
News: Mixed Reality Is the Future of VR Gaming
Don't Miss: The Difference Between Virtual, Augmented, & Mixed Reality


Don't Miss: The Difference Between Virtual, Augmented, & Mixed Reality

Not content with bringing the first untethered mixed reality headset to market, Microsoft wants to expand their Windows Holographic operating system beyond HoloLens into vastly more robust technologies.

Welcome back everyone! It's been quite a while hasn't it? Today we're going to kick off the second part of the Python training series by introducing modules. We'll start off by explaining what a module is and we'll give an example. So, let's get started!

Hello people again, I wrote my last post about crypto about 10 months ago, now I will introduce something not fresh for the science, but fresh for the people who wants to learn. In my http://null-byte.wonderhowto.com/forum/cryptography-0161538/ post of crypto concepts, there is just basics, today we will see something that targets wide concepts like Symmetric crypto, Public Key Cryptography, Hashing, Keys etc...

Greetings my fellow aspiring hackers, It's still Christmas and we have a lot of things and hugs and kisses and ... to share ( you know the things that you do ). I have never done this before but I just felt to encourage you on the quest for knowledge, security and defence, skills and a whole lot more that comes out as a result of pursuing hacking. What we mean by hacking on this forum is White hat Hacking and OTW has great articles on it and I don't need to explain myself on that one.
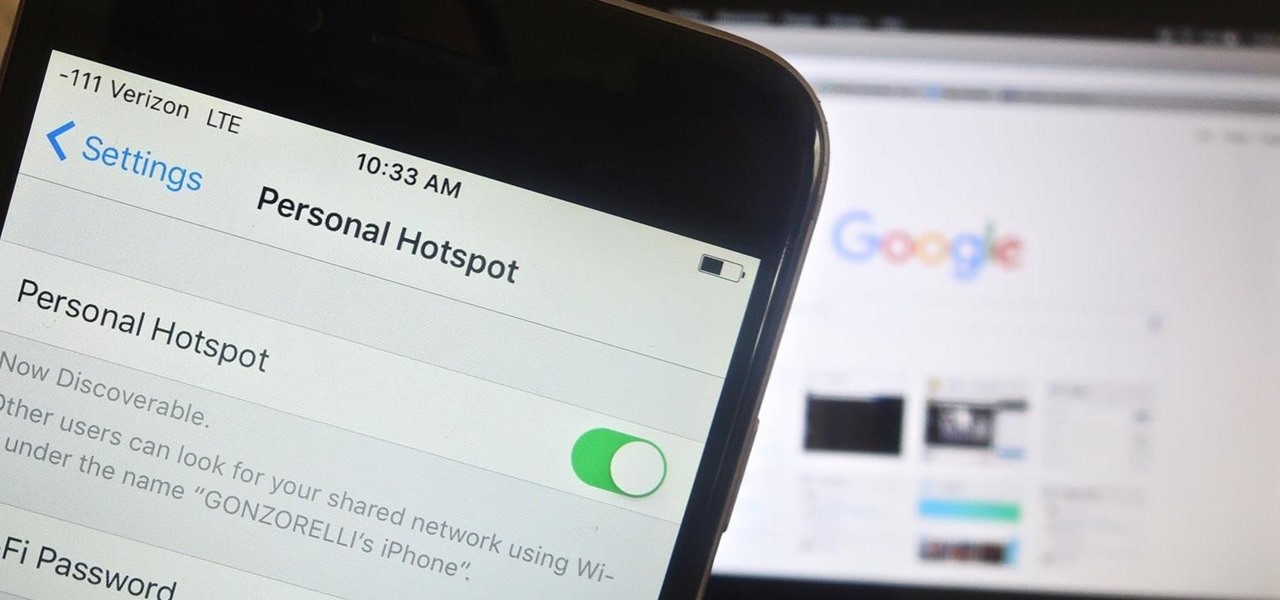
When you're in a bind and need an internet connection for your laptop, look no further than your iPhone. Using the Personal Hotspot feature in iOS, you can share your iPhone's internet connection with other devices by way of Wi-Fi, Bluetooth, or even USB.

Your brain holds a lot of precious information and is capable of great feats. However, there's one quality that doesn't lie among its strengths—memory security. Yes, that's right, your brain can be hacked, and it doesn't take a psychologist to do it. Anyone with the right know-how can change your memories for their own personal benefit, and you can do so to others, too.

Welcome back, curious hackers! In today's tutorial, we will be diving deep into the manipulation of Google Operators, commonly referred to as "Google Dorks" in order to access Surveillance Cameras and other control panels.

One of the first orders of business after purchasing a new smartphone is to load up your shiny new toy with phone numbers, email addresses, and general contact information for all the important people in your life.

As much as it pains me to say it, without my phone, I would pretty much be useless. I can barely remember what I had for lunch yesterday, let alone all of the hundreds of numbers in my contact list. That's why whenever I forget my phone at home, I am pretty much stuck having to choose whether I want to be late to wherever I'm going, or feeling completely lost and disconnected for the rest of the day.

Welcome back, my hacker noviates! In a recent post, I introduced you to Shodan, the world's most dangerous search engine. Shodan crawls the globe from IP to IP address, attempting to pull the banners of each web-enabled device and server it finds.

Apps that have no business accessing the internet can share your location, device ID, and other personal information with potentially malicious data snatchers. If you're connected to the internet on your Nexus 7 tablet, you're a potential target for cyber threats.

I regularly listen to music on my Nexus 7 while working or playing my Xbox. It's light and easy to carry around, and has basically become an extension of my body. The only thing that bugs me is having to constantly turn the screen on to pause or change music tracks. Even if I can do it from my lock screen instead of the actual music player app—I don't want to.

For my money, one of the greatest improvements brought about from the smartphone revolution is the advent of visual voicemail. No longer do we have to slog through dial menus or trudge through every single message to get to the next. We can just look at our messages, right there on our screens, organized neatly like emails or text messages.
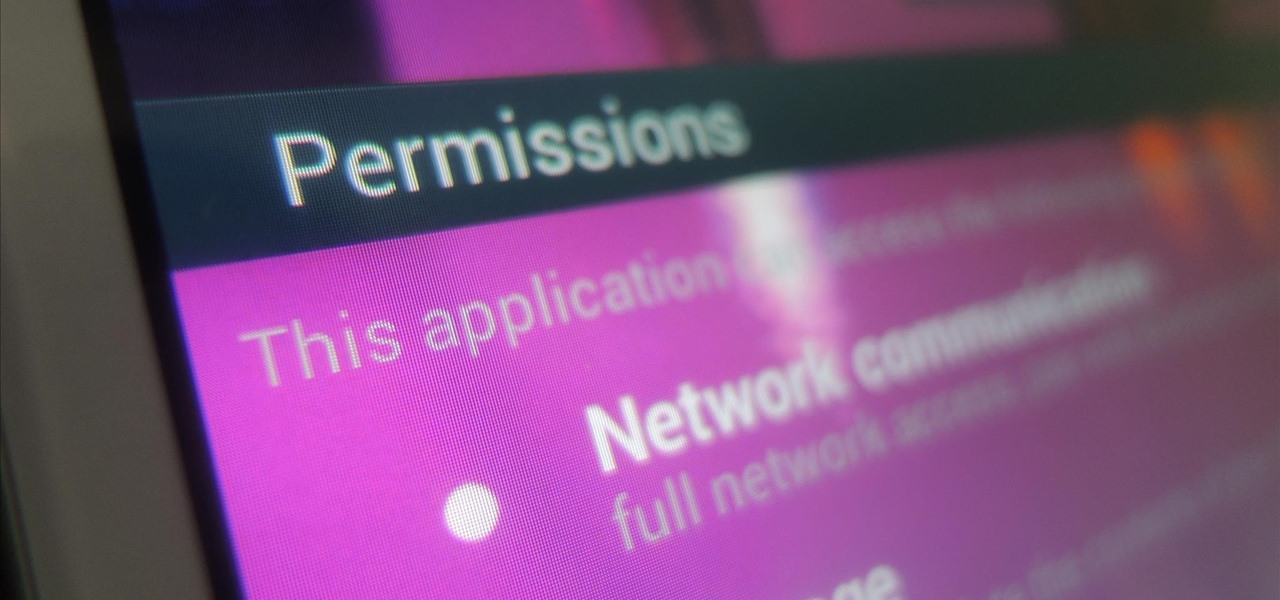
While we're usually responsible for leaking our own private information through mediums like Facebook, there are other times when we mistakenly and unwillingly allow certain applications to scour through our personal data. Some apps may have enabled permissions for internet access, thus allowing it to share said data with its external servers.

Send an email prematurely? Forgot to attach a file? Accidentally addressed it to the wrong person? It happens to the best of us. But what can you do to get it back? Hack into the other person's email account and delete the email before they get a chance to see it? Unless you're a hacker extraordinaire, that option is unlikely. So, what can you do? If the email has already been sent, you're probably out of luck. Even if they didn't read it yet, your chances of retrieving it are slim. But some ...

Before I really get into this article, it's important to note that you do not need a Steampunk persona (or "steamsona") in order to be a Steampunk, or wear Steampunk clothes. Some people like to pretend to be a different person when dressed up in Steampunk clothing, but that is entirely optional, and only to be done if it appeals to you. That said, even if you aren't actually acting as your character, it may still be helpful to have one in mind when putting together an outfit. Personally, I'v...

Hate answering the door, but don't trust your friends with a set of keys? This RFID front door lock made by Steve Pomeroy will solve all your party-hosting problems. It reads the RFID tags in his friends' public transit cards and decides who's allowed in based on "groups" that Steve defines. And I have to say, it's also rather stylish. It's controlled by an Arduino serial console and a custom Android app to add and remove cards. The reader can store 50 or 100 tags at a time and allows 7 diffe...

Are you interested in beginning research of your family's history? I began this journey about 3 or 4 years ago and here is what I found. I've done almost ALL of my research online, and gotten farther, faster and more comprehensively than anyone else who has researched my family the old fashioned ways. This is the kind of thing that technology is made for. Here's how to use it.
This clip will teach you everything you'll need to know to draw a Yoshi playercard emblem in the Call of Duty: Black Ops Emblem Editor.
This clip will teach you everything you'll need to know to draw the dreaded Connection Interrupted symbol in the Call of Duty: Black Ops Emblem Editor.
Love the Yankees? This clip will teach NY Yankees logo playercard emblem in the Call of Duty: Black Ops Emblem Editor.
This clip will teach you everything you'll need to know to draw a Squirtle Pokémon playercard emblem in the Call of Duty: Black Ops Emblem Editor.

This clip will teach you everything you'll need to know to draw a Brazilian flag playercard emblem in the Call of Duty: Black Ops Emblem Editor.

This clip will teach you everything you'll need to know to draw the Redwings logo playercard emblem in the Call of Duty: Black Ops Emblem Editor.

Love Famous? This clip will teach you everything you'll need to know to draw a Famous logo playercard emblem in the Call of Duty: Black Ops Emblem Editor.
Love Chevrolet cars? This clip will teach you everything you'll need to know to draw a Chevy logo playercard emblem in the Call of Duty: Black Ops Emblem Editor.

This clip will teach you everything you'll need to know to draw a PS3 logo playercard emblem in the Call of Duty: Black Ops Emblem Editor.
Want to show off your OG (original gamer) status? This clip will teach you everything you'll need to know to draw a custom Sonic & Tails playercard emblems in the Call of Duty: Black Ops Emblem Editor.
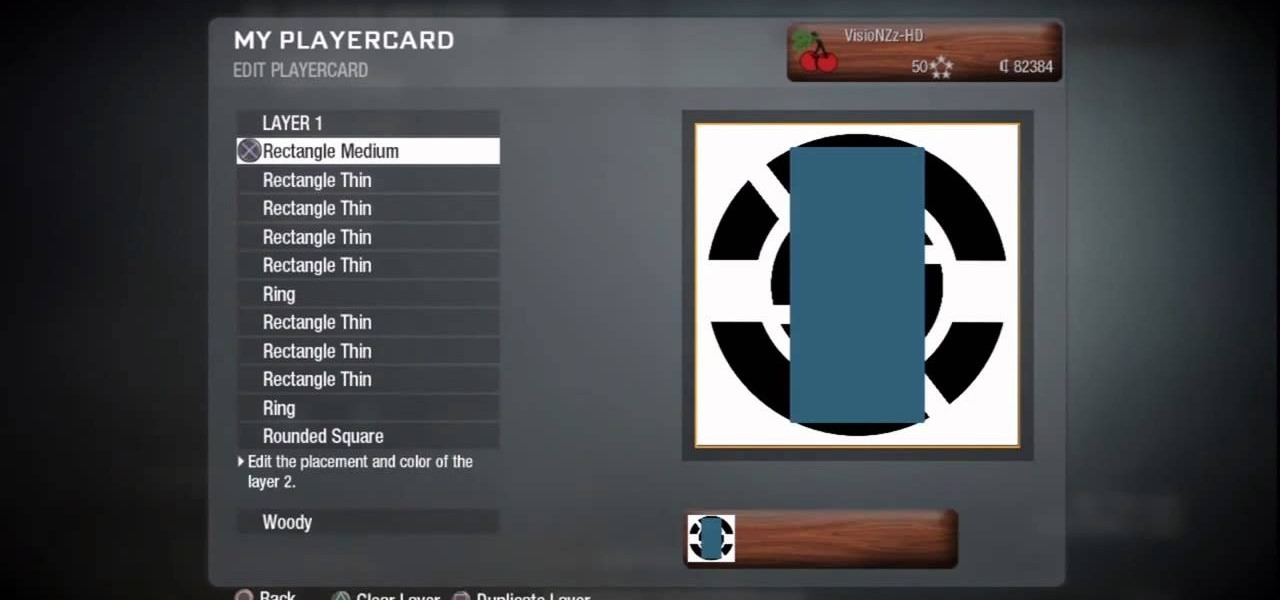
Is your love of Black Ops matched only by your love of skateboarding? This clip will teach you everything you'll need to know to draw skateboard logo playercard emblem in the Call of Duty: Black Ops Emblem Editor.

This clip will teach you everything you'll need to know to draw a custom B-Bomb playercard emblem in the Call of Duty: Black Ops Emblem Editor.
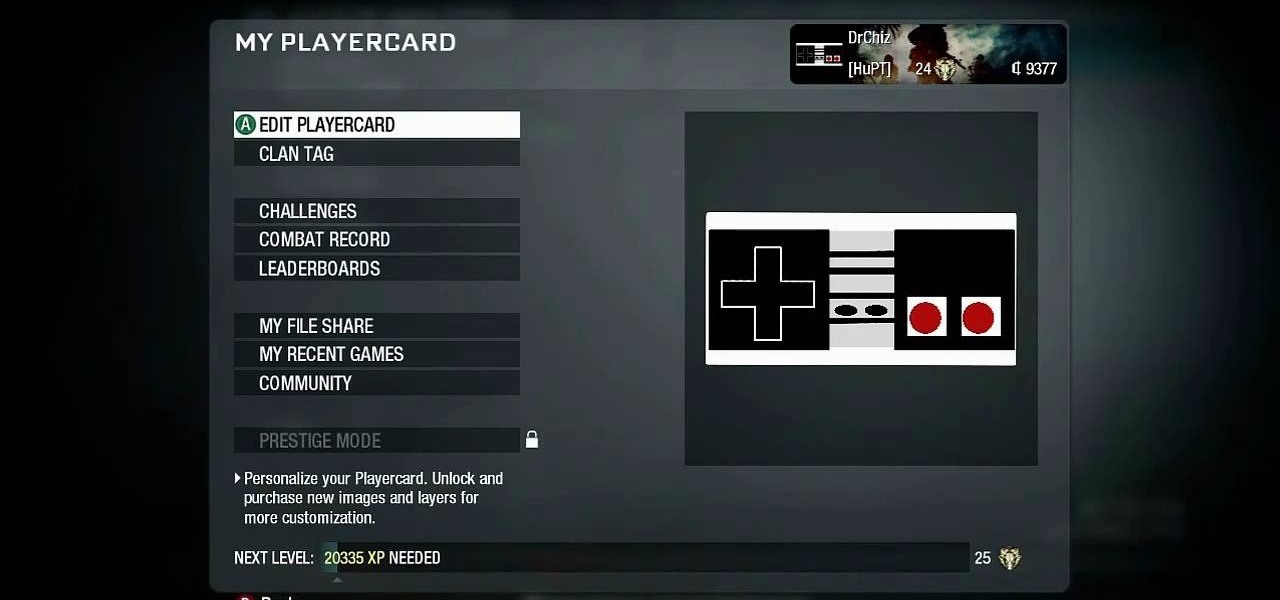
Want to show off your OG (i.e., original gamer) status? This clip will teach you everything you'll need to know to draw a custom NES controller playercard emblem in the Call of Duty: Black Ops Emblem Editor.
Excited about Portal 2? Show the world! This clip will teach you everything you'll need to know to draw a custom Portal 2 playercard emblem in the Call of Duty: Black Ops Emblem Editor.

Love Invader Zim? Learn how to draw Gir in the Call of Duty: Black Ops Emblem Editor. This quick clip will teach you everything you need to know.

Love Portal? Learn how to draw a Companion Cube in the Call of Duty: Black Ops Emblem Editor. This quick clip will teach you everything you need to know.

Love Dragonball? Show the world by using one of the titular orbs as your playercard emblem. This tutorial presents a complete, step-by-step walkthrough of how to draw it in the Black Ops Emblem editor.
Love the Xbox? Show the world by using its iconic controller as your Black Ops playercard emblem! This tutorial presents a complete, step-by-step walkthrough of how to draw it in the Black Ops Emblem Editor.
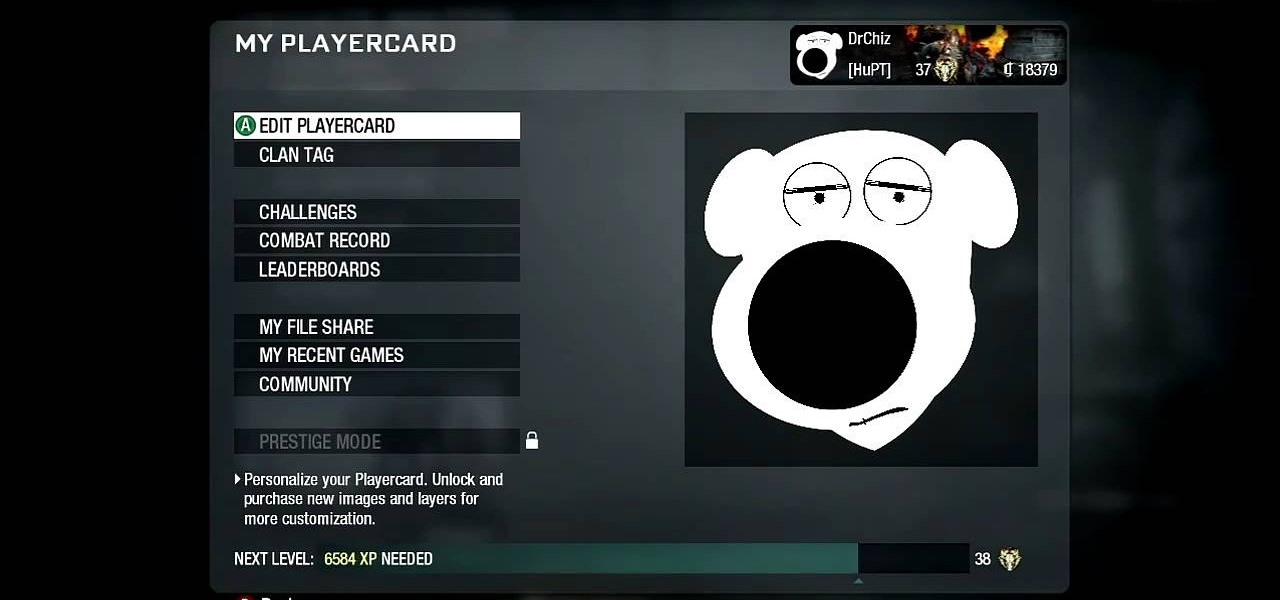
Love Family Guy? Show the world by using Brian as your Black Ops playercard emblem. This tutorial presents a complete, step-by-step walkthrough of how to draw the popular animated dog in the Black Ops Emblem editor.

Love Resident Evil? Learn how to use the umbrella logo as custom Black Ops playercard emblem! This COD tutorial presents a complete, step-by-step walkthrough of how to draw it in the Black Ops Emblem Editor.

Love Assassin's Creed? Learn how to use the Assassin's Creed logo as custom Black Ops playercard emblem! This COD tutorial presents a complete, step-by-step walkthrough of how to draw it in the Black Ops Emblem Editor.