We all want to be healthy, but in practice, it can be tricky, especially from the fitness angle. Our lives seem busier and busier, which makes hitting the gym quite the challenge. What if we told you there was a real way to work on your fitness in the comfort of your own home — in just seven minutes a day? All you need is a chair, a wall, and a 7-minute workout app.

Smartphones have so much sensitive information attached to them. If you share your home with others, then you know the pains of trying to keep anything private. Photos are surely among the things you'd prefer to keep to yourself, so OnePlus has you covered.

QR codes are supposed to make life easier, but having to install potentially shady third-party apps just to scan one is more trouble than it's worth. Thankfully, there's a QR code reader built into all Google Pixels, but you wouldn't know it unless you stumbled across the feature.
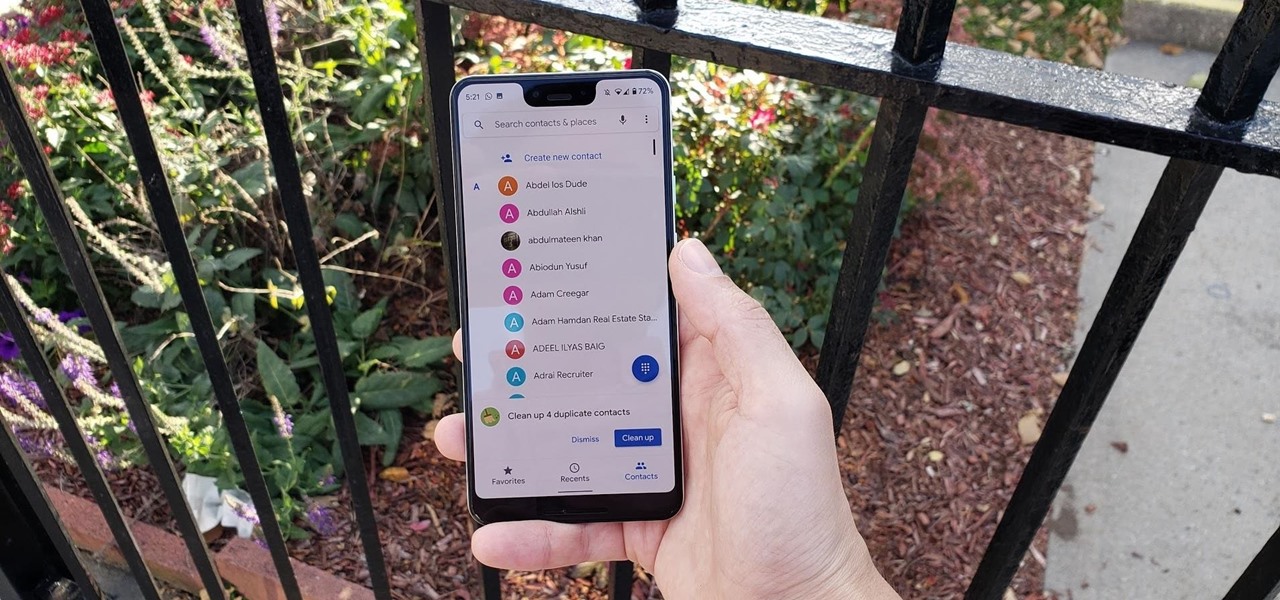
Most of us have had a cloud-connected address book for years now. The result of this is an ever-growing contact list that will continue to get harder to navigate and manage. With the increased size of our contact lists, it becomes more important to sort contacts in a way that works best for us.

iPhones aren't immune to occasional bugs. But starting with the iPhone X, performing a reboot to fix minor issues has gotten a little more tedious. Thankfully, iOS 13 has a hidden option that makes the process a whole lot simpler.

The Pixel's "Flip to Shhh" feature may not be groundbreaking, but it is useful. Third-party apps are copying it for other phones because it's so convenient. But it's not enabled by default and it's fairly hidden in the settings. So to take full advantage of your Pixel's feature set, you should learn how to use Flip to Shhh.

I don't know about you, but I go to Pandora to listen to music. So when the music stops and an audio message from an artist starts updating me on their tour dates or some new product, I get pretty annoyed. The good thing is you can turn these off.

Some may find it annoying to get YouTube notifications randomly throughout the day. Every time a YouTube channel uploads a video, every time someone replies to your comments. But at the same time, you don't want to turn off those notifications so you don't miss out. Well thankfully, YouTube offers a happy medium where you can get important notifications, but only get them once a day at your desired time.

Did you know that the YouTube app can tell you how much time you've spent watching videos? If you're like me, you'll be surprised to know exactly how much of your life is spent inside the popular app. You can get a specific breakdown of how much you YouTube you consume.

Let me paint a picture for you. You're on a long flight home, and while listening to music on your Samsung Galaxy S10, a great song comes on. You want your friend to hear it too, who's also listening to music using a pair of Bluetooth headphones. Thanks to Dual Audio, you can easily share your experience.

Despite the recent gut punch of staff layoffs, Canada-based smartglasses startup North and its Focals are likely to be in the game for a while longer.

Many of our online accounts now come with an added two-factor authentication (2FA) functionality to help keep our data safe. This essentially means no one would be able to access the account until a specific set of requirements were met. It could be a combination of a password with a security key or even a passcode with some form of biometrics, like a fingerprint or face scan.

If you're ever faced with a situation of handing over your iPhone to law enforcement (or getting it taken forcibly), whether by the police, feds, or court system, there are things you can do to prevent them from getting access to all that potentially self-incriminating data. And it takes less than a second.

Every year, fans of Irish culture, as well as those looking to celebrate their own culture, come together on St. Patrick's Day, March 17.

We're still weeks away from a probably HoloLens 2 release, but Microsoft's immersive computing team is still hard at work on other aspects of its "mixed reality" ecosystem.

Samsung isn't set to reveal its latest and greatest — the Galaxy S10 line — until February 20, but that hasn't stopped leaks from giving us an early taste. While we already know what the rumored devices will probably look like, we now have access to their wallpapers as well. Apple fans don't need to be left out of the fun — someone has already cropped these images to fit your iPhone's display.

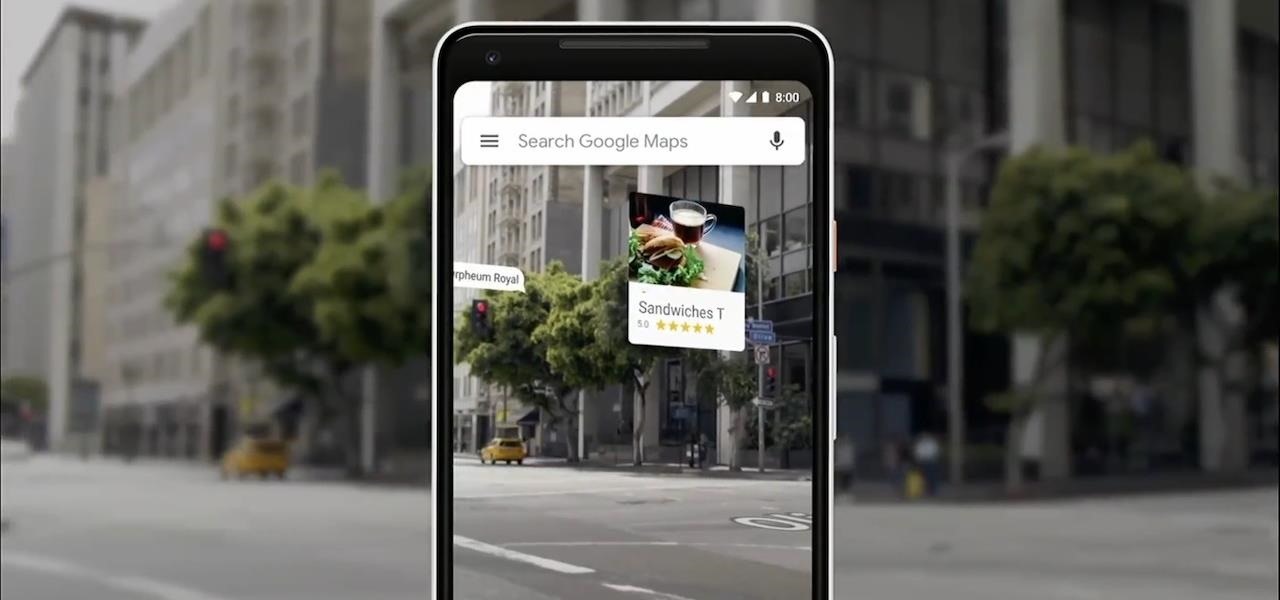
The augmented reality walking navigation mode for Google Maps appears to be closer to an upcoming release for the general public.

If there was a version of the Doomsday Clock for counting down the release of Microsoft's HoloLens 2, then the caretakers of that imaginary clock would move the minute hand to "one minute to midnight."

Whether it's for health reasons or just to look better, many of us want to get in shape. It's a long process that starts with nutrition, and dieting is never easy. Fortunately, there are some great food-tracking apps that will make it a lot easier to become a healthier version of yourself.

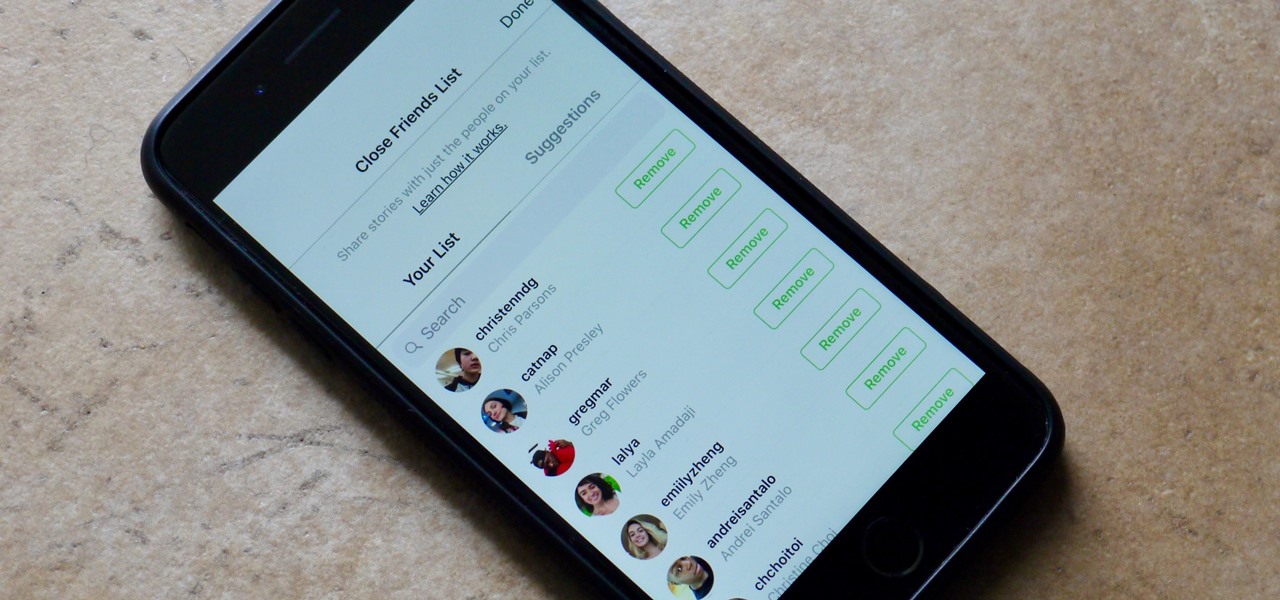
Stories make sharing your day-to-day highlights fun on Instagram. However, other than choosing who to hide stories from, by default, stories don't have much privacy control, especially if your Instagram account happens to be public. Instagram recognizes this flaw, which is what its "Close Friends List" is all about.

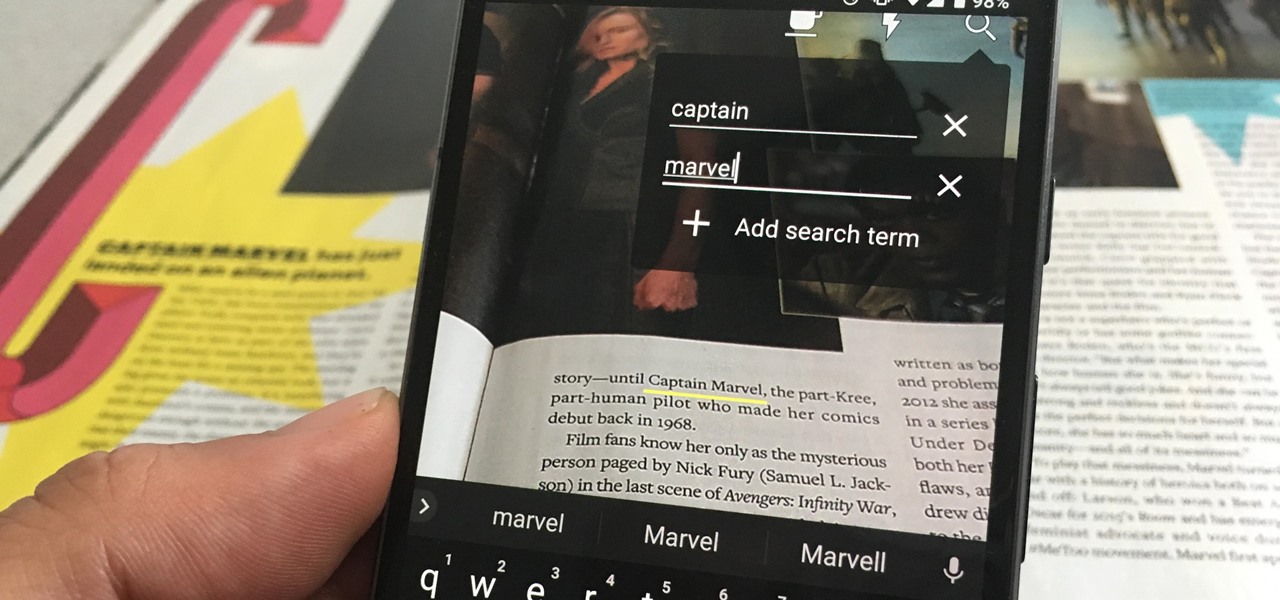
One of the neatest tricks available in Google Lens, an app that can identify and interpret real world information, is the ability to copy text from the app's camera view and paste it into a digital document.

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

Magic Leap has been promising to launch a developer conference for years, and now the company is finally making good on that promise. On Wednesday, Magic Leap sent out the official announcement for its first L.E.A.P. conference, which will be held in Los Angeles in October.

With Android Pie, Google added a genuinely useful feature for Pixels called App Suggestions, which uses AI to predict the apps you might want to use next. These show up at the top of your app drawer and in the new dock in the revamped multitasking UI for quick access. But here's the trouble: Muscle memory is a thing.

Netflix is branching out into the comic book business, and it's summoning augmented reality via Facebook to make the first issue more magical.

Location services company Mapbox has added new capabilities to its location-based gaming tool to fend off Google's challenge for the same mobile app category.

When it comes to augmented reality apps, visually immersive experiences are plentiful, but audio experiences are somewhat underrepresented. A new app for iPhones and iPads seeks to shift the AR paradigm toward the latter.

Following in the augmented reality footsteps of Pokémon GO, Universal Studios has decided to give us an AR version of Jurassic World.

Attention LG V30 and G6 owners — Android 8.1 is coming to a device near you. While fans of LG's latest smartphones are still stuck on Nougat here in the US, we now have confirmation that Oreo's first major update will find its way here, even if we aren't sure when.

Dating websites allow you to see a person in a very intimate context, framing their successes and accomplishments in life to an important audience. The information contained in these profiles often can't be found elsewhere, offering a unique look into the personal life of the user.

As awesome as the 2017 Galaxy lineup may be, few can forget the monstrous disaster that was the Note 7's exploding battery. Needless to say, the last thing Samsung wanted was another news story about a problem with the Note 8's battery. Unfortunately, that's exactly where we find ourselves today.

Just nine days after the official release of iOS 11.2, Apple has released iOS 11.2.1. The update initially seems to have been seeded to only a handful of users and is intended to fix bugs in 11.2.

Ransomware is software that encrypts a victim's entire hard drive, blocking access to their files unless they pay a ransom to the attacker to get the decryption key. In this tutorial, you'll learn how easy it is to use the USB Rubber Ducky, which is disguised as an ordinary flash drive, to deploy ransomware on a victim's computer within seconds. With an attack that only takes a moment, you'll need to know how to defend yourself.

While The Walking Dead has brand recognition for its AR game, ARZombi has ARKit.

Hyundai Motor Company says it will launch its driverless tech ahead of schedule, but the Korean carmaker will remain behind mainstream rivals, including General Motors (GM), Nissan, and Honda.

If you haven't heard yet, Google is revamping the Play Store with version 8.0. While it so far doesn't seem to have any life changing features, there are ones that certainly will make your life easier, like their new updates feature.

Thanks to Apple's ARKit, a new app will let iPhone users measure distances through the magic of augmented reality.

There is now another way for doctors to use augmented reality in operations. This time, it's for plastic surgery — Specifically facial surgery.

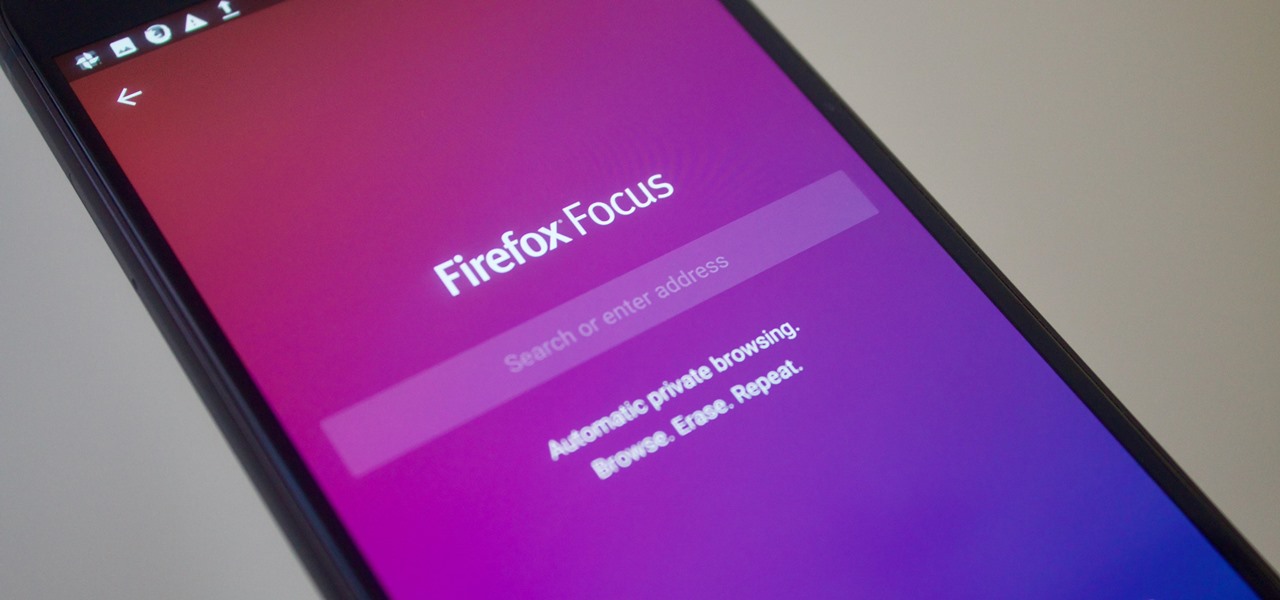
Firefox Focus is Mozilla's effort to make your internet experience a little more secure. Originally released in November 2016 for iOS, Focus blocks internet trackers, search history, anything that gets in the way of a clean, private browsing experience.

Social engineering makes headlines because human behavior is often the weakest link of even well-defended targets. Automated social engineering tools can help reclusive hackers touch these techniques, but the study of how to hack human interactions in person is often ignored. Today, we will examine how to use subtle, hard to detect persuasion techniques to compromise a human target.