
How To: Play specific hands in no limit Texas Hold'em
Learn how to play no limit Texas Hold'em hands after the flop with specific examples. This video will give you some great insight on how to play and why.


Learn how to play no limit Texas Hold'em hands after the flop with specific examples. This video will give you some great insight on how to play and why.
Youtube comments - some of the most beautiful pieces of rhetoric displayed on the internet. There are any number of reasons why you may wish to link directly to a youtube comment. A specific youtube comment perhaps, one that captures the essence of the emotional response a viewer might have when watching that particular Youtube video.
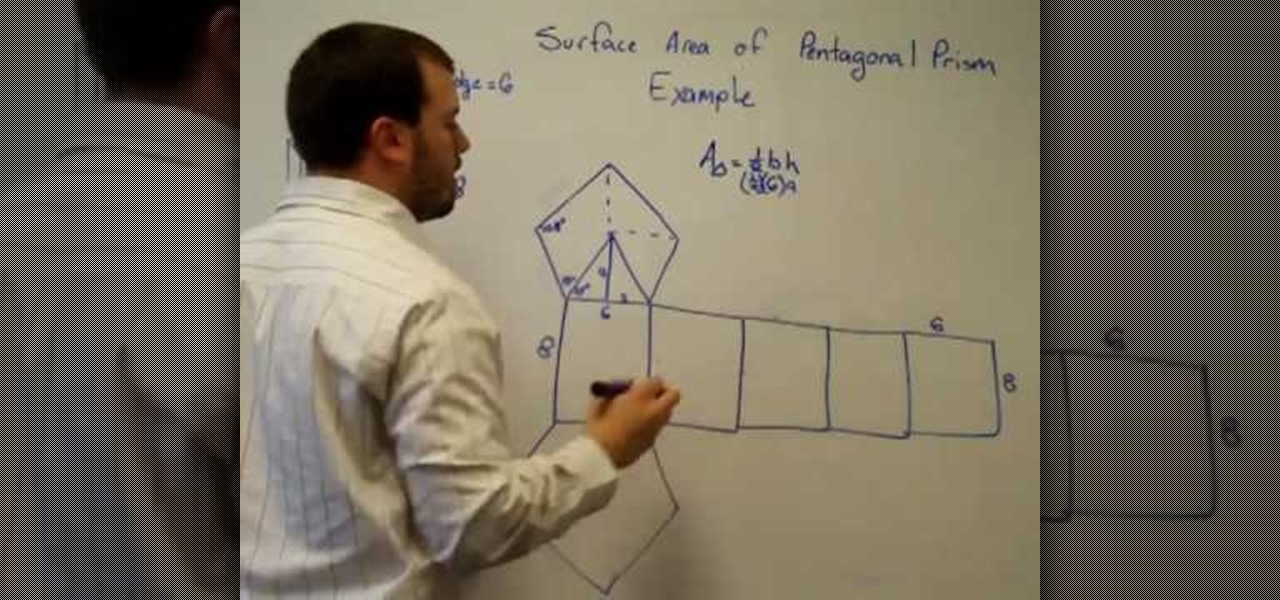
In this video, we learn how to find the surface area of a prism using a specific example. First you will need to find the base and height of your prism. If the base edge is 6 and the height is 8 you will do the equation Area= 1/2 bh. Doing this math out on your calculator, you will get the answer of 12.39. This is what the size of each triangle in the prism is going to be. The area of one pentagon (or the base) is 61.92 inches squared. If you need help with this, you can try drawing the pictu...

You can gain even greater precision on the Canon EOS 7D digital SLR camera by using Spot AF or AF Point Expansion. When you manually choose one AF point, you also have the option of changing its size. You focus point will be exactly what you want. Very specific.

Computer vision company Blippar has already dabbled with outdoor AR navigation, but now it wants to make it easier for people to make their way through indoor spaces with augmented reality.

A VPN service is almost an essential these days. Good ones can block ads, prevent tracking cookies, encrypt your internet traffic for better security, and even spoof your device's location to bypass geo-restrictions — all things you should be concerned about in the age of NSA snooping and Facebook data mining.

infosecinstitute posted a handy article about what to expect in the new year for cyber security, along with highlighting major game changers from 2015; 2016 Cyber Security Predictions: From Extortion to Nation-state Attacks - InfoSec Resources.
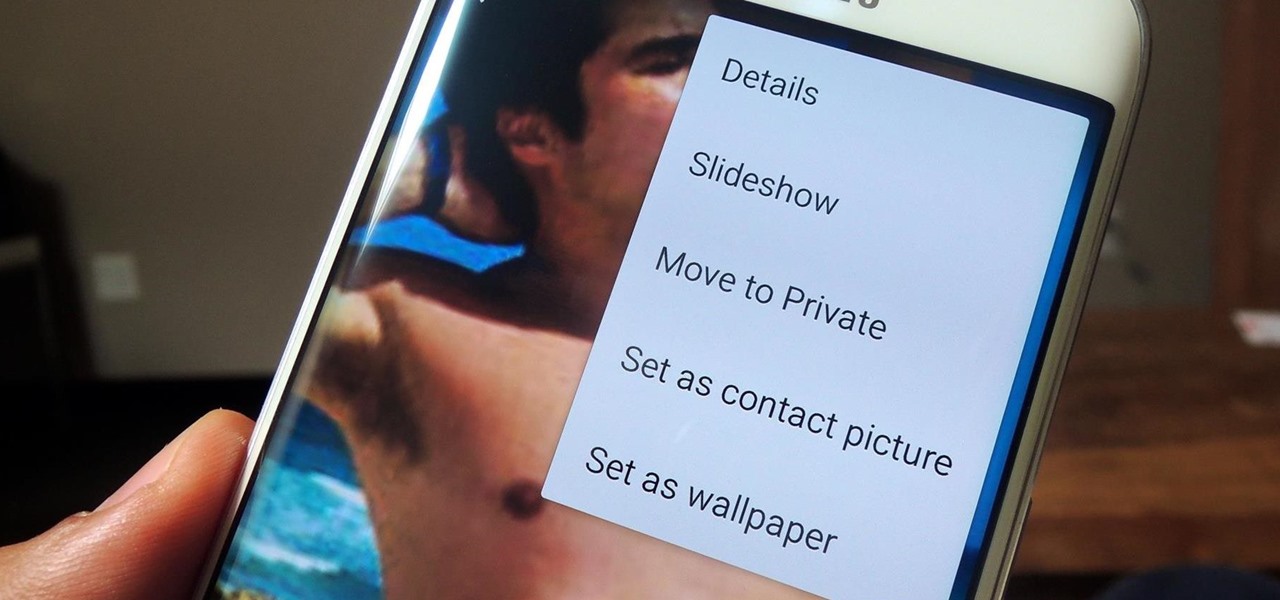
If you have a smartphone, chances are you have something on it you don't want others seeing. Whether it be photos, videos, or documents, some things are best left private. Not everyone is a saint, after all.
What can be said about Spotify that most of us don't already know? It's the most popular digital music streaming service out there, giving you access to millions of songs on your computer. However, the mobile service was once an exclusive feature for paid subscribers. Not anymore, suckers.

If there's one way to get a visceral response from someone, it's bringing up the DMV. Regardless of the reason, whether it's the long lines, disgruntled employees, or just general inefficiency, I have yet to meet a single person who doesn't mind the trip. Just look at all those happy faces.
Using ASP.NET Secure Services and Applications Services
In this video tutorial, Chris Pels shows how to use the ASP.NET IIS Registration Tool to configure ASP.NET. First, see how file extensions are mapped to ASP.NET in the IIS Manager on a global and web-site-by-web site basis. These script maps provide the basis for configuring individual ASP.NET applications to run under a specific version of the .NET Framework. Next, see how aspnet_regiis.exe, the IIS Registration Tool command line utility, is specific to each version of the .NET Framework and...

There's actually more to the dialer screen on your OnePlus than meets the eye. Besides its obvious purpose of calling people, there's a vast array of secret codes that you can input to troubleshoot your device, in addition to revealing important information, making anonymous phone calls, and so much more.

Cruise Automation is actively seeking to recruit a lead engineer to head its development efforts of 3D maps with expertise in city environments, signaling the GM driverless unit's move towards a mobility-as-a-service business model.
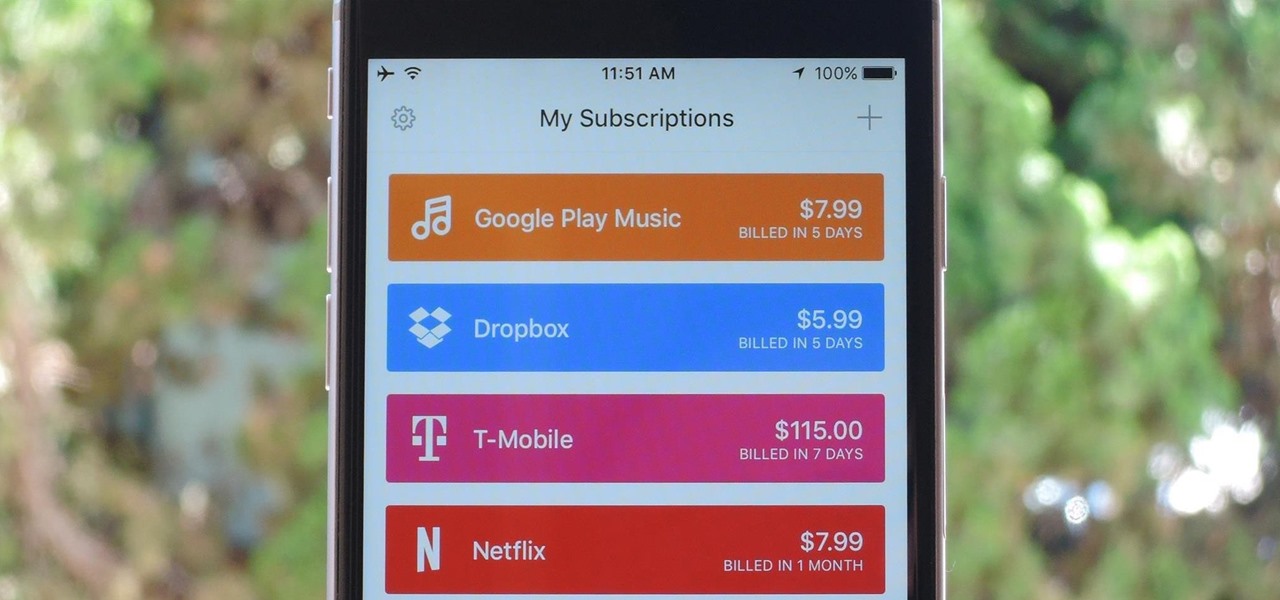
As the internet continues to become a bigger part of our day-to-day lives, we slowly but surely start to rack up a bunch of web-based subscriptions. These internet subscription services—Netflix, Hulu, and Amazon Prime, just to name a few—may seem innocuously cheap individually, but when combined, they actually comprise a significant portion of our monthly bills.
In places like underground bars or national parks, your phone's Internet service is sure to slow down to a very sluggish pace, making it difficult to surf the web. Or worst case, data will be non-existent, leaving you with only low-level network support for calls and SMS text messages.

Need to know what kind of oil your car needs? How about your vehicle load capacity? What about the standard maintenance procedures for you specific make and model? All of this and more can be located inside your owner's manual. If you don’t have an owner’s manual for your used car, you may still be able to find one even if your car is an antique.

In this video, we learn how to write a winning resume and cover letter. First, you want to remember that your resume online needs to be keyword rich, so you will have greater chances of getting an interview. To find keywords for your resume, look up different job descriptions to change your resume to fit that specific job. List your specific qualities that make you the best candidate for that job. For your cover letter, make sure you always send it along with your resume. You want to capture ...

New to Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this Excel tutorial from ExcelIsFun, the 180th installment in their series of digital spreadsheet magic tricks, you'll learn how to count specific words, specific numbers, numbers greater than a hurdle, numbers between two values, values that are NOT equal to an amount, words that end in es, all words, all numbers, all content, all blanks, all things which aren't words ...
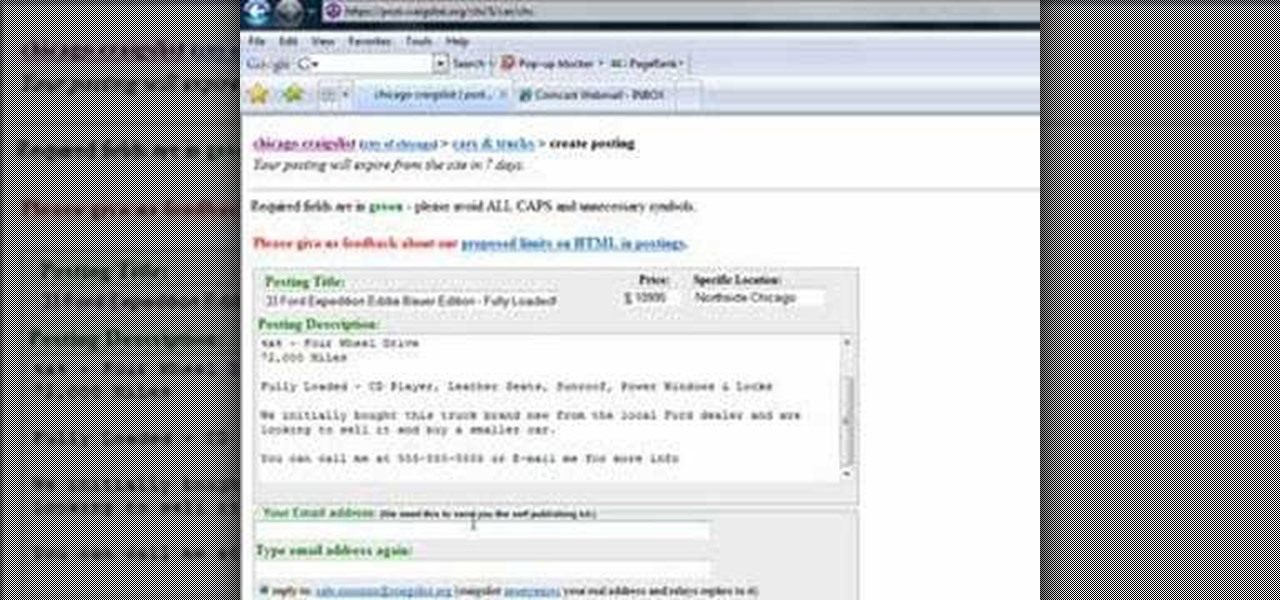
This six minute video shows you how to sell your car on craigslist. First, go to craigslist.com and click on the nearest city (or country). Follow the links to list an ad for a car for sale. You will want to put the kind of car in the posting title because that is used in sorting search results. In the posting description it is important to be as specific as possible - again describing the car, giving some history of the car like if it has ever been in an accident and if you have had any work...
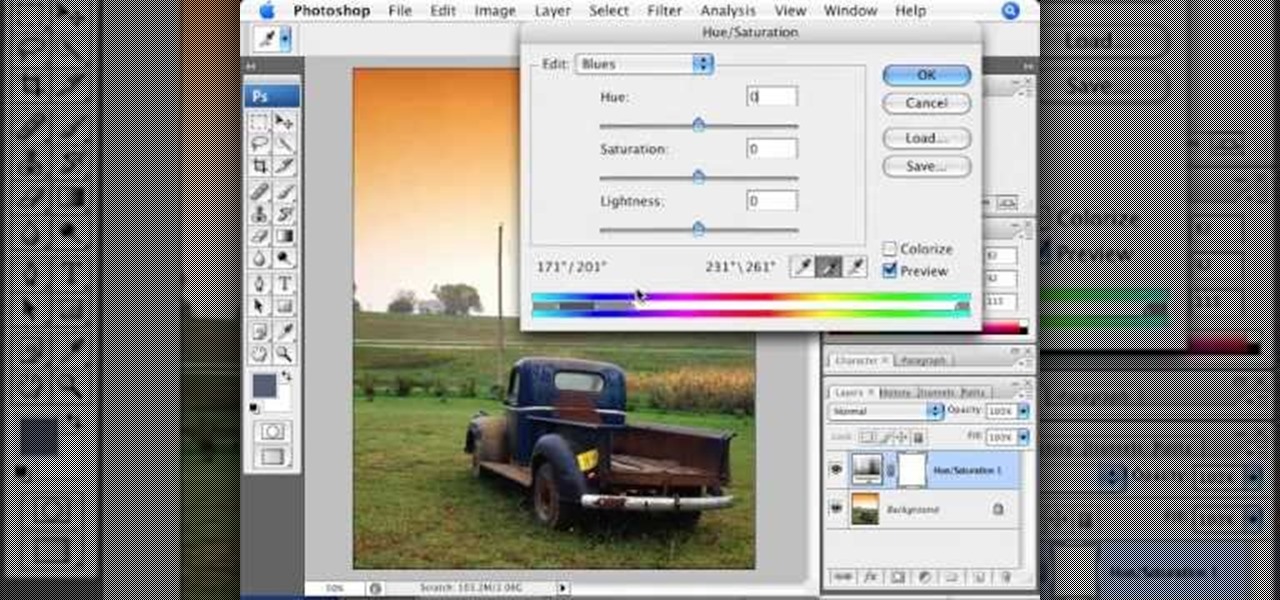
Adjusting the color of specific objects within your images in Photoshop is crucial. Sometimes fine tuning the color of just one component in an image is required. While an image may be adjusted globally at once, this approach lacks flexibility. This tutorial will show you the proper steps from the creation of an adjustment layer to the appropriate and functional calibration of the hue and saturation options. Get the most out of these tools and maximize your productivity in Photoshop.

Gathering information on an online target can be a time-consuming activity, especially if you only need specific pieces of information about a target with a lot of subdomains. We can use a web crawler designed for OSINT called Photon to do the heavy lifting, sifting through URLs on our behalf to retrieve information of value to a hacker.

It's happened to all iOS users: You're talking to a friend or watching TV, and all of a sudden, you hear "I'm not quite sure what you've said." Apparently, your phone heard something that resembled "Hey, Siri," and activated the assistant. But now, thanks to a new patent from Apple, the days of unexpected Siri may be numbered.

As competition for Spotify and Pandora, Samsung released Milk Music earlier in 2014, a free music streaming service for their Android devices. While Milk was unique to Galaxy owners only, it was popular enough that we showed you ways to get it on non-Galaxy devices as well.

Location-based app shortcuts in iOS 8 work at places like Starbucks, the Apple Store, as well as train stations, banks, hospitals, grocery stores, and more. When you're in the vicinity of these locations, a small notification appears at the bottom left of the lock screen. You you can slide up on these icons (as you would on the camera icon on the lock screen) to access specific apps based on where you're located, making it easy to access your Starbucks account when you're buying coffee or che...

Why unlock your Samsung Galaxy S3 to use with a different SIM card? One possible reason is that you love your phone, but not your cellular provider because of the poor service or an unreliable connection. If you purchased a Samsung GS3 with AT&T, T-Mobile, etc. on a contract, it might be locked for a specific amount of time called the contract period.

The Red One Camera has three buttons labeled A B and C on the back of the camera. Each of these buttons have a specific feature that is the default setting. Learn what these buttons do.
Find out how to use the powerful search functions in WonderHowTo. Learn how to refine your search to specific categories and subcategories.
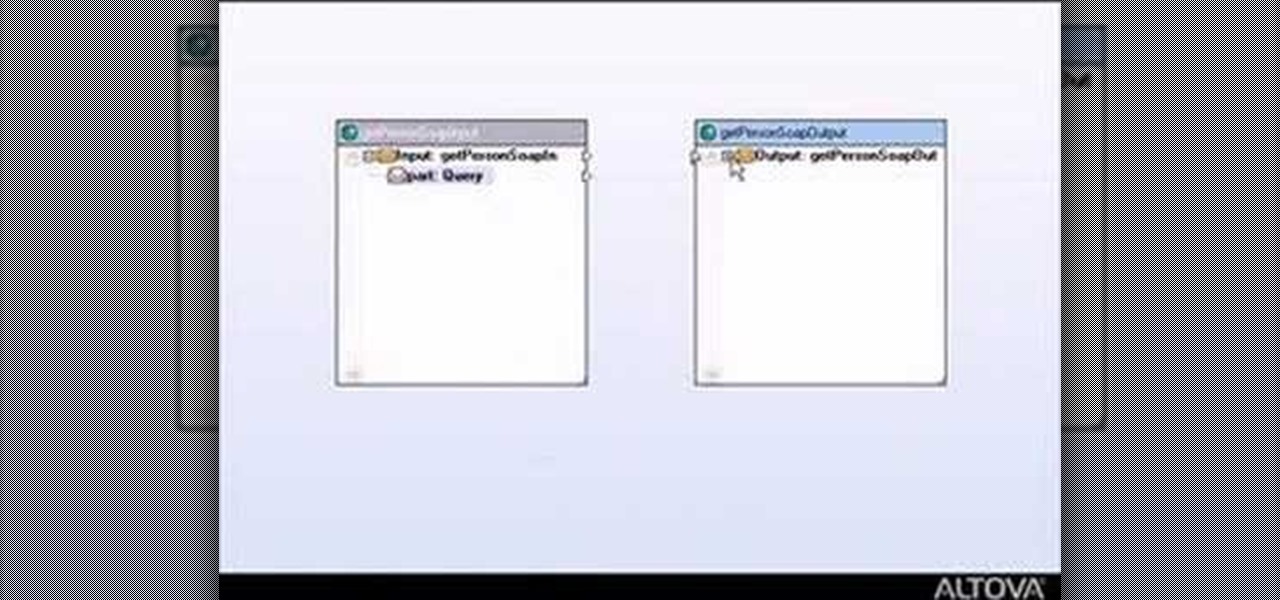
This tutorial shows you how to build web services with MapForce. Load an existing WSDL file and build a complete web service by retrieving data from databases or XML files and using a visual function builder. It's easy to build web services in MapForce as this tutorial shows.

In this video tutorial, viewers learn how to zoom in and out on a Mac computer. To access the zooming tool, begin by clicking on the Apple menu and select System Preferences. Under System, select Universal Access and check On under Zoom. In Options, users are able to set specific settings such as the maximum and minimum range of zoom. The keyboard shortcut for zooming in is: Option, Command and =. The keyboard shortcut for zooming out is: Option, Command and -. This video will benefit those v...

This video teaches you how to become a DJ. In this session we can learn how to keep the beat off beat by keeping the timing of the beats the same. This video shows the specific way of increasing the beats and decreasing the beats according to the tracks that are played. This tutorial also has a live sample of how a beat can be matched off and a how to maintain a constant interval between the beats. It also has some specific instructions on how to maintain a constant interval between the track...

While we haven't covered Amazon Web Services, or AWS, on Null Byte before, Amazon's cloud computing platform is ripe for attack by hackers, pentesters, and cybersecurity researchers. It's also an excellent cloud hosting service to build or use vulnerable-by-design AWS setups and frameworks.
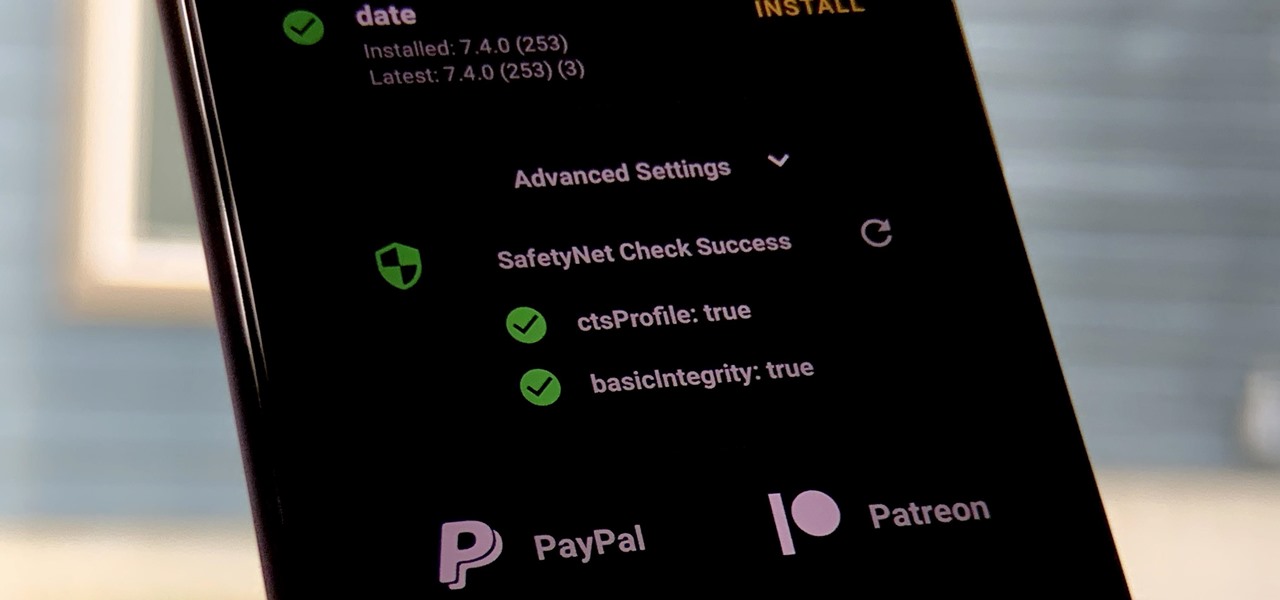
One of the longest-running cat and mouse games in Android has to be that of Google's SafetyNet feature and specific apps that can trip the flag. Many developers have resorted to using Magisk to create their modules since it can systemlessly pass SafetyNet in most cases. However, EdXposed is having some issues passing SafetyNet right now, which affects more than just your mods.

More often than not, road trips will include unforeseen pit stops that have to be made, no matter how well prepared you are. In the past, making an unscheduled stop may have led to headaches and delays when your navigation app got off track, but thanks to a feature in Google Maps, this is no longer an issue.

France's Groupe PSA (formerly known as PSA Peugeot Citroën) — one of the world's top-10 carmakers — aggressively seeks to take a lead in the rollout of the industry 's first driverless cars, as it becomes the first mainstream carmaker to announce it will launch a Level 3 self-drive vehicle launch by 2020.

When Facebook purchased WhatsApp for $19.3 billion back in 2014, we all knew this was coming—it just took longer than we thought. But starting today, the data mining became official, and now, information from your favorite messaging app is no longer out of reach for the world's biggest social media site.

You must have read news about hackers dumping the data online, recent one was Ashely Madison. It's only the big companies' data, which gets noticed once it is out. There are many other small leaks which don't even get a mention. So this article is the first one of my series which will help you to find hacked accounts. Some of you must already know about this, but this post is intended for the new learners. This also serves as an example of my learning how a good service can be used in other w...

I've been lucky enough to never be a victim of street crime, but I have read and seen too many articles and videos to completely rule it out as a possibility. You can do some things to prevent it, but if your life suddenly turns into a scene from Friday the 13th, you'll want to be prepared with some sort of way to let others know you need help. This is where Shake2Safety comes in, a free Android app from Phontonapps.
A shady practice in place by AT&T and Verizon Wireless—and possibly more wireless carriers—was recently uncovered. Outgoing data requests sent from devices on these service providers are being injected with a Unique Identifier Header (UIDH) that allows websites, the carriers, and potentially even government agencies to track your online activity.
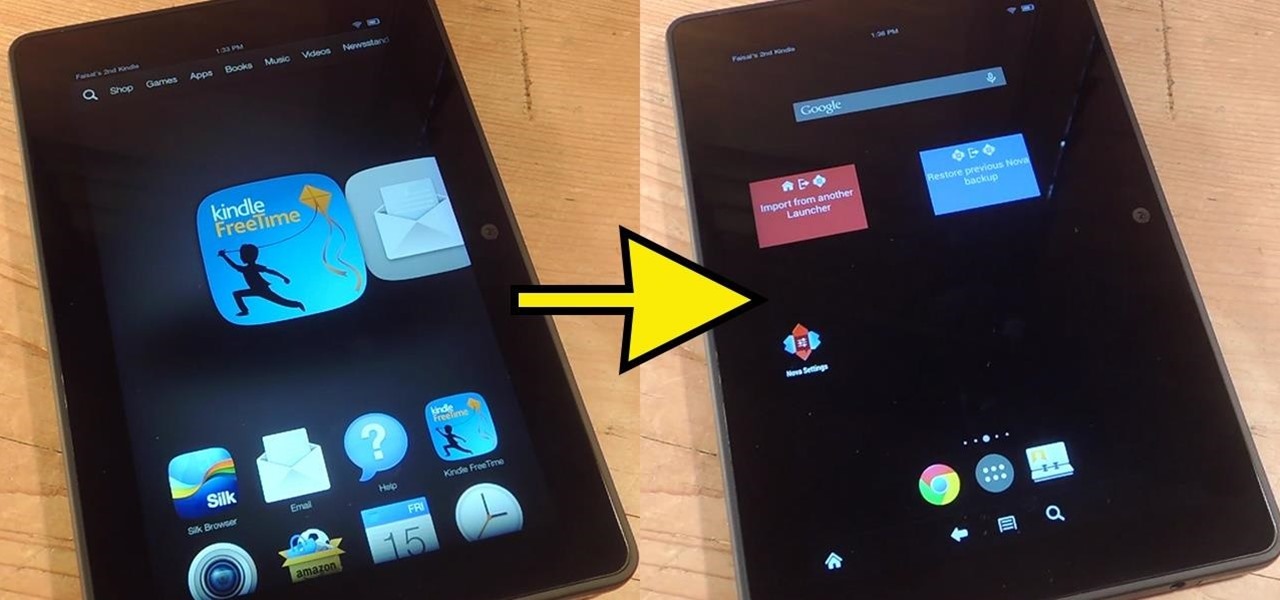
Stocked with a 7-inch LCD display and 323 PPI (pixels per inch), the Kindle Fire HDX is one of the best tablets on the market for enjoying some great literature or entertaining streaming services—and I take full advantage of what this device offers.