Well before Magisk was in our lives, the Xposed framework was where all the mods and magic happened. Magisk was built on a similar concept with the ability to customize your system via modules. We can thank Xposed for where we are today in terms of root-related mods, but it's not done just yet — it's still very much alive and kicking after all these years.

There's always an iPhone in our list of top phones for privacy and security, due in large part to advanced security measures like Face ID, consistent iOS updates, and easy ways to prevent unwanted access and excessive data sharing. However, some of those options actually do the opposite and hinder security. It all depends on how you use your iPhone, but you should at least know everything available.

Defcon is the largest hacker conference with something for everyone, whether it be the talks, parties, villages, or any of the hundreds of events. In this guide, we'll take a holistic view at everything that goes into attending the con for the first time, from securing your electronics and making the most of your time to the logistics of getting there and finding the right place to stay.
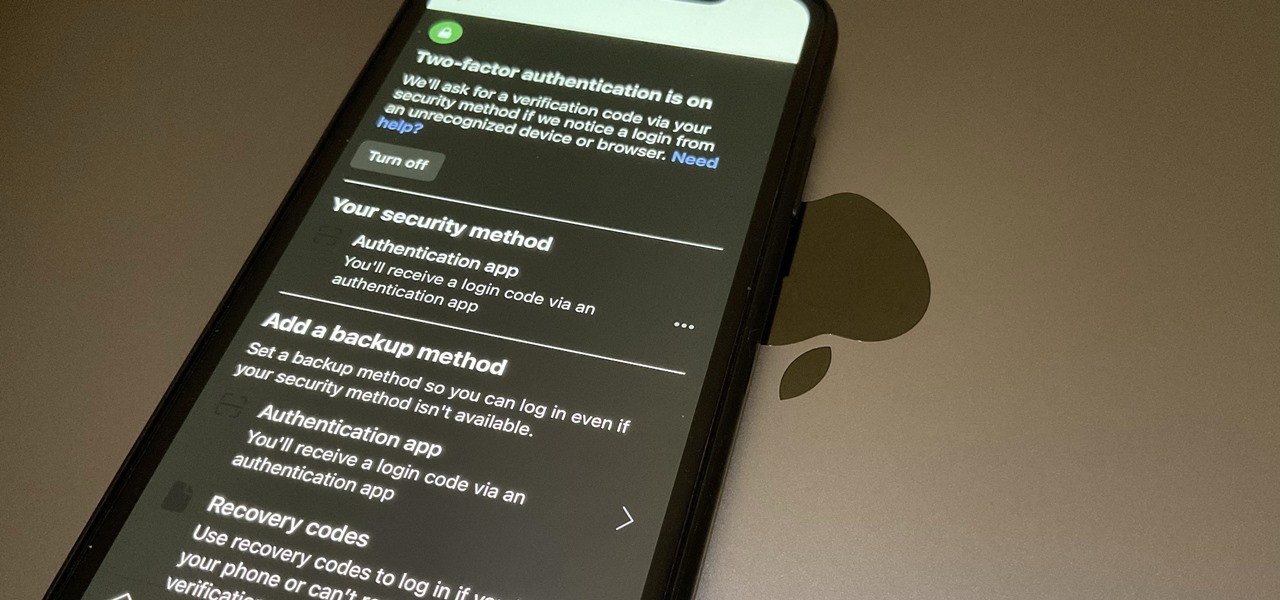
Most websites and apps support two-factor authentication (2FA), which adds an extra layer of security to your accounts by requesting another form of identification beyond username and password. The second factor can be a recovery code, physical security key, or one-time password (OTP) that only you can access, even if someone else has your password. This process is easier than ever thanks to iOS 15.

Identifying security software installed on a MacBook or other Apple computer is important to hackers and penetration testers needing to compromise a device on the network. With man-in-the-middle attacks, packets leaving the Mac will tell us a lot about what kind of antivirus and firewall software is installed.

There's a lot of misinformation about VPN services, and it stems from the fact that not all of them are created equal. Some focus on privacy, others on security, and a few VPNs are seemingly even purpose-built for the polar opposite: data collection. We made this guide to help clear the air on some of these issues while objectively ranking the best of the best.

Apple's bringing big changes to your iPhone's lock screen in iOS 16, and one of those changes lets you pick an always-updating wallpaper for your local weather conditions. If you don't want to wait until the fall for the stable iOS 16 version and don't want to install any iOS 16 betas, you can still get an always-updating weather wallpaper for your lock screen on iOS 15.

After nearly two months of beta testing, Apple is finally pushing the iOS 15.6 software update to all iPhone users. While it's not as feature-rich as the iOS 15.5 or iOS 15.4 that came before it, there are still a few things you'll want to know about it.

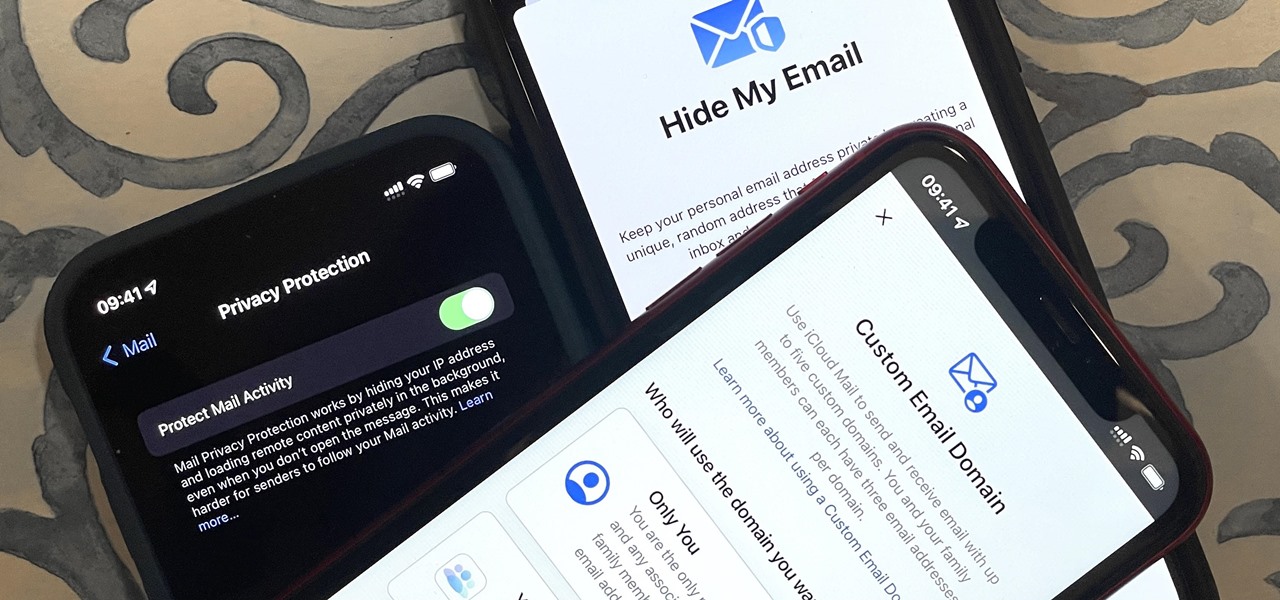
Privacy is a growing concern in the tech industry, but Apple has fallen behind many of its peers when it comes to email security. Fortunately, iOS 15 changes that. Your email address is the key to a vast amount of personal information, not to mention a stepping stone into your other online accounts, so it's great to see new features for iPhones that protect email accounts and their contents.

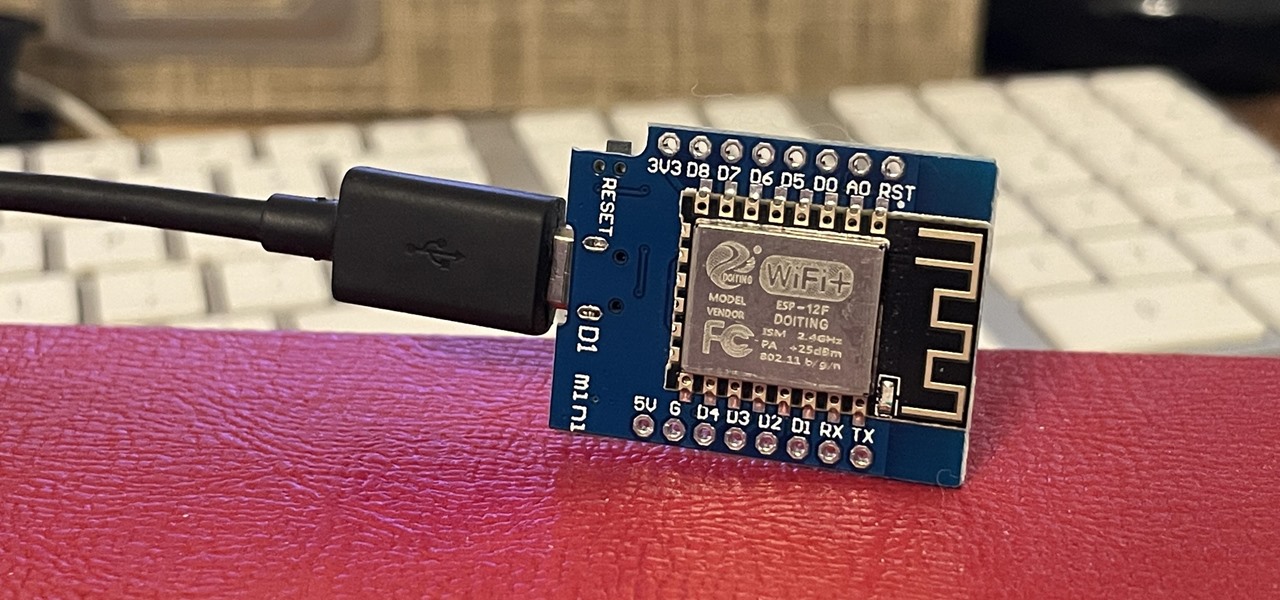
If you've wanted to get into Wi-Fi hacking, you might have noticed that it can be pretty challenging to find a safe and legal target to hack. But you can easily create your own test network using a single ESP8266-based microcontroller like the D1 Mini.

If you've spotted an unintended Ethernet connection and wondered what you could do with all of the information coursing through those wires, there's an easy way to hack into it and find out.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

Overall, iOS is more impressive than ever with its stability enhancements, security tools, suite of apps and services, and intuitive user interface. With each passing update, things just get better and better for iPhone users. But don't think for a second that this is all because of Apple's genius — many of these features were at least partly inspired by tweaks made by the jailbreak community.

Rooting. As an Android user, I'm sure you've heard the word once or twice. According to Kaspersky, 7.6% of all Android users root — but for the 92.4% who don't, we wanted to talk to you.

Besside-ng is the hidden gem of the Aircrack-ng suite of Wi-Fi hacking tools. When run with a wireless network adapter capable of packet injection, Besside-ng can harvest WPA handshakes from any network with an active user — and crack WEP passwords outright. Unlike many tools, it requires no special dependencies and can be run via SSH, making it easy to deploy remotely.

Apple's iOS 16.3 update for iPhone had impressive new features, but iOS 16.4 might impress you even more.

Apple's latest big software update includes an entirely new Apple app, a controversial change in the TV app, better Siri control, an improved Shortcuts app, interesting Safari upgrades, Apple Music Sing, and more. Keep reading to see what iOS 16.2 has to offer your iPhone.

Android 11 is here. Prior to Google dropping the naming scheme, this would have been a dessert with an R name (maybe Rice Krispies Treat or Red Velvet Cake) — but nope, just plain ol' Android 11. And after months of betas and a global pandemic, it finally debuted a little over a year after Android 10.

via Phillip Bloom & Engadget & Variety When SNL DP Alex Buono saw Philip Bloom's Dublin's People short he was so impressed he decided to shoot the entire 35th Season Opening Sequence on the 7D.

In this video, you'll find instructions on how to use the Ettercap plug-in dns_spoof to set up DNS spoofing on a local area network. This Ettercap plug-in is ony one potential way to pull of DNS spoofing, and only works if the attacker is on the same subnet. To get started DNS spoofing with Ettercap, press play! Use DNS spoofing in Ettercap.

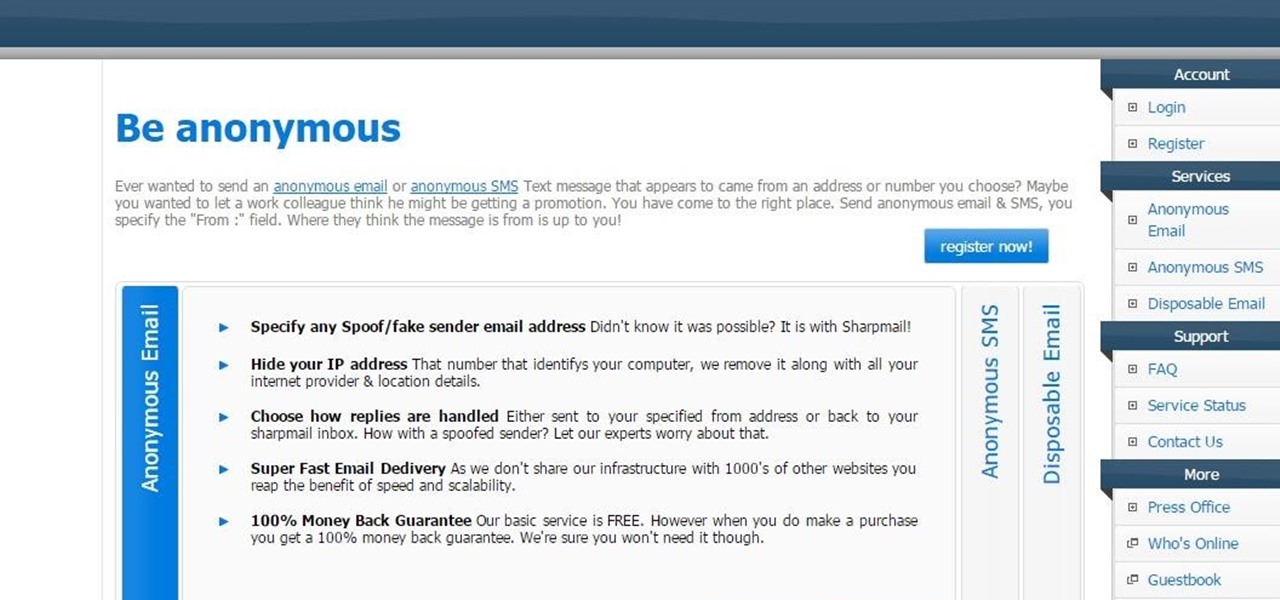
Welcome, The Geeks!! This is my first article on email spoofing and hope everyone likes it.

I shot this X-Men: First Class Spoof with the new Technicolor CineStyle picture profile (it was a 5d, as well). I had done some initial testing when the profile first came out, but never shot a real project on it. This X-Men short is my first real world experience with the profile.

Spoof of the Sherlock Holmes: A Game of Shadows movie poster just in time for Christmas!

WonderHowTo user lex lugo of Bootleg Entertainment posted this fun spoof on musical classic Westside Story to the Canon 7D World forum. The short starts off with some pretty (amazingly) goofy dance-offs; stay tuned 'til the end if you dig 2D violence.

So the singing is kind of lame, but we love the lyrics.

Most of the oddest games in the world are free web games. They may not always be well made, but low budgets (and consequently low risk) allow them to be as weird as they fancy. That's a big part of why they are so interesting. Prime examples such as Don't Take It Personally, Babe, It Just Ain't Your Story and Lesbian Spider Queens of Mars have graced these pages previously, and both are great games. But the quality of the games hasn't stopped mysterious Glorious Trainwrecks user snapman (else...

In this article, I'll show you how to easily "hack" Facebook, Twitter, YouTube, and any number of similar account types with an Android app called FaceNiff.

Have you ever noticed that whenever you setup your voicemail account after getting a new cell phone number, it asks you to create a security pin to access your voicemail from other phone lines?

For those that don't know, Pastafarianism is the understanding that the entire universe was created by a flying spaghetti monster. These people have made a statue as a shrine to worship. (he he) Originally a poke at organized religion, the Flying Spaghetti Monster has taken hold as a spoof belief structure in that it is no more or less feasible than any other monotheism. Think what you want, but the statue is great. They tour it all over a county.

I have had a lot of people ask me, "How does my neighbor keep getting into my wireless?!". Chances are, these people are all using WEP, a deprecated wireless encryption protocol. Either that, or you are using one weak WPA passphrase.

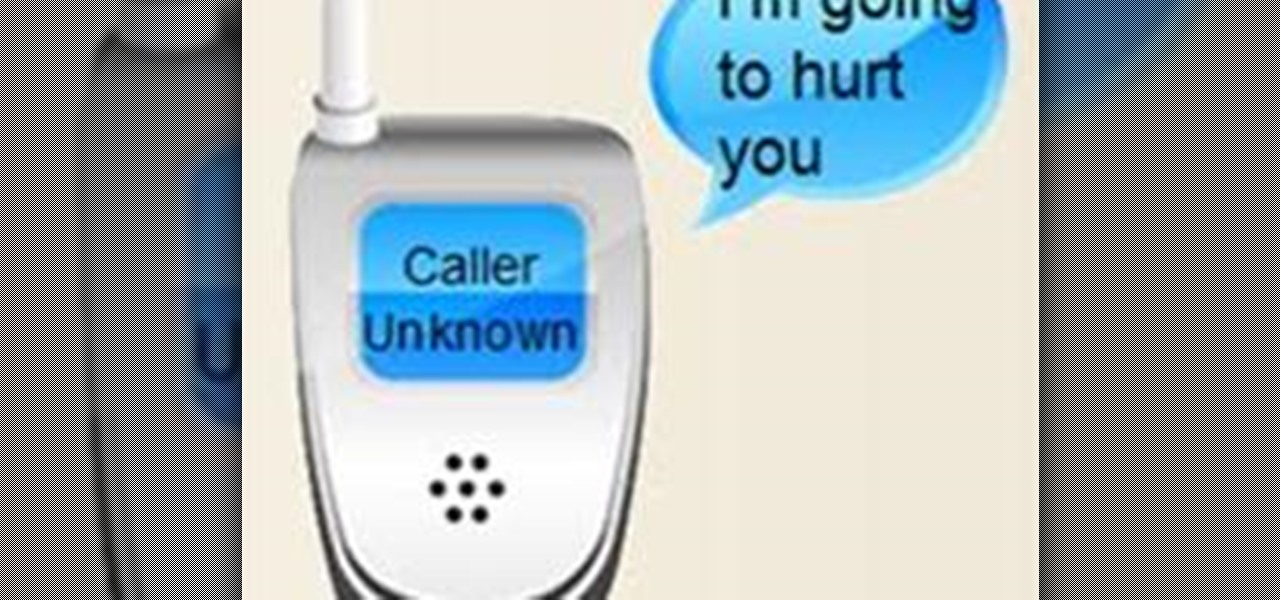
Prank Calls, Masked NumbersWho is calling your phone or your child's? Pranksters use a lot of tricks to make sure they can get on your nerves. Being able to trace prank calls is important because you're not going to learn much from your Caller ID, since most prank callers use an unlisted number - such as, a cell phone number. Many also use special code *67 to mask the number so your Caller ID will show "Blocked Number" or "Private Number". There are a lot of mild cases of so-called phone bull...

We're officially seeking Null Byters on a weekly basis who are willing to take the time to educate the community. Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (IF up to par, of course). There is no need to be intimidated if you fear you lack the writing skills. I will edit your drafts if necessary and get them looking top-notch! You can write tutorials on any skill level, and about anything you feel like sharing that...

Japanese game shows are legendary for being more extreme (and absurd) than their American counterparts. Chris Farley immortalized the concept in a classic SNL sketch, and MXC and Ninja Warrior have both achieved great success dubbed and subtitled on American television. A big part of their appeal is how demanding they are compared to U.S. game shows. Only a few people have actually won Ninja Warrior in its 23 seasons on the air, and MXC is a constant comedy of failure and pain.

Review: Get Him to the Greek So much puke

I shot this X-Men: First Class Spoof with the new Technicolor CineStyle picture profile (it was a 5d, as well). I had done some initial testing, when the profile first came out, but never shot a real project on it. This X-Men short is my first real world experience with the profile.

When your computer first connects to a nework, it sends out a request on the network to lease an IP from the router. The router then leases your computer an unused IP address, which is used as a unique routing address for sending traffic that is meant for you, to you. As everything tends to, this method has its flaws.

Alec Baldwin loves word games? Enough to get kicked off an airplane? Apparently. Yesterday, while sitting in first class on his American Airlines flight back to New York from LAX, a flight attendant "reamed" him off the plane for playing the popular Scrabble clone, Words with Friends, and not turning off his phone and obeying signs requiring seat beats. Apparently, the aircraft was still at the gate and unmoving. His tweet:

Our mission for this week's Community Byte was to create a Python program to crack web-based passwords, like the ones you would see on an email or router login. I wanted it to be universal in the sense that it could be easily modified and adapted to another website just by changing a few variables. That was a success! Even though people weren't on time to the coding session, everything went well.

Often times when staying at a hotel or anywhere for that matter, you'll whip out your laptop and check the local area for Wi-Fi. I know you've all been in my shoes when you find an unsecured network that appears to be public Wi-Fi belonging to the hotel or airport, and you connect to it. You connect fast and perfectly, only to find that when you open your browser, it says you don't have an account, and are filtered from accessing the web. This is because the owners of the network want to keep...

After a decent amount of downtime, one of the best indie game sites on the internet has finally relaunched! PixelProspector is a one-man gaming blog and YouTube channel devoted to the weird and beautiful world of indie games. In the first half of 2010, it received a huge boost in popularity from its video 235 Free Indie Games in 10 Minutes, a hypnotic montage of the best indie games the site had to offer at that point. And to celebrate the relaunch of the blog, which now has an improved desig...