All across the web, countless users and critics have already decided that Periscope, the Twitter-owned live video-streaming app, has killed (or is on the verge of killing) Meerkat off for good.

Lending someone your phone to make a call is always an awkward situation, as you closely monitor them to make sure they stick to a phone call rather than wandering off into private applications like your photo or messaging apps. You don't necessarily want to eavesdrop on their conversation, but trusting people with your phone is difficult, especially if you have some risqué or embarrassing pictures stored on it.

If you live in a small town, weather apps can be unreliable. Before moving to Los Angeles, I always had to add or subtract five degrees or so from what my weather app said because I couldn't trust it. With the help of BloomSky, you will be able to get an accurate weather reading directly from your backyard.

If new leaked images are to be trusted, an iPhone with a display around 5 inches will be released later this year. From Italian site Macitynet, images show a device that's stated to be the new iPhone 6 side-by-side with the new Samsung Galaxy S5. A couple of weeks ago, I showed you leaked internal emails and memos that suggested Apple was concerned with not only Samsung's marketing strategy, but about the industry trend towards larger devices.

One of many cool features in iOS is the ability to listen to your Music app and have the player options, as well as album art, available on your lock screen. While that's super convenient, it's not all that easy on the eyes. The player is placed over a blurred version of whatever your lock screen wallpaper is.

Katie wanted to make a difference in the world, and thanks to the ACUVUE 1-DAY Contest, and Disney Channel star and singer, Bridgit Mendler, her dream became a reality. Watch ACUVUE's video below and check out our tips on how you too can begin the transformation and motivate others to make a difference.

I learned the hard way that boxed dyes just don't work well for me. A few months ago, I tried one that had a pretty name like "soft violet black." Sounds nice, right? What I ended up with was brown hair and hot pink roots. Trust me, it wasn't cute.

Ever wonder what your brain looks like while you're singing? No? Neither had I, but as this music video for the song "Better Man Than He" by SiVU (aka James Page) will show you, the answer is "pretty cool."

Convenience is a big deal these days. You can buy single-serving or single-use sizes of just about anything, from fruits and vegetables to sanitizing wipes, and, apparently, even bananas. Uhh, it already has a wrapper...

One of the roles our government has taken on is to provide us with information to be used in making decisions.

Have a super secret spy communication you'd like to send out, but don't have the funds to hire your own trusted operatives to deliver the message? Then stick to what you're used to—email it. SafeGmail is a browser extension that allows you to send encrypted emails right through your regular Gmail account. While this may seem a bit unnecessary for most messages, encrypting your email can definitely be useful.

It seems like every other day there's a new security threat or data leak in the news. Whether it's your credit card PIN or your smartphone's apps leaking your email address, no one wants their personal information out there, especially passwords. And if you use the same email address and/or password for more than one site, the effects of someone getting hold of your credentials can be catastrophic.

Hate answering the door, but don't trust your friends with a set of keys? This RFID front door lock made by Steve Pomeroy will solve all your party-hosting problems. It reads the RFID tags in his friends' public transit cards and decides who's allowed in based on "groups" that Steve defines. And I have to say, it's also rather stylish. It's controlled by an Arduino serial console and a custom Android app to add and remove cards. The reader can store 50 or 100 tags at a time and allows 7 diffe...

Security researcher and iPhone hacker pod2g has brought attention to a flaw in Apple's iOS that allows the user to change the reply address of an SMS message. This bug has been a part of the iPhone's SMS since the first iPhone in 2007, but Apple has yet to address it. Basically, there's a section in the text payload called User Data Heading (UDH) that controls some advanced features, one of which is the reply address. By changing the reply address of a text message, you can make someone send ...

This series of videos focuses on a typical UV workflow in Houdini 9. Learn how to create projections, edit UVs with a variety of tools, save out UV maps, and apply textures. Please download the project files below to follow along with these Houdini 9 texturing lessons.

Here's a low-key way to take advantage of someone's trust. Gain access to a friend or frenemy's iPhone and add curse words as separate new contacts to their contacts page. Sit back and wait for your friend to text someone. Enjoy.

Crayola Washable Watercolors offer the best and brightest watercolor painting experience, without the mess! They come in a variety of vibrant colors that blend smoothly for more color-mixing possibilities. Washability you can trust™! This video has great ideas for projects to do with your kids!

With the prestige appeal of its original programming and relatively low subscription price, Apple TV+ is one of the more appealing streaming options out there — and you don't need an Apple device to subscribe and watch movies, TV shows, sports, and other Apple TV+ content.

Apple just rolled out the of iOS 14.5 to developers and beta testers, and one of the headlining features is the ability to keep your iPhone unlocked when your Apple Watch is nearby. As these things tend to go, Android has actually had this same feature for years, though it isn't quite as polished.

There have been concerns with how much personal information Google tracks and all the things they know about us. Of course, that's what makes Google services so useful, they can use that information to cater to each of us individually. So yes, it serves a purpose, but it's not great for personal data security.

When your iPhone goes missing, it's serious business. Depending on your usage, your whole life might be connected to your iPhone, not the least of which includes debit cards, credit cards, and Apple Pay Cash stored in Apple Pay. While it's nearly impossible for someone to use your money with Apple Pay, it's still a good idea to disable it until you find your iPhone, just in case.

Mystery is a tricky thing. Used correctly, it can give onlookers the impression that wondrous and perhaps valuable things are afoot. However, once the veil of suspension of disbelief is removed in any significant way, that same mystery can quickly turn into not just skepticism, but outright anger at what may have seemed like an attempt to dupe trusting onlookers.

We need to take our privacy and security much more seriously. Whether it's malware-infected apps or the mishandling of our data by companies like Facebook, there are threats all around us in this digital world. Fortunately, some smartphones are simply designed to protect us better.

Keystroke injection attacks are popular because they exploit the trust computers have in human interface devices (HIDs). One of the most popular and easily accessible keystroke injection tools is the USB Rubber Ducky from Hack5, which has a huge range of uses beyond simple HID attacks. The USB Rubber Ducky can be used to attack any unlocked computer in seconds or to automate processes and save time.

Kodi, formerly known as XBMC, is one of the most versatile media players available. With it, you can play virtually any internet and media file in a large variety of formats, and it can be used on practically every single operating system out there, including iOS 10. Kodi, an open-source software, was originally designed to connect to your TV so you could control your media from up to ten feet away, and the core functionality still shines today. All of this is what makes Kodi so popular today...

An average user's smartphone tinkering doesn't go much further than taking their phones out of the box, signing into their account, and installing apps. But some of us want more functionality and customizability than the basic experience provided by Android and iOS.

Of course, if it were a perfect form of currency, it would have become the standard by now. But it hasn't. Wanna know why? The story begins with the advent of agriculture, when humans had settled down under groups as units called villages, over 10,000 years ago.

INTRODUCTION Hello dear null_byters here we go again with our third part of this serie.

Welcome back, my neophyte hackers! There are innumerable ways to hack a system. We must not overlook any of the possibilities if we want to "own" the system. As systems become more and more secure, we need to be vigilant in our search for weaknesses. In this hack, we'll look at abusing the trust that a user innately has for software updates to install our own listener/rootkit on their system.

Step1. Determine the type of job you want. Make sure that you have a detailed and complete profile on ‘linkedin’. You must also have a number of connections. Then decide which job you are looking for and the typical functions and titles. Also choose which type of industry you would like to work in and also choose what locations. You also need to write down specific names of organizations that you want to work for and who are they.

Having a boring Facebook profile is lame! Impress your friends and flaunt your social networking skills by sprucing up your Facebook profile.

Learn how to read a person just by looking at their hand using the ancient art of palmistry. Step 1

Learn how to spot a dishonest contractor for home repair. It’s no accident contractors have such a bad reputation – they get more fraud complaints than any other workers! Here’s how to find a reputable one – and skip the scammers.

Have you ever thought of building your own social networking site? Before you get to making websites like Facebook, you need to start off smaller, and this 29-part video series is where to begin with developing a social networking community website . Before you start with these lessons though, make sure you have all the following:

It's nearly impossible not to be at least somewhat familiar with Microsoft Excel. While it's needed for many office jobs and data analysis fields, hackers could also benefit from improving their spreadsheet skills. Many white hats already know some of the essential Excel hacks, such as cracking password-protected spreadsheets, but there's so much more to know from an attack standpoint.

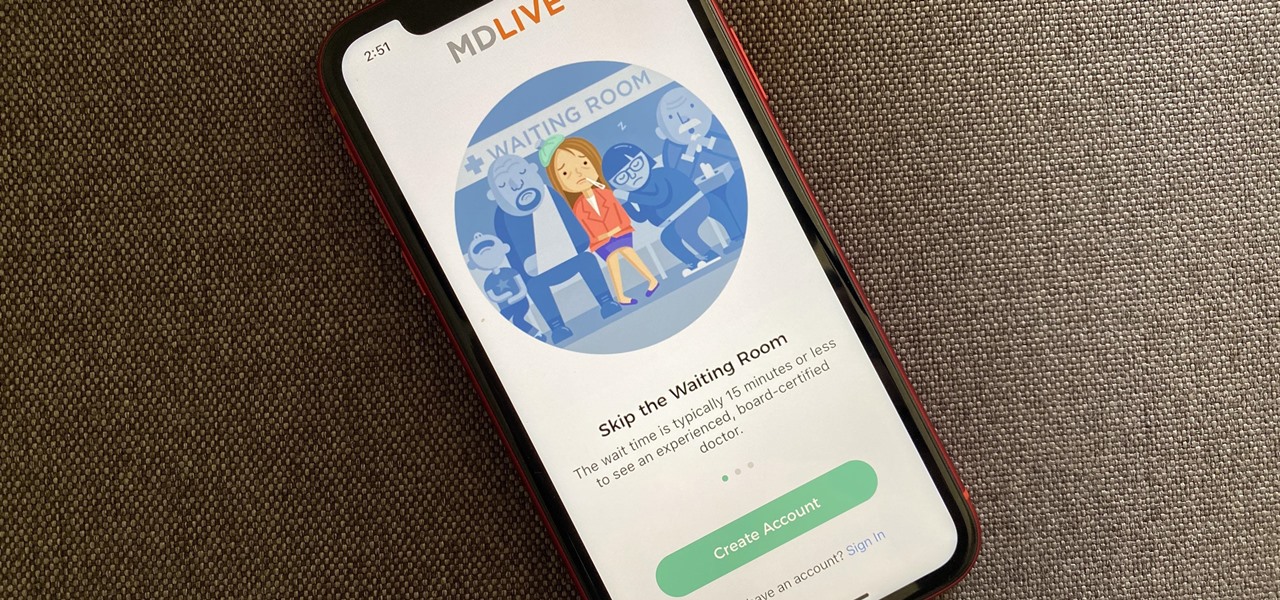
If there's any silver lining to being stuck at home right now, it's the fact that many of us have way more time to take care of those things that have been sitting on our back burner for ages, like beefing up our resumes.

The World Health Organization has declared the new coronavirus a pandemic, and the Centers for Disease Control and Prevention recommends video visits with a healthcare professional to reduce the risk of being exposed to the coronavirus that causes COVID-19. If you are experiencing mild flu-like symptoms, virtual doctor visits may also prevent you from endangering others.

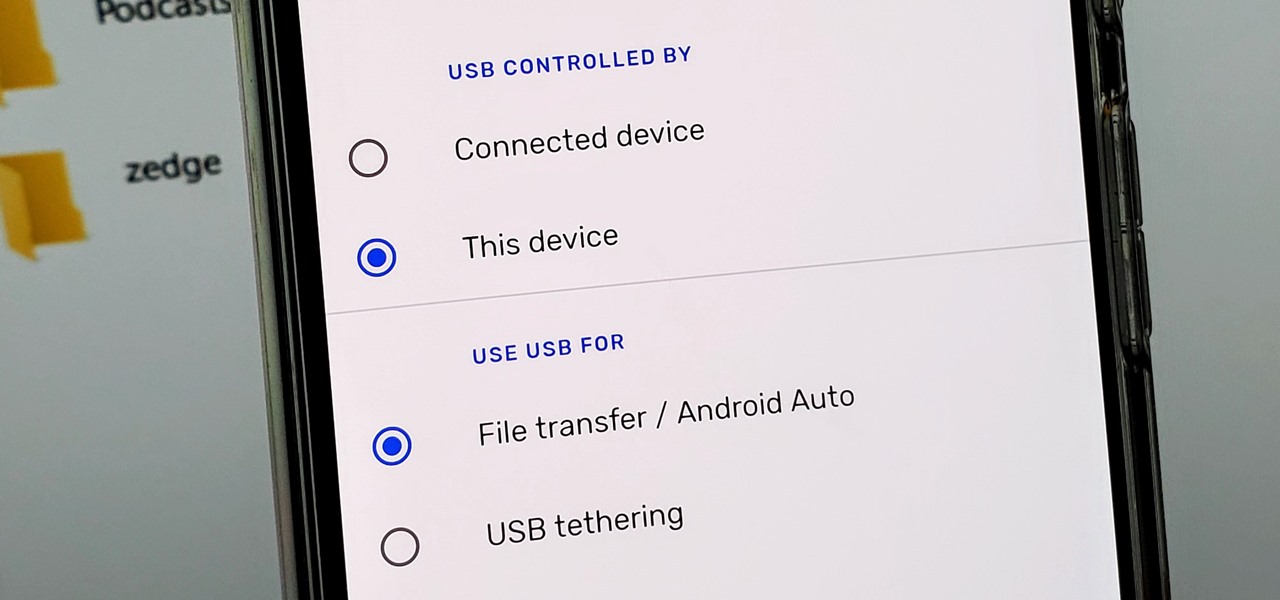
Back in the earlier days of Android, you were able to connect your phone to a computer, and it would mount automatically. This meant once the USB connection was made, your internal storage would pop up on the computer and you could go about your business. But recent versions of Android changed that to help increase security.

One of Android's biggest strengths relative to iOS is how simple it is to sideload apps that aren't on the official app store. Rather than having to sign IPA files or tell your phone you trust a developer every two weeks, you can just enable a setting and be done with it.

Decades ago, Japan rocked the automobile industry with its revolutionary manufacturing and car quality, but today that title seems to be moving over to Elon Musk's electric car company Tesla. Nevertheless, Japan isn't done innovating mass-produced hardware.