While developers received iOS 12.2 beta 3 on Feb. 19, public beta testers had to wait one extra day, following suit with previous iOS 12.2 beta releases. The third beta update includes fixes for Group FaceTime and the missing date on the lock screen, as well as a few tiny app updates.
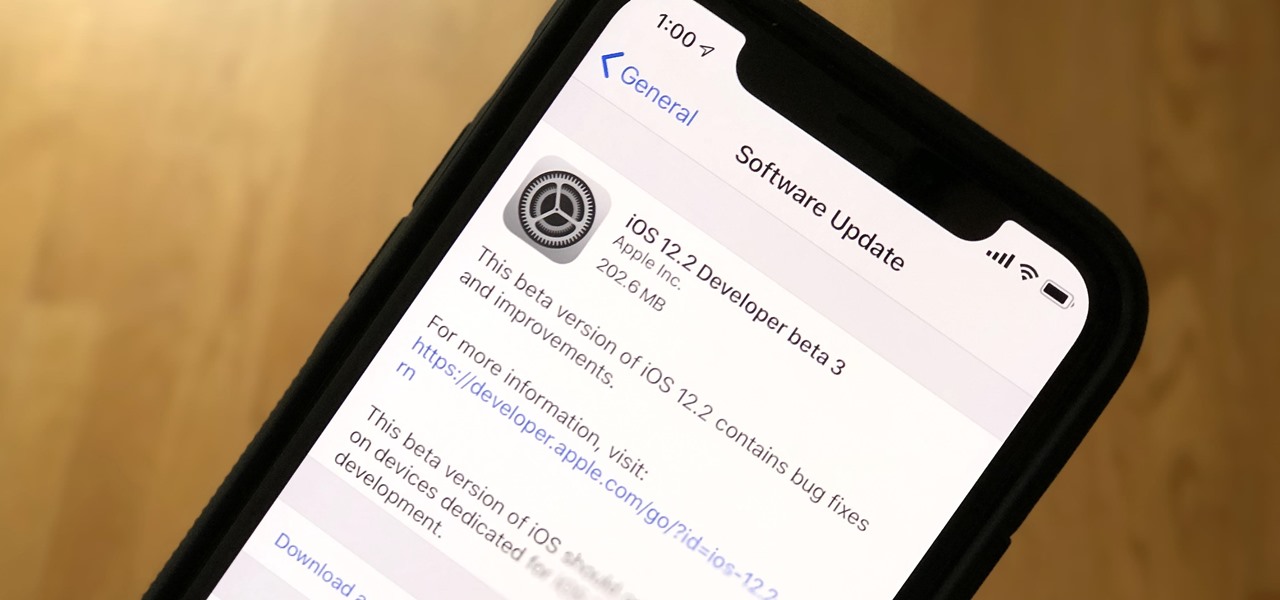
Apple just released the third iOS 12.2 developer beta Tuesday, Feb. 19, fifteen days after the release of iOS 12.2 developer beta 2. Beta 3 fixes an issue with the lock screen, and reintroduces Group FaceTime to beta testers. Overall, iOS 12.2 hosts a wealth of new features as well as bug and security patches.

While Apple has moved on from Touch ID to Face ID in newer iPhone models, there are still plenty of iPhones with fingerprint sensors — in fact, Apple's second-generation iPhone SE is the first new Touch ID iPhone in three years. With Touch ID, you can register up to five fingerprints, but it doesn't stop there. Using a little-known trick, you can sneak another five fingerprints in there for a total of ten.

There once was a time in the Android rooting scene where we couldn't rely on using a custom recovery for all of our modding needs. Manual file flashing was very popular in the early days of Android before custom recoveries started taking over. With the rise of TWRP, it seemed like there was almost no need for manual file flashers; however, they appear to be making a welcomed return in a big way.

Things that are supposed to make life easier for developers and users are often easy targets for exploitation by hackers. Like many situations in the tech world, there is usually a trade-off between convenience and security. One such trade-off is found in a system known as Distributed Ruby, which can be compromised easily with Metasploit.

In about 27% of all car crashes, someone was using their cell phone. You may think texting is the big problem here, but many fail to realize that even the smallest smartphone interaction could spell disaster. Thankfully, Google Maps has rolled out an overdue feature that'll help ensure a safer drive.

Depending on how you use your phone, you may have noticed your status bar is a bit crowded due to various icons being enabled. While some icons make sense to have, such as Wi-Fi and Bluetooth, the VPN key icon can be redundant, especially if the app uses a notification. Good thing, there is a way to get rid of the icon.

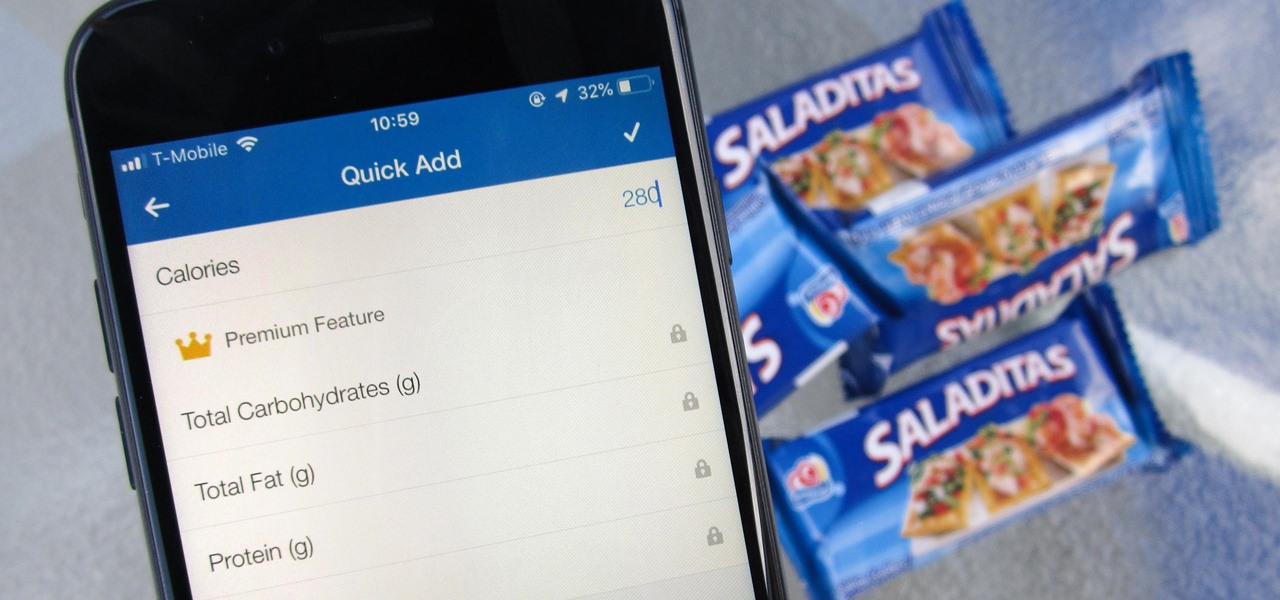
It's only normal to snack on a few french fries every once in a while when you're on a diet, but it's still important to hold yourself accountable, even when you cheat just a little bit. MyFitnessPal, for both Android and iOS devices, has a database of nutritional information to help keep track of the meals you eat, but it also has a way to add calories on the fly without digging for data.

Last year, Razer kicked off a new trend by building a smartphone from the ground up with mobile gamers in mind. At the time, many thought the Razer Phone solved a problem that no one really had — but a year later, we're starting to see that gaming phones are perfect for more than just Fortnite players.

It's the icing on top of your cake (or whipped cream on top of your Android Pie) of despair. You may have not had the easiest time rooting your device, but you feel like you overcame all of the obstacles. Only now to discover that those very apps and mods you were rooting for still won't work — and the signs point to a lack of root access. Don't lose hope, because we have some tricks up our sleeve.

With the recent launch of the OnePlus 6T, the company continues to impress us with some of the best phones when it comes to the rooting and modding. OnePlus has made it easy enough to get up and running with the rooting process as fast as possible. The OnePlus devices follow the same core principles Google uses for their Pixels, which is excellent news for both the user and the development side of things.

Let's face it, iPhones are expensive. With the latest iPhone XS Max reaching as high as $1,449, our wallets could all use a little support. That's where Black Friday comes in, supplying us with deals and discounts on iPhones of all kinds. If you're looking for a new iPhone this holiday season without having to break the bank, you've come to the right place.

A week after the L.E.A.P. Conference, our cup of Magic Leap news continues to floweth over, with the company's content chief giving us some insight into the company's strategy, and Twilio sharing what its virtual chat app looks like.

Over the years, Magic Leap's long-cultivated shroud of mystery led some onlookers to buy into the company's dream before even trying the device, while for others, the secrecy seems to have stoked the kind of resentment and overcorrecting critique usually reserved for the mighty Apple.

One of the things that sets a seasoned hacker apart from the script kiddies is the ability to effectively sneak past antivirus defenses when executing an attack. One way to do this is to use custom shellcode in an exploit. Not everyone is an expert at writing shellcode, but luckily there's an easy way to do this that is both quick and effective.

On the surface, AppleCare+ seems like an expensive and gimmicky option to tack onto your already pricey iPhone 11, 11 Pro, or 11 Pro Max. Upon further inspection, however, you'll see that its seemingly expensive price tag is chump change compared to the fees you'll have to pay if you end up having to repair your premium device outside its one-year warranty.

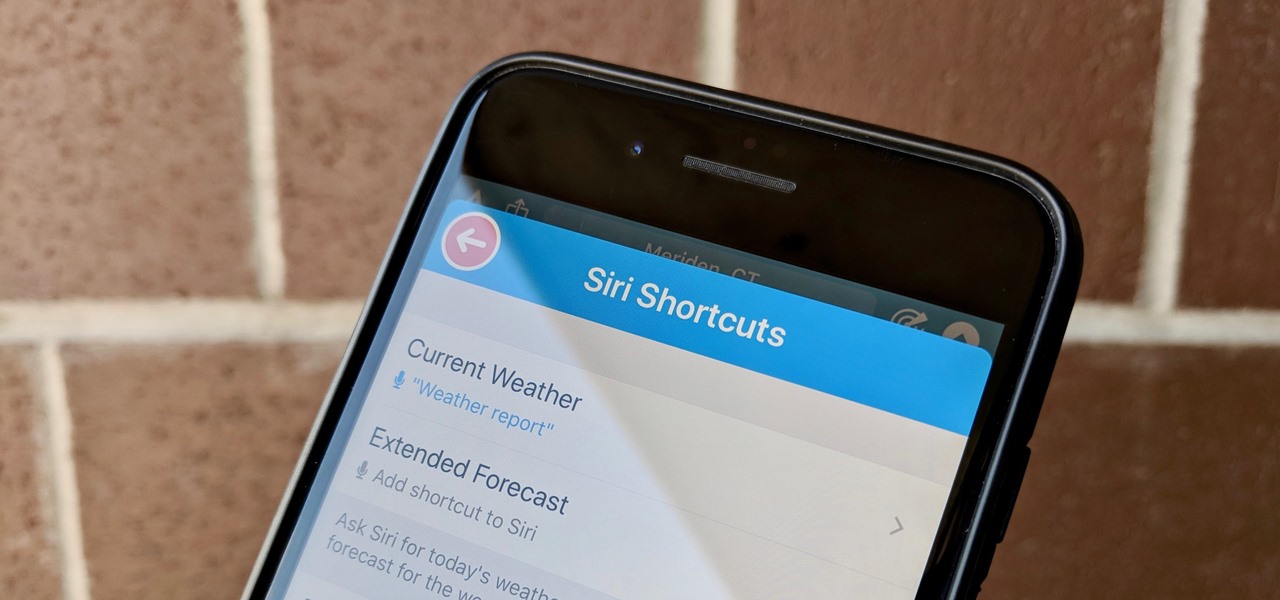
Since its humble beginnings on the iPhone 4S, Siri has come a long way. While each iteration of iOS sees new features for the iPhone assistant, iOS 12 offers users some of the best advancements in Siri we've seen in a long time, not the least of which is support for Shortcuts, Apple's replacement to the Workflow app.

From its introduction and all the way through iOS 11, FaceTime has been restricted to one-on-one calls. Apple will be changing that in a future iOS 12 update with Group FaceTime, which adds support for up to 32 people total in group audio and video calls. But that's not all we'll be getting in iOS 12 — there are more features that FaceTime has or will be getting soon that you should know about.

The first few minutes after gaining access to a MacBook are critical — but where do we begin? Using tools built into macOS, we can develop an in-depth understanding of running background processes, detect antivirus software, locate sensitive files, and fingerprint other devices on the network. All of this can be done without installing additional software or modifying any files.

While it's not the best shopping holiday of the year, Labor Day does have a few sweet deals on smartphones this weekend. There are phones from OEMs such as Apple, Motorola, and Sony on sale, to name a few, from stores such as Amazon, Best Buy, and Walmart.

From day one, my favorite thing about the Magic Leap One has been its portability. It's so well designed that it just screams to be taken out for a walk through the city. Alas, Magic Leap says the device is (currently) designed to be used indoors, preferably in settings containing few windows or black surfaces.

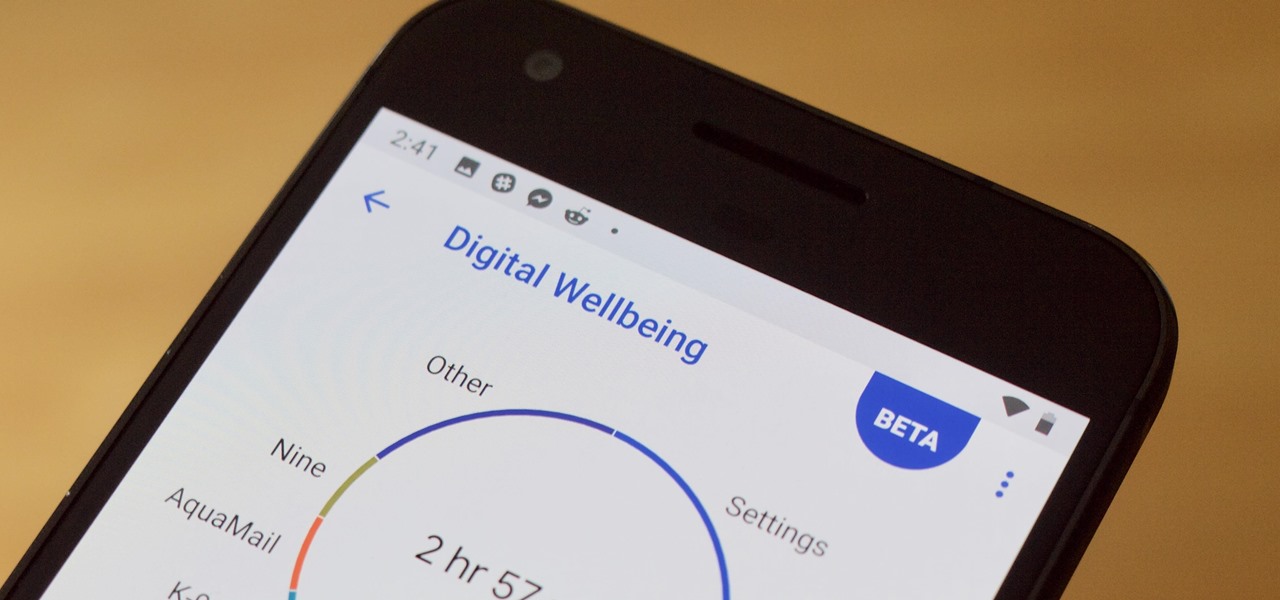
Is your smartphone taking over your life? Do you need help putting your Pixel down at night? Well, update to Android Pie! Android 9.0 comes with Digital Wellbeing, a new tool to both help you understand your smartphone habits and perhaps step away from the apps, games, and notifications every now and then.

The gig economy is thriving, and if you aren't already making money with your phone, you could be missing out on easy residual income. Some people just want extra cash, and some even manage to completely ditch the 9–5, enabling them to work at their own pace and set their own hours.

Due to weaknesses in the way Wi-Fi works, it's extremely easy to disrupt most Wi-Fi networks using tools that forge deauthentication packets. The ease with which these common tools can jam networks is only matched by how simple they are to detect for anyone listening for them. We'll use Wireshark to discover a Wi-Fi attack in progress and determine which tool the attacker is using.

There are dozens of apps like Glympse, Family Locator, and Find My Kids that let parents see where their children's phones are, but they all have one fatal flaw: It's incredibly easy to spoof locations to make it look like the phone is somewhere else.

You may have heard of a signal jammer before, which usually refers to a device that blasts out a strong enough radio signal to drown out the reception of nearby devices like cell phones. Purpose-built jammer hardware is outright illegal in many countries. Still, Wi-Fi is vulnerable to several different jamming attacks that can be done with Kali Linux and a wireless network adapter.

It wasn't Christmas, but for Amazon Prime members, it was darn close: Amazon Prime Day, one of the biggest shopping days of the year, came and went earlier this week. Unfortunately, there weren't many Prime Day-specific deals to be had for augmented reality fans, but that doesn't mean AR-loving Amazon Prime members were completely left out.

On August 1, Google Play started requiring new app submissions to target at least Android 8.0 Oreo's API. Then, as of November 1, all updates to existing apps were required target the same API. While at first glance, this change may mean little to you, it will have a profound impact on Android. Now, your favorite apps will be getting better.

When you drive along the deceptively sedate streets of Silicon Valley, there are few hints that all those nondescript office parks and low-rise buildings contain the very future of the planet, but they really do. On a recent trip to tech's epicenter, I found that out firsthand when I got to visit the offices of Meta, the startup that produced the Meta 2 augmented reality headset.

A team of academics from three different universities and two private companies have just discovered a new vulnerability that affects almost every Android device since 2012. The vulnerability is known as RAMpage, and it could be used to gain complete control over the device.

In its latest feature with an assist from augmented reality in storytelling, the New York Times shows readers the virtual crime scene it constructed to prove that the Syrian military conducted chemical warfare against its citizens.

While there aren't as many improvements compared to iOS 11's Photos additions, the tabs menu in Apple's updated Photos app for iOS 12 was revamped to include "Memories" inside a new "For You" tab that also houses featured photos and effects suggestions. This is also where you see sharing suggestions and all of the albums others have shared with you.

There's always an iPhone in our list of top phones for privacy and security, due in large part to advanced security measures like Face ID, consistent iOS updates, and easy ways to prevent unwanted access and excessive data sharing. However, some of those options actually do the opposite and hinder security. It all depends on how you use your iPhone, but you should at least know everything available.

While numerous startups are competing to convert the AR Cloud from a pie-in-the-sky to a reality, Wikitude is thinking smaller with the latest edition of its augmented reality SDK.

Hackers rely on good data to be able to pull off an attack, and reconnaissance is the stage of the hack in which they must learn as much as they can to devise a plan of action. Technical details are a critical component of this picture, and with OSINT tools like Maltego, a single domain name is everything you need to fingerprint the tech details of an organization from IP address to AS number.

With the exception of "Reflection" on the iPhone X, Apple hasn't updated their catalog of ringtones and alarms since iOS 7 dropped back in 2013. Since then, the company has come a long way with the quality of the iPhone's speakers, but their tones haven't adapted to meet those changes. That's left an opening for others to create their own ringtones mastered for the iPhone.

Apple first included a dual-lens camera onto its iPhone 7 Plus back in late-2016, yet not many developers besides Apple have harnessed the depth data that "Portrait" mode photos provide. A relatively new app is changing that, though, by using that depth information to let you add realistic-looking light sources to your photos.

Backdooring a powered-off MacBook is easy when a few minutes of physical access is allowed. That attack works well if the hacker also shares a Wi-Fi network with the victim, but this time, I'll show how to remotely establish a connection to the backdoored MacBook as it moves between different Wi-Fi networks.

The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company email addresses, potentially giving attackers access to a company account if the employee reuses a compromised password.

The conversation of which operating system is most secure, macOS vs. Windows, is an ongoing debate. Most will say macOS is more secure, but I'd like to weigh in by showing how to backdoor a MacBook in less than two minutes and maintain a persistent shell using tools already built into macOS.