Before you can work in Adobe Flash CS3, you'll need to know how to work with it. Learn how with this clip. Whether you're new to Adobe's popular Flash-development platform or a seasoned web developer looking to better acquaint yourself with Flash CS3, you're sure to benefit from this free software tutorial. For more information, including detailed, step-by-step instructions on how to use the program's draw tools, watch this video guide.

As many of you stop-motion animation practitioners out there have probably realized, Legos are a great material for that medium, allowing for great diversity while being relatively easy to work with. Can they fly though? This video features a British boy explaining how to use a free computer program called Bafran to make Lego characters appear to be flying in an animated video.
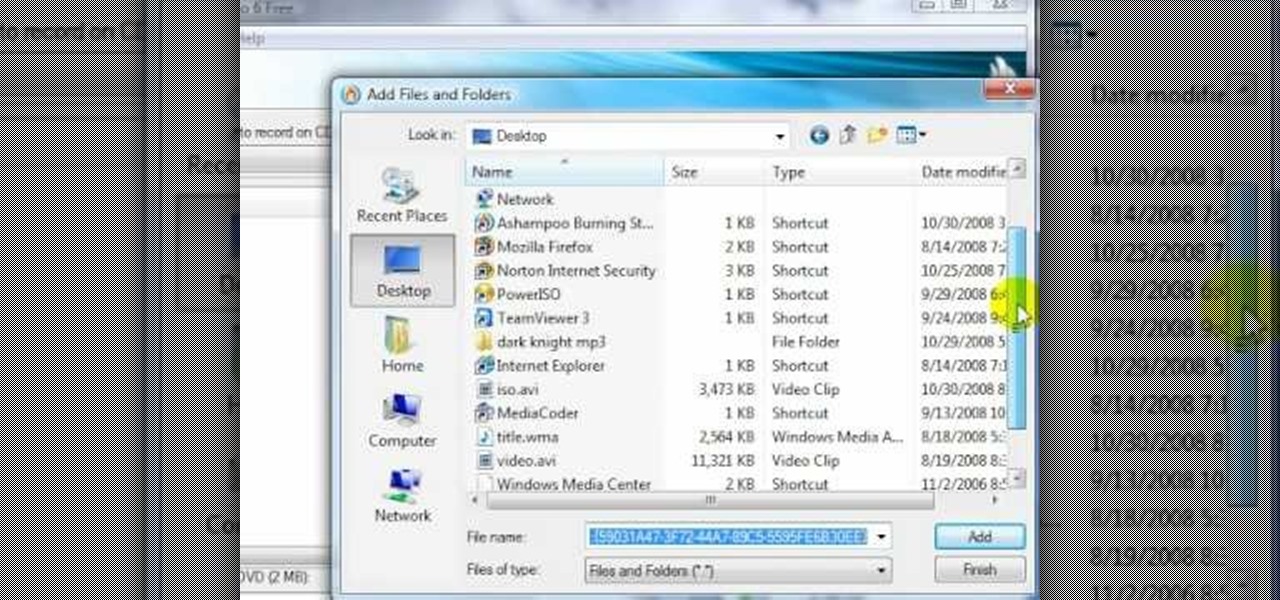
In this video tutorial, viewers learn how to create an ISO image. Users will need to download the program, Ashampoo Burning Studio 6. Begin by going to the Google search engine and search for the program. Select the result from download.com. Click on Download Now and save the file. Double-click on the file and follow the instructions to install it. Then open the program and select Create/Burn Disc Images. Select the type of disc image that you would like. Then click on Add and select the file...

In this video tutorial, viewers learn how to rip audio and video from You Tube to an i-Pod or computer. Users will need to download the Free Studio program from located the video description. Once the file is saved, double-click the file and follow the instructions to install the program. Now find a video or audio from You Tube and copy the URL. Now open the program, paste in the URL and download the file. This video will benefit those viewers who enjoy watching or listening to videos on You ...

Big business is on the web these days and you don't have to build a shopping website or blog to get involved.

This video from CNET Insider Secrets tells you how to recover deleted files from a data drive. If a disk is still readable by the computer, files may be recovered. Files may be recovered using the PhotoRec program, PC Inspector or other programs that may be available. An example is shown where mp3 files are deleted from a flash drive. We are then shown how files are recovered using the PhotoRec program, including how to select the correct file system. The mp3 files are recovered along with va...

This video teaches you how to open .zip files with a just few easy steps. First, you need to download a program Winrar. The download can be found at http://www.rarlab.com/download.html and the download should start immediately. Once the download is complete, open the program.

Now your computer is running slowly while opening the multiple programs, and for checking mails. The following steps easy to get faster the computer.

A quick video showing how to get free music online. May take a couple minutes per song. To prove quality I used the song i download in the video as background music. "I Wish" by Skee-Lo

New to the Ubuntu Linux distribution (or one of its derivatives) and looking for a way to start programs automatically when you boot up your machine? Take heart: This video tutorial will show you how to accomplish just that using your system preferences. Take a look!

New to OpenSceneGraph and not quite sure where to begin? If so, you're in luck. This tutorial will walk you, step-by-step, through the creation of your very first OpenSceneGraph program for the Mac OS X platform.

Don't let a bunch of programs run in the background and hog your Palm Treo's resources! Watch this electronics tutorial video to learn how to close them out. This how-to video makes maximizing your Palm Treo 750's power easy.

Watch this software tutorial video to learn how to quickly unzip archived files using the program WinZip. WinZip makes unzipping and unarchiving archived files quick and easy, and this how-to video provides helpful tips on how to use the program.

This computer programming tutorial screencast teaches programming tips and tricks on Ruby on Rails. This Ruby on Rails how to video covers basic string manipulation.

To avoid sports-related injuries, it is essential to warm-up before a race or a game or even before a training or practice session. Watch this video tutorial to learn how to warm up before running by doing side steps from Gilbert's Gazelle training program. This how-to video is a must watch for all track and field athletes.

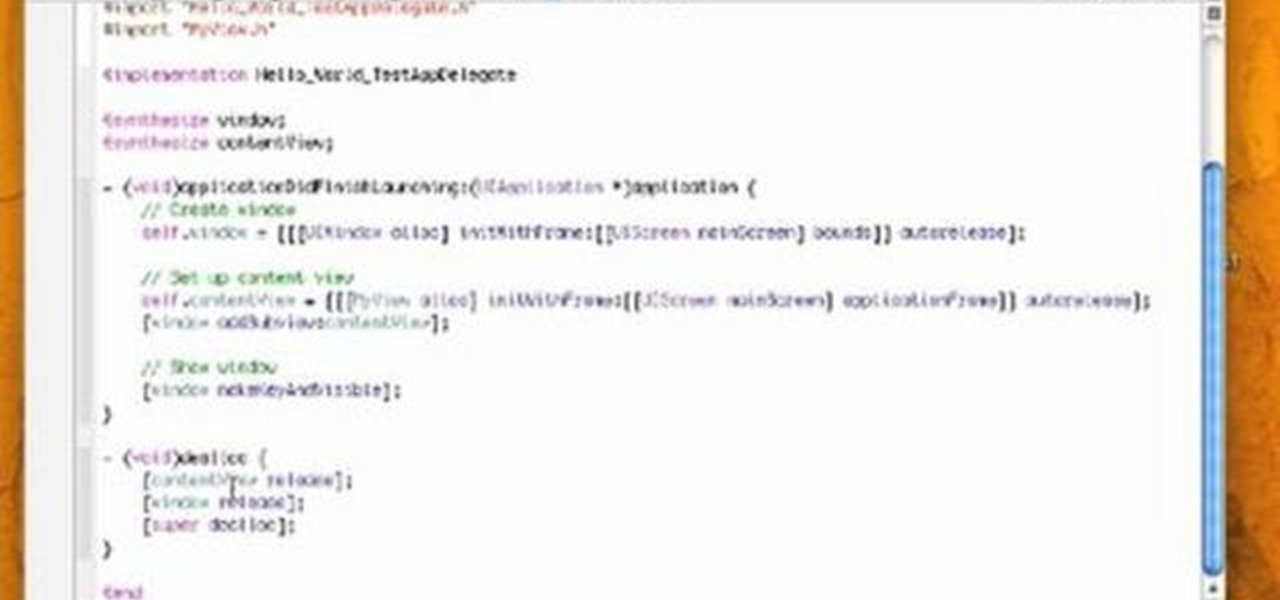
Check out this video screencast tutorial to help beginner iPhone programmers get started. This tutorial shows how to draw "Hello World!" text on the screen of the iPhone in Mac OSX with the help of Objective C (ObjC) in Xcode for Cocoa programming on your Mac OS.

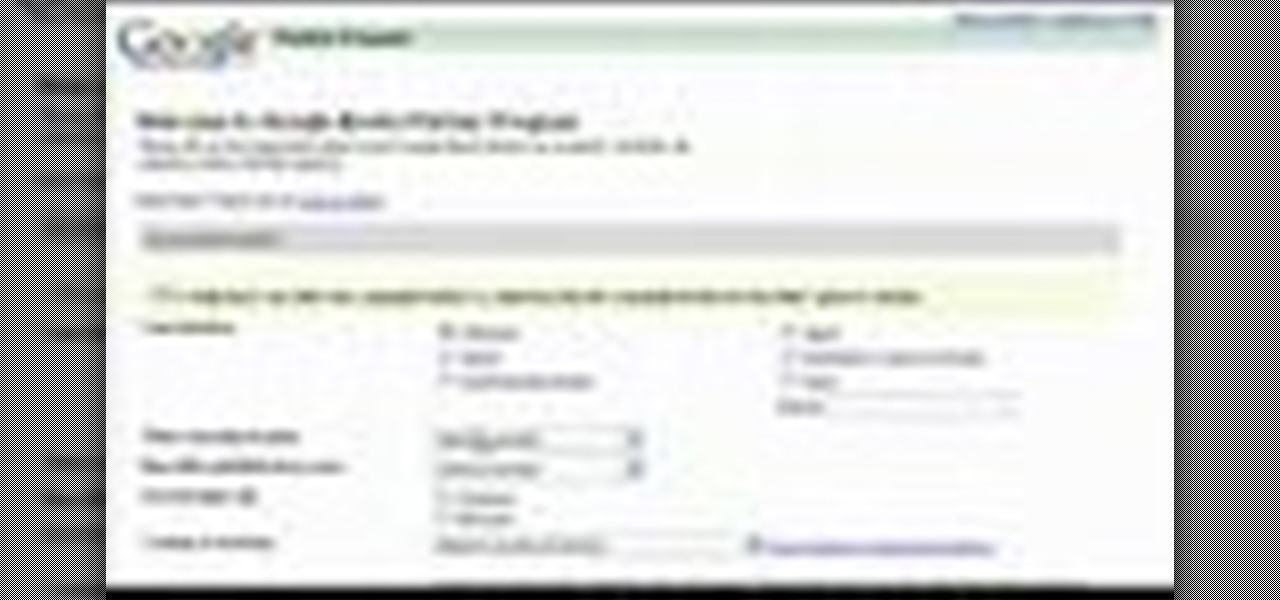
Learn how to apply for a Google Books Partner Program account, which allows you to submit your content for display on Google Book Search.

A VB.Net 2008 tutorial on how to make a program that can count cards in a blackjack game.

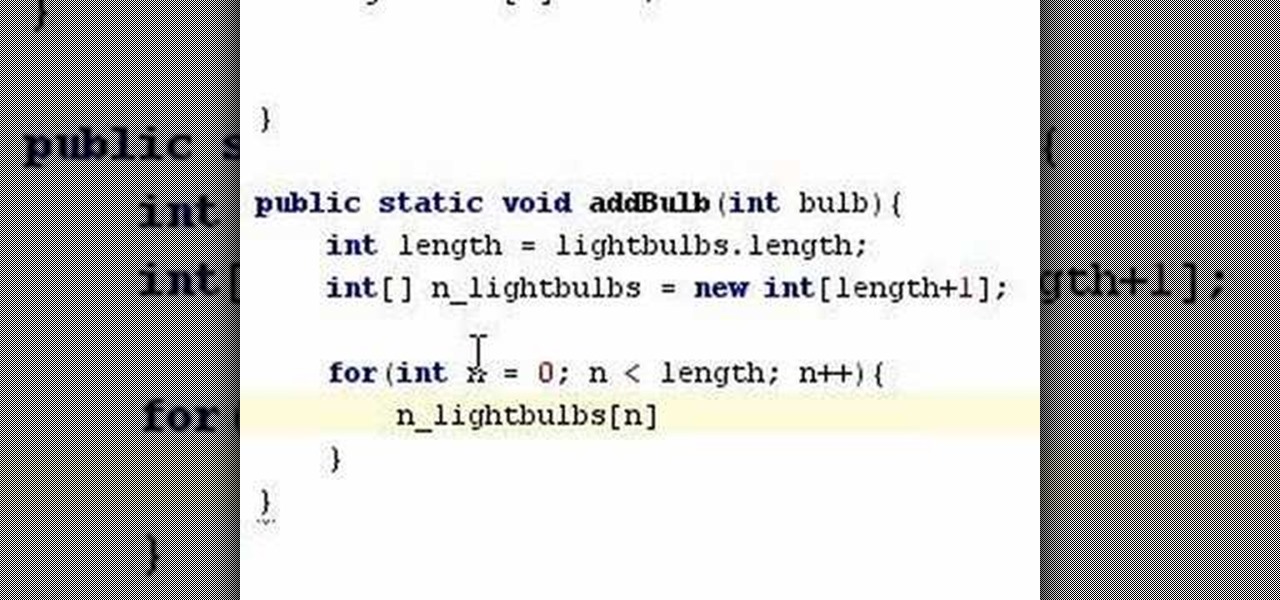
A tutorial on how to unroll and append elements to an array when programming in Java.

Learn to program If & Switch Statements in Java. This tutorial uses Java 1.6 with NetBeans 5.5.1 beta

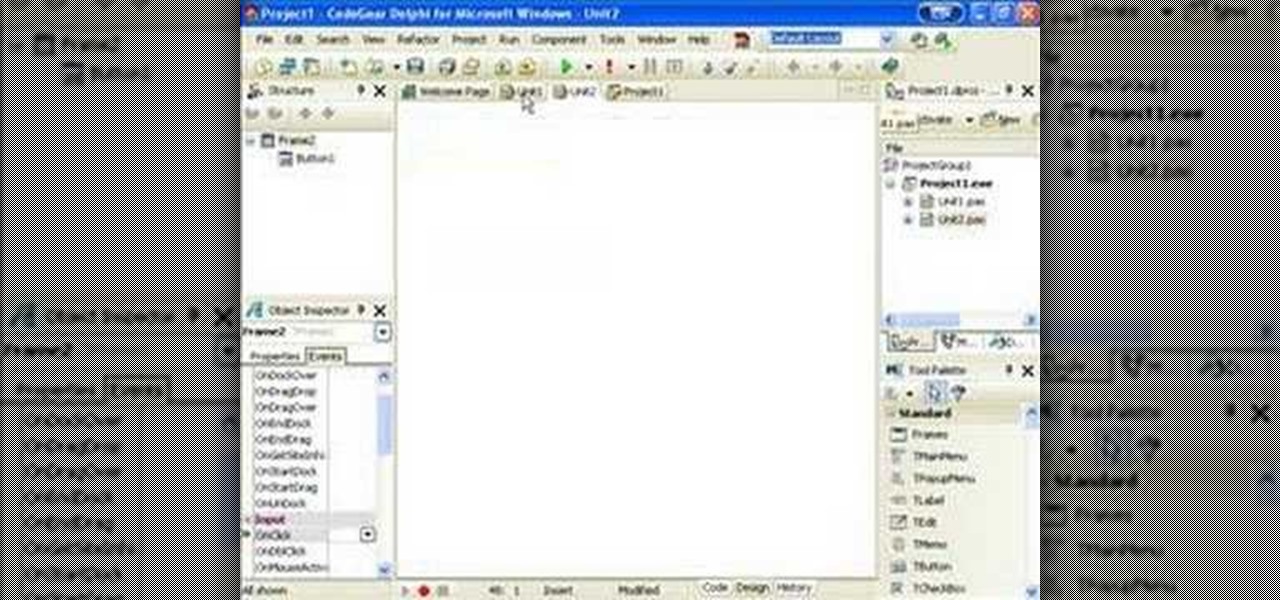
Delphi controls have an owner and parent property, find out what the difference is and how to use them when programming in Delphi.

You can connect your Nintendo Wii Wiimote to your PC using GlovePie input emulation software and a bluetooth connection. Learn how to program your PC to detect motion from dual input the Wiimote using GlovePie. You'll be able to connect two Wiimotes to your PC.

In this tutorial you will see how to use Jimmy's speed math program that he wrote in Flash. A download to the program is included. This is a GREAT way to help your kids or students (or maybe adults?) get better at math.

Microsoft Excel is one of the most powerful programs for modern businesses. By allowing you to manage, sort, and analyze large collections of data, Excel provides an essential service for any company interested in using the power of data science to its advantage.

Whether you're looking to add a substantial coding foundation to your hacking skill set or want to get a job in programming and development, knowing one or two programming languages just isn't going to cut it.

Augmented reality gaming pioneer and Pokémon GO mastermind Niantic is putting the pieces on the gameboard to prepare developers and gamers for the launch of its AR cloud platform.

While MacOS computers have been spared from some of the most famous malware attacks, there is no shortage of malicious programs written for them. To keep your computer safe from some of the most common types of malware, we'll check out two free tools. These tools can automatically detect ransomware encrypting your files and watch for unauthorized access to your microphone and camera.

Format strings are a handy way for programmers to whip up a string from several variables. They are designed to save the programmer time and allow their code to look much cleaner. Unbeknownst to some programmers, format strings can also be used by an attacker to compromise their entire program. In this guide, we are going to look at just how we can use a format string to exploit a running program.

The one thing that separates a script kiddy from a legitimate hacker or security professional is the ability to program. Script kiddies use other people's tools, while hackers and security pros write their own tools. To that end, we're going to see how a stack overflow vulnerability allows us to flood a variable with enough input to overwrite the instruction pointer with our own commands.

As demand for AR and VR developers continues to increase, particularly with the advent of Apple's ARKit platform, Unity has partnered with online learning company Udacity to help developers sharpen their skills for these jobs.

For companies wary of the temperature, PTC just made it easier for them to dip their toes in the waters of augmented reality.

Google just released Android 7.0 Nougat, and as usual, they're doing a staged rollout. This means that most users won't actually get the update on their Nexus devices for a few weeks—that is, unless they take matters into their own hands.

If you want to make some money from catching bugs and are sick of pentesting Facebook, Google, and Microsoft's products, Uber may be your new favorite playground.

Researchers have discovered a "severe vulnerability" that allows attackers to use eBay to distribute malware, and the online auction company has no plans to fix the problem.

How's it goin'? In this tutorial, we will learn about the security issues of the popen and system functions. I've seen a few people attempting to run command line utilities or whatever it is they require with calls to these two functions but may not know the security implications which come along with it. I will show you using an example from the wargame IO Smash The Stack.

In many programs on Linux, you'll come across programs which allow you to specify additional arguments instead of just simply running the program by itself. If you've used the Kali distribution, I'm more than certain you'll have come across these with the command line tools, else if you have been following these tutorials, we have already come across three tools which also use the same technique, i.e. gcc, gdb and wc. How do we do this with C? Let's find out.

As many of you know, processor's clock frequency improvement got stuck in about 2003, causing the origin of multicore CPU (and other technologies). In this article I'll introduce you on how to run code simultaneously in various processors (I suppose that all of you have a multicore CPU). When you write code without any parallel directive, it only executes in one CPU at the same time (see it below). OpenMP make simple to work with various cores (if not with all of them) , without so much heada...

bObsweep robotic vacuums automatically clean whenever instructed to do so by an owner or because of a pre-programmed schedule.

I have shown here to install Java development kit. It also contains the settings of path and classpath to prepare for java programming.

When it comes to text documents and spreadsheets, Microsoft Office is the be-all and end-all office suite—but it's not cheap. Paying anywhere from $140 to $400 puts a big dent in your bank account, especially if you're a broke college student eating ramen for breakfast, lunch, and dinner. Something that I wish I would've known about during college is Microsoft's HUP (Home Use Program). With HUP, any employee or student of an organization that has a Microsoft volume license is eligible to purc...