As an adult you will come a cross a point in time when you need to make the right impression by writing a formal letter. Follow the format and you will be able to be most effective at conveying the information in your letter.
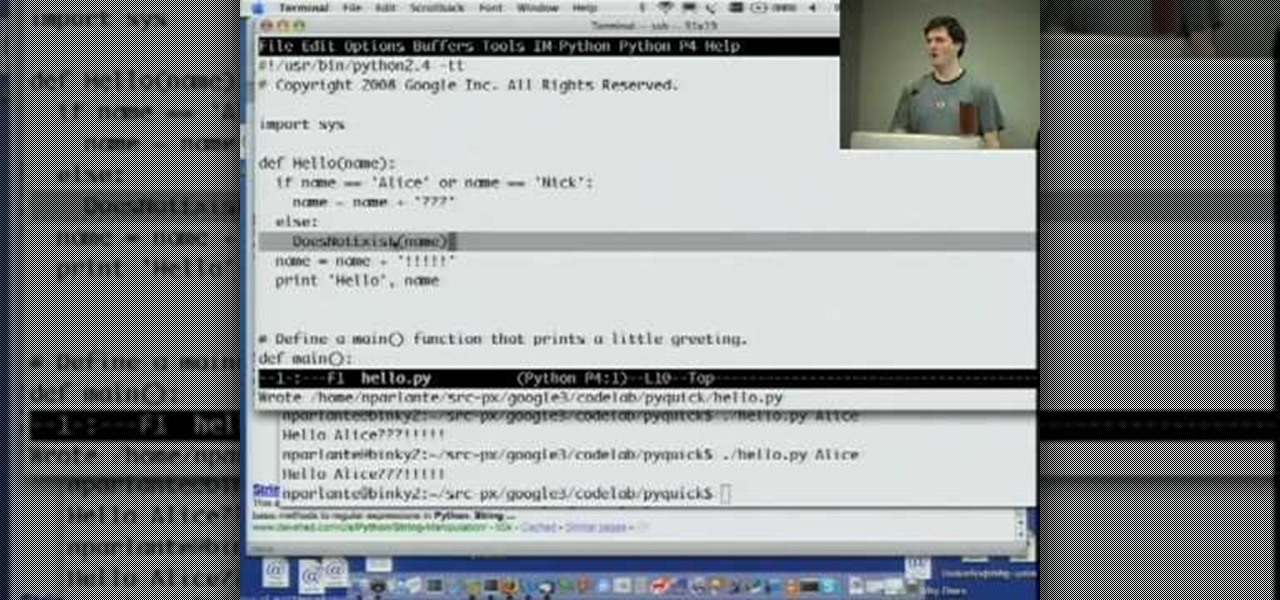
Welcome to Google's Python Class – a seven-segment, two-part free virtual class for people with a little bit of programming experience who want to learn Python. The class includes written materials, lecture videos, and lots of code exercises to practice Python coding. The first exercises work on basic Python concepts like strings and lists, building up to the later exercises which are full programs dealing with text files, processes, and http connections. The class is geared for people who ha...
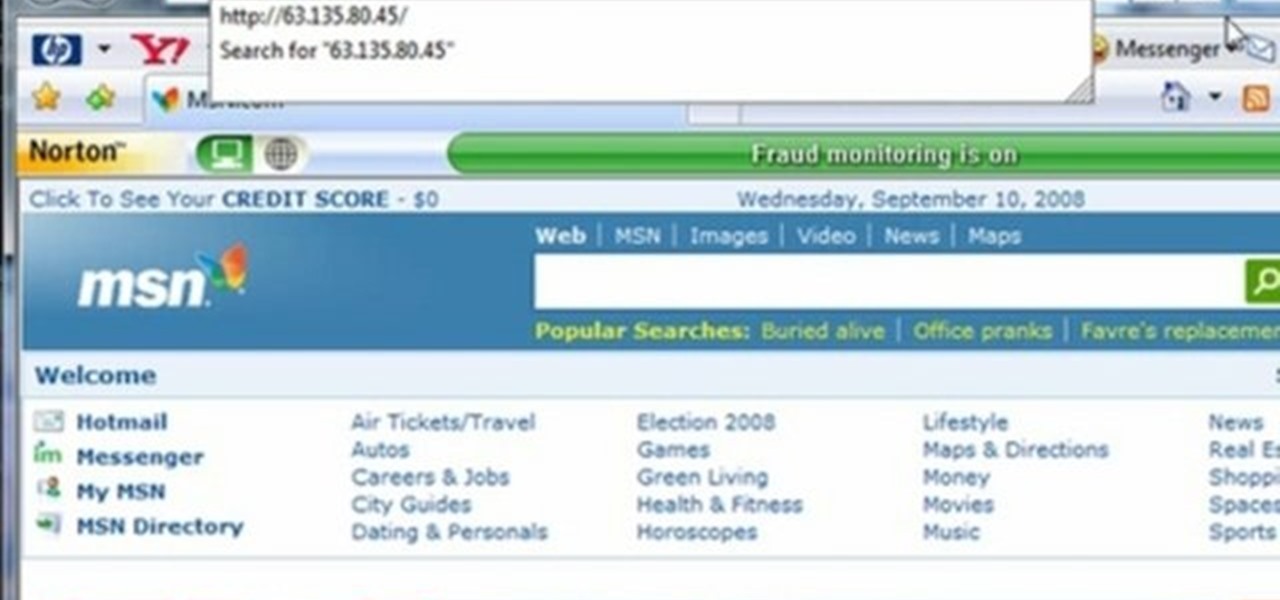
This video tutorial gives you a way to access websites that you can not normally access because of a web block or filter. What you need to do is click on the ‘Start’ button and then click on ‘Run’. In the small window, type in ‘cmd.exe’; this then opens a black window. Then type in ‘ping’ and the website; this gives you an address that you type in directly to your web browser, granting you access to a normally blocked website. This comes in very handy when you are in such locations like schoo...
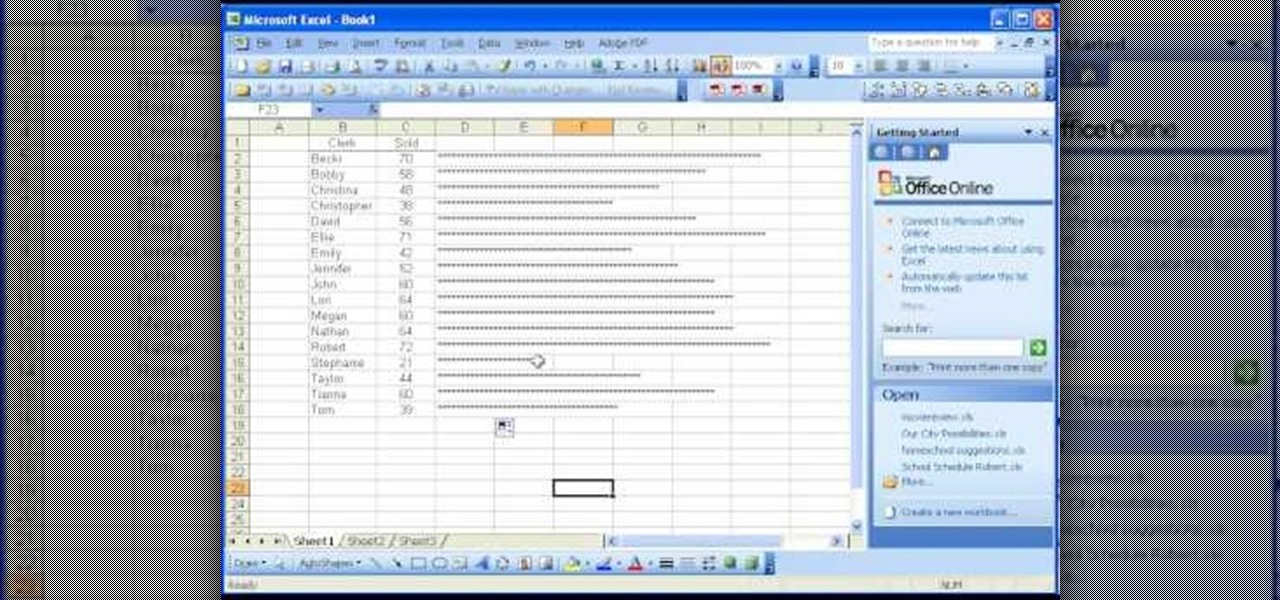
There are many functions in Microsoft Excel. One function that people rarely use is the Repeat function or REPT. In this video, an example used is a chart of people and their sales of a certain item. Just looking at the numbers, it is hard to compare the different sales easily, but a more visual approach may work better. Next to one of the cells, type in "=REPT(" which is the repeat function. A popup should say "=REPT(text, numbertimes)". For "text", type in *** or anything, really. For "numb...

This daring docu-drama explores the esoteric underground of hard-cider brewing. This fast paced thriller is sure to captivate the mind, and leave you on the edge of your seat. OK, it's just a video shot with a 3mp Cannon digital camera on video mode and edited with some lousy free software. There are two different methods used to make this hard cider. 5 gallons of fresh cider with a starting specific gravity of 12 were pitched with White Labs liquid English Cider Yeast. This should yield arou...

Tim Carter discusses the different types of wood and how they are recognized and how their attributes are utilized. Informative video will help to make sure you use the proper wood for your build.

There are two main types of shafts for horse dawn carriages, U-Shaped fixed shafts and independent shafts. watch this video to learn how they work.

Managing Panoramas (henceforth known as panos) and HDR photos in Lightroom is an important step in making your life a lot easier if you like that type of photography. What happens after shooting a lot of either type of photography is that your library becomes really cluttered. As if the clutter wasn’t bad enough, it just becomes flat-out difficult to start processing these types of photos. So instead of ditching Lightroom when you shoot at pano or HDR set, check out this week’s video and give...

This is a tutorial on how to edit type in a layered file and a flattened file in Photoshop.

From pirates to playboys to Village People, there are as many types of mustaches as there are types of men—but all of them need a good trim every once in a while.

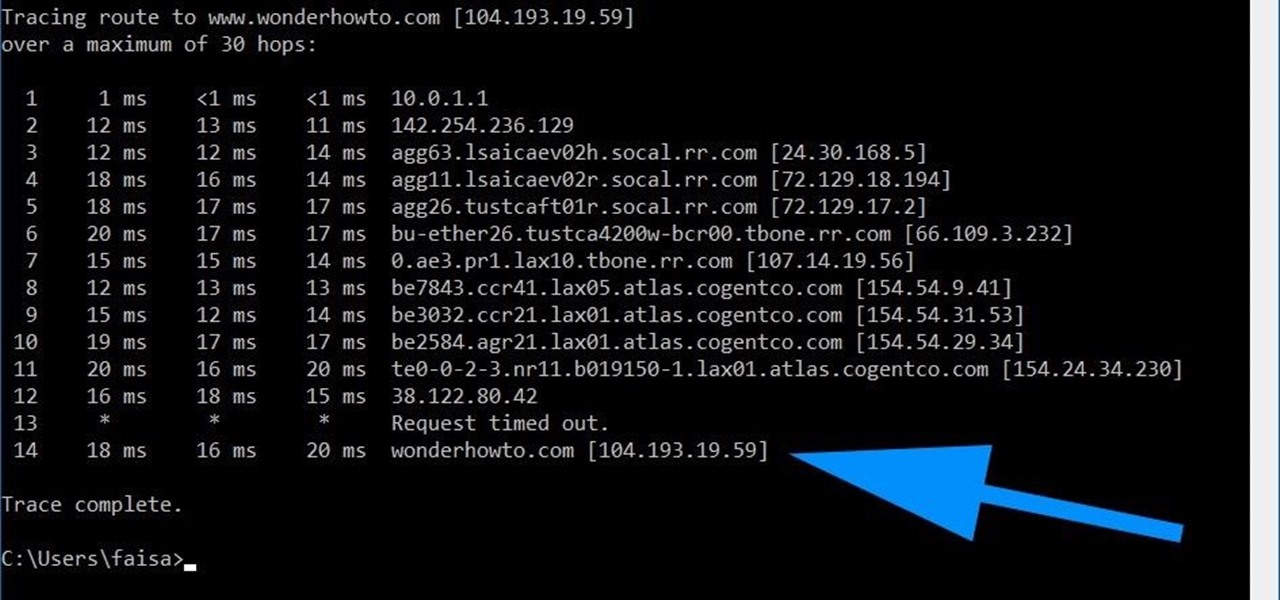
Using a simple trace trick, you can easily look up the IP address and its location for any website. This method uses a command line command to first find the IP address of a given website, and then uses a free online tool to get that IP's location.

TWRP is the premiere custom recovery for Android because of how many devices it supports and how simple it is to use. But installing it in the first place hasn't always been the easiest thing to do — until now. With the help of a Magisk module, you can finally use one Android device to flash TWRP on another.

The biggest hurdle to rooting is that it usually requires a computer. Things get complicated when you're trying to use a desktop operating system to exploit a mobile OS, and the connection isn't always reliable. But with the help of Magisk, you can now use one Android phone to root another.

There's nothing quite like getting lost in the TikTok void. While you'll likely never run into the same video twice, the same can't be said for popular sounds and fads. Some trends get so viral, it feels like you hear the same song or track every other TikTok. Just know this: you don't have to put up with any trend you're sick of.

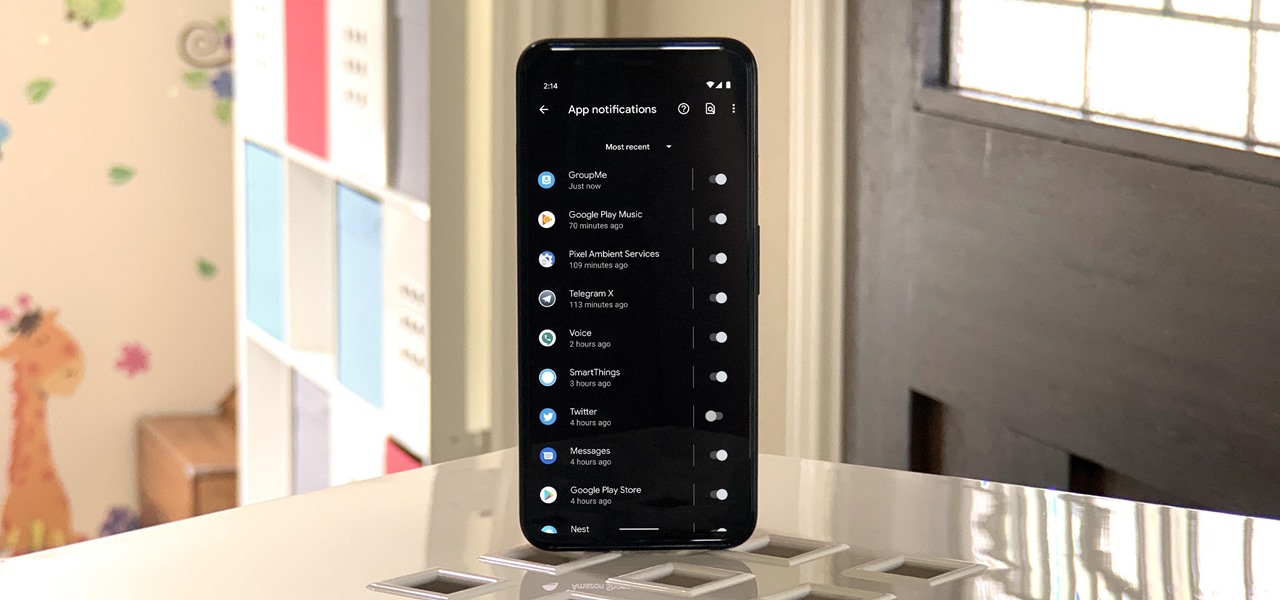
Sometimes you might find that a certain app keeps sending you notifications. What are you to do? There are plenty of useful apps that might send one too many push notifications, but that doesn't mean you should dump them. Luckily, Android gives you complete control over how each installed app handles notifications.

When you're going somewhere for the first time, it's nice to know what the destination will look like. Street View in Google Maps is the perfect tool for that, though it's always been a little awkward to access. But now, Google added a new overlay that will put Street View content literally one tap away at all times.

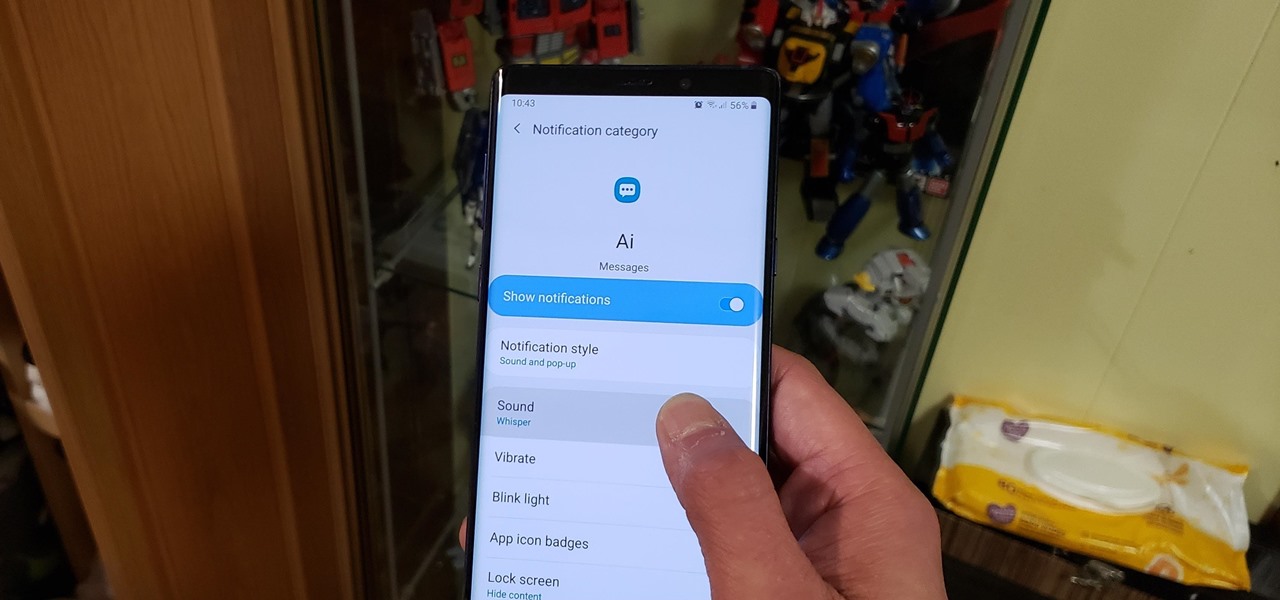
Some messages take precedence over others, so having the same notification tone for all your threads isn't always the best solution. Fortunately, Samsung Messages has a simple option you can tweak to set custom sounds for specific chats to help you stay on top of priority conversations and reply much faster.

Having an efficient workflow is an integral part of any craft, but it's especially important when it comes to probing apps for vulnerabilities. While Metasploit is considered the de facto standard when it comes to exploitation, it also contains modules for other activities, such as scanning. Case in point, WMAP, a web application scanner available for use from within the Metasploit framework.

With the raw, visceral feeling of zooming around on the open road, it's easy to get carried away when you're out for a ride on your chopper, super bike, or scooter. This increases your chances of getting lost, plus routes can differ slightly for motorcyclists and cagers, unbeknownst to most drivers. Luckily, Waze has rolled out a feature that caters specifically to bikers.

PowerShell Empire is a post-exploitation framework for computers and servers running Microsoft Windows, Windows Server operating systems, or both. In these tutorials, we will be exploring everything from how to install Powershell Empire to how to snoop around a target's computer without the antivirus software knowing about it. If we are lucky, we might even be able to obtain domain administrator credentials and own the whole network.

Devastating and deadly, land mines are a persistent threat in many areas of the world. Funding to clear regions of land mines has been decreasing, but new research may offer a less dangerous method of locating hidden, underground explosives by using glowing bacteria.

The rumors have been confirmed by Samsung themselves: Samsung has developed a virtual assistant of their own, named Bixby.

Anyone who's ever flashed factory images to manually update an Android phone knows how tedious the process can be. Unlocking the bootloader and flashing Android firmware requires the use of ADB and Fastboot—but, like getting a whole pizza pie when all you wanted was a slice, users in the past had to download the entire Android Studio development package or SDK in order to get the two utilities.

When WhatsApp first came out in 2010, it quickly gained notoriety as a great way to meet new people all over the world thanks to group chats, which allow multiple admins for each group that can all add participants from their own contacts lists.

If you're an Android fan, you're probably familiar with Qualcomm's Quick Charge technology or, at the very least, what it can do. Quick Charge 3.0, the third generation of Qualcomm's fast-charging technology, is built into most Snapdragon SoCs and it's what lets you charge your phone's battery up to 70% power in just 30 minutes. What's not to like?

Data visualization has many applications in virtual and mixed reality, since a third dimension literally adds important depth to the represented information. A new app called HoloFlight is a good example of this, combining flight-tracking data and the Microsoft HoloLens to surround you with a look at every plane in the sky.

Microsoft recently announced that they're producing HoloLens units fast enough to keep up with demand, which means you can acquire up to five dev kits right now—if you've got the $3,000 fee for each one.

Mozilla helped get the ball rolling with WebVR, but support for the technology has been notably absent in Google Chrome until recently. Now, the latest Chromium developer build offers limited support.

Swipe keyboards such as GBoard, SwiftKey, TouchPal, and Swype are handy for quick one-thumbed typing on an iPhone, but Microsoft upped the game with its experimental Word Flow Keyboard. In short, the keyboard fans out to occupy the natural range of your thumb, where you can type or rely on predictive swiping.

When you want to leave someone a quick message, you often write it down on a sticky note and paste it to the relevant location. Alternatively, you call to leave a voicemail. Holo Voice Memo lets you do both at the same time by leaving an audio clip on a physical object in the room so anyone with a HoloLens and the app can play it back.

Your iPhone might have a great camera, but it can be irritating to get things like exposure and focus right when your fingers are all over the 'viewfinder.' The Pictar aims to change that by making your iPhone as much like a DLSR as it can, keeping your fingers from obstructing your next great photo.

Welcome back, everyone! In this lesson, I'm going to go over the use of the echo function and variables, as well as basic syntax.

Welcome back, my novice hackers! In this series, we have been exploring how a forensic investigator can find evidence of illegal or illicit activity. Among other things, we have examined the registry and prefetch files for artifacts and have done some rudimentary forensic analysis. For those of you who are seeking career as a forensic investigator or security engineer, this can be invaluable training. For hackers, it might be life-saving.

When performing something such as a mass mailer attack on a company, sending executables usually isn't the best option. That's why, in this tutorial, I'll be teaching you how to code a VBA script macro into a Word document in order to compromise a system. Combined with a little social engineering, this can be a very effective technique.

Welcome back Java programmers! In this tutorial we'll being going over Variables/DataTypes and Type-casting

infosecinstitute posted a handy article about what to expect in the new year for cyber security, along with highlighting major game changers from 2015; 2016 Cyber Security Predictions: From Extortion to Nation-state Attacks - InfoSec Resources.

In previous tutorials we have encountered these things called pointers and addresses but we still don't know what they really are. Let's learn a bit more to clear things up.

I've been a fan of potatoes ever since I can remember... but mainly because they weren't a big part of my daily diet (which usually consisted of rice). And because my experience with potatoes was so limited, I only knew of two varieties growing up: big, brown Russets and sinewy sweet potatoes. As for cooking with potatoes—well, I'm embarrassed to admit that the only time I cooked potatoes when I was a kid was with the instant kind.

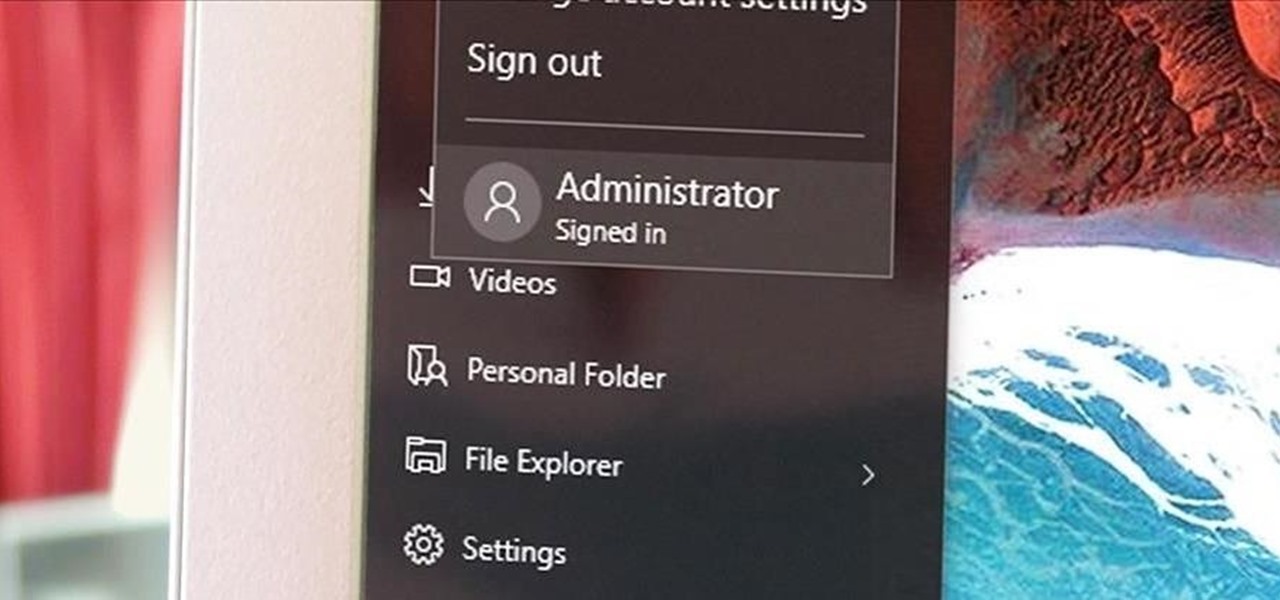
Windows has always had an "Administrator" account that allowed you to install programs and manage system files with elevated privileges. The difference between this account and a regular user account with administrator access was that you never got bothered by annoying User Account Control popups when you were logged in as Administrator.

This is a tutorial and informational video for people who are interested in art and wondering what type of real-life jobs they can do in the art world.