What’s better in the summer than playing around in the water? Lounging in the pool, water balloon fights, and playing in the sprinklers helps us forget how much it sucks to be outside in 100+ degree weather.

This tutorial illustrates how a wireless pinhole spy video camera can jam wireless internet or WiFi signals.

Watch this how to video as Jennifer Thoden takes you through every step of installing a bead chain system for your Roman shades or balloon shades. Gather your supplies and learn how to assemble the clutch and thread the unit. Keep your windows from looking bare with a Roman shade bead chain system.

Don't buy those $100+ laser pointers. Watch this video, and for under $50 you can make your own that is capable of burning, popping balloons, and cutting things!

When you look at the top corner of your phone, what do you see? Upon upgrading to Android 11 or iOS 14, you'll see either "5G," "5G+," or "5G E" if you're connected to the right network. But what exactly do these symbols mean? They indicate not only if you're using 5G, but also what type you're connected to.

While Apple's AR wearables development continues clandestinely, its mobile ecosystem is laying the foundation for the software side of its smartglasses, with Apple Arcade serving as the latest example.

If you're concerned about someone accessing your OneDrive files, you may want to upgrade your protection by enabling fingerprint or Face ID unlocking. Your sensitive information deserves to be protected, and now you can do so easily. Worry no longer — if you need to let someone else use your phone, with a password-protected OneDrive, sneaky file grabbers will be out of luck.

When you visit a website in Safari, it's most likely keeping tabs on your browsing activity. It could be keeping track directly, or its third-party content providers and advertisers can be spying on you. All three could happen simultaneously. This enables them to serve you content that's tailor-made for you, but it can also feel like an invasion of privacy.

While Google has a water-resistant phone in the Pixel 2, its CES booth was anything but. According to Tech Crunch, Google had to shut down its two-level outdoor booth once it began to rain at the Las Vegas trade show. Even though Las Vegas is the driest city in the country, Mother Nature always has her idea of fun.

Surveillance is always a useful tool in a hacker's arsenal, whether deployed offensively or defensively. Watching targets yourself isn't always practical, and traditional surveillance camera systems can be costly, lacking in capabilities, or both. Today, we will use motionEyeOS running on a Raspberry Pi Zero to create a small, concealable Wi-Fi connected spy camera that is both affordable and easily concealed.

Listen up, fool! You can now get a (loud) nudge in the right direction by Mr. T, thanks to Waze. The navigation app has incorporated a few well-known voices over the past few years, but none have had us more excited than the addition of this beloved fixture of the 1980s. Waze made the announcement that Mr. T's voice would be joining the likes of Arnold Schwarzenegger and Morgan Freeman via their company blog. That's the great news. The bad news is that Mr. T is only available for Waze users i...

Bose Corp is the latest company trying to make another dollar off of you without your permission. Bose Connect, the companion app to the swag $350 Bose headphones, is not the Jane to your Jack that maybe we all hoped it to be.

The Drug Enforcement Agency (DEA) has been purchasing spyware from the Milan-based Hacking Team and its US subsidiary Cicom USA since 2012. Public records reveal invoices between Cicom USA and the DEA that have ranged between $22,000 to $575,000 from 2012 to 2015.

Just like in the Spy Kids 3D movie, US soldiers may soon upgrade their mission planning from 2D to 3D. Welcome to the wonderful world of augmented reality, US Army.

Baidu Inc, the "Chinese Google" search engine and technology company, which has been actively pursuing self-driving cars, reported that a gang of hackers recently attempted to steal its driverless car technology.

Google's new Project Fi cellular carrier has been making waves across the mobile industry, so we decided to put it to the test against T-Mobile, one of the more established networks. For the actual testing, we slapped a SIM card from each carrier into two identical Pixel XL phones, which offer full compatibility with both networks.

The new lock screen in iOS 10 is a lot different than previous versions, but one thing that stuck around is the quick access camera shortcut. The only real difference aside from aesthetics is that now you don't have to swipe up from the camera icon. Instead, you can simply swipe to the left from right side to quickly snap a picture.

It's a given that if you're driving, you or someone you know has Waze as a go-to on their smartphone. The Google-owned crowdsourced navigation app is one of the best for avoiding traffic, roadblocks, and even cops.

The art of taking secret photos is one that requires keen awareness and skill. Not only do you need to ensure that your subject remains oblivious, but you also need to make sure that no one near you notices what you're attempting to do. It's great when you buddy is acting a fool, but sucks when they stop their shenanigans when they notice you pulling out your camera phone in an effort to evade your picture.

These days, there is no shortage of ways to exchange files to and from friends and family: text messages, email, Bluetooth transfer, and cloud services are just a tiny sliver of what you can use to share music, photos, videos, and more.

As many of you know, I firmly believe that hacking is THE skill of the future. Although the term "hacking" often conjures up the image of a pimple-faced script kiddie in their mother's basement transfixed by a computer screen, the modern image of the hacker in 2015 is that of a professional in a modern, well-lit office, hacking and attempting to development exploits for national security purposes. As the world becomes more and more digitally-dependent and controlled, those that can find their...

As the developer behind the most popular root methods for hundreds of Android devices, Chainfire knows the ins and outs of Android root procedures. But this doesn't mean he's infallible—occasionally, some of his root utilities can cause minor bugs.

Thanks to a couple of photoshopped images that made rounds across Twitter last year, iPhone users were duped into thinking that iOS 8 included a security feature that would lock individual apps. Of course, none of it ended up being true, but we covered other features and apps that could accomplish roughly the same thing.

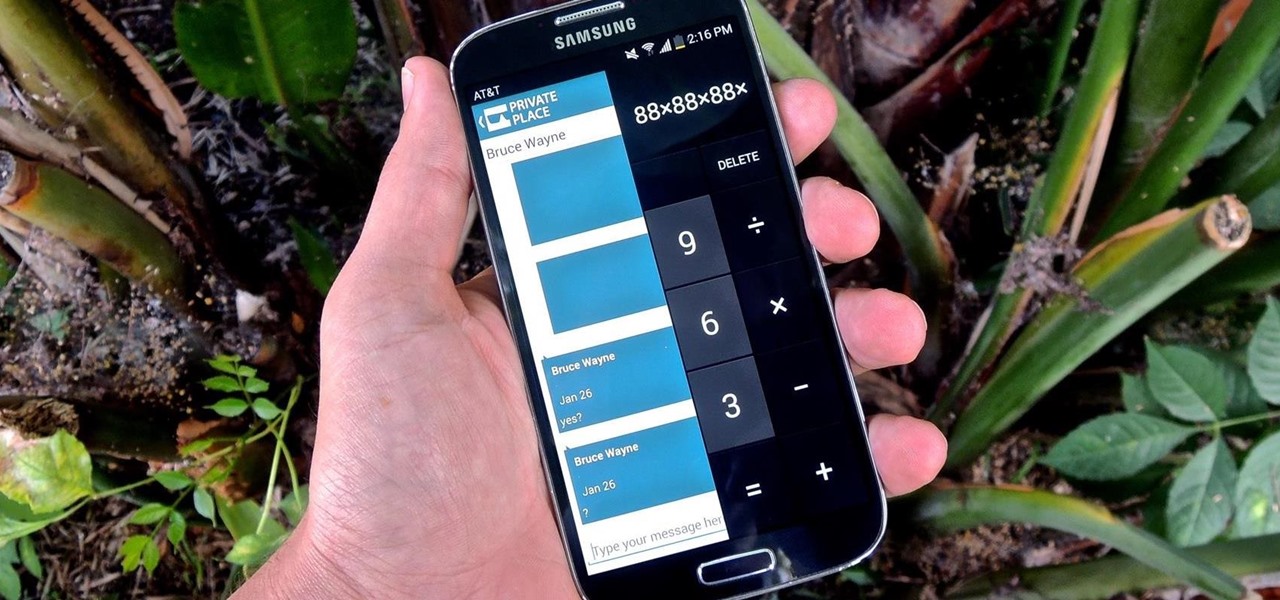
Whether you're a secret spy or just a regular person with a few secrets, you may want to keep certain information on your smartphone private, and it's totally possible on Android to do so.

In previous posts here, I have pointed out that hackers are in high demand around the world and in nearly every industry. Every military and espionage unit of every country is trying to hire high-quality, experienced hackers as fast as they can to hack their adversaries' computer systems in order to gain a strategic advantage and to spy.

Ever use an open hotspot on your Note 3, only to find out that it's severely restricted to what sites you can access? While getting online with free Wi-Fi is great for those who have a limited data plan, when that one site you absolutely need to visit is blocked, you're left frustrated and sent back into the Wi-Fi menu for another access point.

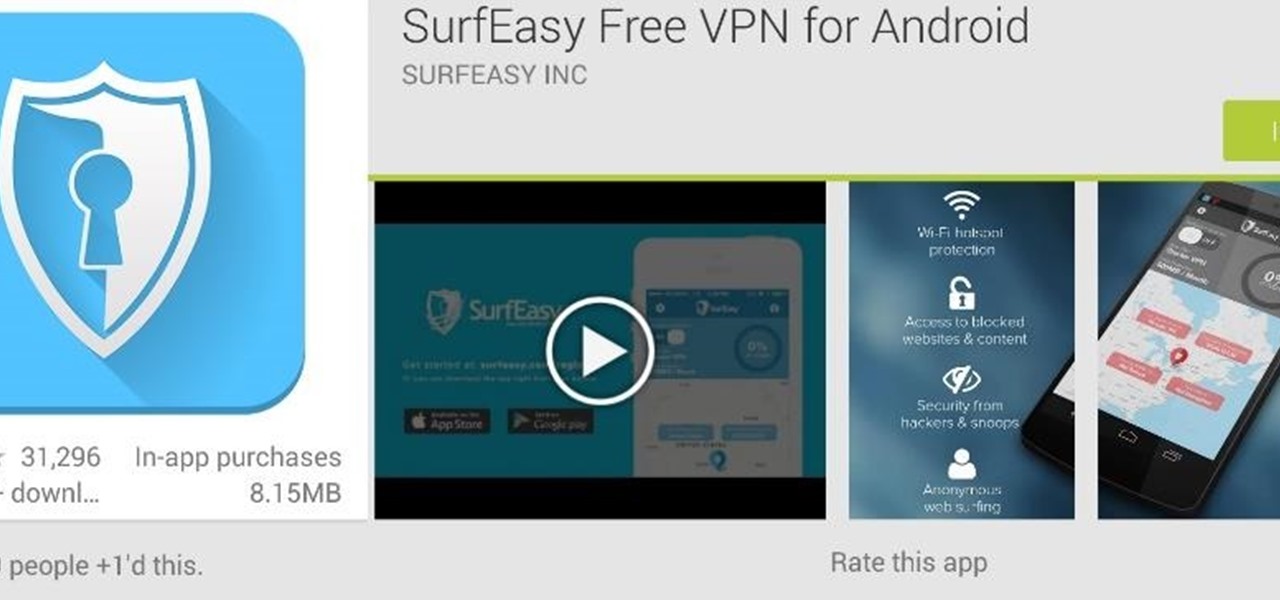
When browsing the web, you may not be quite as anonymous as you think, especially if you are using public WiFi. The easiest way to stay as anonymous and safe as you are going to get, is to use a VPN (there are a number of great free ones). In this tutorial, we will show you how to set up a VPN on Android, and how this protects you.

In the wake of the NSA controversy and its subsequent fallout, many dashed towards finding means of secure communication—using private internet browsing and encrypted text messaging applications—out of fear of being spied on.

The NSA's massive internet spying efforts will continue. In President Obama's latest press conference, he went public to (in so many words) say that the NSA's spying efforts will continue uninterrupted. This, coming just weeks after the Amash Amendment which would have defunded the program, was narrowly defeated in the House (you can check if your congressmen voted against it here).

Since The Guardian published leaked documents exposing the depth of the NSA's spying powers, many people who've never put much effort into protecting their privacy are finally starting to pay attention. Evidence of public opinion concerning PRISM can be seen from the rise in traffic for pro-privacy sites like DuckDuckGo to the petitions demanding that the program be scaled back or done away with altogether. Some would argue that you waive your right to privacy by signing the terms of agreemen...

Gaining remote access to a phone isn't only for super hackers and spies. There are plenty of times when the average smartphone user would want to have remote access to their device.

The new 007 film, Skyfall, comes out this Friday, and dreams of becoming a super-spy have taken over my mind. Only I can't afford any of James Bond's awesome gadgetry or amazing cars—and you probably can't either.

Want to find out if your neighbors are talking about you? You could always hack their webcam or turn your iPhone into a secret spy camera, but unless you have a key to their house, that could be tricky to do without getting caught.
An amazing amount of news this week; new proposals and new agreements have sprung up. But so has our "need" to spread our presence. The military warns of another war, while 26 congressmen decry the use of drone strikes. Read on:

A-BnC Parties and More, Inc. demonstrates how to construct a do-it-yourself music guitar cut out for your musical theme party centerpieces. The guitar is accented with guitar strings made from black yard, heavy black card stock and clear push pins. Judy shows how to take a plain white polystyrene guitar cut out, paint and add these lovely accents. She puts it on another budget Just Add Sand centerpiece base and accents with two pieces of onion grass. Add balloons, a table name and table place...

Judy of A-BnC Parties and More, Inc. shows you how to make an economical do it yourself music note centerpiece. Three music notes are attached to wooden dowels which are added to a budget Just Add Sand centerpiece base. The centerpiece is accented with two pieces of onion grass. Add balloons, a table name and table place cards for an economical musical themed music note centerpiece for your Bat Mitzvah, Bar Mitzvah, wedding, special event or party!

If you've recently built a Wi-Fi spy camera out of an ESP32-CAM, you can use it for a variety of things. A baby monitor at night, a security camera for catching package thieves, a hidden video streamer to catch someone going somewhere they shouldn't be — you could use it for pretty much anything. Best of all, this inexpensive camera module can perform facial detection and facial recognition!

In a surprising twist of expectation management, Magic Leap managed to not only ship but deliver the Magic Leap One I ordered on Wednesday by 4 p.m. PT on the same day.

Ever wanted to know what sea creatures sound like? This video will allow you to hear fish talk and whales sing by altering a kids toy called a spy ear!

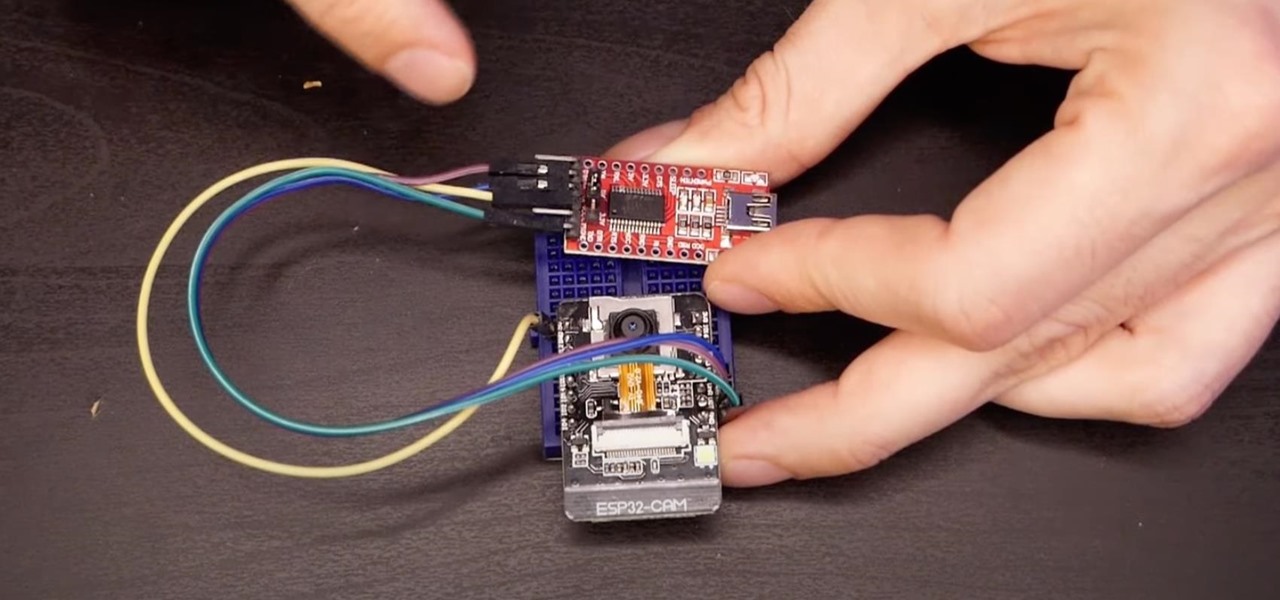
The ESP32-CAM is a convenient little camera module with a lot of built-in power, and you can turn one into an inconspicuous spy camera to hide in any room. There's only one issue: it does omit a USB port. That makes it a little harder to program, but with an ESP32-based board, FTDI programmer, and some jumper wires, you'll have a programmed ESP32 Wi-Fi spy camera in no time.