' universe until the recently renewed animated show returns to Adult Swim.

Your email inbox is a treasure trove of personal data. The people you contact, your writing style, which messages you flag as spam — all of this information and more can be used to paint a clear picture of you. Google knows this as well as anybody, so they use this data to constantly improve your experience in Gmail.

Following in the augmented reality footsteps of Pokémon GO, Universal Studios has decided to give us an AR version of Jurassic World.

Researchers have developed a new method that harnesses the power of augmented reality to detect a patient's heart rate using a Microsoft HoloLens and computer vision.

Attention LG V30 and G6 owners — Android 8.1 is coming to a device near you. While fans of LG's latest smartphones are still stuck on Nougat here in the US, we now have confirmation that Oreo's first major update will find its way here, even if we aren't sure when.

Earlier this week, Snapchat announced a partnership with NBCUniversal regarding the 2018 Winter Olympic Games in South Korea. Starting on February 10, Snapchat will be streaming a feed of NBC's live broadcast of the Olympics in Pyeongchang.

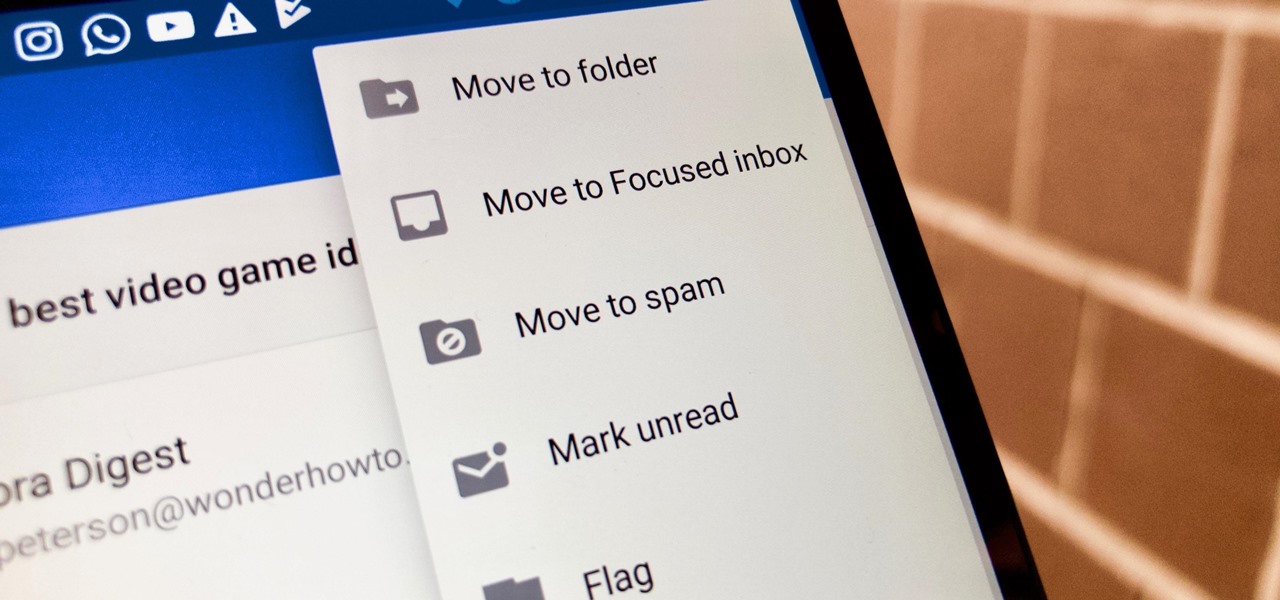
Nobody likes spam, and that's why email apps continue to vie for your digital attention by boasting about new ways to filter and reduce unsolicited messages. Outlook, an already fantastic client for focusing your cluttered inbox, has now joined in on the action, giving its users new, simple tools to fight against junk mail.

The internet is constantly under siege by bots searching for vulnerabilities to attack and exploit. While conventional wisdom is to prevent these attacks, there are ways to deliberately lure hackers into a trap in order to spy on them, study their behavior, and capture samples of malware. In this tutorial, we'll be creating a Cowrie honeypot, an alluring target to attract and trap hackers.