This video massage tutorial shows how to perform a Swedish massage on the arms and legs. The massage strokes are demonstrated twice to give a detailed explanation of the technique and specifics of biomechanics as well as show the flow of a good massage. Watch this instructional video and learn how to give a Swedish massage on the arms and legs.

Proper breathing is a very important part of Pilates exercise. Many Pilates exercises are taught with specific instructions on how to use the breath with them. Often in our daily lives our breath becomes very shallow, most people only breathe into the upper part of the chest. Watch this pilates how to video to learn proper breathing techniques.

Learn live saving techniques by watching this how to video. This video teaches you how to use a pocket mask and perform CPR on a baby. Because babies are much smaller than adults it is important to follow specific guidelines to save their lives.

In this video golf lesson instructor Steve Bishop discusses some tips on a specific pre-shot routine for the full swing and the reasons behind each part of the routine.

This video shows you the proper technique to draining the engine fluids from the radiator and connected hoses before removing the engine for disassembly. Explains the process for using your specific engine repair manual to label all of the wiring, vacuum lines and hoses so that installation later will be smooth.

If you know how to use After Effects, you're probably very familiar with the ability to add 3D lights to a scene, and allow them to interact with 3D layers. In 3D applications like CINEMA 4D, lights are an essential part of your project, but how do you make them look at a specific "point of interest" or object? This tutorial shows you how.

If you use After Effects you have become familiar with the Work Area, a range of time that allows you to focus on a specific range of time. You can work exclusively in this area, or work in the larger time of the composition, only to preview or render that area of time when you go out to final. In CINEMA 4D, users can achieve similar results using the Preview Range. This tutorial will show you how.

If you're reading this, you're likely a tech-savvy coding pro whose analytical talents are mostly applied to designing apps, cracking passwords, and infiltrating networks — all of which are admirable activities for both aspiring and seasoned white hat hackers. But there are other profitable ways that you can put these types of skills to use, namely in the world of investment and trading.

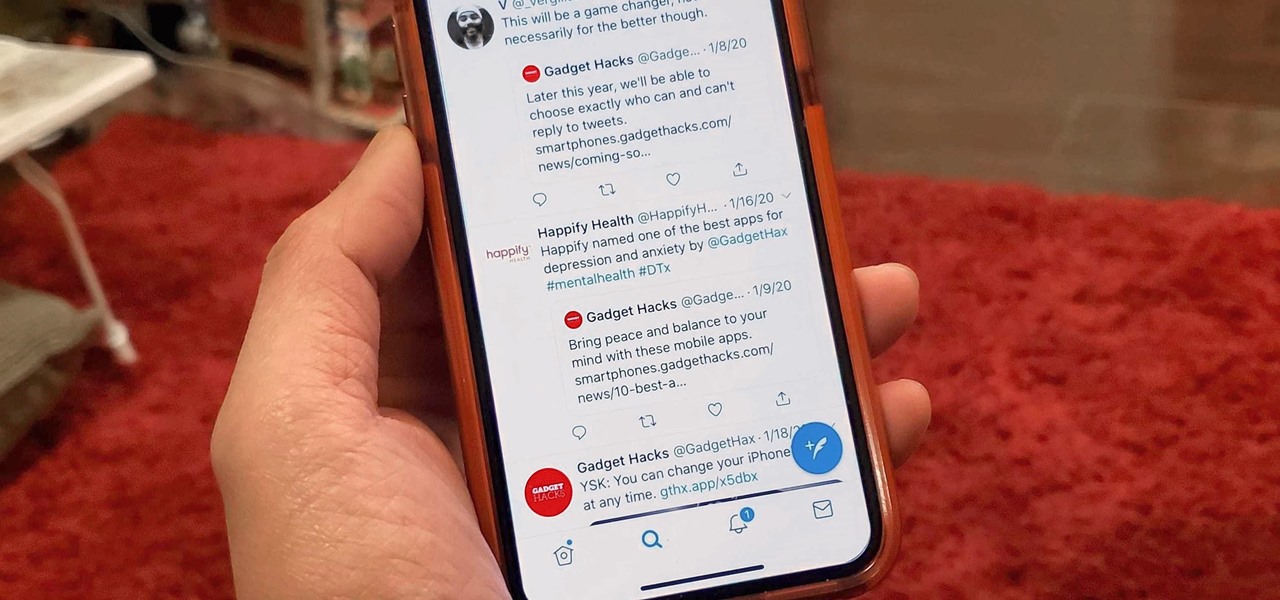
If there's an influential tweet, you can see what people are saying about it by reading its comment thread. But what about quote tweets, aka tweets someone posted on their own timeline that quote the initial tweet? These don't show up in comment threads, but there is a way to find them.

QR codes are supposed to make life easier, but having to install potentially shady third-party apps just to scan one is more trouble than it's worth. Thankfully, there's a QR code reader built into all Google Pixels, but you wouldn't know it unless you stumbled across the feature.

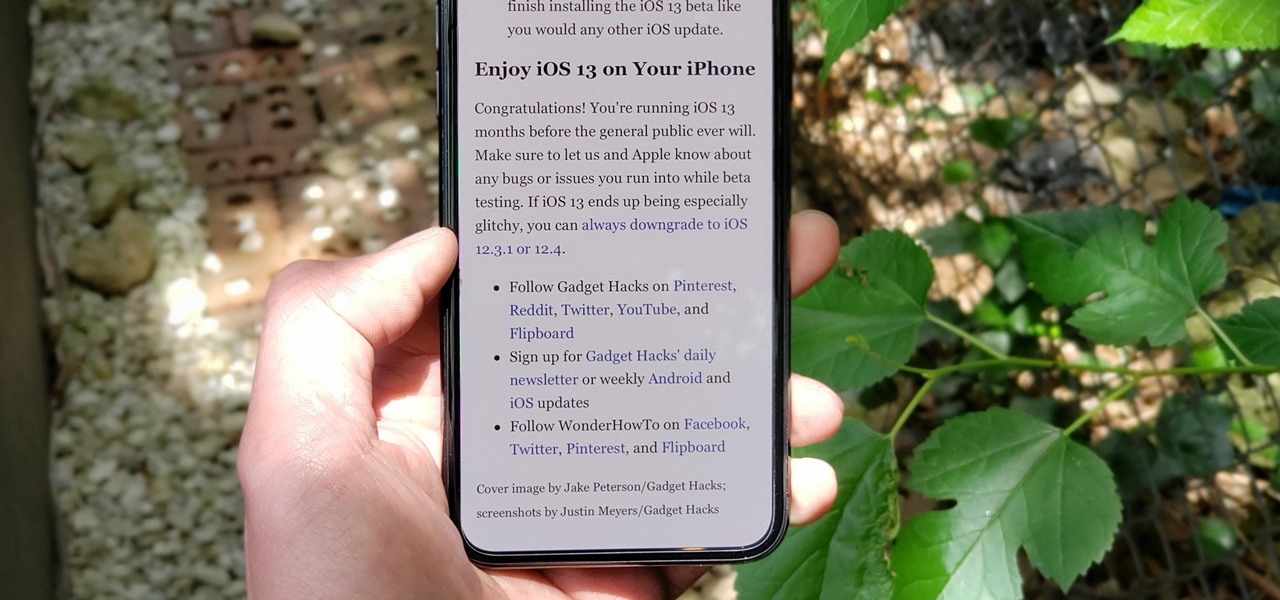
The Reader mode in Safari is a great way to view a webpage on your iPhone in a stripped-down manner, removing unnecessary images, videos, and advertisements for a streamlined experience free of distractions. Apple's iOS 13 improves upon Safari Reader when it comes to choosing which sites you want it to run automatically on, so everything is more accessible with more controls to work with.

An incredible amount of devices use Bluetooth or Bluetooth Low Energy to communicate. These devices rarely have their radios switched off, and in some cases, are deliberately used as trackers for lost items. While Bluetooth devices support MAC address randomization, many manufacturers do not use it, allowing us to use tools like Bettercap to scan for and track Bluetooth devices.

If you ask Siri to check the weather on your iPhone right now, you'll get information from the stock Weather app in iOS — even if you have and prefer other weather apps installed. But that doesn't have to be the case. Thanks to Siri Shortcuts in iOS 12 and later, you can set specific phrases that Siri will respond to for any compatible weather app you want.

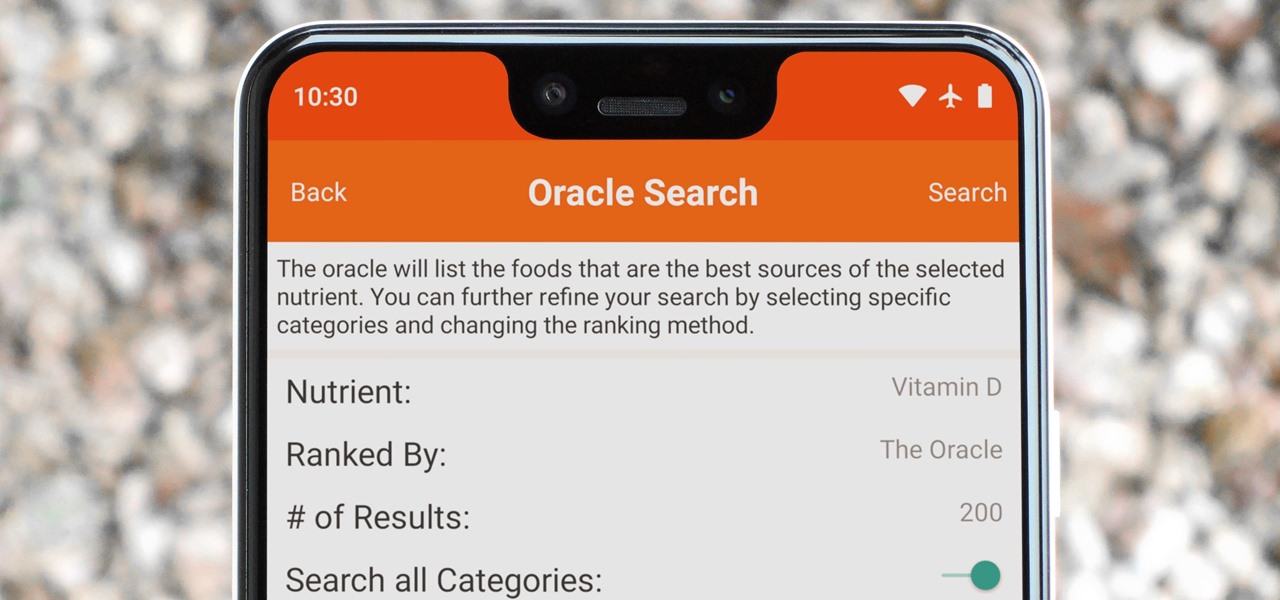
Micronutrients are essential to our health. Unfortunately, many of us aren't getting enough of each nutrient from our diets. It isn't that the food we're eating is bad, but rather we are not eating enough of the right food to get our recommended daily allowance. But with the help of a micronutrient tracker, we can change this.

Safari has a convenient "Find" feature to search for specific words and phrases in a webpage, and Apple Books has a similar feature for e-books and PDFs. But those do nothing for you when searching text in the real world. Hardcover and paperback books are still very much a thing, as well as paper-based documents, and finding what you need is as simple as pointing your iPhone's camera at the page.

You may have heard of a signal jammer before, which usually refers to a device that blasts out a strong enough radio signal to drown out the reception of nearby devices like cell phones. Purpose-built jammer hardware is outright illegal in many countries. Still, Wi-Fi is vulnerable to several different jamming attacks that can be done with Kali Linux and a wireless network adapter.

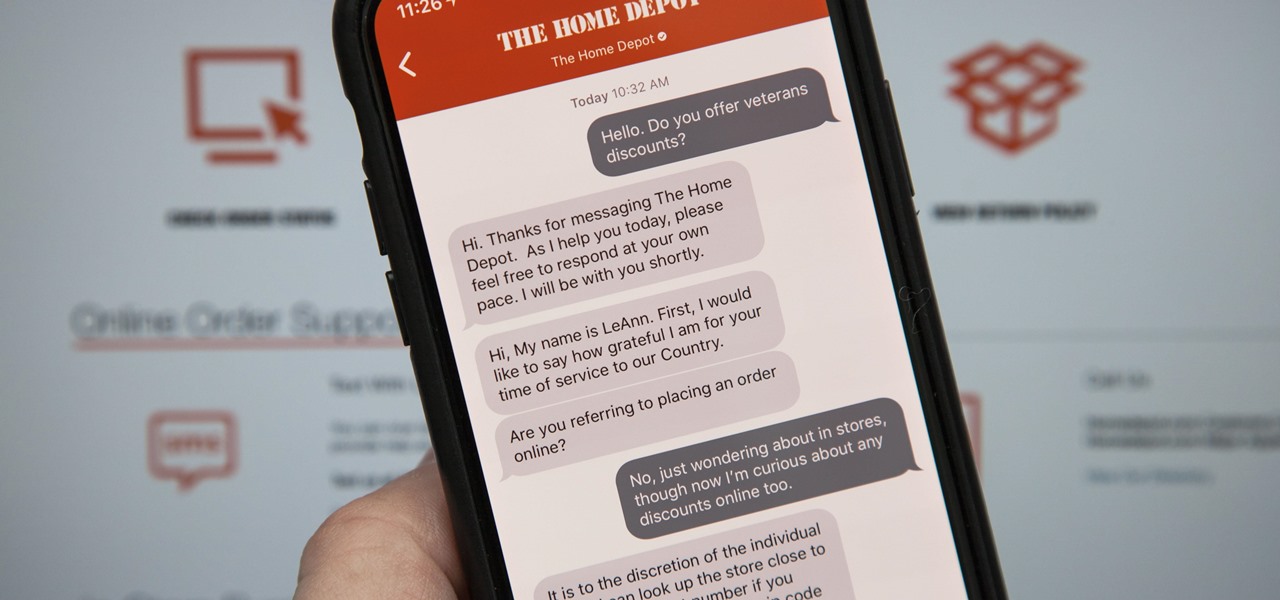
Apple first announced Business Chat, a new way for customers to communicate with companies, at WWDC 2017. While Business Chat did not arrive with the initial release of iOS 11, Apple pushed it out in iOS 11.3 so companies can offer customer service in a whole new way, and it works pretty much the same in iOS 12 and higher as it did back then.

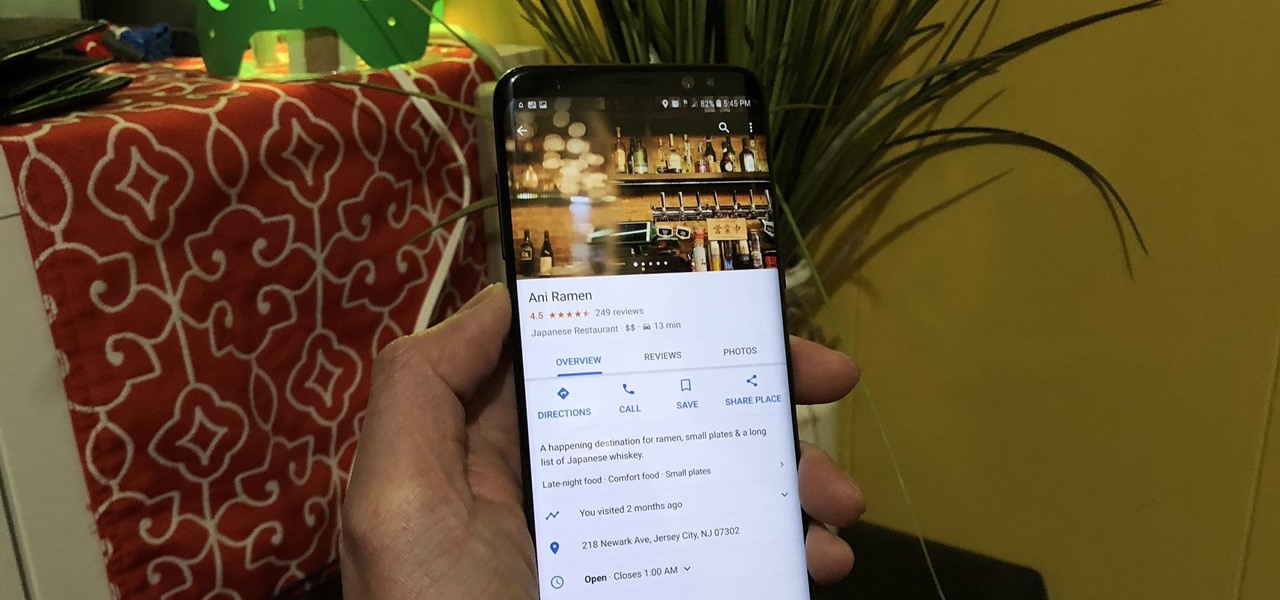
Going out to dinner on a Saturday night can be more trouble than it's worth when you find yourself waiting for hours on end just to be seated. Thankfully, Google Maps has some very useful data that can save you from a headache the next time you head out to your favorite restaurant.

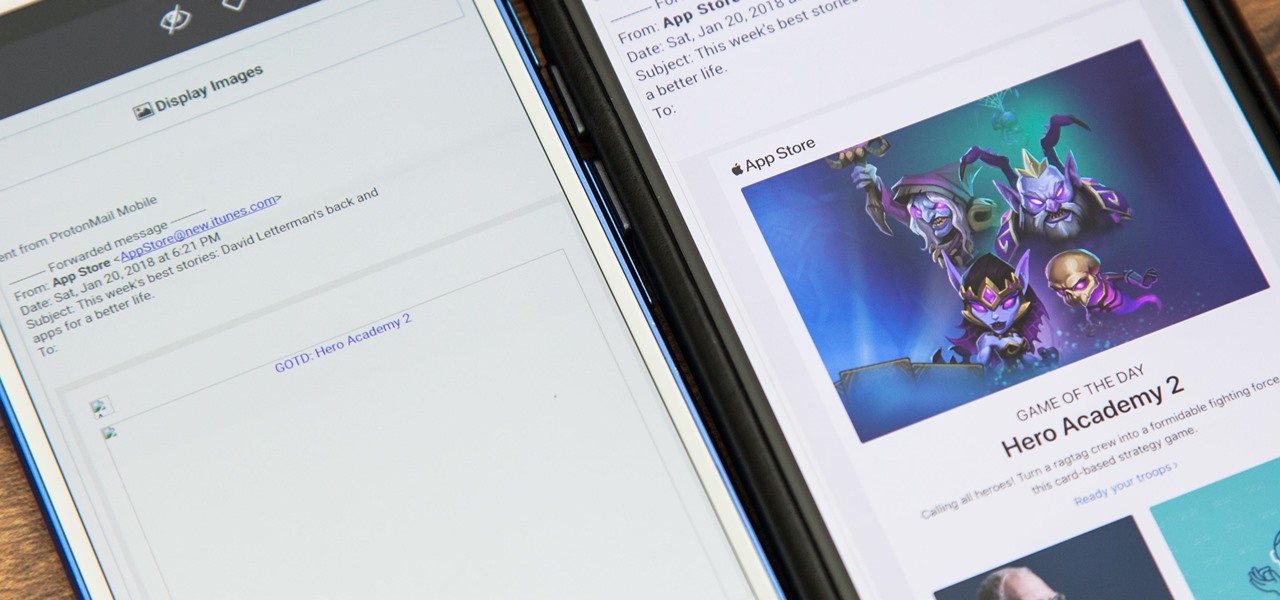
By default, images embedded using external links will not automatically load in any emails that you get with ProtonMail. This is a security mechanism that can prevent malicious code from being executed on your system, but it can also be fairly annoying to have to manually load images in email after email.

As we have seen previously with the likes of SethBling's Mar I/O videos and other examples, video games seem to be a great source for training AI neural networks. Augmented reality and machine learning are part of a collection of technologies that seem to be growing toward a point of maturity, and that will likely cause them to be intertwined for the foreseeable future. As developers, machine learning will definitely change the way we create software in the coming future. Instead of going lin...

The Operative Framework is a powerful Python-based open-source intelligence (OSINT) tool that can be used to find domains registered by the same email address, as well as many other investigative functions. This reconnaissance tool provides insight about your target through examining relationships in the domains they own.

Most messaging apps have it, so it's about time WhatsApp did too. The WhatsApp beta now has a search bar for emojis.

A young child becomes very thirsty very often and seems tired all the time. A visit to the pediatrician determines she has type 1 diabetes. The onset of type 1 diabetes may seem sudden, and it can be, but the disease may actually have been triggered by common childhood viruses years earlier.

The best way to spread Christmas cheer is singing loud for all to hear, right? Wrong.

It took nearly six months, but Google has finally made its wildly popular iOS keyboard available to Android users. Technically, it's just an update to the existing Google Keyboard app for Android, but it renames the app to "Gboard" and includes all of the features from iOS, so Android users can stop feeling like Google's neglected stepchildren.

Traditional root ad-blockers like AdAway and AdBlock Plus have no effect on YouTube anymore. Until now, if you wanted to get rid of the commercials that play before your favorite videos, there have only been two ways—either by paying for a YouTube Red subscription, or by using an Xposed module to modify the YouTube app itself and force it into not showing ads.

If you've ever made graphs and charts, you know it can be a struggle to represent a large amount of data. It's something that just doesn't work very well on a flat surface. In virtual and mixed reality, however, the data can exist all around you.

In this tutorial I am going to show you how to create an undetectable Meterpreter Trojan using a Domain name. I have taken a few guides/tutorials and built it into one. The first part is creating the DNS Payload. The second part is creating the Executable file. Part 3 is using both in Shellter to create your undetectable Trojan. Part 4 is setting up your listener using Armitage.

A motion-based lock screen app called GestureLock was among the winner's at 2106's Android Experiments I/O Challenge, and it lets you set a specific motion (gesture) that you use to gain access to your locked phone.

This technique shows you how I have made these gorgeous little paper flowers that match project Nos161

In this article I will show you how to obtain victim's credentials without cracking any hashes. There are a couple of ways to perform this task (for example dumping the SAM file and cracking the NTLM hashes), but here I will explain how to do it using PowerShell and a bit of social engineering. We are going to create a fake login popup.

Depending on how many Watch-compatible apps you have, the Home screen on your Apple Watch is either insanely clean or absurdly messy. When I first synced my Watch with my iPhone, I was attacked with a huge honeycomb of apps, strewn across my Home screen in no particular order.

There's no such thing as a perfect Android keyboard. Some, like Swype, have gesture typing down to a science, but lack in predictive technology. SwiftKey, on the other hand, boasts awesome next-word prediction, but less than stellar gesture typing. Many others are optimized for multiple languages, space saving, or emojis, but none are without their flaws.

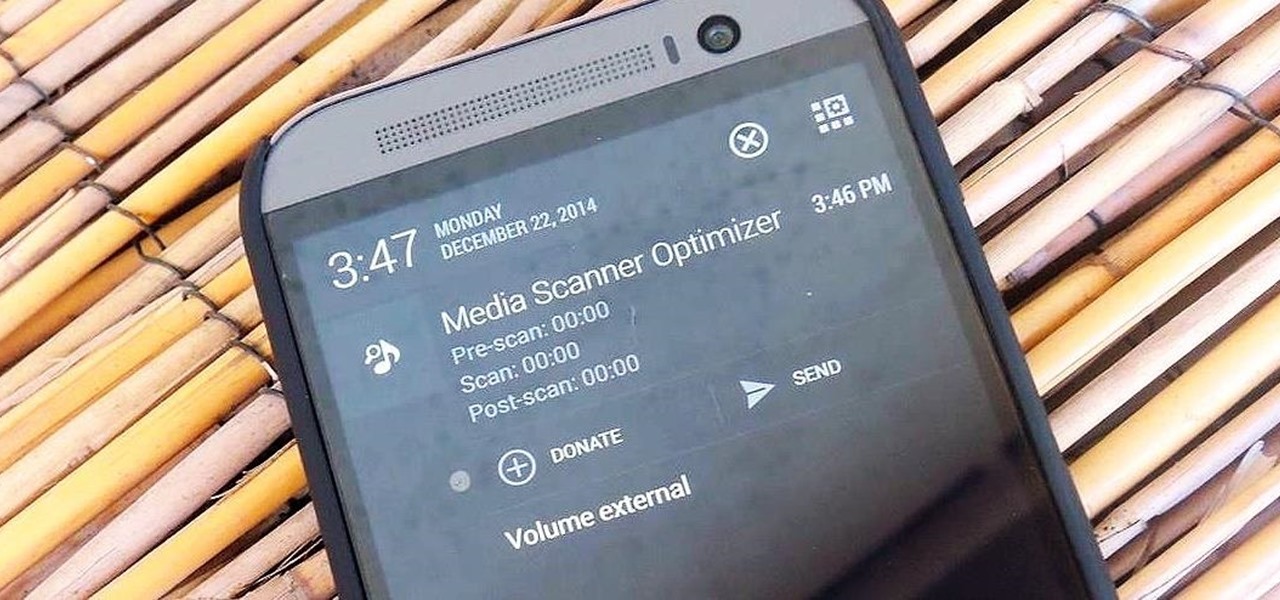
Battery life is extremely unpredictable on an Android. Finding the right ROM and kernel combo can make or break having the kind of battery that will last you all day long. Even if you do find the perfect pair, you then have to worry about apps, widgets, and other processes constantly waking your phone and draining your juice. While your media scanner isn't the biggest battery hog out there, it can definitely take a chunk out of it.

Welcome back, my hacker novitiates! As you know by now, the Metasploit Framework is one of my favorite hacking tools. It is capable of embedding code into a remote system and controlling it, scanning systems for recon, and fuzzing systems to find buffer overflows. Plus, all of this can be integrated into Rapid7's excellent vulnerability scanner Nexpose.

Keeping a close eye on your device storage can be a 24/7 job, especially if you're space is filling up and your device doesn't have SD card support. No matter how close of an eye you keep on it, there are always going to be apps updating databases, adding to their cache, and deleting old files.

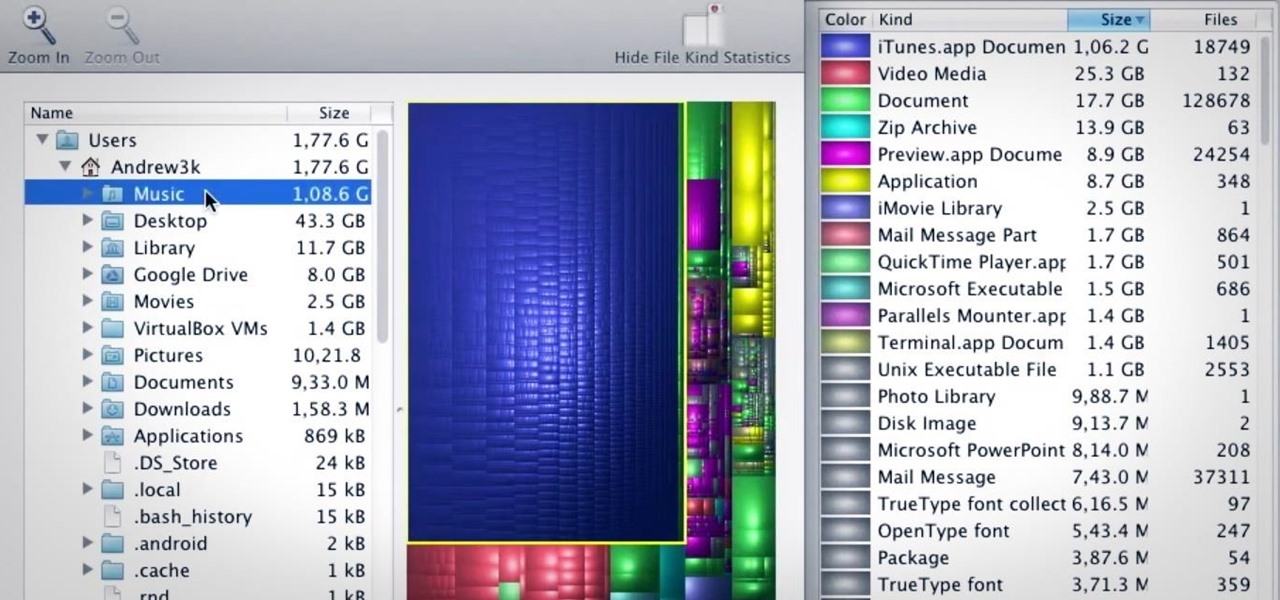
I love my MacBook Air, but the fact that it runs on only 128 GB of flash storage causes me to move most of my files to the cloud. I don't mind having to be connected to the internet in order to access my files, but it's definitely a hassle trying to figure out which files I should move in order to save the most space. Usually, I don't even bother even trying until I see the dreaded "Your startup disk if almost full" warning. Currently, the only real way to find your biggest files in Mac OS X ...

Third-party keyboards have become a game changer for iPhone owners since their integration in iOS 8. And while the major players from the Android realm—Fleksy, SwiftKey, Swype—already have their keyboards on the iOS App Store, their products are relatively standard fare.

Snapchat recently introduced geofilters to its ephermal messaging platform—cute stickers that you can add on your Snapchat, which showcase your location.

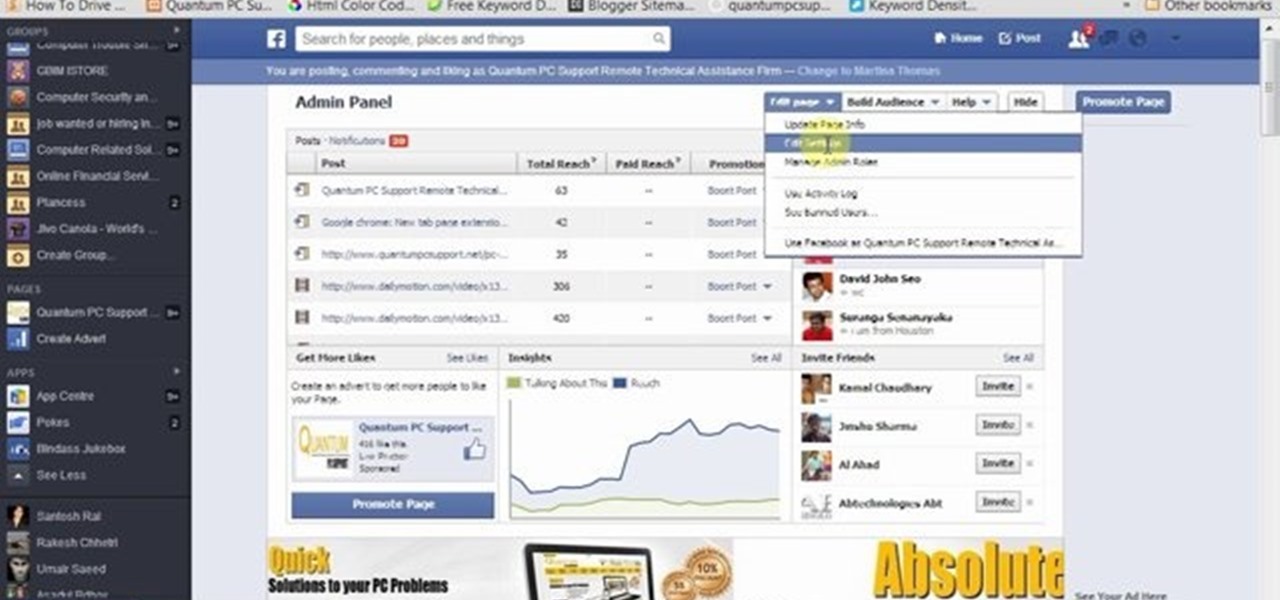
This video will show how to target your facebook post for a specific audience. With this tutorial video you could target a set of audience who has interest about the post.