As the Chromecast becomes more and more popular (it's even available overseas now), the market has seen an avalanche of Chromecast-compatible apps. We can play games, cast TV stations, and even mirror our screens, but today I'm going to show you a multifaceted tool that'll do everything from broadcasting your camera to displaying your documents.

After much hype and even more leaks, the HTC One M8 has finally been unveiled at the company's New York release announcement.

As softModders, the first thing we do after updating to the newest version of Android is to root, install a custom recovery, and install a superuser app. By doing this you open up your HTC One to a vast quantity of new apps and tweaks you can use to truly make your phone One of a kind.

Welcome back, my novice hackers! I have tried to emphasize throughout this "Hack Like a Pro" series that good reconnaissance is critical to effective hacking. As you have seen in many of these hacks, the techniques that we use are VERY specific to the:

The Samsung Galaxy S5 was just officially announced at Mobile World Congress. The new flagship device will be available worldwide beginning April 11, 2014, including all major U.S. and international carriers. With over 200 million Galaxy devices sold to date, the S5 doesn't stray too far from the trend, at least not aesthetically. We've still got a high-grade plastic shell with perforated back covers, and four color choices at launch. Our highlights of the release event are as follows.

Whether you have the original Nexus 7, or the 2013 Nexus 7 tablet, rooting it will give you access to tomorrow's features, today.

The flexibility within Android is pretty amazing. Unlike iOS, you can make a lot of modifications with nothing more than a download from Google Play, but to really step up your softModder game, you'll need to go a little further.

If you're marginally inclined towards computers, you've probably been approached at some point by a family member who wants you to "fix" their system during a visit home. With the holidays coming up, these opportunities (or ambushes) are even more likely.

When it comes to the user interface, you're pretty much limited to the stock one that comes on your Samsung Galaxy Gear smartwatch—a carousel of large black and white icons representing the features and applications on the watch.

Just because a problem is small or superficial doesn't mean it can't annoy the living crap out of you. Others may think you're overreacting, or even have the audacity to roll their eyes, but you're in your own personal hell.

If you've seen our guide on the 18 coolest features in iOS 7, you know that there's a lot to like about Apple's new mobile OS, but there's also a laundry list of grievances to go with it. One that bugs me is the lack of Home screen customization, something that has always driven me to jailbreak in the past.

One of the most heated topics in the Android community now (and probably forever) is stock Android, with lots of users requesting the ability to use it rather than the manufacturer's skin.

You probably already know what you want to do when you grab your phone. More than likely, you're either going to make a call, send a text, or open an app. So why can't you just do that right from your Samsung Galaxy S3's lock screen?

Welcome back, my aspiring hackers! As mentioned several times in previous Linux tutorials, nearly everything in Linux is a file, and very often they are text files. For instance, all of the configuration files in Linux are text files. To reconfigure an application in Linux, we simply need to open the configuration file, change the text file, re-save, and then restart the application and our reconfiguration is applied.

The shortest distance between two points is a straight line, but the shortest way to launch an app on an iPhone can be a much more complicated process.

Welcome back, my rookie hackers! When Wi-Fi was first developed and popularized in the late '90s, security was not a major concern. Unlike wired connections, anyone could simply connect to a Wi-Fi access point (AP) and steal bandwidth, or worse—sniff the traffic.

Everyone hates to feel like they've been taken advantage of, especially when buying a used vehicle. The thought comes across every car buyer's mind... "Did I just get taken by that smooth-talking salesman?" When it comes to cars, how do you know if you're really getting a good deal, or if you're being offered a fair price for your car? After all, cars are most peoples second largest investment, so we need to make this decision wisely.

Welcome back, my budding hackers! I began this series on Linux basics because several of you have expressed befuddlement at working with BackTrack on Linux. As a hacker, there is no substitute for Linux skills.

One thing you can always count on from Google Play is a never-ending list of lousy launcher apps. Just search for "launchers" on the store and you'll see hundreds of apps hoping to replace the one you're already using. Problem is, none of them really stand out from the crowd. If you're not interested in a stock-look or iOS clone, you're out of luck.

There are hundreds of keyboard shortcuts out there, but these 7 are the ones you'll definitely want to remember. I use them every day, and you should too. Step 1: Tab Domination

Welcome back, my nascent Hackers! In my last blog, we looked at a passive way to gather information necessary for a hack. The advantage of using passive recon is that it's totally undetectable, meaning that the target never knows you're scouting them and you leave no tracks. The disadvantage, of course, is that it's limited to only some websites and not entirely reliable.

Welcome back, my novice hackers! Most of my tutorials up until this point have addressed how to exploit a target assuming that we already know some basic information about their system. These include their IP address, operating system, open ports, services running, and so on.

An average of 140,000 hard drives crash in the United States each week, according to online backup service Mozy. Additionally, 70 percent of Americans have lost a laptop, smartphone, or tablet, and the average person now loses 1.24 devices each year—less than half of which are ever recovered.

Ever use Nexflix and YouTube on Your Nexus 7 tablet? It sucks! The menus are too big and not enough videos are shown on the screen. What gives?!?

If you're an avid PC gamer, then you're probably well familiar with the term overclocking, which is basically just tweaking your computer hardware to run faster than it was originally intended.

One of the best aspects of Android is its customization options. You can change launchers and icons, add widgets, and replace standard apps with others that allow full customization. Android allows your device to really take on your personality, from the inside and out.

Steampunking Nerf guns by painting them is a pretty common practice among Steampunks, but unfortunately, the really amazing-looking ones involve literally taking the gun apart, painting it, and then screwing it all back together.

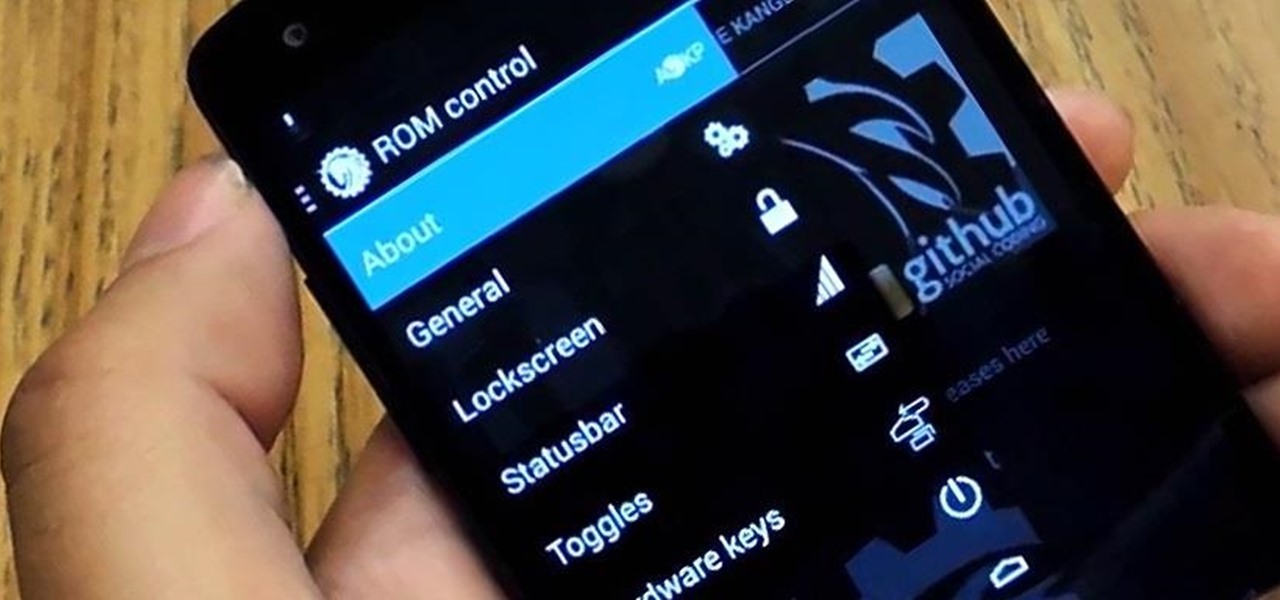
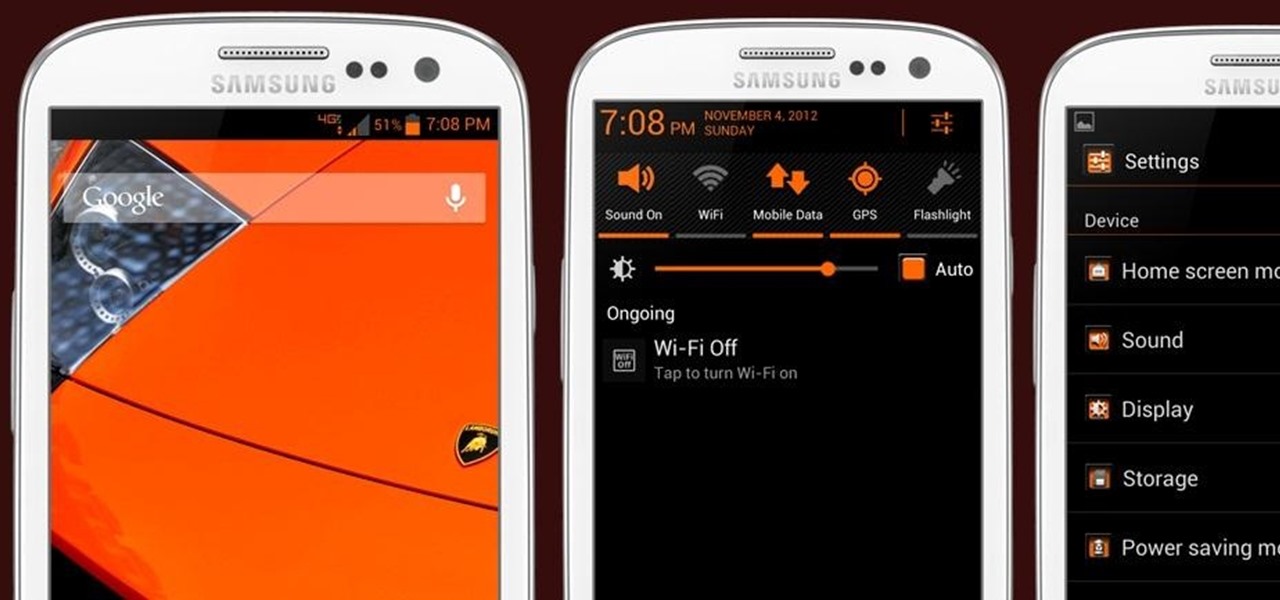
One of the best things about the Samsung Galaxy S3 is the ability to modify the device in countless ways, as with any other Android device.

It's a controversial headline, I know, but bear with me and I'll explain in due course. Disclaimer: I was once a child, and I played lots of video games. I didn't look anything like this child.

One of the most frustrating things on the Internet are sites that make you register just to view content. I'm not talking about paywalls—I mean the sites that make you give them personal information to look at free articles or forum threads. Most people are uncomfortable with this because a lot of these sites either spam you themselves, or sell your information to someone else who will.

Changing the carrier name from an unlocked iPhone's status bar has been possible to do ever since Cydia released Zeppelin earlier this year. The application comes with preset logos you can use such as Pac-Man, Space Invaders, the Assassin insignia of the Assassin Order from Assassin's Creed (well, that was a mouthful) and my personal favorite...

One of the more enjoyable parts of Christmas (other than opening gifts of course) is going out to find the perfect tree, struggle bringing it into the house, and decorating it. As the years went by, I realized that our tree looked exactly like every other tree in the neighborhood: the same lights, the same angel at the top, and the same red, green and white ornaments.

Once you have the skills to bring your ideas to life, the hardest part is coming up with ideas. What do you do when you can't think of something to make? What happens when your well of inspiration runs dry?

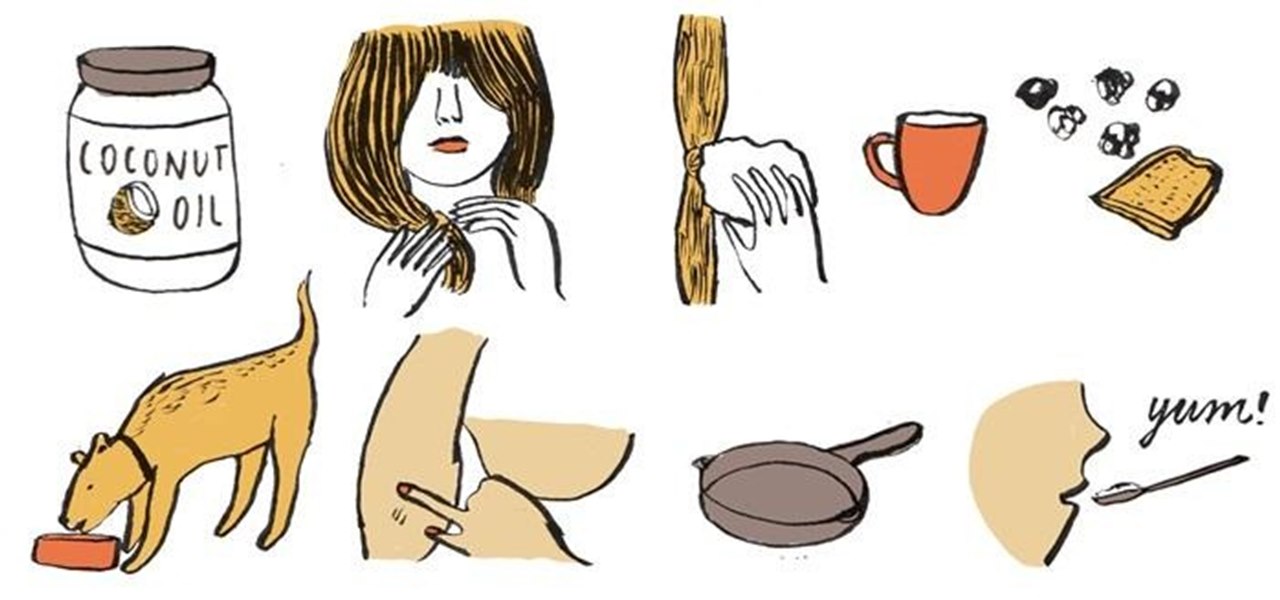
What can't coconut oil do? This edible oil, extracted from the copra or meat of a coconut, has done what most other food, beauty, and health trends have not: demonstrated real lasting power. Indeed, the "superfood" continues to make headlines, with its many uses the subject of debate, study, and fervent support. From the obvious (cooking) to the less so (home improvement), there are likely many coconut oil uses you're not yet aware of.

Let's say that you've got the look down, and you have your Steampunk props all ready to go. Congratulations! You're a Steampunk!

A travelator, also known as a moving walkway or moving sidewalk, seems like a tricky thing to build in Minecraft, especially when it's zigzagging, but there are really simple autowalks out there (like this one).

When it comes to milk, my family consumes anywhere between two and four gallons every two weeks. That's about four to eight gallons every month. That's a lot of milk—and a lot of empty milk jugs! Instead of simply tossing them in the recycling bin, why not get creative and make something useful out of them yourself?

Firstly, let me say a few quick things: Once built, this is a lazy (one button) way to harvest melons, but this is going to be a complex and lengthy build.

Here at WonderHowTo, we've been following the Minecraft LEGO set for quite some time, through its development on LEGO CUUSOO (a LEGO site where users can submit ideas for LEGO sets) to its eventual implementation.

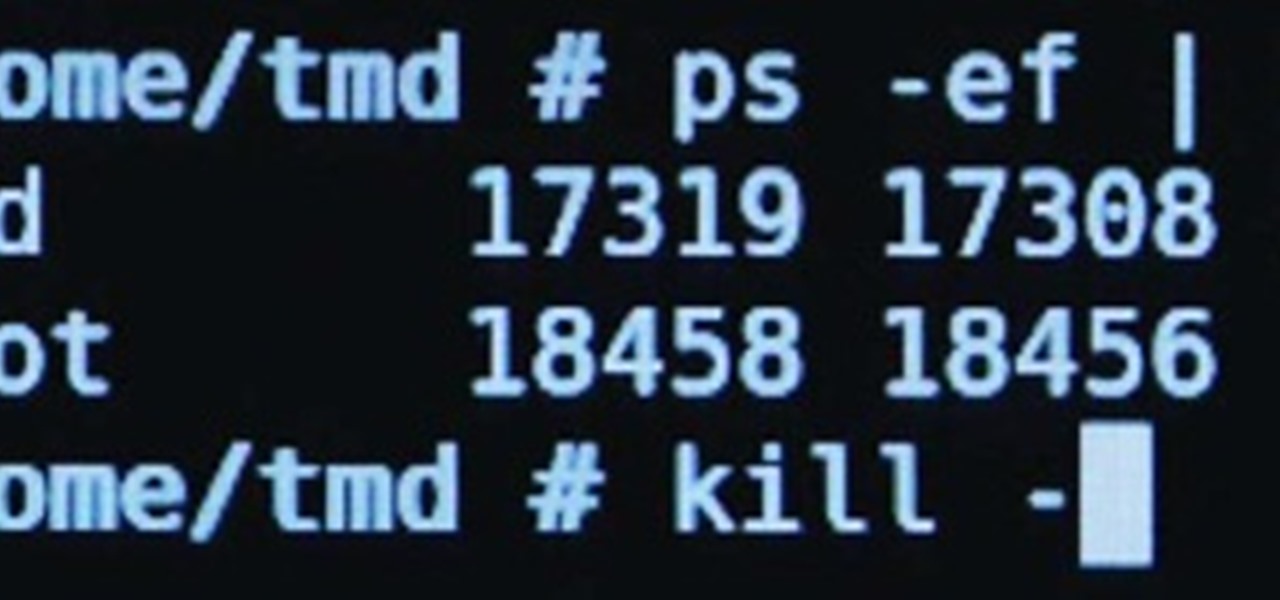
I may be a bit weird, but I enjoy listening to music at night as I fall asleep. Sure, you could create a playlist of songs so that it stopped after all the songs finished playing, but I have a rather extensive database of music and I enjoy listening to them randomly. Also, I like to ensure it terminates after a specific amount of time (I don't want it playing all night). Or sometimes I use it when I am cooking so that when the music stops, I know I need to check on my food, etc.