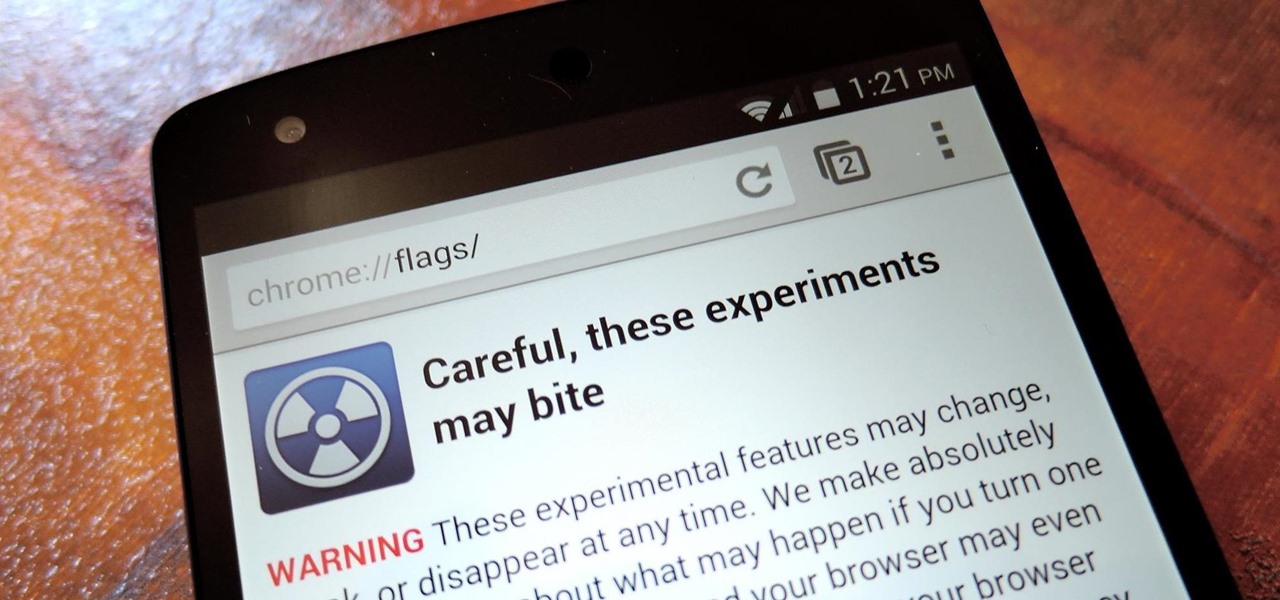
Android's auto brightness feature was recently updated, and as of version 5.0, a new "Adaptive brightness" feature was added. This allows users to set a preferred overall brightness level, but still have the ambient light sensor adjust the backlight accordingly.

Resources for finding new music are at our disposal in all corners of the internet; the only problem is deciding which one is the best for you. Spotify, Pandora, and Rdio all have options to discover new music on your smartphone, but they tend to expose mostly established artists, making the process of finding lesser-known but good music a game of trial and error.

What Is IPython? IPython is a richly featured replacement for the standard python interpreter. It offers a wider range of functionality, that the standard
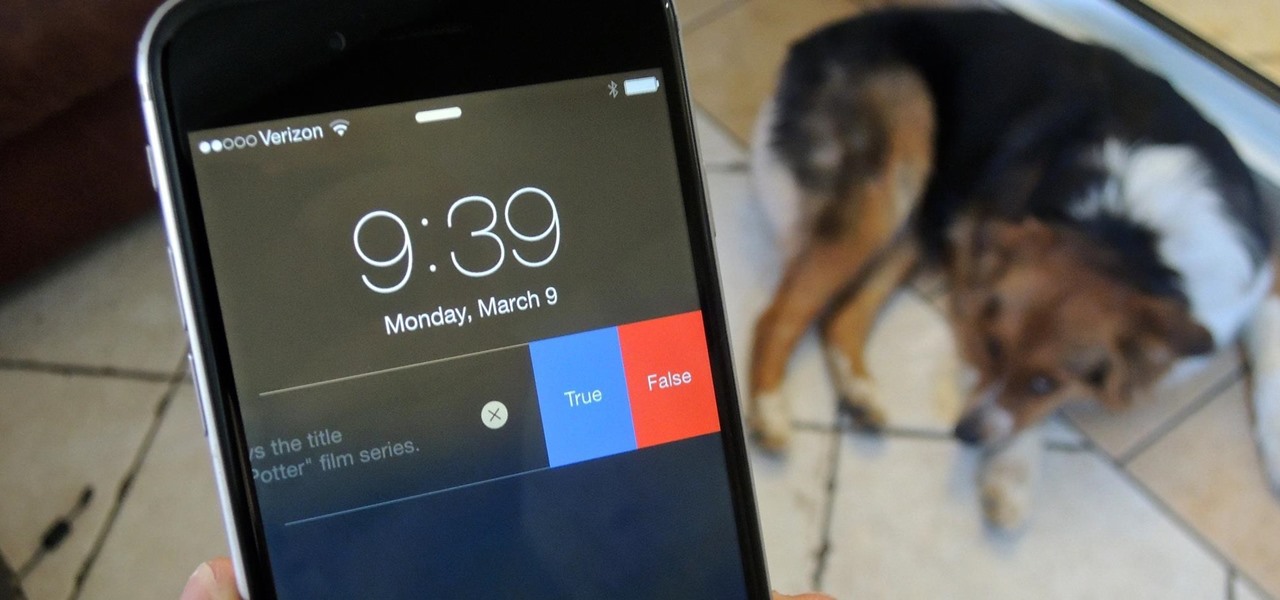
The bulk of my mobile gaming is done in instances of boredom, like sitting in a waiting room or watching bad TV. So when I heard about a new trivia game that pits every user against each other just once a day, I was immediately intrigued; it's a new spin on a very popular platform.
With the advent of text messaging, our communication habits have changed drastically. Social niceties are still there, but we budget our words a little more since they have to be typed out rather than spoken. After all, SMS stands for "Short Message Service," so this is the nature of the beast.

Hello Elite Hackers! Welcome to my 3rd Post, which explains how to hack any account like G-mail, Facebook, etc.

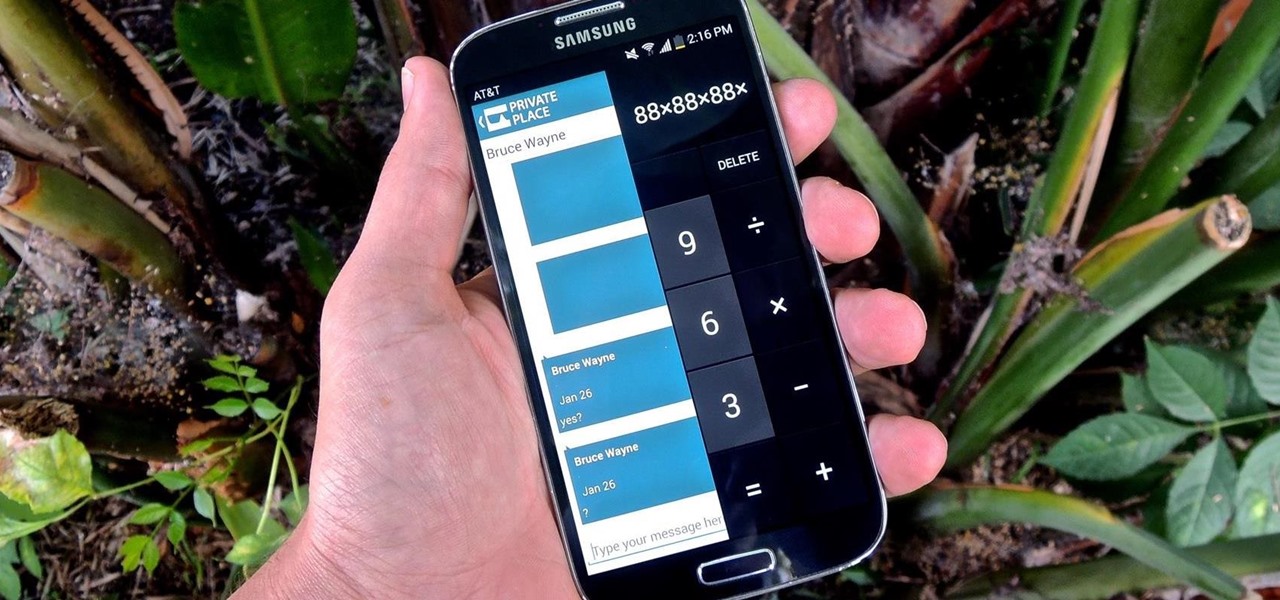
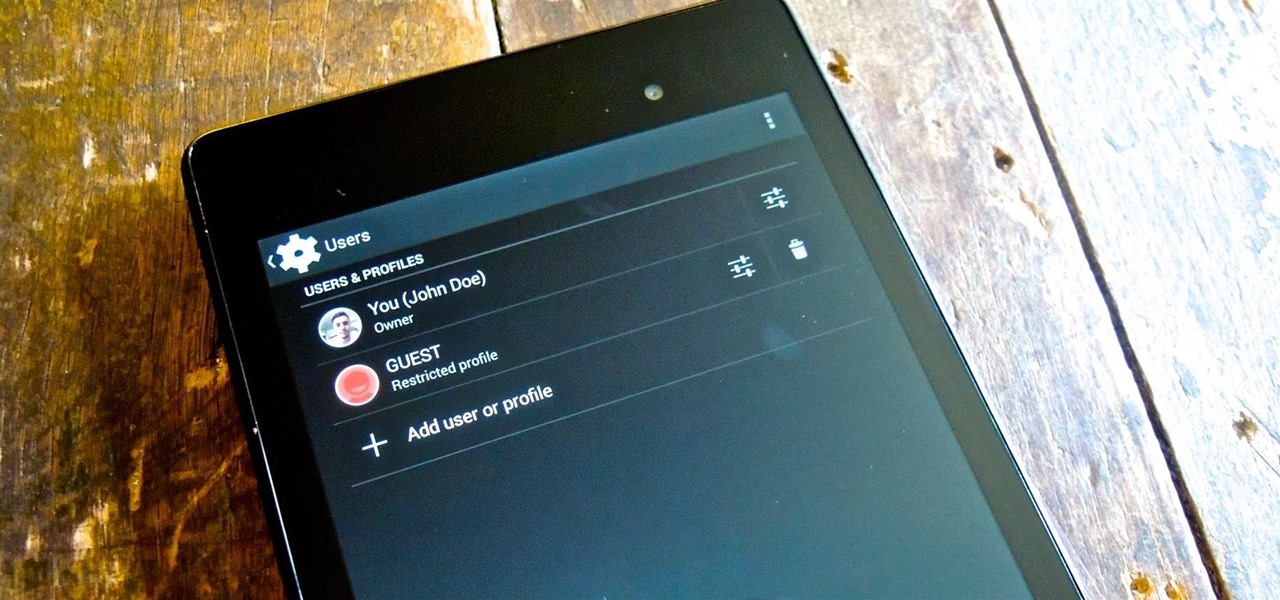
Whether you're a secret spy or just a regular person with a few secrets, you may want to keep certain information on your smartphone private, and it's totally possible on Android to do so.

My college days are long behind me, and while I don't necessary miss them, I am jealous of all the countless resources available to students these days. Apps like PhotoMath are something I wish I had access to in my student days, making assignments less strenuous and easier to complete.

The Nexus 6 is one of the few devices on the market that sports a 1440p "QHD" display. This means that the amount of pixels displayed is higher than almost any other smartphone, which sounds great on the surface, but is not without its drawbacks.

When you search for a specific location or business with the Google app, a Knowledge Graph card is usually the top result. This card displays a handy mini-map and offers a quick link for directions to the location of your query, but it has one irksome flaw—these links can only be opened by the Google Maps app.

Every so often, we come across an app that makes us wonder "Why didn't someone think of this before?" This is definitely the case with developer Dor Sakal's latest offering, FloatNote.

Placing widgets on your device's home screen is a quick way to gain instant access to shortcuts or to specific aspects of an app, like music controls or weather forecasts. As more and more developers create various types of app drawers and shortcuts, many overlook widgets and what they have to offer.

Google continues to be the most commonly-used search engine for a reason. While continuing to stay ahead of the pack with advanced semantic search functions, Google even introduced Knowledge Graph results that offer key information without ever having to click a search result.

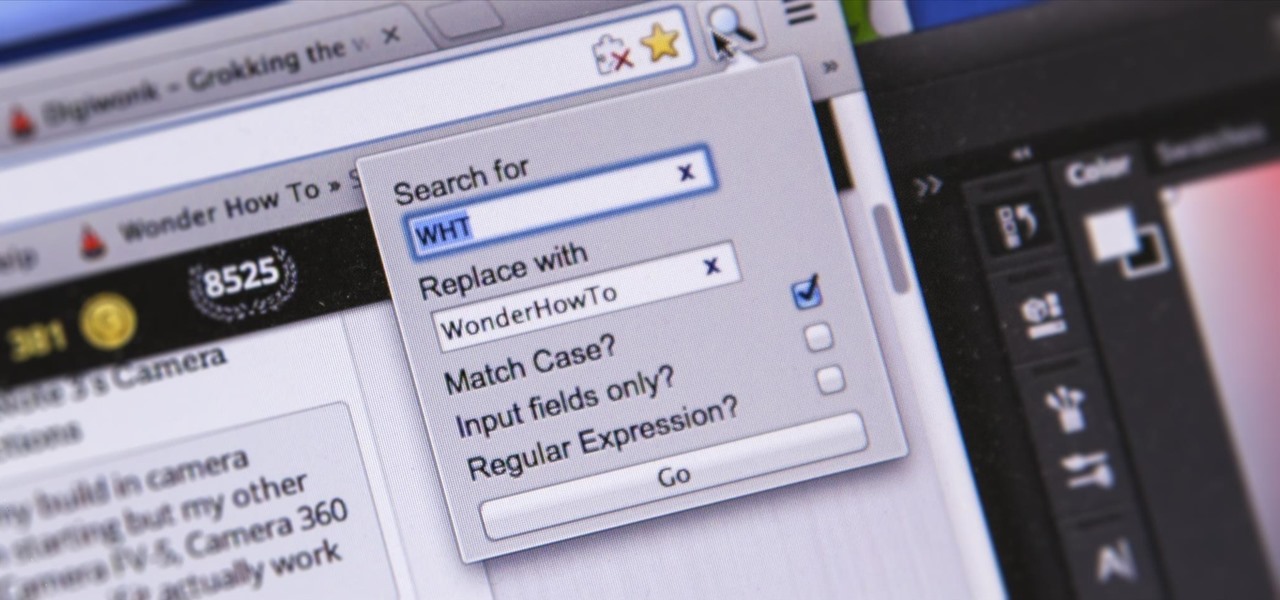
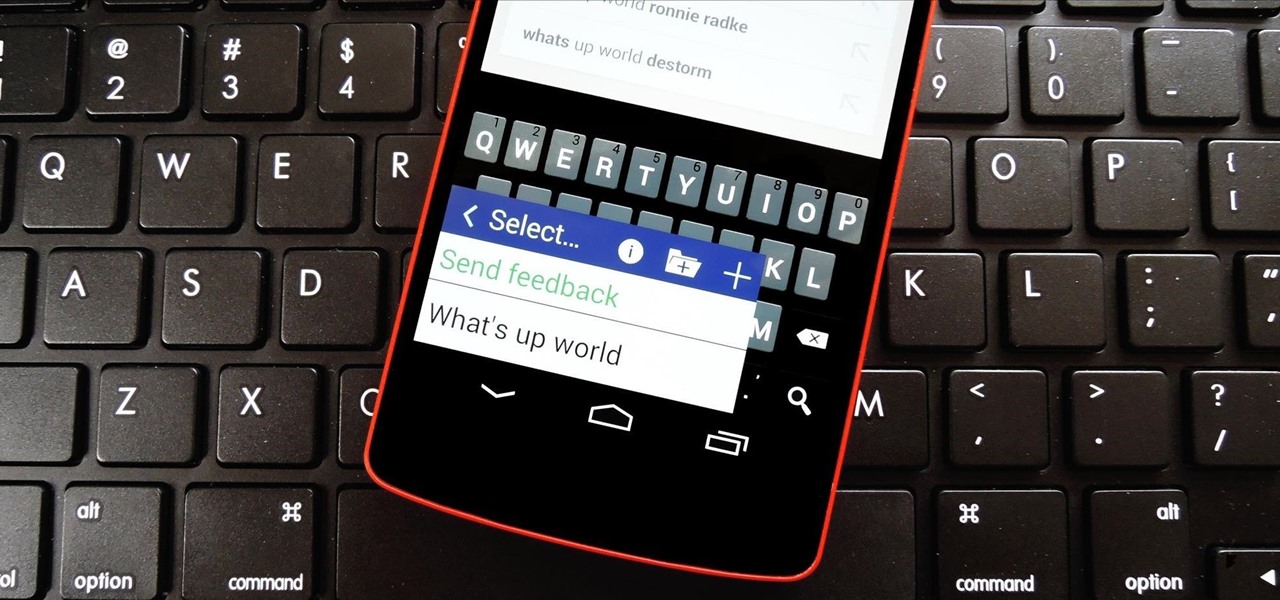
I'm sure you've been there—halfway through typing something out, you realize that one word you've been using more than any other has been misspelled. Perhaps it's a single word, acronym, or line of code that you find yourself typing quite often at work, but this one requires complicated hand gymnastics that you'd simply rather not perform over and over again.

With the release of the ARChon Runtime, many Android apps can now be run within the Chrome web browser. Minor changes must be made to existing Android APK files before they can be installed on Chrome, so the process isn't exactly as easy as pasting an Android app into a folder on your computer.

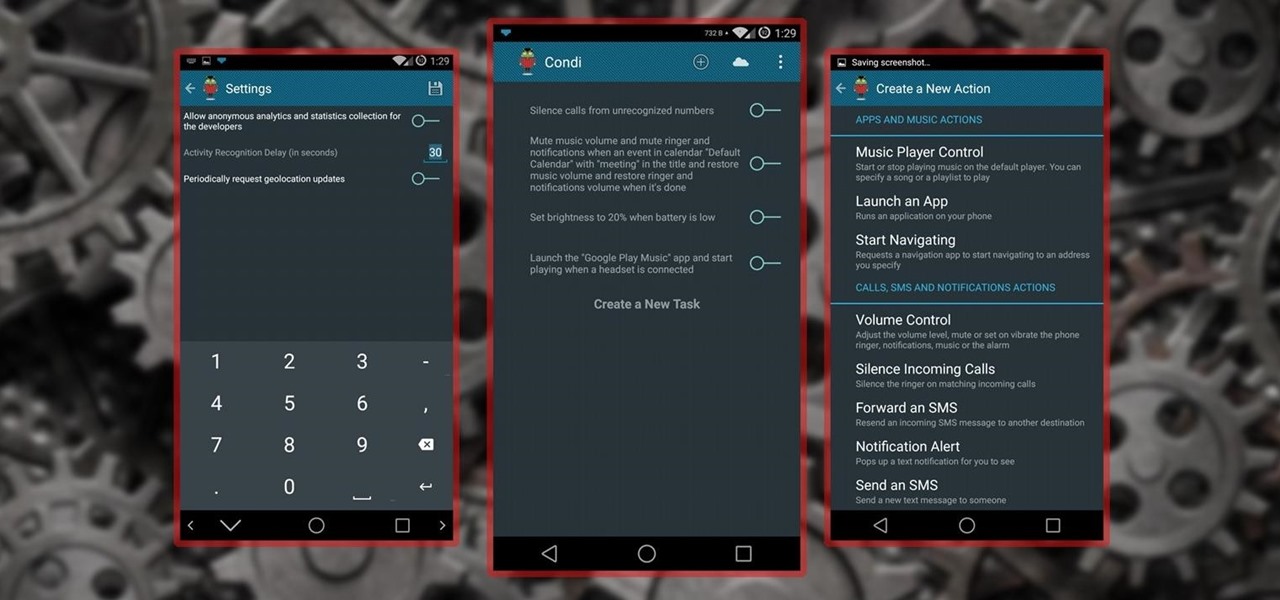
No matter whether you're a seasoned Android veteran, or just starting to get into the scene, you have probably heard of Tasker, the king amongst all the various automation tools available.

In 2012, VideoLan published a beta release of their wildly popular desktop media player, VLC, for the Android platform. However, because the non-profit development team did not have access to popular North American Android devices, they opted to exclude the USA and Canada from their initial release. That is, until now.

This video will show you how to change the default downloading folder for your downloads. When you download a video or file it is saved in the default downloading folder in our PC. You have to go to that folder then copy or move the folder in a specific location. But you can get rid of such extra work by setting your downloading folder in a different location you want. The next time you download something that will be saved in your specified location. Watch the video.

Summer is here and flocks of people will make their way to beaches, lakes, and rivers across the country. But before heading out to places like these, it's always a good idea to check the local weather forecast first.

Welcome back, my rookie hackers! Most often, the professional hacker is seeking protected information from the target system or network. This might be credit card numbers, personally identifiable information, or intellectual property (formulas, plans, blueprints, designs, etc.). Most of my Null Byte guides have been focused on getting into the system, but this only begs the question—"what do I do when I get there?"

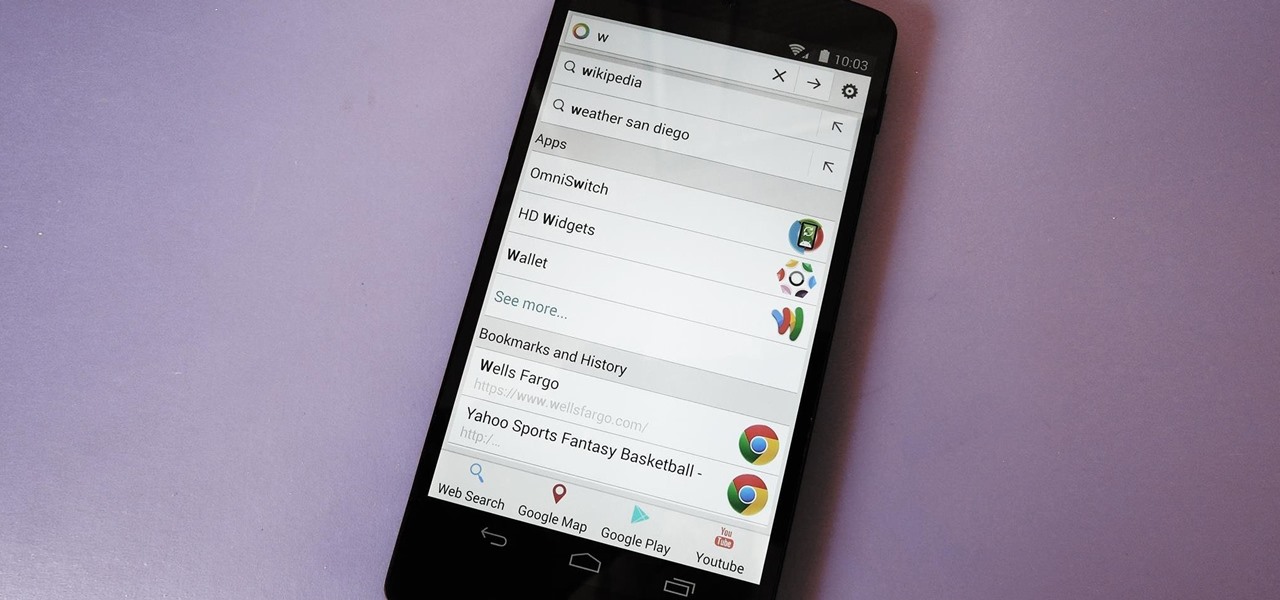
Prior to the release of Android 4.0, most devices had a dedicated search button. This functionality allowed you to search Google from your home screen and app-specific content from within any app. Eventually, though, this dedicated search button was ditched in favor of an icon in the action bar of apps, and a search bar on the home screen.

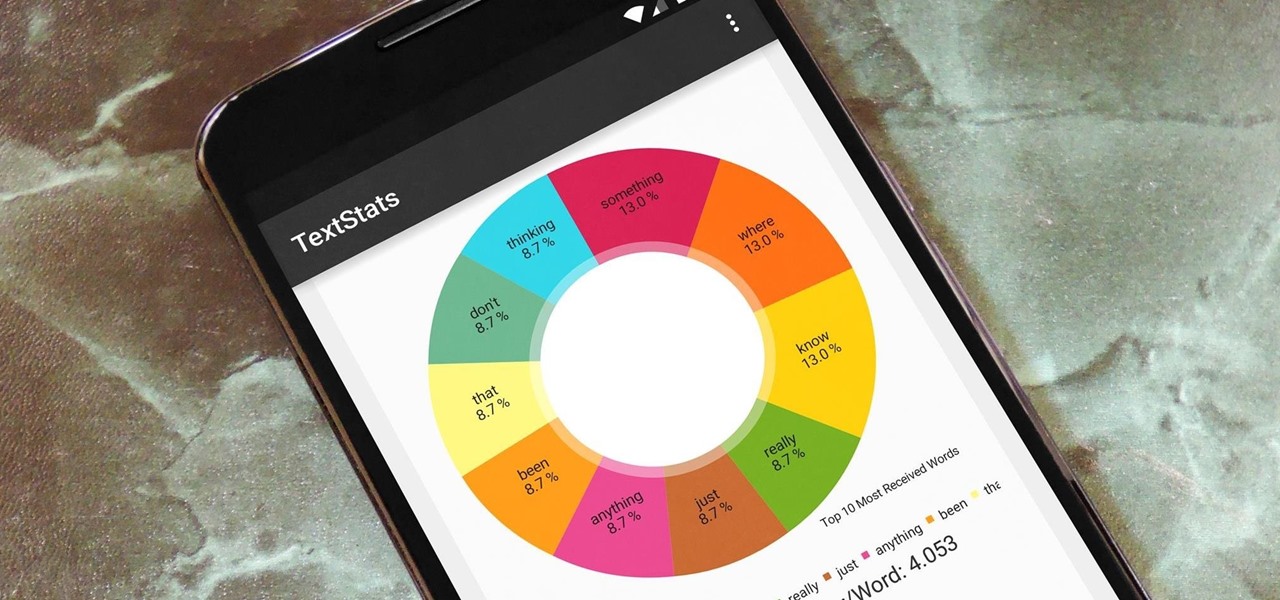
There are a lot of instances where we find ourselves typing virtually the same phrase that we've typed many times before. Whether it's the standard spousal reply of "I'll be home in a few", or a work-related phrase like "I'll have that to you by the end of the day", typing phrases like these can feel very redundant at times.

Netflix has received a lot of publicity lately, and not because of its impressive worldwide library. From blog wars with Comcast to streaming deals with Verizon, it's easy to forget that the company exists for our entertainment, but sometimes that entertainment has drawbacks.

The old "my battery is dead" excuse for not calling your mother may soon be a thing of the past. A team from the Korea Advanced Institute of Science and Technology (KAIST), led by Professor Jo Byeong-jin, has developed a "wearable thermo-element" that can be built into clothing to power your electronic devices. The science behind the innovation converts body heat (thermal energy) into usable electric energy. Made with lightweight glass fiber, this small thermo-element strip can produce about ...

With the release of Jelly Bean, Chrome became the default web browser on Android. The wildly successful desktop browser was now fully entrenched in the world's largest mobile operating system.

Whenever I hand my tablet over to someone, my heart always races for a second at the thought that they may stumble across my private pictures, texts, and videos. I trust them, and they may not be the snooping type, but it can be easy enough to come across private stuff by accidentally opening a gallery or messaging app.

You have warm toast, but your butter is chilled to a rock-solid state. Sure, you could warm a bit of that butter up in a microwave before spreading, but chances are you're just as impatient as the rest of us, so you slap that frigid butter on and hope for the best. It always ends up the same, though.

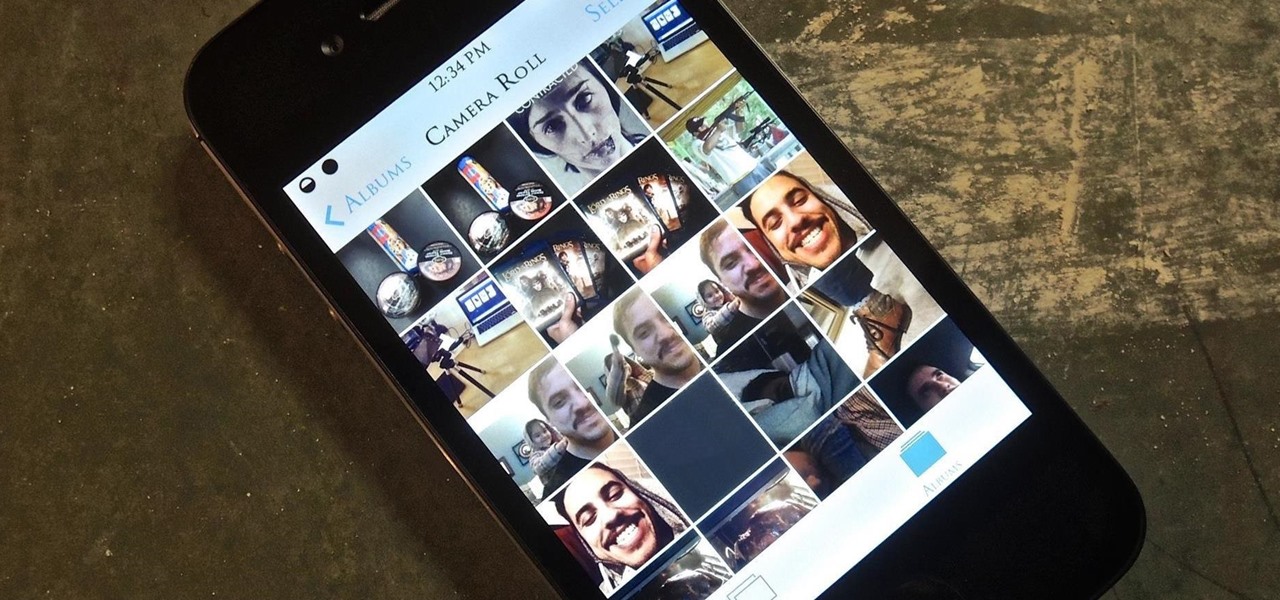
I have over 400 photos on my iPhone, and I don't even know where half of them came from. Scrolling through all of those pictures is a pain in the ass, but it's not nearly as bad as trying to actually find an old image. Organization is not my strong suit, so I'm definitely not the type to create new albums to sort through my 400+ photos.

I regularly listen to music on my Nexus 7 while working or playing my Xbox. It's light and easy to carry around, and has basically become an extension of my body. The only thing that bugs me is having to constantly turn the screen on to pause or change music tracks. Even if I can do it from my lock screen instead of the actual music player app—I don't want to.

My friends can be pretty shitty sometimes, but they're my friends nonetheless. On various occasions, they've secretly taken my device and made me look foolish by posting crude and embarrassing posts to Facebook, Instagram, or Twitter. With friends like these, who needs enemies, right? And it's because of these types of friends that we need to substantially upgrade the app security on our devices.

The space on your phone is extremely valuable, so getting the most out of your screen real estate can help you out when multitasking or for just making your device feel bigger. One thing that is often overlooked when it comes to saving space on the screen is the keyboard.

The absence of a physical keyboard is both a gift and a curse. When it was announced in 2007 that the first iPhone would have a touchscreen only, people literally lost their shit. Now, almost 7 years later, you'd be hard-pressed to find a smartphone that still has a physical keyboard.

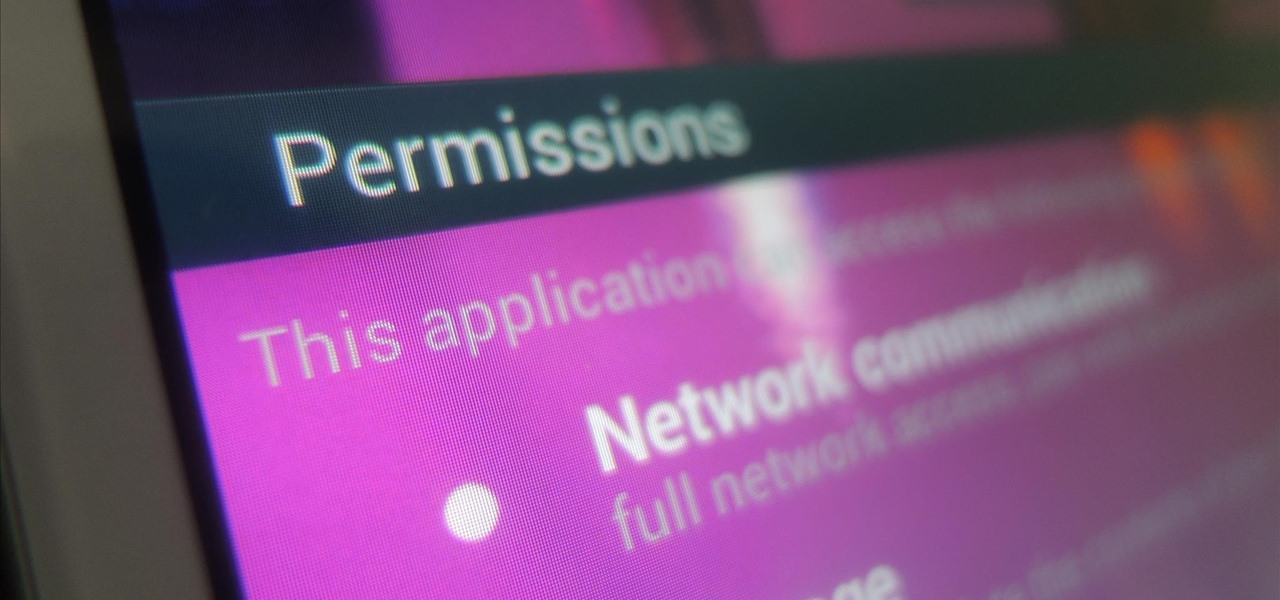
While we're usually responsible for leaking our own private information through mediums like Facebook, there are other times when we mistakenly and unwillingly allow certain applications to scour through our personal data. Some apps may have enabled permissions for internet access, thus allowing it to share said data with its external servers.

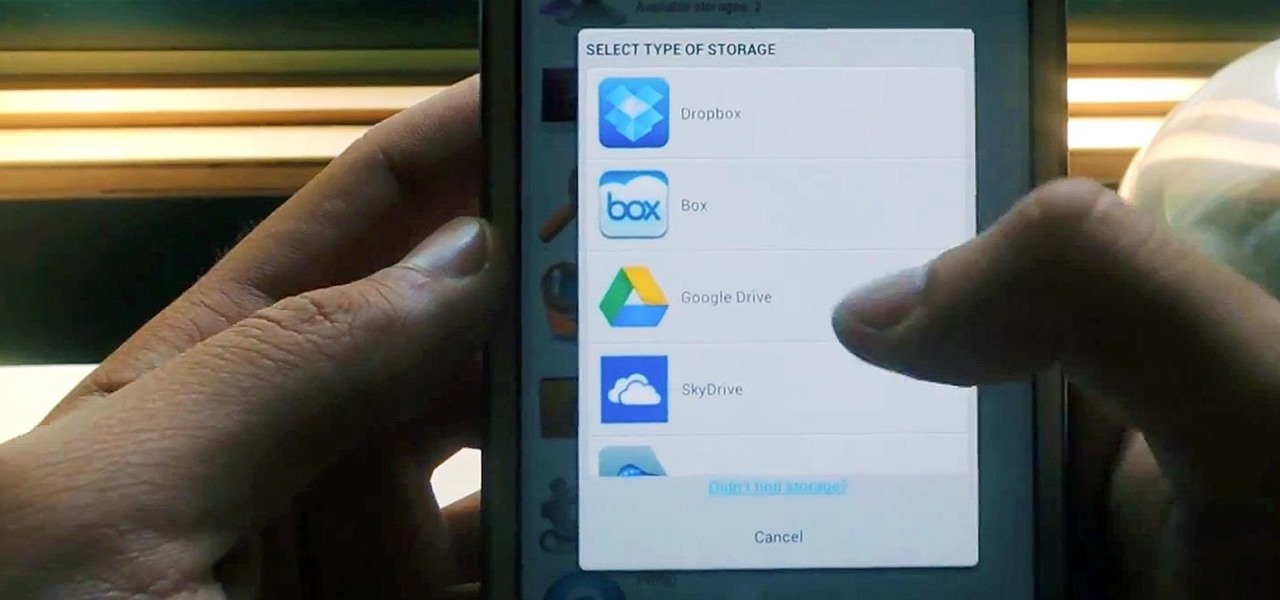
Cloud storage looks pretty good compared to the heavy restrictions that hard drives and other types of external memory carry. The cloud is not only limitless in what it can hold, but it can also easily be accessed from any device that has Internet—your smartphone, work computer, personal laptop, tablet, and more. While accessing a specific cloud storage system like Dropbox or Google Drive may be easy on your Samsung Galaxy Note 2, managing all of them individually can not only get confusing, ...

In my first tutorial on Linux basics, I discussed the importance of hackers using Linux and the structure of the directory system. We also looked briefly at the cd command. In this second Linux guide, I'll spend a bit more time with changing directories, listing directories, creating files and directories, and finally, getting help. Let's open up BackTrack and getting started learning more Linux for the aspiring hacker.

Rooting your Samsung Galaxy S4 has many advantages; theming, free wireless hotspots, deleting system apps, and generally being ahead of the curve when it comes to updates. It's also great for simple things like centering your clock or freezing apps.

Welcome back, my newbie hackers! We've already saved the world from nuclear annihilation and covered our tracks afterwards, but the world is still threatened by a malicious, megalomaniacal dictator with missiles and nuclear weapons.

Unwanted advertising is everywhere. Annoying pop-up ads, overly loud late night commercials, spam...it never ends. And before spam, there was junk mail. Junk mail is even worse because unlike TV commercials and internet ads, it's physical. You can't just delete or ignore it—and it's an awful waste of paper. So what can you do about it?

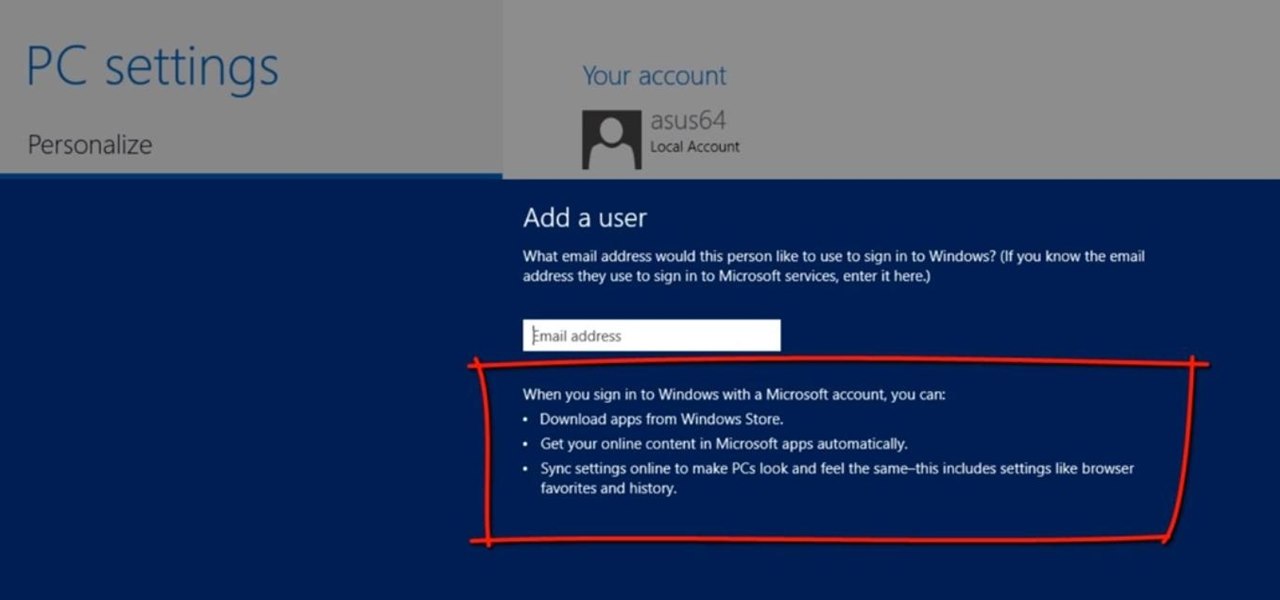
This Windows 8 tutorial will show you how to create a local user account on your PC. When you create a local user PC account, you will only have access to your account from that individual computer. A local Windows 8 user account uses a user name and password to login.

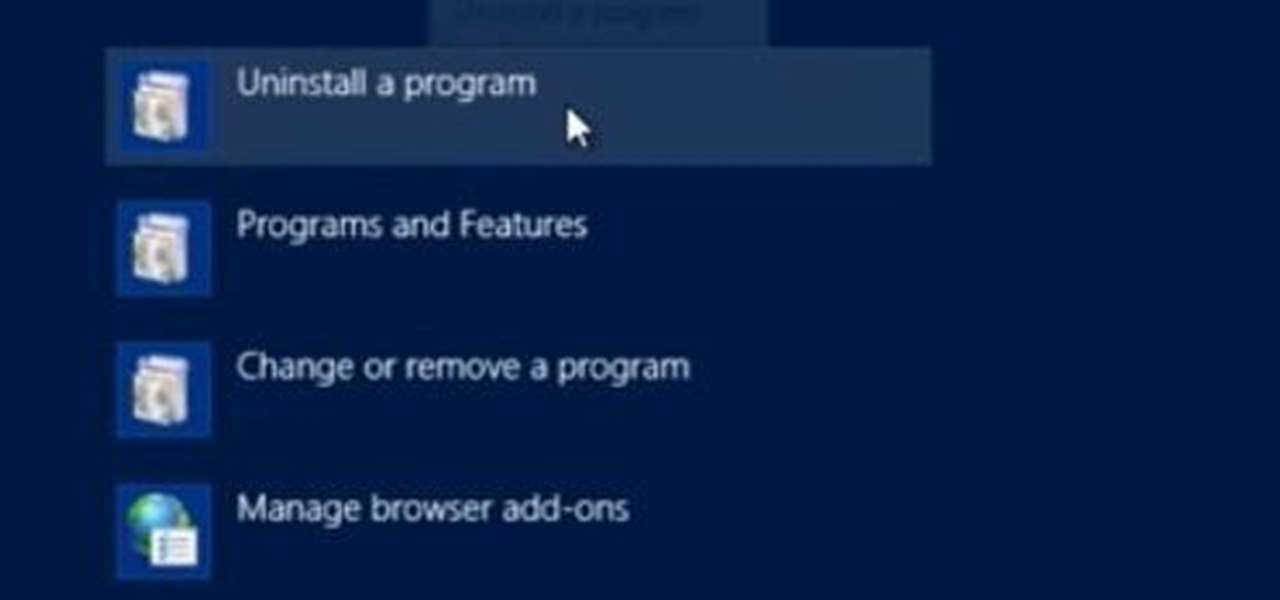
In this Windows 8 tutorial, I will show you how to uninstall applications that you no longer need or do not want on your computer.