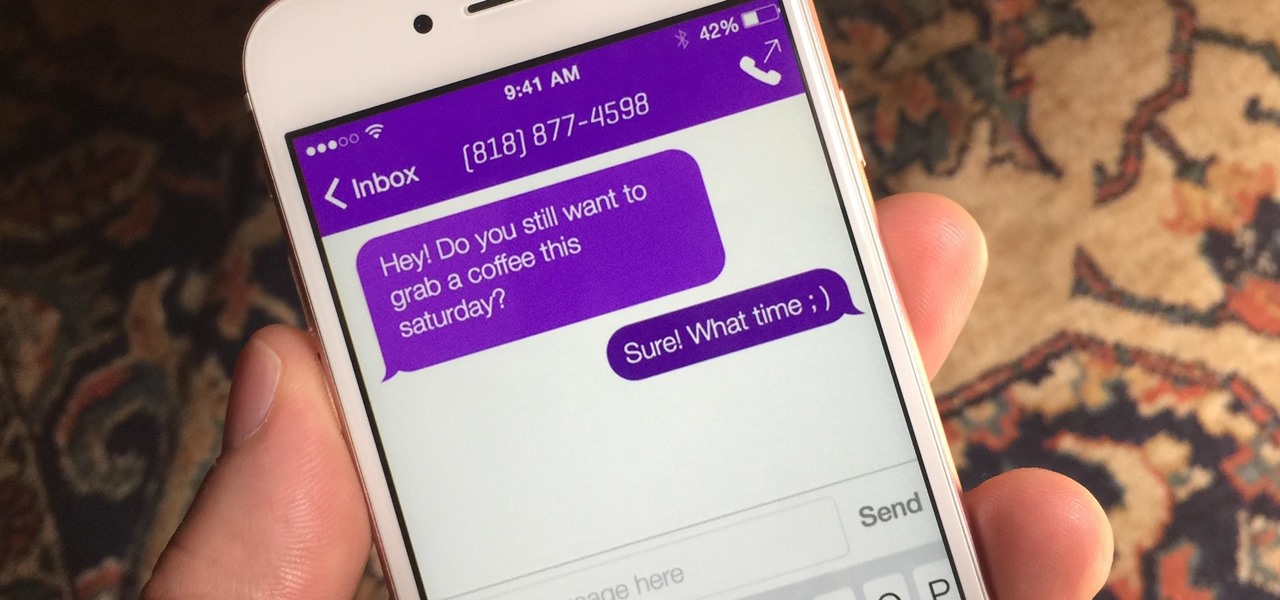
So you want to know what that person who is always on their phone is up to? If you're on the same Wi-Fi network, it's as simple as opening Wireshark and configuring a few settings. We'll use the tool to decrypt WPA2 network traffic so we can spy on which applications a phone is running in real time.

China-based virtual reality headset maker ANTVR has decided to enter the augmented reality space, and to do so it's launching its headset on Kickstarter. The company claims that its new Mix AR device has a field of view that surpasses the Meta 2, the HoloLens, and others within a smaller form factor and at a fraction of the price. But there's a catch.

Just days after Bose did its best to frame a pair of glasses frames with spatial audio as "augmented reality," a patent application from Magic Leap, surfaced on Thursday, March 15, offers a similar idea, but with real AR included.

A router is the core of anyone's internet experience, but most people don't spend much time setting up this critical piece of hardware. Old firmware, default passwords, and other configuration issues continue to haunt many organizations. Exploiting the poor, neglected computer inside these routers has become so popular and easy that automated tools have been created to make the process a breeze.

Amazon's first venture into the wireless phone market was a crash and burn moment — and that's us being kind. Their FirePhone went down in flames almost instantly, no pun intended.

In a world increasingly regulated by computers, bugs are like real-life cheat codes. They give you the power to break the rules and do good or bad without ever leaving your seat. And government agencies around the world are discovering and stockpiling unreported bugs as cyberweapons to use against anybody they see fit.

"Cooking" with liquid nitrogen seems like one of those activities that should be strictly limited to pros who are appearing on Top Chef, but it's the only way you'd ever be able to make Dippin' Dots at home. If that isn't enough of a reason for you to get some LN2 for your kitchen, check out this dose of pretty:

Salad greens are a staple in my house and for good reason: they're cheap, nutritious, and work as a base or an accompaniment for almost all meals. However, it's all too easy to forget about them and then pull out a bag filled with sludgy dark goo or yellow, inedible leaves.

Sometimes it's the little things that make our days better, like finding a dollar in our recently washed jeans or a box of donuts in the lunch room. But your Nexus 7 tablet's lock screen isn't typically one of those things—it's just a lock screen after all.

It may not be as large as the Samsung Galaxy Note 2, but the Galaxy S3's screen size is still big enough to make iPhone owners cry themselves to sleep. The 4.8-inch AMOLED display with 720 x 1280 pixels makes the GS3 a great mobile companion—and an even better portable gaming device.

There are many impressive features on a Samsung Galaxy Note 2, but just like any other smartphone on the market, the most used one is the camera. How many times did you take a picture today? Or admire all the selfies in your gallery? Or upload a video to Instagram, Vine, or Snapchat?

From a very early age we have an intrinsic obsession with things that float. Why do you think we love balloons and bubbles so much? So, it's no surprise that our smartphones are being invaded by floating features.

This is a really serious video. This video tell us about how to get rid of virus/spyware. It is based on JNBJABNK's own experience. She describe some step to destroy the virus which affected the computer. First of all make sure to confirm your system have spyware. Then open my computer folder and trace as quick as possible the infected file. Then run a full virus scan on that file. Delete the virus using the spy ware you have in your computer. On completing that you should restart your comput...

The ability to browse the web in coffee shops, libraries, airports, and practically anywhere else you can imagine is more than convenient, but convenience has risks. Using public Wi-Fi allows others to spy on you easily. Even your own internet service provider can see every website you've ever visited. Don't fall into the trap of protecting your identity, data, and devices after it's too late.

Throwaway phones aren't just for seedy criminals and spies—they can be useful for many everyday situations.

Welcome back, my rookie hackers! "How can I travel and communicate over the Internet without being tracked or spied on by anyone?" It's a question many Null Byteans have asked me, so I have decided to write a comprehensive article addressing this issue.

Why can't I see who is stalking my Facebook profile?

Former Google and Uber engineer Anthony Levandowski's scathing accusations challenging the physics behind Tesla CEO and founder Elon Musk's claims about Autopilot should force Musk to make his case that self-drive cars don't need LiDAR in the next few months.

Tesla's Autopilot self-drive interface in its new Model 3 signals the carmaker is already prepping its cars for Level 4 driving years ahead of the competition.

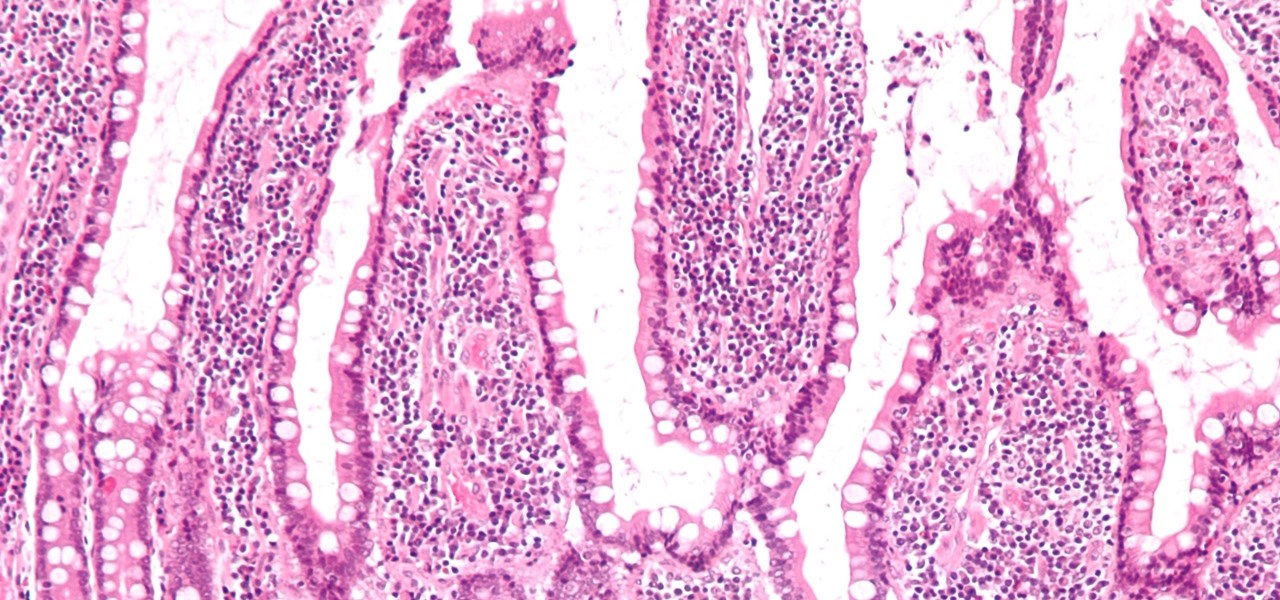
If the all the fingerlike projections in our gut were flattened out, its surface area would be 100 times bigger than our skin's. It's so large that the actions of just a small part of it can impact our health. A new research study has found that enterochromaffin cells in the intestinal lining alert the nervous system to signs of trouble in the gut — trouble that ranges from bacterial products to inflammatory food molecules.

While it may seem like the Cold War 2.0 is happening, at least some US spies are getting the content Americans need. That's right, Electrek has gotten some new pictures of the Tesla Model 3.

Chrysaor, a zero-day spyware believed to have been created by the Israeli "cyber war" group NSO, is an even greater threat to Android phones than it ever was to iOS.

Huawei is making a fresh attempt at launching into the US market to challenge Apple and Samsung's monopoly on premium smartphones. In its latest attempt to break into America, Huawei is trying to get its Chinese mobile chipset accredited by AT&T.

Last week, the U.S. Justice Department issued criminal indictments against seven Iranian hackers. These hackers, working for private companies in Iran, are accused of orchestrating DDoS attacks against U.S. financial institutions from 2011-2013 as well as intruding into the control panel of a small dam in Rye, New York. It is thought that these attacks were a response to the U.S. tightening financial restrictions on Iran during those years and the NSA-based Stuxnet attack on their uranium enr...

As touchscreen phones continue to evolve, the need for physical buttons seems less and less pronounced. While hard keys may seem like an endangered component on mobile devices, save for the Samsung Galaxy line, it'd be difficult to fathom a world where volume keys are absent.

Although this century is still young, with little fanfare we may have just witnessed the "Hack of the Century." AV software developer Kaspersky of Russia recently announced that they found that some hackers have stolen over $1 billion from banks around the world!

Welcome back, my nascent hackers!

Certain files contain sensitive data that you don't want being shared with just anybody. Even still, it would be nice to be able to send such a file to a certain confidante without fear of it falling into the wrong hands.

Hi! Let me get started on this subject as it is a very "touchy" subject. We all want to "hack" these days, and that's logical. Te be real honest here, i was inspired once by the words someone from the Null byte community said. In the (near) future, wars will be ended by computers and not a nuclear missile. That's something i really do believe in. But let us take a defensive measure instead of the offensive one. Sure, Full frontal bryte forcing is an option, but when it'll come that far we'll ...

There's really nothing safe about transmitting sensitive information electronically, but even if it gets there safely without being seen by prying eyes, there's no guarantee what happens to it once it reaches its destination. And let's face it, there are some things that you just don't want floating out there forever. So what can you do? Whether you want to send an email, a text, or a link, there are ways to send messages that self-destruct so that once they're read, they immediately vanish. ...

The pumpkin is everyone's favorite cucurbit come Halloween time, and while there are only a few types of Halloween-friendly pumpkins out there, there is definitely no shortage of what you can do with them.

It's no secret that there's a lot of surveillance going on these days. It's easier than ever to end up in a database, and even former government agents are speaking out about the atrocious amount of spying being done against our own citizens. They've targeted our laptops, cars, IP addresses, and now they're coming for our iPhones. AntiSec hackers managed to get their hands on a list of over 12 million Apple UDIDs (Universal Device IDs) from an FBI computer, and they published 1,000,001 of the...

Data makes the world go round. It has gotten to the point that it's considered the most valuable resource, perhaps even more important than oil. Businesses use data to collect critical information about their users and improve their services; governments utilize it to improve things like public transportation; doctors analyze data to find more ways to save lives.

No one ever said you had to be a culturally-relevant pun for Halloween, you know—or a scantily-dressed version of the inmates from Orange is the New Black.

Although Christmas is a time to spend with family and be happy and full of joy, sometimes it's nice to pull a prank here and there, especially since many will not be expecting them.

Soda bread, corned beef and cabbage, and colcannon are all great dishes to serve up on St. Patrick's Day, but desserts really let your inner leprechaun come out to play. Not only can you have fun incorporating all kinds of tasty Irish liquors into baked goods, you get to dye things green.

Halloween is a night to dress up as any character you'd like—but for women, that typically means wearing something skimpy or downright absurd. From "sexy" policewomen to nearly undressed fairy tale princesses, we're surrounded by costumes that leave little to the imagination. And, let's be honest: who wants to spend a chilly October night in barely-there clothing?

Depending on who you ask, internet connectivity should be a basic human right. With Google recently embarking on a project to provide internet capabilities to remote corners of the world using balloons and satellites while Facebook attempts to do the same with unmanned drones, the concept of free web access is steadily gaining steam.

Bottled water is a rip-off. Not only is it pretty much the same stuff that comes out of your tap for free, but plastic bottles are rarely recycled and thus account for a huge amount of the waste that's overflowing our landfills. Next Up: Water Bottles You Can Eat

Food is a necessity, sure, but every now and then it's so satisfying to eat something because it is fun and delicious. While eating a whole tub of homemade ice cream might satisfy your need for gluttony, there's a way to take it even further—make your dinnerware edible.