
How To: Wear Hijab in different styles
Learn how to wear different types of hijab in different styles in this two part series. The hijab details have been explained in terms of the hijab material and hijab durability.


Learn how to wear different types of hijab in different styles in this two part series. The hijab details have been explained in terms of the hijab material and hijab durability.

This is a great video that breaks down the different types of microphones available and how you can use them to get different results or resolve different problems. If you use the right microphone, your videos will come out that much better.

Does your video look flat? By using Three Point Lighting, you will be able to give your flat video more dimension. In this tutorial, Israel Hyman demonstrates the effects of the key light, the fill light, and the back light. This is a long standing lighting technique that you definitely should know if you plan on shooting any type of video.

Coach Tom Martin discusses different techniques for shooting and the various types of shots used in the game. Among these are the wrist shot, snap shot, and the slap shot. A recap is given at the end of the video. Throughout the video, tips appear in the form of pop ups.

Tennis Pro Brad Gilbert discusses and shows techniques for hitting an overhand smash. The types of overheads discussed are the basic, scissor-kick, backhand, and bounce. They are summarized at the end of the video. Additional information is given in sidebars and popups during the video so it's easy to understand.

This video demonstrates how to work the medial deltoid muscles on an ordinary gym machine, the lateral raise. This video walks you through setting up the machine to your body type and doing the excercizes correctly on the machine.

How to fix those loose and jiggly cupboard doors on your kitchen or bathroom cabinets. For this repair, you're going to need a flat head or phillips head screwdriver. Now, the type of screwdriver you're going to need is really dependent on the type of screw you have holding your cabinet door to your cabinet. We're going to use a phillips head screwdriver because, as you can see here, the top of our screw head is shaped like that of a crosshair. If it were shaped like one long groove in a stra...
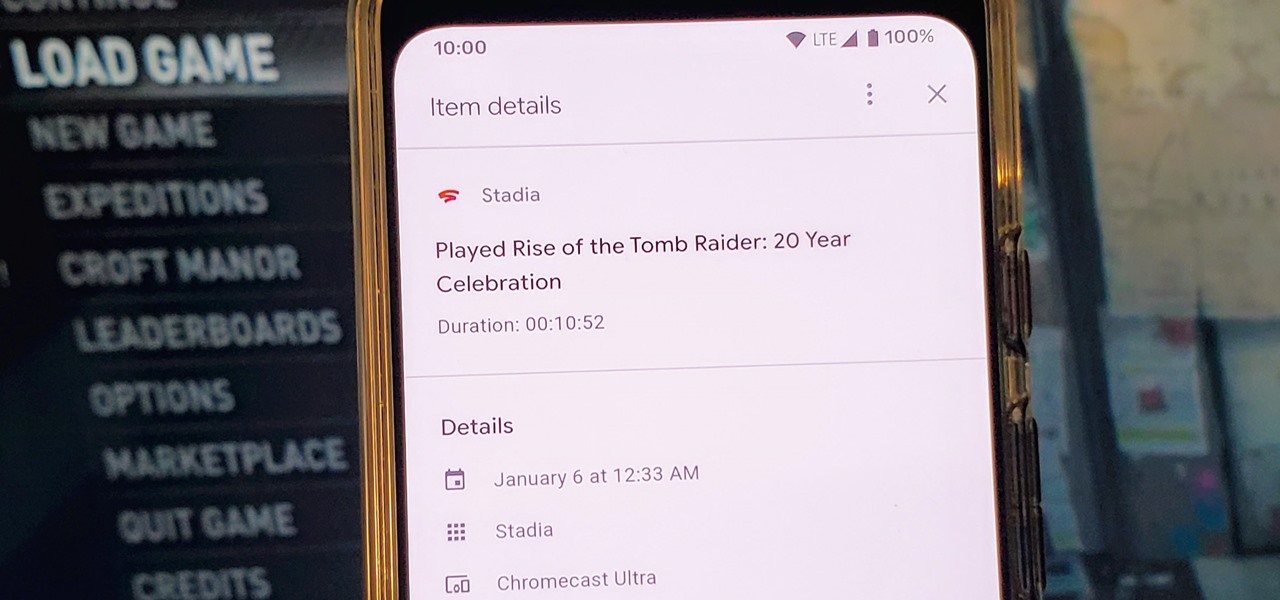
Since Stadia is an early access game streaming platform, Google is still working on bringing big things to the table. You can expect wireless Stadia controller support for many more devices, high-quality 4K gaming on all Chrome web browsers, and more Google Assistant features. They also managed to silently sneak in a way to keep track of your Stadia gaming sessions too, which is pretty handy.

Brute-forcing is an easy way of discovering weak login credentials and is often one of the first steps when a hacker finds network services running on a network they gain access to. For beginners and experienced hackers alike, it's useful to have access to the right tools to discover, classify, and then launch customized brute-force attacks against a target. BruteDum does it all from a single framework.
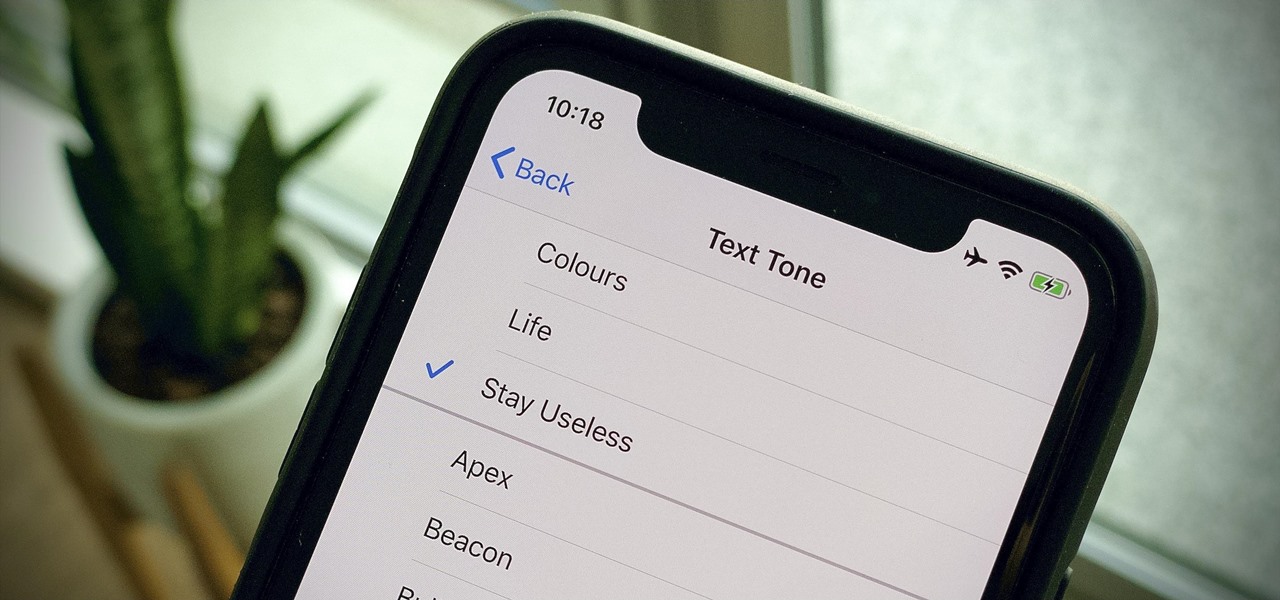
Apple hasn't refreshed its text tones on iPhones since iOS 7. That's six years of the same sounds. And while text tones like Bamboo and Hello have undoubtedly aged like fine wine, that's still too long to live with the same old sounds day after day. Let's take matters into our own hands — let's make our own text tones, right in Music on macOS 10.15 Catalina.

Apple's latest update for iPhones, iOS 13, introduces over 200 new and exciting features. Many of those changes come to Siri, resulting in a better, more useful version of the digital assistant we've known for years. If you simply look at iOS 13's webpage, however, you wouldn't realize just how much Siri has changed this time around. We're here to fill in the blanks.

The art of privilege escalation is a skill that any competent hacker should possess. It's an entire field unto itself, and while it's good to know how to perform the techniques involved manually, it's often more efficient to have a script automate the process. LinEnum is one such script that can be incredibly useful for privilege escalation on Linux systems.
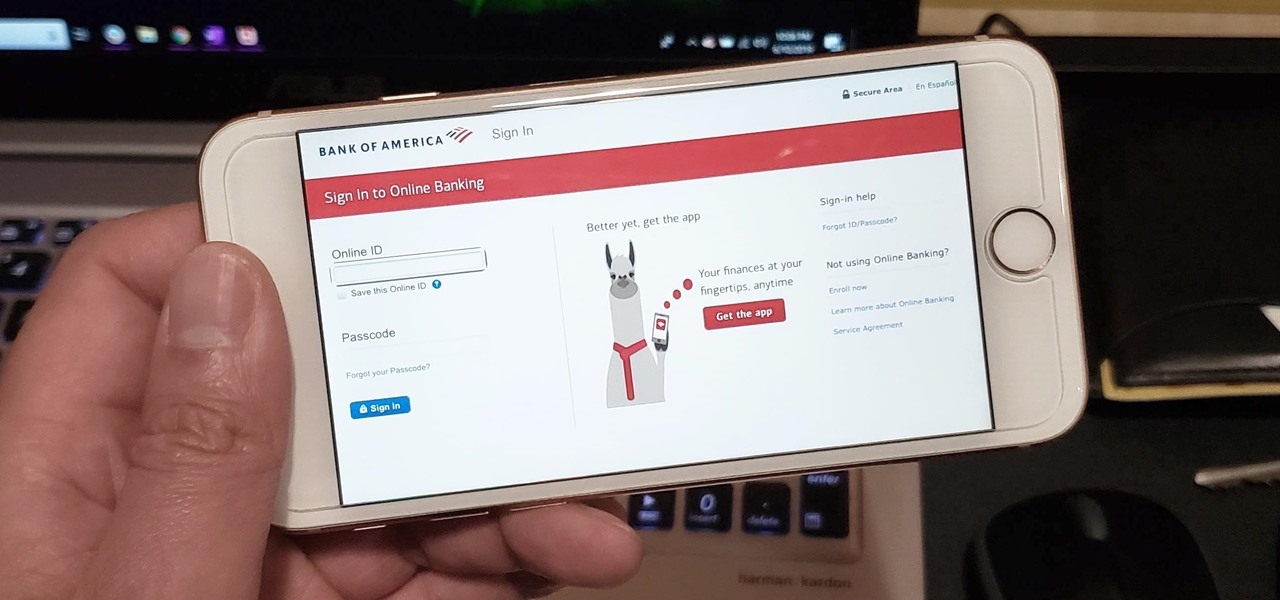
Ever since iOS 7, you could ask Safari on iPhone to show you the desktop version of a website, and in iOS 9, it became even easier to do. However, it's always been a hidden feature, something you wouldn't know is there without reading articles or tips online telling you what to do. Apple's iOS 13 update shines a light on it so everyone will know it's there, ready to use.

If you find yourself with a roommate hogging limited data bandwidth with video games or discover a neighbor has invited themselves into your Wi-Fi network, you can easily take back control of your internet access. Evil Limiter does this by letting you control the bit rate of any device on the same network as you, allowing you to slow or even stop data transfer speeds for them completely.

Apple's scheduled to show off the first look of iOS 13 at WWDC 2019 on June 3, but what will the new operating system hold for iPhone? Rumors suggest that many features initially planned for iOS 12 will show up in iOS 13, codenamed "Yukon," and dark mode will be the big ticket item this year.
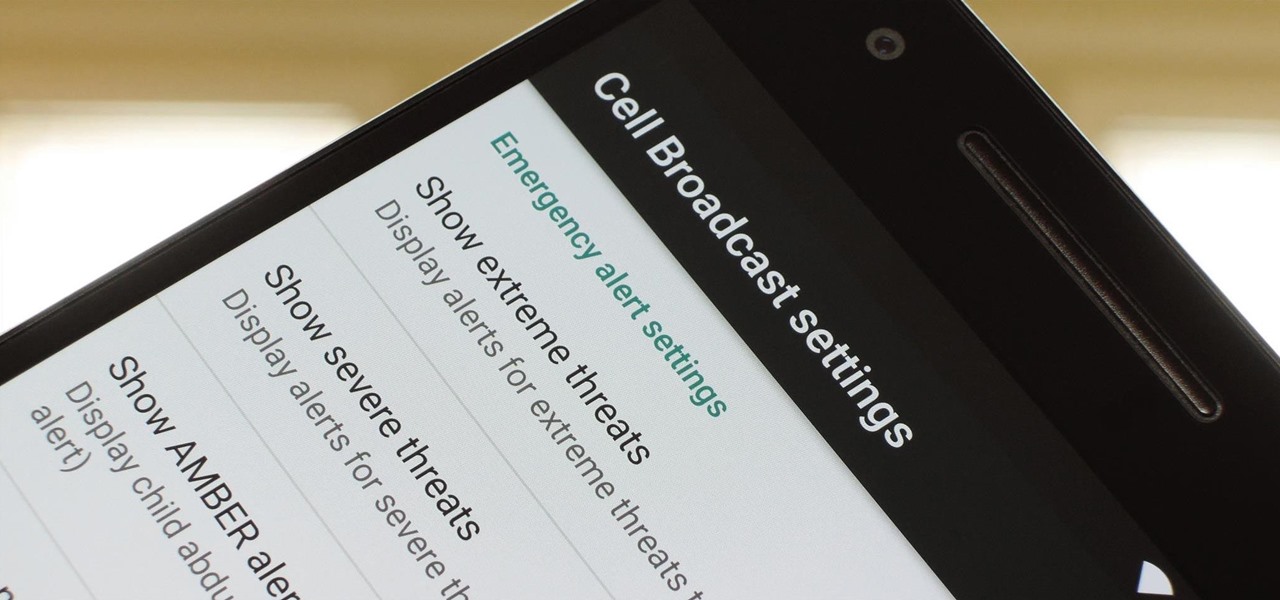
To bring things up to code with a new FCC standard, Android recently added an "Emergency broadcasts" feature that will make your smartphone notify you whenever a potential safety threat or Amber Alert is posted in your area. Even if you have your phone set to silent, these emergency alerts will cause your device to emit a loud, piercing sound when a potential threat is nearby.
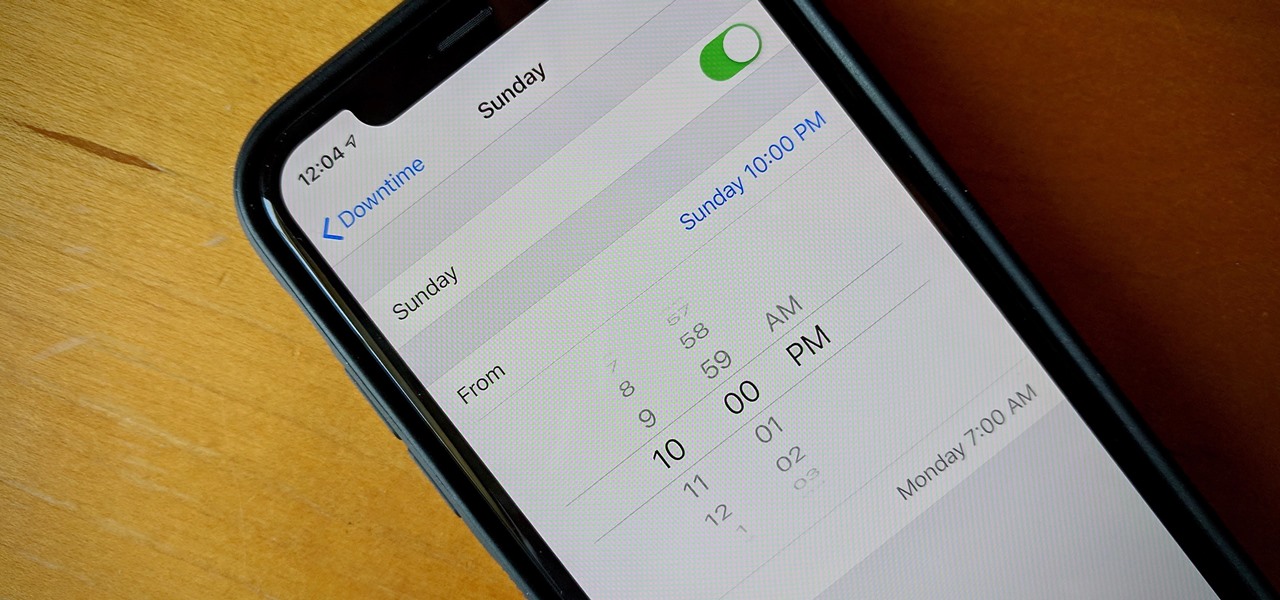
When Apple released its Downtime feature in iOS 12, it gave us an easy way to control how much time we spend on our iPhones — but it wasn't perfect. When setting Downtime, you' were forced to use the same time schedule for every day of the week, so your weekdays and weekends had the same restrictions. Apple fixed that issue in iOS 12.2 and later, so lockout periods can be more customized.

Waking up your Apple Watch to see "your heart has shown signs of an irregular rhythm suggestive of atrial fibrillation" might come as a shock. While your watch can send you warnings if it detects a fast or low heart rate, those messages are pretty vague, while the abnormal arrhythmia alert can downright scary. So what should you do if you receive one of these AFib notifications?
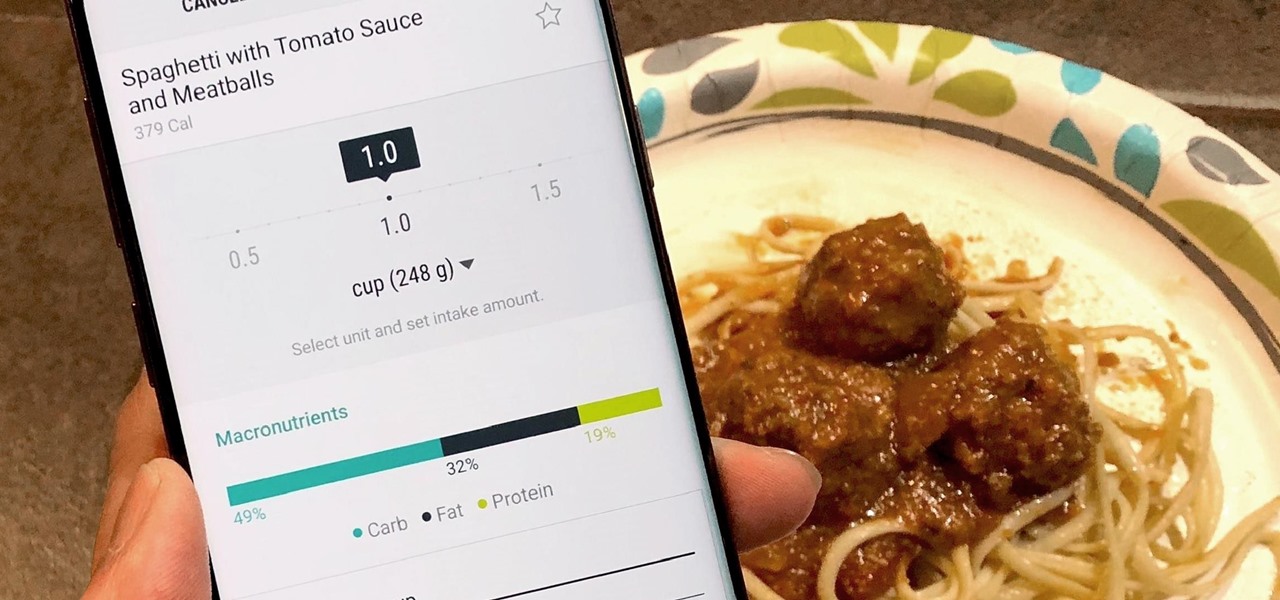
The most essential part of a healthy lifestyle is managing your diet — after all, what would be the point of a daily workout regimen if you were eating junk food? Thankfully, Samsung Health makes it easy to record your calorie and nutrient intake to get a clear picture of your dietary habits and how you can make them better.

Cracking the password for WPA2 networks has been roughly the same for many years, but a newer attack requires less interaction and info than previous techniques and has the added advantage of being able to target access points with no one connected. The latest attack against the PMKID uses Hashcat to crack WPA passwords and allows hackers to find networks with weak passwords more easily.

If you're on the hunt for a profitable side-gig, or even a completely new way to to make money, you'll want to take a look at Upwork, a leading freelancing platform that connects skilled freelancers with clients from all over the world.

Wi-Fi devices are continually emitting "probe frames," calling out for nearby Wi-Fi networks to connect to. Beyond being a privacy risk, probe frames can also be used to track or take over the data connection of nearby devices. We'll explain how to see nearby devices emitting probe frames using Probequest and what can be done with this information.

The HoloLens team is finally beginning to realize that to truly engage the mainstream, augmented reality needs to make its way out of the lab or factory floor and onto the streets.

Wi-Fi tools keep getting more and more accessible to beginners, and the LAZY script is a framework of serious penetration tools that can be explored easily from within it. This powerful and simple tool can be used for everything from installing new add-ons to grabbing a WPA handshake in a matter of seconds. Plus, it's easy to install, set up, and utilize.

It is often said that the best hackers remain unknown, and the greatest attacks are left undiscovered, but it's hard for an up-and-coming penetration tester or white hat to learn anything unless one of those factors is actually known or discovered. But the end goal here in our SQL injection lessons is to make that statement as true as possible for us when performing our hacks.
Sure, emojis are all the rage, but there's not an emoji for every emotion or feeling just yet. That's where emoticons come into play, emoji's older typographical sibling. Unfortunately, emoticons can be hard to type out, easy to forget, and ASCII art, in general, can be pretty time-consuming to create from scratch — but there's an easy way to forgo all these issues — make keyboard shortcuts.
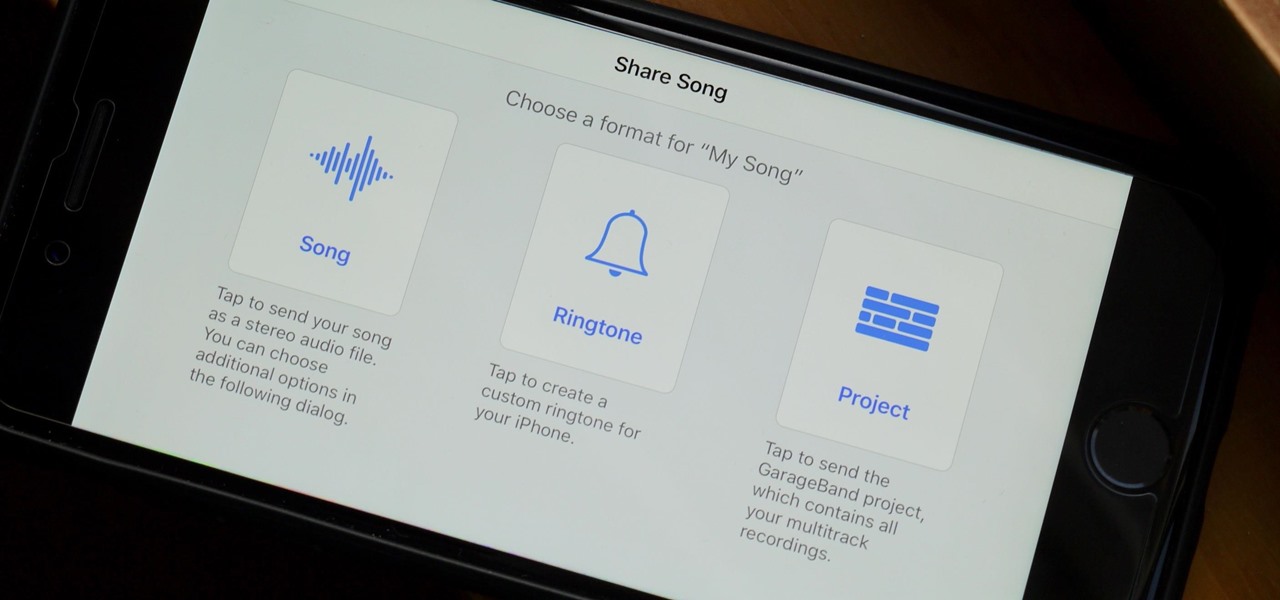
When you make an awesome song or beat that you're proud of in GarageBand for iOS, one way to show it off is to turn it into a ringtone or alert tone for your iPhone. That way, anytime you get a phone call or a notification, your musical creation will sound off, and everyone around you will hear it in all its glory. Plus, it's way cheaper to make your tones than to buy them off of iTunes.

Format strings are a handy way for programmers to whip up a string from several variables. They are designed to save the programmer time and allow their code to look much cleaner. Unbeknownst to some programmers, format strings can also be used by an attacker to compromise their entire program. In this guide, we are going to look at just how we can use a format string to exploit a running program.

Configuring onion services for the first time can be tricky. A surprising number of system administrators make seemingly trivial mistakes that ultimately lead to catastrophic cases of de-anonymizing supposedly anonymous sites on the dark web. OnionScan is a tool designed to identify common misconfigurations in onion services and aid us in understanding how to fix them.

JavaScript is one of the most common languages used on the web. It can automate and animate website components, manage website content, and carry out many other useful functions from within a webpage. The scripting language also has many functions which can be used for malicious purposes, including stealing a user's cookies containing passwords and other information.

While hackers adore the command line, working with the GUI (graphical user interface) of an operating system has some advantages. This is especially true when it comes to post-exploitation. When we can control the mouse and keyboard of a remote computer, we can truly say we have complete control over the device. Today, I'm going to introduce to you the PyAutoGUI module, which does just that, and just how much fun you can have with it!

Barrow's article on Pupy made me wish for a RAT that could target an OS frequently used by gatekeepers at startups, tech companies, and creative firms: macOS. Once run, a RAT can do severe damage by dumping a user's stored credentials for many accounts. The best loot lives in the Chrome Password cache, and EvilOSX, an OS X RAT, infiltrates macOS and dumps these credentials.

Unless you're a WhatsApp pro user, you may be surprised to know that there are text formatting options that you can apply to your messages. Markdown characters can help you emphasize certain words or phrases by making them italicized or bold, and it'll even let you cross out words and change the font. It's one of those nice touches that isn't available in most other messaging apps.
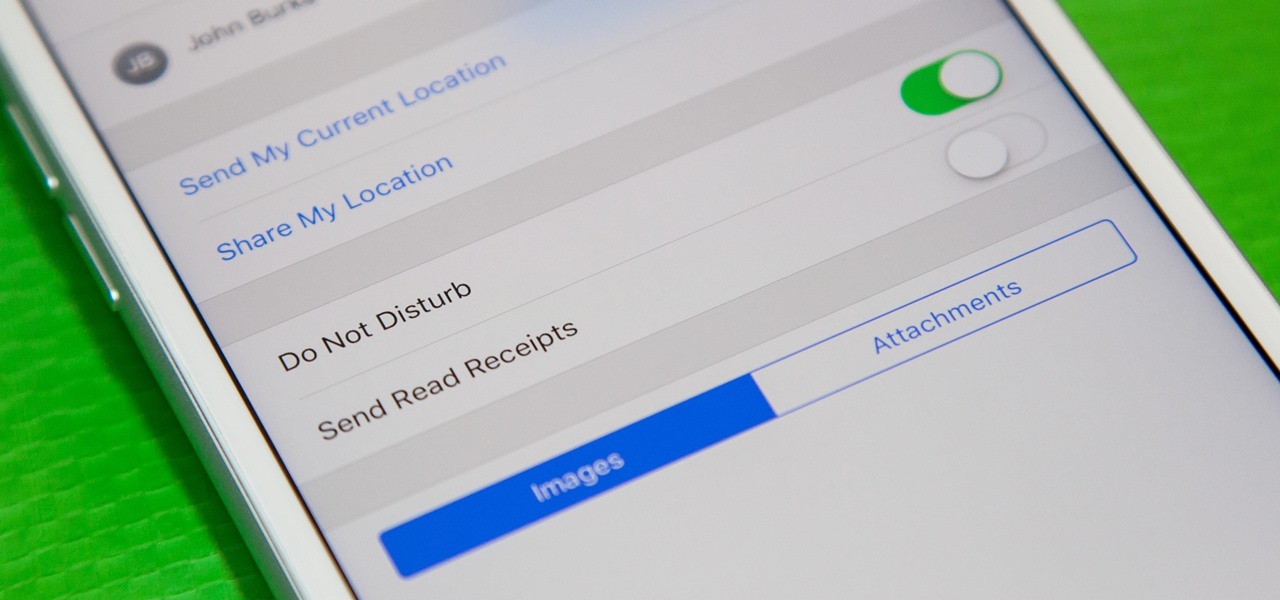
When somebody is in the middle of rapid firing you some text messages and they become too much for you to bear, you have a few options on your iPhone. You can simply leave the conversation, if it's an iMessage group chat with four or more participants, or you can put the whole message thread on silent, which applies to everyone, no matter if it's iMessage, SMS, MMS, or a group conversation.

The new Leaf with Nissan's ProPilot driverless feature could launch as soon as this year, following a teaser image and video the Japanese carmaker released of its flagship EV yesterday.

The $25 million development alliance Jaguar Land Rover's mobility unit InMotion has formed with US-based ride-share firm Lyft reflects how the British luxury carmaker is leaning towards a fleet service business model for its driverless offerings.
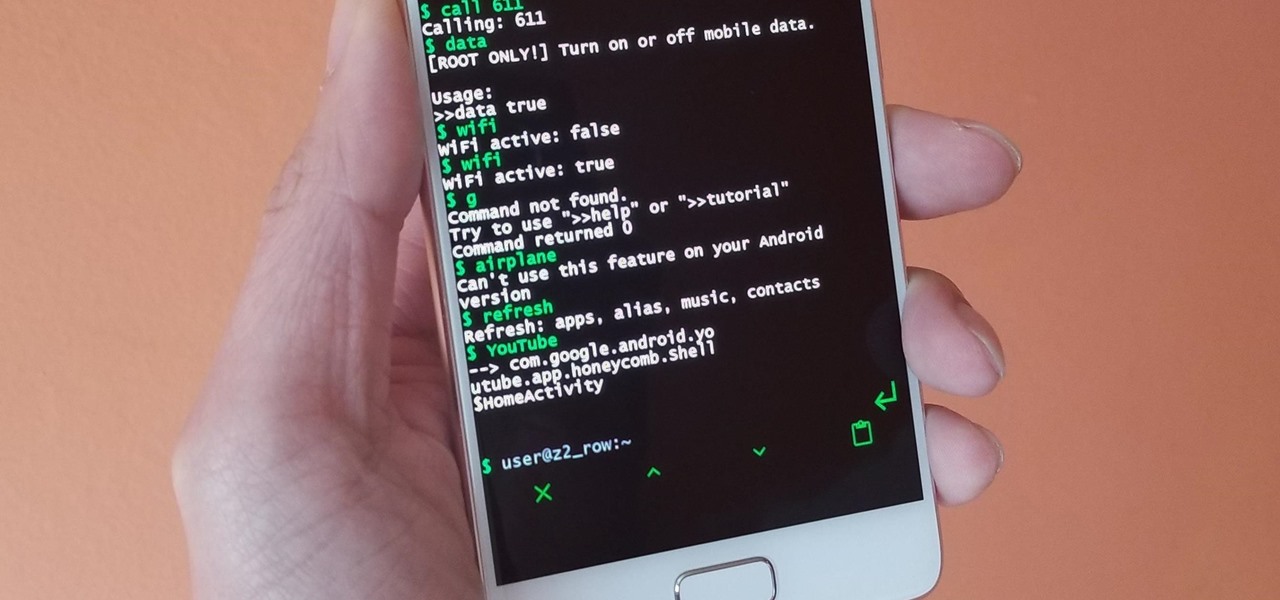
Running commands on Linux seems so complicated for the layman that it may as well be a foreign language. But for the die-hard terminal users, or for those who are just curious about the Linux experience, there's a new Android launcher that gives your home screen a command line makeover.

Connecting your devices with a cable is the fastest and most reliable way to transfer files between them. Now that most Android devices have either USB Type-C or a Micro-USB port that supports USB OTG, phones are capable of importing media files directly from a camera using a simple (and cheap) adapter.

Our quest to find novel compounds in nature that we can use against human diseases —a process called bioprospecting — has led a research team to a small frog found in India. From the skin slime of the colorful Hydrophylax bahuvistara, researchers reported finding a peptide — a small piece of protein — that can destroy many strains of human flu and can even protect mice against the flu.

We can add one more health effect of our gut bacteria to the growing list. Researchers from the UK have just reported that the gut microbiota plays a role, both directly and indirectly, on the toxicity and efficacy of chemotherapy. Their findings are published online in the journal Nature Reviews Gastroenterology & Hepatology.