Welcome back, my novice hackers! Reconnaissance is one of the most important preparatory steps to hacking. As I have emphasized many times before here on Null Byte, you must know the operating system, the ports, the services, the applications, and sometimes even the language of the target to be effective. If you haven't taken the time to gather this info, then you are likely wasting your time.

There are a ton of streaming services available at your disposal in the Google Play Store—Spotify, Pandora, TuneIn Radio, Last.fm, and the list goes on and on. These apps help satisfy my day-to-day cravings for good beats, but I tend to do a little too much hopping around from music app to music app (and music widget to music widget) in the process.

Unwanted advertising is everywhere. Annoying pop-up ads, overly loud late night commercials, spam...it never ends. And before spam, there was junk mail. Junk mail is even worse because unlike TV commercials and internet ads, it's physical. You can't just delete or ignore it—and it's an awful waste of paper. So what can you do about it?
Part of the process to answer the topic question is to discover the answer to three other questions, which are: (1) Who am I? (2) Who do I want to help? (3) How do I want to help?

Music today is easily and readily downloaded, and because of that, many of us end up with giant music collections. If you're using iTunes, you can organize your music into specific playlists so that you always have what you want to listen to easily accessible. Take a look at this guide on how to create an iTunes playlist.
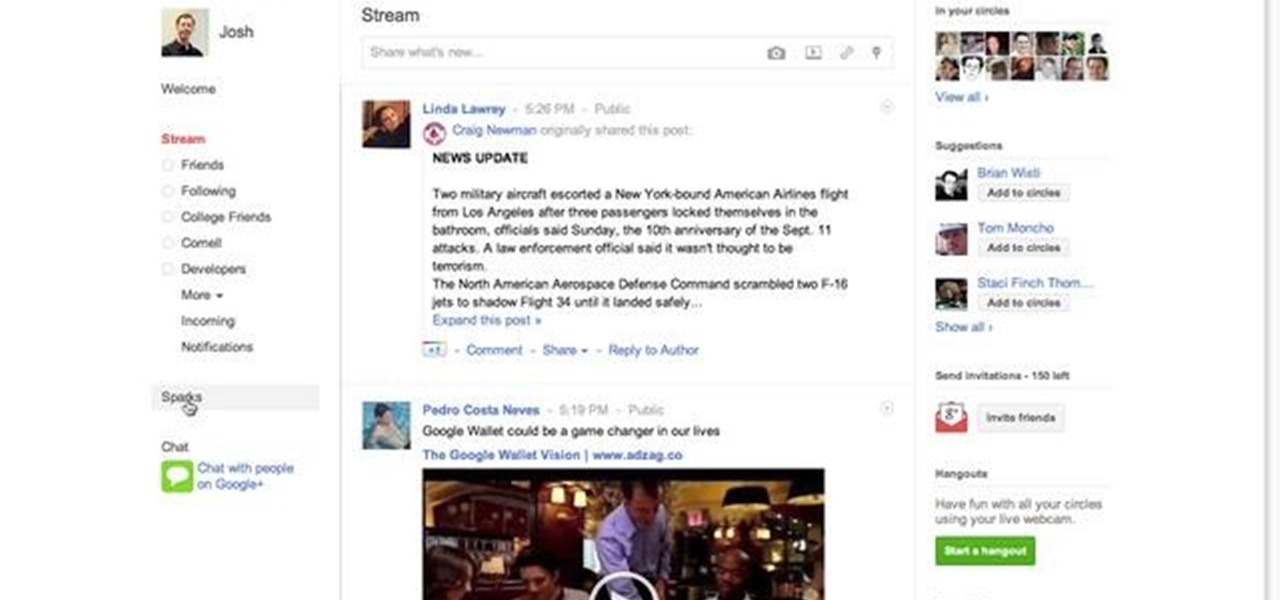
The Google+ Sparks feature is a kind of social search that allows you to find and read different articles and websites that have been selected by the people you follow and other Google+ users. It can help you find interesting posts and information on a specific topic.

Every effective combat team needs a Medic, and in Battlefield Bad Company 2: Vietnam this is especially true. This video will show you some strategies you can you to play the Medic class effectively and also analyze all of their class-specific weapons.

Steampunk may be the period-specific punk of the moment, but cyberpunk is still awesome. In this video you'll learn how to make a really original cyberpunk / goth nurse Halloween costume with makeup and some simple costume pieces.

In the studio world, and the ensemble scene, you're going to be handed ALOT of sheet music, sometimes it has only a few notes for a specific melody, and sometimes it's a whole lot of notes for the entire song. Knowing how to read these notes are important, and it can be very daunting at first, but if you practice every day anybody can read. In this video you will learn the basics of reading the notes on the staff with the note names for the treble clef.

In almost all charts and forms of sheet music, the composer will more than likely have added rhythmic dictation to the staff, a specific rhythm that he wants you to play over the progression using the chord. In this video you will get a breakdown of basic rhythmic dictation of a quarter note, eighth note and more on top of how to read these in notation format!

If you're struggling to find all the hidden spiders on Hobgoblins level, you're in luck! Some can be pretty tricky due to specific circumstances that you will need to meet and some are harder to find if someone doesn't tell you about them. In this video you will get a full walkthrough of each spider location as well as commentary explaining each location and the circumstances you will need to put yourself in to get them.

Spider-Man Noir, a universe catered to the stealthier, forward thinking Spidey. To get a full 100% play through, you're probably searching for all the hidden spider tokens. If you're lost or confused, this great video will give you a complete walkthrough of every location along with great commentary to help if you get confused on specific areas.

Learn how to create a new BlackBerry Internet service email account on a BlackBerry device running version 5 of the BlackBerry OS. This clip will show you how it's done. Whether you're the proud owner of a BlackBerry smartphone or are merely considering picking one up, you're sure to be well served by this video guide. For detailed information, including step-by-step instructions, take a look.

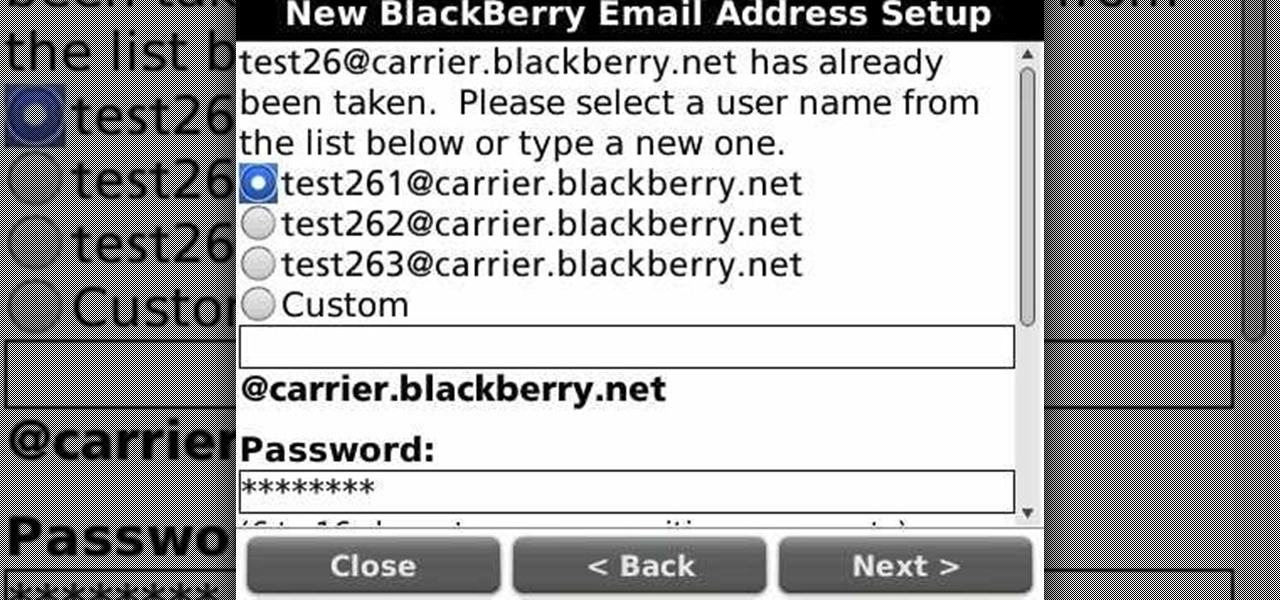
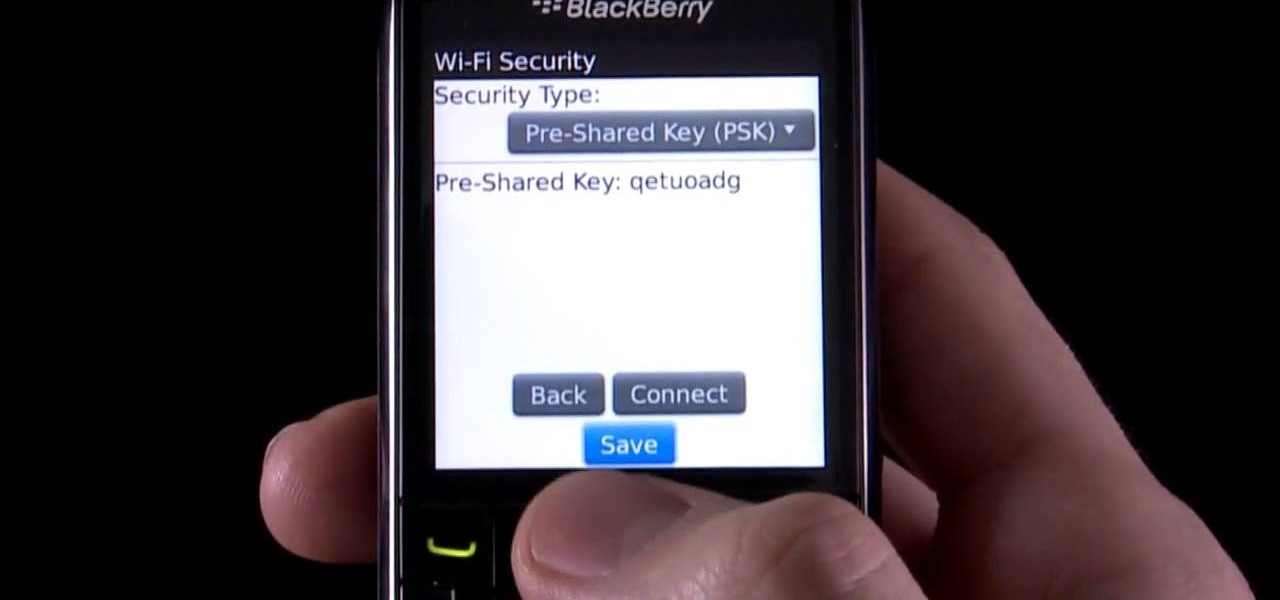
Learn how to force your BlackBerry Pearl 3G to connect to a specific wireless (Wi-Fi) network. This clip will show you how it's done. Whether you're the proud owner of a BlackBerry smartphone or are merely considering picking one up, you're sure to be well served by this video guide. For detailed information, including step-by-step instructions, take a look.

The iPhone has always been hamstrung by its alignment with AT&T, the worst of the big 4 US cell service providers. If you have an iPhone and are planning on unlocking it for use with another provider, or just want to use it without being connected to AT&T's network, this video is here to help. It will show you how to activate an iPhone instantly without a service plan using any AT&T SIM card.

Old camera equipment like flashes and lenses are often praised by modern photographers, but getting them integrated into new digital photography setups can be a challenge. This video will show you some tips for using old flashes with new digital cameras, including a great trick for making your digital camera recognize the flash by covering one specific contact. Don't get a new flash, use an old one with the skills you learn in this video.

Though the Google home page may appear simple, its search tool is anything but. This quick clip from the folks at CNET TV demonstrates a number of the search engine's most obscure and most useful features, all certain to help you to find your desired information more quickly. For specifics, and to get started using these great search hacks yourself, give this guide a look.

The guys from Achievement Hunter are here to show you not how to get a specific achievement, but instead a couple of Avatar awards. These can be used on your Avatar characters to make them look a bit more Western. The awards are easy to unlock and result in a mixture of different pieces of clothing. So check it out, pay attention, and good luck!

If you're a user of Google Chrome, you likely appreciate the browser for its speed. But were you aware the browser can be made faster still? This tutorial from Tekzilla demonstrates how to use smart shorcuts to speed up your web surfing. For specifics, and to get started using smart shortcuts yourself, watch this helpful how-to.

Origami a pine cone. First, fold the paper in 16ths both ways. Make a specific zig-zag pattern. Watch to learn more!

Eve takes us step by step through a full make-up application and is specific about the brushes and techniques that she uses.

Last weekend, some unlucky Gmail users inadvertently had their email accounts wiped out. Actually, it was 0.02 percent of all Gmail users—or roughly 40,000 of the 200 million who use the email service, due to an "unexpected bug" which affected copies of the data. Gmail does make backup files of everything, so eventually everyone will reclaim their email history. In fact, as of yesterday, Google has successfully restored all information from their backup tapes and has started returning everyon...

Military service records can teach you a lot about a person. If you want to see the service records of a friend or family member to prove their service or simply research your past, watch this video to learn how you can.

In order to build Google Chrome extensions, you will need to familiar with scripting and codes. These are small programs that add additional functions for programmers. It is a compressed directory. These files must have a particular name: i.e. "manifest" (manifest.json). An extension will have at least one of the following: browser actions, page actions, content scripts, and utility web files.

This video tutorial from DrJailbreak presents how to download and install Androidlock on your iPhone and iPod Touch.Androidlock is a type of application that locks screen to prevent unauthorized access. You have to draw a specific pattern on the screen to unlock your device. It is advisable not to create too difficult Androidlock pattern because you can forget it.You also can turn off Androidlock if you open subsettings, select More and then Mobile Substrate Add-ons option.To get Androidlock,...

Richpin's Auto Repair shows you how to properly identify the rear axle of a Jeep Grand Cherokee. This information will allow you to obtain the correct information for replacing this specific automobile part. The video will show you where you need to look beneath the vehicle to find out which style of rear axle your Jeep Grand Cherokee has. You'll be shown where to clean the dirt off of a specific area of the axle to obtain this important information. In this particular case, the rear end axle...

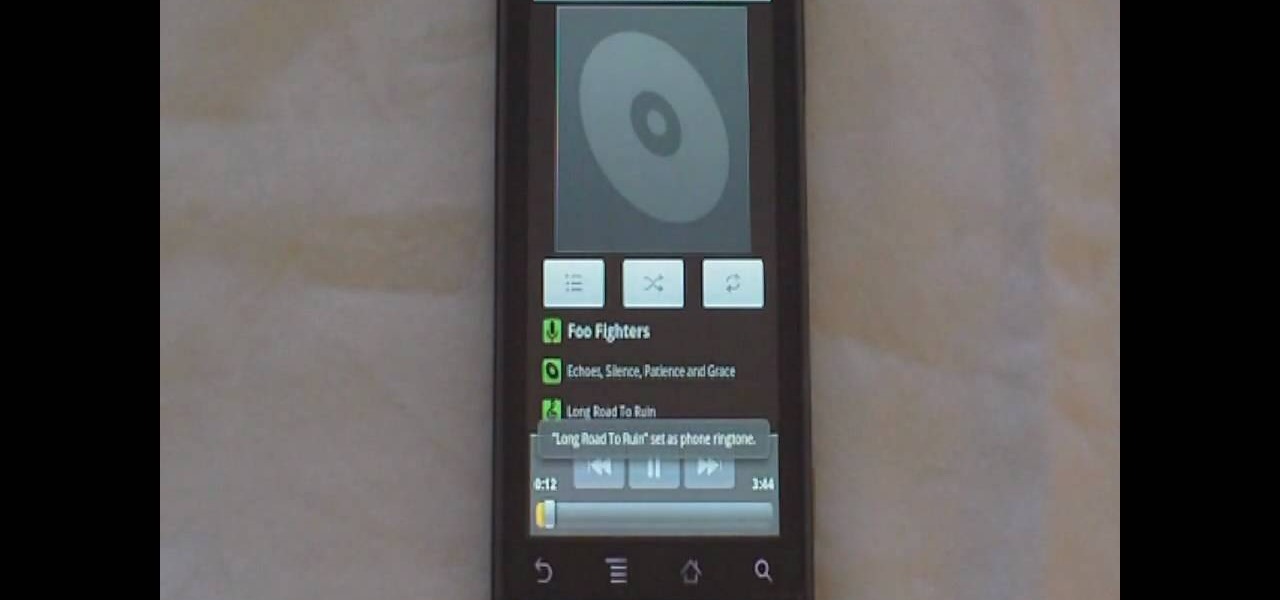
Phil from droidboards.com shows you how to set a specific MP3 that you have as a ringtone on your Motorola Droid. As long as you have this new phone and MP3's in your play list. The MP3 that you select from your phone can be used as a ringer for a specific contact and can still be used as a traditional MP3. This video will teach you step-by-step how to do it showing you on the phone while talking you through it so you can set a ringtone for any individual you want.

In this video, potter Simon Leach offers tips on how he decorates the ceramic pots that he has made. This video offers some great suggestions on decorating pottery that you have made, or have purchased unfinished. This video does not teach any specific decorating techniques, but focuses more on the process of a potter when contemplating decorating their creations. This video does cut off at the end, so do be sure to watch the continuation of Leach's tips in which he gets into more specific de...

This video describes a Taylor Swift inspired updo performed by a hair stylist. It shows the specific tools and other products that the stylist uses to get a woman with longer hair. The video suggests having a friend help, though the style could be performed by yourself. This video also shows a great way to increase the body of long hair and how important that is to create the style. One could definitely learn some hair styling tips and tricks from this video and is a great step-by-step video ...

This is a walkthrough of Halo Wars so you can beat it before your friends do. This is the first chapter of Halo Wars for XBOX 360. Check it out, a cheat walkthrough from Mahalo Gaming.

Check out this Halo Wars walkthrough. It will help you beat Halo Wars before all of your friends. This is a 3 part series for XBOX 360 from Mahalo Gaming.

In this video tutorial, Chris Pels will show how to configure an ASP.NET web site to use a specific version of ASP.NET/.NET Framework. First see how to identify what version of the .NET Framework a web site is associated with by viewing the script map in Internet Information Server (IIS). See how a script map is associated with the root in IIS and then with individual web sites. Next learn about the ASP.NET IIS Registration tool (aspnet_regiis.exe) used to configure IIS or an ASP.NET web site...

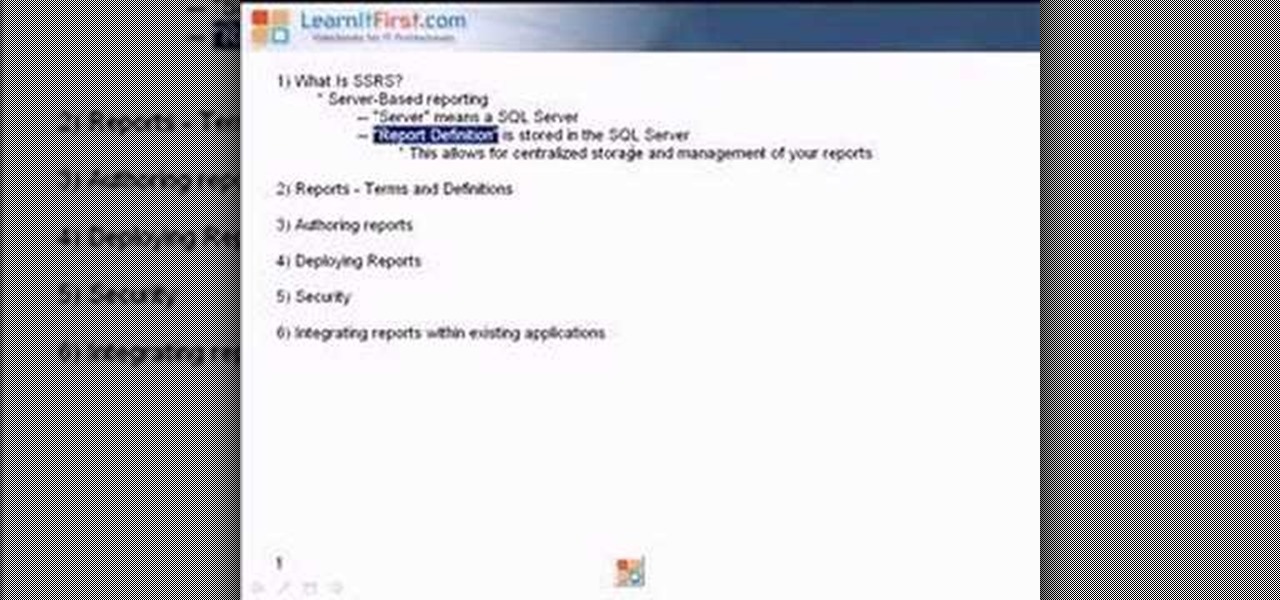
This video talks about what SQL Server Reporting Services (SSRS) is and designed for the absolute beginner - someone who wants a high-level overview of Reporting Services.

You may not have thought of dorks as powerful, but with the right dorks, you can hack devices just by Googling the password to log in. Because Google is fantastic at indexing everything connected to the internet, it's possible to find files that are exposed accidentally and contain critical information for anyone to see.

Thanks to recent reports, we now know third-party apps have a lot more access to our Gmail than we may have initially thought. In fact, these third-party apps have the ability to read our emails, not because these companies are necessarily shady, but because we agreed to it. Luckily, there's a way to view which apps have this access, as well as a way to boot those apps from your Gmail entirely.

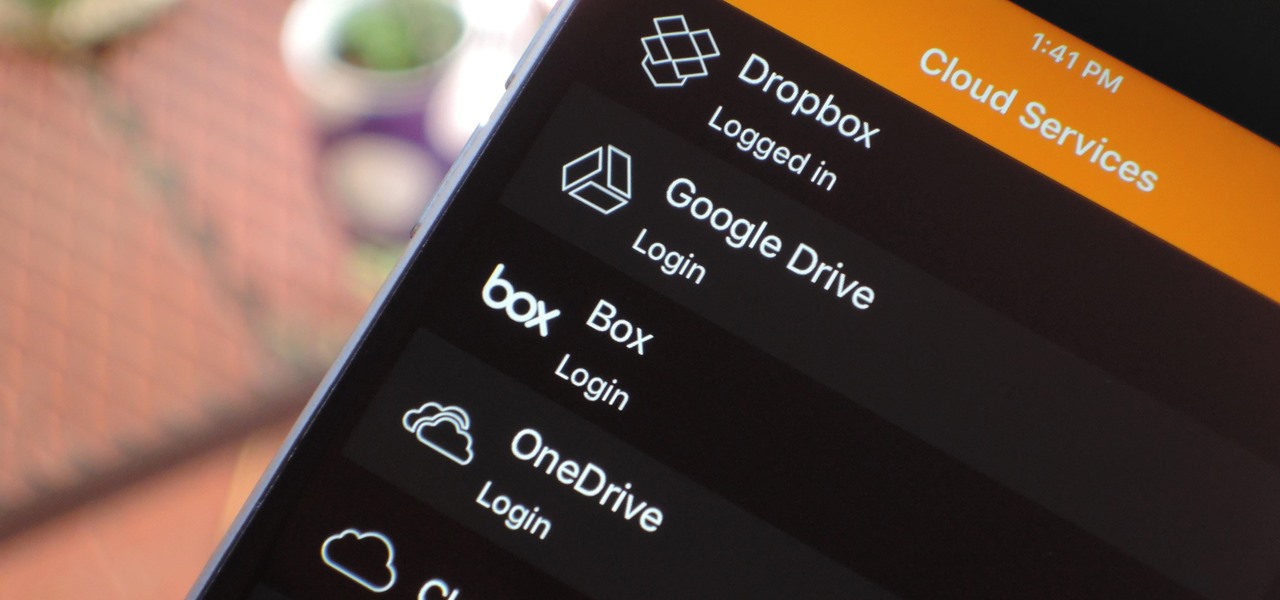
If you have movies and videos stored on Box, Google Drive, Dropbox, or OneDrive, you should definitely be using the VLC app for iPhone. After setting a few things up, VLC will let you stream videos directly from any of these services with a proper video player UI, complete with gesture controls.

Hello Friends … My name is Suresh Senarathna and this is my first “How-To” post,

A lot of people think that TOR services are unhackable because they are on a "secure environment", but the truth is that those services are exactly the same that run on any normal server, and can be hacked with the same tools (metasploit,hydra,sqlmap...), the only thing you have to do is launch a transparent proxy that pass all your packets through the TOR network to the hidden service.

If you're a U.S. expat living, traveling, or studying abroad, or just someone who typically uses virtual private networks (VPNs) in order to access the North American video libraries of services like Hulu or Netflix, you were probably surprised to see that these video streaming services don't work on your Chromecast or Chromecast 2.

This is second post in my series of posts for finding hacked accounts online. Please do read the part 1 of the post at http://null-byte.wonderhowto.com/how-to/find-hacked-accounts-online-part-1-0164611/