Have you ever fallen victim to a clever Jedi mind trick? Don't worry. It happens. There are evolutionary reasons as to why our brains sometimes give into the oldest tricks in the book. Fortunately, the more you understand the tricks of a salesman, the easier it is to avoid their gripping psychological influence. Clue #1: Too Much Specificity

After years of making do with a cheap knife, I finally bought a really good 8" chef's knife—a Henckels, although I was also eyeing a Global santoku. It quietly but literally changed my life.

Valentine's Day is a day for love, but it also just happens to be the time when every flower shop in town hikes up their prices. Chocolates are still relatively cheap, but I never understood why you have to give the gift of bigger love handles when something more creative gets the job done at a much cheaper price.

Welcome back, my greenhorn hackers! In a previous tutorial on hacking databases, I showed you how to find online databases and then how to enumerate the databases, tables, and columns. In this guide, we'll now exfiltrate, extract, remove—whatever term you prefer—the data from an online database.

While most people were worried about having the scariest costume when I was younger, I was always more interested in the candy. While everyone wasted time trying to perfect their costume, I was busy mapping out every detail in my city, finding the most efficient way of getting the most candy in my pillowcase(s) before the night ended. Although I'm long retired from the game, it's about time to pass along all of the tips and tricks I've learned from my youth for getting treats. So, here I pres...

Welcome back, my fledgling hackers! It's been awhile since we did a Metasploit tutorial, and several of you have pleaded with me for more. I couldn't be happier to oblige, as it's my favorite tool. For the next several weeks, I'll intersperse some new guides that'll help expand your Metasploit skills and keep you abreast of new developments in Metasploit, so look for them in the near future.

Welcome back, my fledgling hackers! The database is the hacker's "pot-of-gold," as it contains information that is very valuable to both the business and the hacker. In this, the second of my series on hacking databases, we're on the "hunt" for Microsoft's SQL Server. Although far from the most commonly used database (Oracle hold's that title), Microsoft's SQL Server is very often found in small-to-medium sized businesses. Even a few big businesses use it.

Sugru is some pretty versatile stuff. The company's slogan is "Hack things better," and for good reason. It sticks to aluminum, steel, ceramics, glass and plastics, it's waterproof and heat-resistant, and it can be molded into any shape you can imagine. Anything from your kitchen cabinets to your bicycle can be improved with some Sugru and a little creativity, and gadgets are no exception. Here are 10 of the coolest hacks to fix or upgrade your smartphone, tablet, or camera.

Just because a problem is small or superficial doesn't mean it can't annoy the living crap out of you. Others may think you're overreacting, or even have the audacity to roll their eyes, but you're in your own personal hell.

Welcome back, my rookie hackers! Many newbie hackers focus upon the technical aspects of hacking and fail to give enough attention to social engineering. In fact, I would say that technical hacks should ONLY be attempted if social engineering attacks fail. Why bother spending hours or days trying to hack a password if someone will simply give it to you?

Welcome back, my fledgling hackers! One of the first issues any hacker has to address is reconnaissance. Before we even begin to hack, we need to know quite a bit about the target systems. We should know their IP address, what ports are open, what services are running, and what operating system the target is using. Only after gathering this information can we begin to plan our attack. Most hackers spend far more time doing reconnaissance than exploiting.

Welcome back, my fledgling hackers! If you're like most aspiring hackers, at one time or another you've probably spent too much time playing Call of Duty and not enough time preparing for your final exams.

In my first tutorial on Linux basics, I discussed the importance of hackers using Linux and the structure of the directory system. We also looked briefly at the cd command. In this second Linux guide, I'll spend a bit more time with changing directories, listing directories, creating files and directories, and finally, getting help. Let's open up BackTrack and getting started learning more Linux for the aspiring hacker.

Welcome back, my fledgling hackers! In one of my recent articles, I showed you how to install BackTrack as a dual boot system on a Windows computer. In this tutorial, I will walk you through BackTrack, giving you a tour of the most salient features for the hacker-to-be.

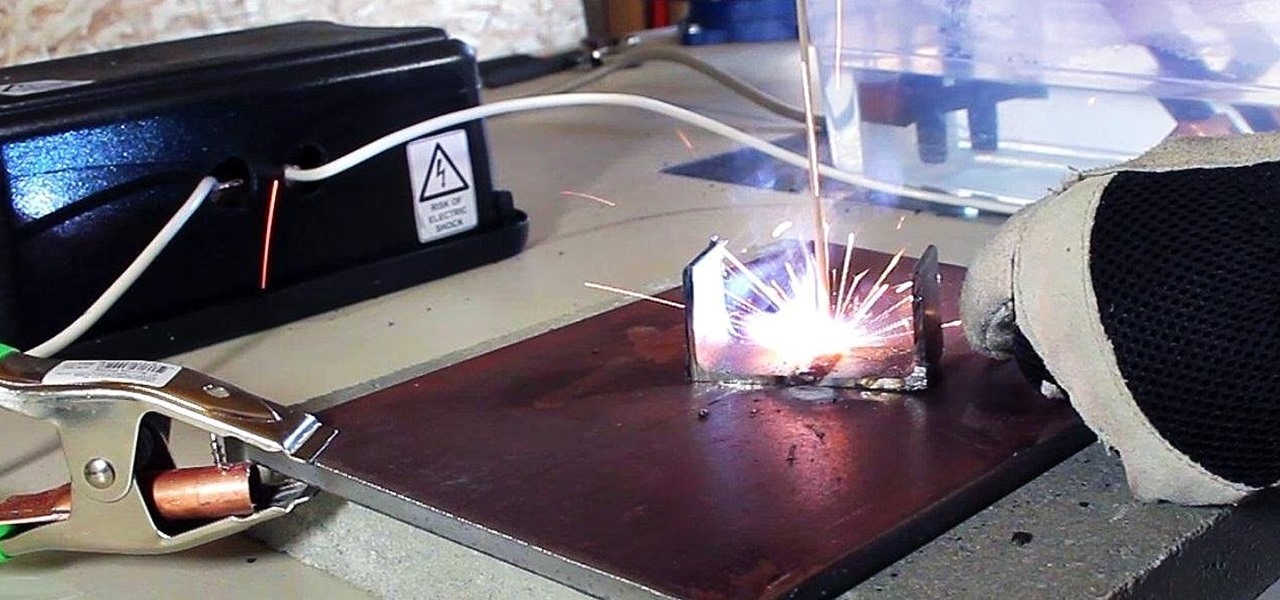
In a previous article, I demonstrated an Arc Welder made using parts from old microwave ovens. Video: .

With this article, I'll be continuing the series I started with my recent plague doctor article. That is, examining tropes that may at first appear to not fit into Steampunk.

First of all, I would like you all to meet my good friend Iggy. There he is, in all his scaly reptilian glory. As you can see, he spends a lot more time on top of his cage than inside of it. You see, Iggy here doesn't deal well AT ALL with confinement. I don't know if it's possible for a lizard to be claustrophobic, but if it is possible, then Iggy definitely is. When his previous owner gave him to me, I tried to keep him in the cage, but I quickly realized that it was a bad idea. When confin...

One of the most frustrating things on the Internet are sites that make you register just to view content. I'm not talking about paywalls—I mean the sites that make you give them personal information to look at free articles or forum threads. Most people are uncomfortable with this because a lot of these sites either spam you themselves, or sell your information to someone else who will.

While there are countless ways to welcome in the new year, many of them involve imbibing copious amounts of delightfully spirited libations. If you're anything like me, I know you're fearing the monster hangover on New Year's Day.

The creation of private browsing was brought upon by the backlash against ad tracking and other ways that sites and agencies take away users' privacy online. People were tired of getting spammed with ads for Vitamin C pills simply because they visited WebMD. Private browsing is now built into all of the major browsers and is used frequently. While private browsing is more infamously known as the "Porn Portal," and does prove to be a great way of keeping racy content out of the sight of others...

People take their Black Friday shopping seriously. Some of them are even willing to fight over it. Every year the stories get crazier and crazier, and someone always gets hurt (or even killed).

If you're dressing up as someone iconic for Halloween, having the right voice can make or break your costume. Think about it—having a Darth Vader lookalike walk up to you and start talking like Alvin the Chipmunk would probably ruin the effect (and possibly be a little creepy).

When browsing the web, I enjoy my privacy. It's reassuring that I can peruse the internet without the worry of having my activity tracked back to me, allowing me to leave fun, anonymous comments when I get the urge to troll.

Stand out from the high street fashion clones with stuff you’ve fashioned yourself. It’s easy to take old pieces of electronic junk and transform them into all sorts of fun ‘n’ funky geeky accessories. Like a totally useful tote bag, a what-on-earth-is-that wallet and a bedazzling belt. It’s terribly geeky but chicy too. Here’s how…

A few days ago, Russian hacker Alexy Borodin found a way to get free in-app purchases on an iPhone or iPad. In-app purchases include things like items and power-ups for iOS games, as well as subscriptions and "premium" memberships for certain apps.

It's already Halloween and the night is fast approaching. You swore to yourself last year that you wouldn't wait until the last minute again for a Halloween costume, yet here you are on Samhain without a costume… again. All of the costume shops are sure to be crammed with last-minute shoppers, and you don't feel like spending a lot of dough anyway, so what are your options?

A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.

Today, sailing is usually done for leisure or pleasure rather than traveling or moving cargo. While shipping is still the most viable way of moving goods overseas, with the advent of the airplane, sailing has transformed from a necessity to a sport. Some people put their sailing skills to the test in sailboat races; some just find it exciting to be riding the ocean waves on a non-motored vehicle, using techniques which sailors have employed for thousands of years.

Ultimately a doctor’s note is the only necessary proof needed to show your boss that you really did go to the doctor’s but if you feel like making an airtight case you can always take a few extra steps to make sure there’s not a shadow of a doubt.

Ever wondered what it was like to have tons of money in Happy Aquarium? Don't let others make fun or your friendly fishing skills, show them who's fish-master. Hack your doe with Cheat Engine for bragging rights.

Hacking Happy Aquarium is easy. As long as you have Cheat Engine. Anybody can do it. Not everybody knows how to hack though. Learn how to cheat right here.

In this free video series, our expert will offer up tips and advice on how to pick an RV or Pop-Up Camper. If you have been thinking of buying a recreational vehicle, let our expert explain the finer points of this sizable purchase. You will learn about pop-up campers, towable campers, and motor homes, including how to decide what you need, how much you can afford to spend, and what you should learn from a walk through. Get the inside tips on buying a camper or RV from an expert, and hit the ...

In this video dancing lesson, our expert dance instructors will demonstrate how to do the West Coast Swing Dance, which is a variation of the traditional Lindy Hop swing dance. They will give a step-by-step lesson on the footwork, passes and body movements for West Coast Swing Dancing, as well as a demonstration of the dance being performed. Looking to get started on the swing dance scene, but don't want to spend the money on professional lessons? This is the video dance lesson for you, so gr...

There’s a good chance that you’ll be alone in life one day, and no... I’m not talking about a couch-bound, dateless loser with a pocket pussy and a bag of potato chips. I’m talking about alone. In the wilderness. Hungry. Cold. Lost. You can’t stay in one place too long, so it would be nice to have something to carry your belongings in. Maybe it’s post-apocalyptic land where you’re the sole survivor, and all the backpacks and rucksacks in the world are but mere ash. Either way, knowing this si...

In just a few weeks, on May 29, the annual AWE (Augmented World Expo) conference will take place once again in Silicon Valley (Santa Clara, California, to be exact).

Silence spreads over these mountains like nothing I've ever felt. If I didn't have Moby blasting in my earphones, there'd probably be no other sounds around. Well, except for someone, Phil probably, murmuring in a nearby tent just low enough to make his words indiscernible.

For the uninitiated, it can be difficult to buy that special hacker in your life a perfect holiday gift. That's why we've taken out the guesswork and curated a list of the top 20 most popular items our readers are buying. Whether you're buying a gift for a friend or have been dying to share this list with someone shopping for you, we've got you covered with our 2018 selection of hacker holiday gifts.

Defcon is the largest hacker conference with something for everyone, whether it be the talks, parties, villages, or any of the hundreds of events. In this guide, we'll take a holistic view at everything that goes into attending the con for the first time, from securing your electronics and making the most of your time to the logistics of getting there and finding the right place to stay.

So, your grandmother finally wants to ditch her flip phone for a shiny new smartphone? Congratulations. But helping her get used to her new device, even when it's an iPhone, is no small task. Grandma mastered checking her email in late-2012 and just recently learned there's a thing called "Facebook." But we love grandma, and thanks to this guide, we can definitely make this happen for her.