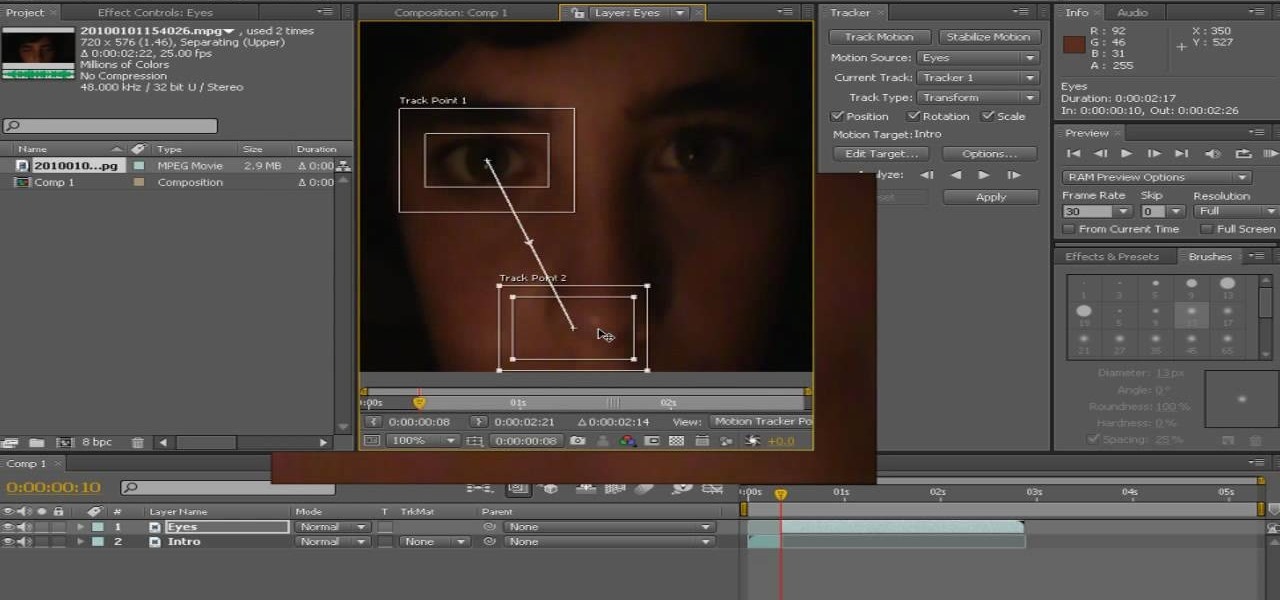
What every indie filmmaker needs is a little program called After Effects. After effects does wonders for any film requiring a little special effects that would normally be too expensive to make "real". Like this glowing eye effect. See how to make an eye glowing effect in Adobe After Effects.

You don't need a lot of money to build yourself an impressive home theater system. Yes, typically putting one together means piecing together a bunch of speakers, a supersized plasma HD TV, and whatever other add-ons you want. But really getting a great cinematic experience involves nothing more than having a computer with some fancy programs.

It's easy when Jamie-B from Total Recall Films takes an in-depth look at filming and editing techniques you can easily use to make your next film look and feel professional using a well know technique called "tricking the camera" -- and the viewer. Watch to see how to make a one-camera shoot look like multi-cams.

Animation controls run on the bottom of the screen. The time slider is the most important control for designing frames in Maya. Playback is exactly intuitive. This is a basic overview of Maya animation protocol and a lesson in using Maya tools.

Check out this video from Sessions on using the color wheel. Better understand color relationships, color schemes and color theory. This is a great lesson for designers, artists, stylists and decorators. Create color harmony using the color wheel. Tutorial video from Sessions Online Schools of Art & Design's "Color Theory" course. Part of Sessions' Graphic, Web, Digital Arts, Marketing, and Multimedia Arts Design certificate programs.
Creating curves with the pen tool in Adobe Illustrator is a good challenge. Check out this video on both drawing and editing with the pen tool. Click once in a place and then drag. This pulls out the direction handles.

Practice the left hook and jab/hook combi in boxing. These are basic and beginner techniques you must master to compete in the ring.

Check out these general tips to get the most out of your hurling training program.

Does your calculator just crunch numbers? Boring no longer. Mod your calculator into a fun video game console by installing Super Mario.

VNC stands for Virtual Network Computing. It is remote control software which allows you to view and fully interact with one computer desktop (the "VNC server") using a simple program (the "VNC viewer") on another computer desktop anywhere on the Internet. The two computers don't even have to be the same type, so for example you can use VNC to view a Windows Vista desktop at the office on a Linux or Mac computer at home. For ultimate simplicity, there is even a Java viewer, so that any deskto...

Netcat is a featured networking utility which reads and writes data across network connections, using the TCP/IP protocol.

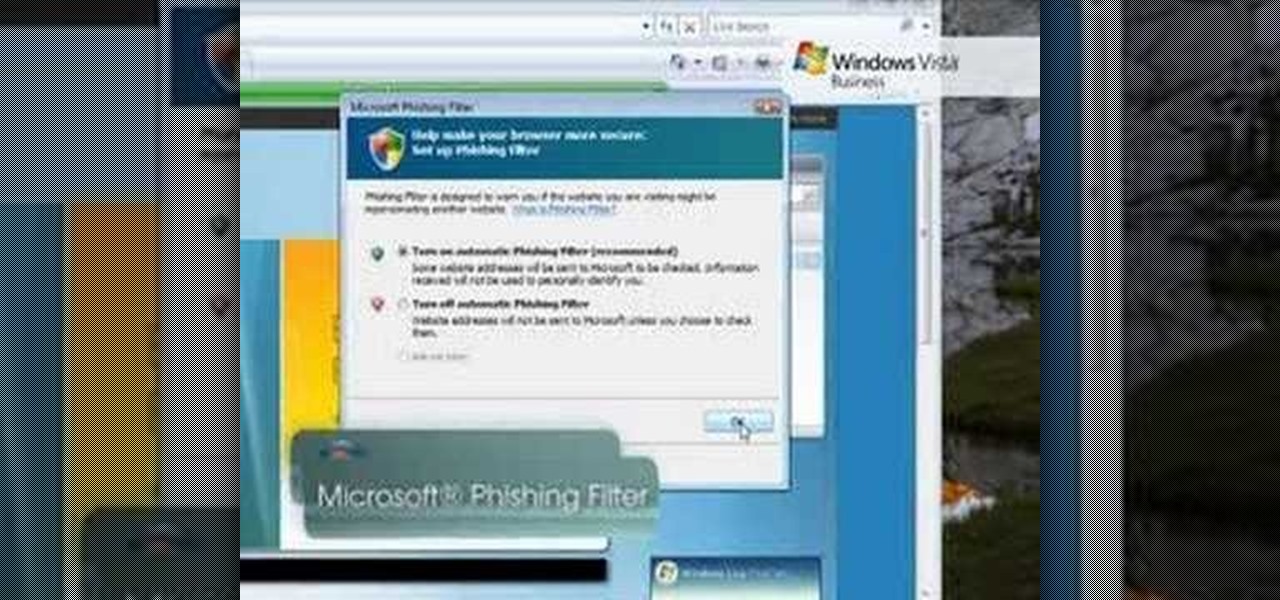
Check out this video tutorial to learn more about the Phishing Filter on Internet Explorer 7. Web browsers such as Microsoft's Internet Explorer 7 have become an important part of the computing experience for business and home users around the world. With the popularity of web browsers for accessing information, running programs, and even accessing corporate resources, the browser has become a target for viruses, malware, and phishing schemes that present real dangers to Internet users. Inter...

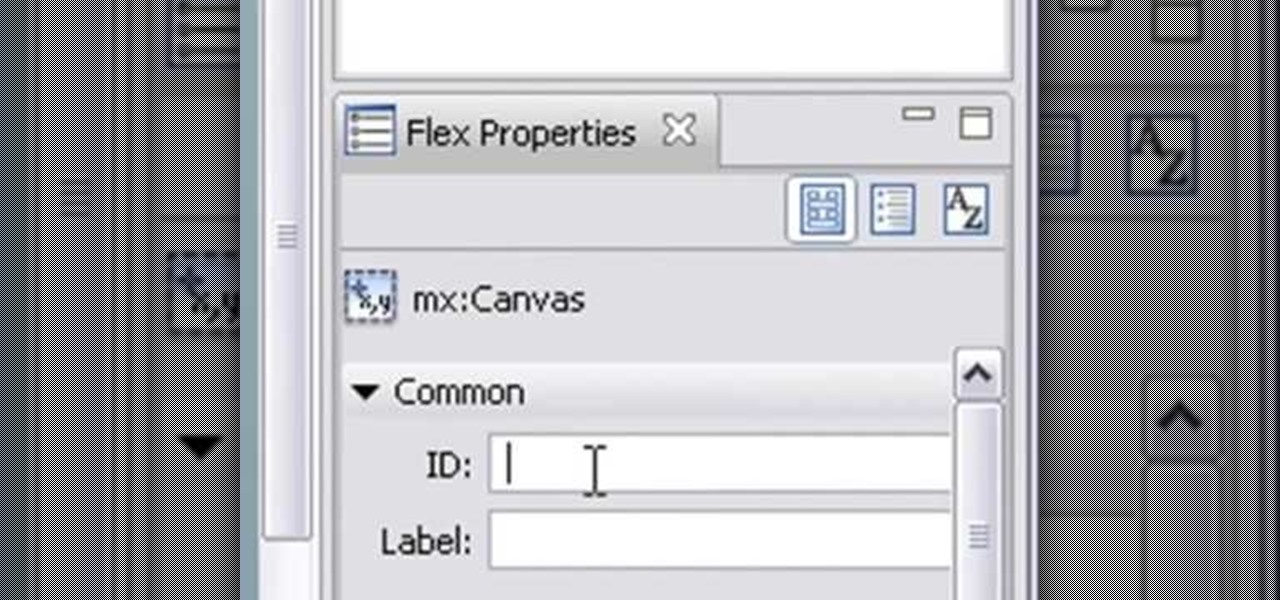
Altering the preloading screen in Flex 3 sure can be complicated, to say the least. Wouldn't it be awesome if the whole process was easier? Maybe if someone made, I don't know, a tutorial that walked you through the steps so that even a beginner could understand the procedure. Wouldn't that be fantastic? We thought so too... so here it is. Watch and learn how to change the Flex preloading screen in this programming tutorial.

Mike Lively of Northern Kentucky University demonstrates how to create a 3D plotting program for the sinc math function. Part 1 shows how to convert a Flash Package into a Flex application. Part 2 shows how to get the sinc function running and add different textures. Create a cool interactive 3D plotter in thie Adobe Flex Builder 3 and Papervision3D tutorial.

This instructional video will show you how to box model a female head in the program Blender. In this segment, this tutorial will take you from cube to a base head mesh which can be used to create any head from.

If you need to create an animated character, Maya is the software program for you. If you don't know how to make that character you've dreamed up, then maybe you should check out this Maya video tutorial on an important step -- creating a skeleton structure. Creating bones could be a daunting task in Autodesk Maya 8.5, but with the help of this four-part video, you'll see how to create those realistic bones for your animation with ease. You'll also see some common unintentional wrong rotation...

Watch this to see how to hookup a digital to analog television converter. When analog broadcasting ends in February 2009, you're either going to have to buy a new TV, pay for cable, or get a converter box.

A flaw in WPS, or WiFi Protected Setup, known about for over a year by TNS, was finally exploited with proof of concept code. Both TNS, the discoverers of the exploit and Stefan at .braindump have created their respective "reaver" and "wpscrack" programs to exploit the WPS vulnerability. From this exploit, the WPA password can be recovered almost instantly in plain-text once the attack on the access point WPS is initiated, which normally takes 2-10 hours (depending on which program you use).

Windows 7 has a ton of new features available, and a lot of them are accessible right from the desktop! With features like Aero Shake, Peek and Snap, it's easy clear a cluttered desktop. There's cool wallpapers to add, a newer and more efficient taskbar, improved gadgets, and more. See for yourself.

This video tutorial belongs to the software category which is going to show you how to convert a Word document to a password protected PDF file with NovaPDF. Go to NovaPDF and download the program and install it. It is a paid program. Select the word document that you want to convert and select print option. Under the name of the printer you will find novaPDF option. Select this and click 'preferences'. Now click on 'security' and select high level encryption. In the document permissions, sel...

If you have not used your eRecovery system in a long time and have forgotten the password, have no fear. This video is here to help you retrieve your details and use your program again. In this clip, learn how to recover any lost passwords with Acer's eRecovery Manager for Linux.

In this how to video, you will learn how to master and mix a rap song using Cool Edit Pro 2. First, download the program and open the vocal track in the program. Double click the vocals to highlight it all. Next go to effects and pick amplitude and amplify. Choose center wave and click okay. Go to amplitude again and choose dynamic processing. Choose very fast processing. Go to delay effects and type in 250, 10, 1812, 20, 100%, and 30% in the window. Next, go to filters and pick FTT filters. ...

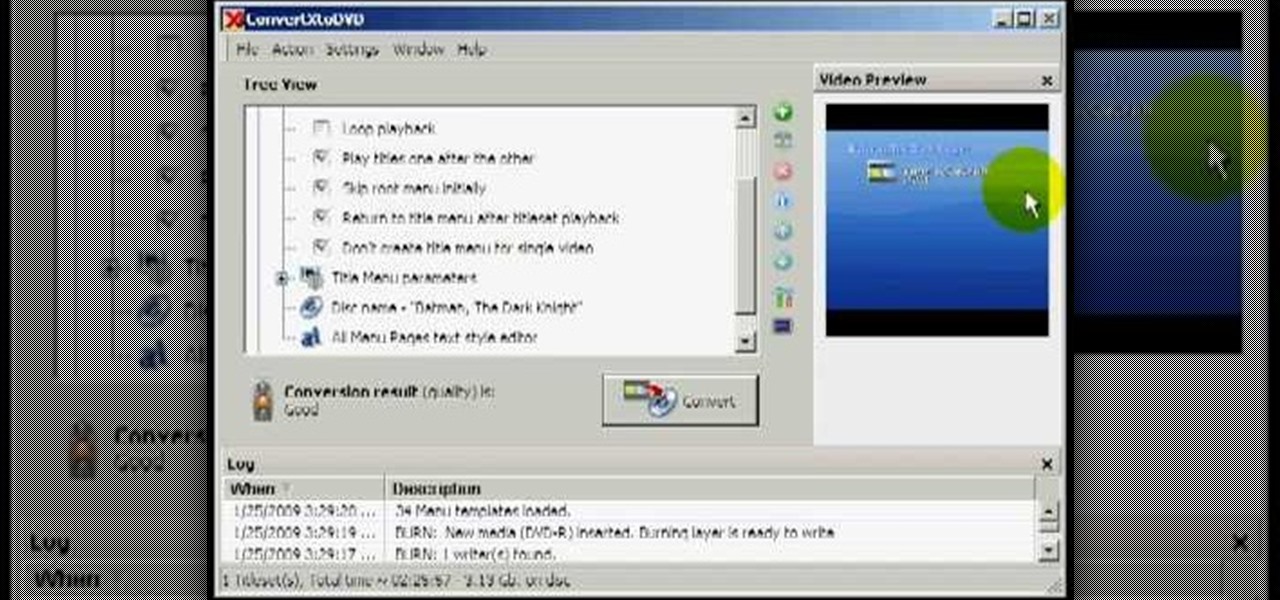
In this video from Act2Scene5 we learn how to convert movie files to DVD player playable video using ConvertXtoDVD. All you have to do is take a movie file and drag it into the interface. The program will import it into the program. Once it's in the application, you have several options you can do. You can change the name of the DVD so you can name it. You can also set the DVD to auto start. You can use loop playback where the video will restart after watching it through. Another option is to...

Wartex8 demonstrates how to use remote desktop in Windows XP. Remote Desktop is a useful utility that you can use to control another computer and its applications.The necessary steps that are adopted to activate remote desktop are:1) Right click on my computer icon (either the icon on the desktop or the one on the start menu list) and select properties, and a new dialog box called system properties will pop up on the window.2) In the System Properties, select the computer name tab and write d...

If you have just purchased a new Ford Taurus, you may have noticed the new SYNC feature. SYNC is a GPS built right into your dashboard. If this is your first time using a global positioning system, you may need a few pointers. Check out this video and learn how to access step by step directions and get where you need to go.

Not enough space on your laptop? No problem! Grab a new hard drive from your local office supply store and follow this tutorial to learn how to install it.

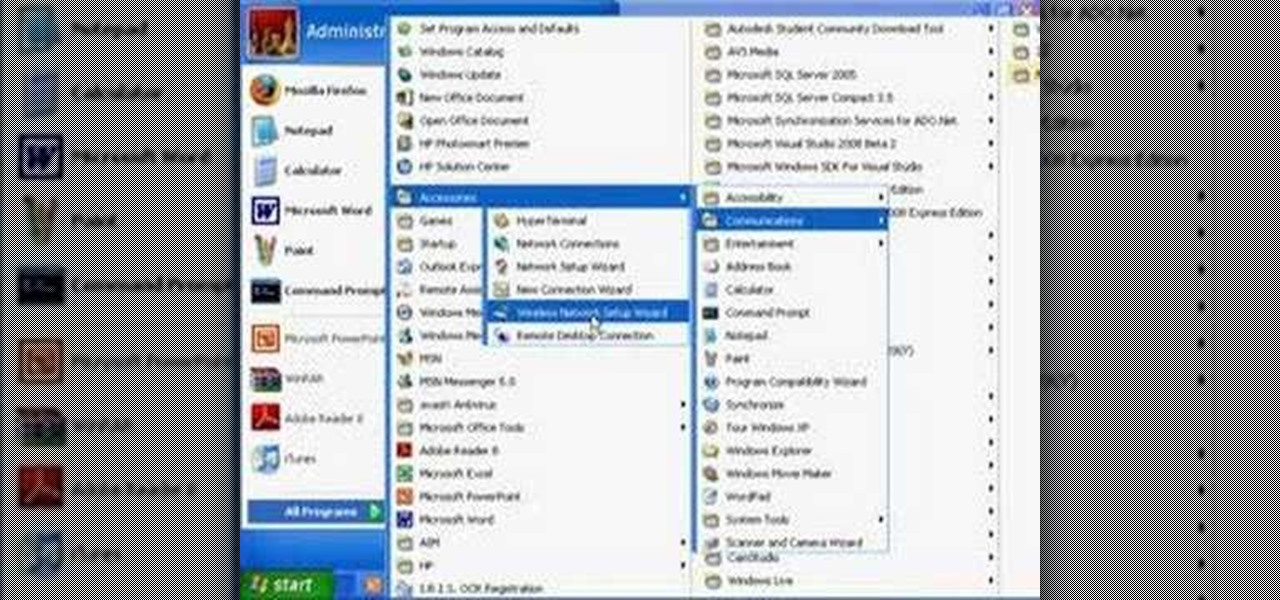
Although it is a rare and potentially frightening occurrence, knowing how to do a system restore in Windows XP is an important thing to know how to do. To get started with a system restore, select the Start menu in the lower right of your screen. Then select All Programs. Then from the All Program menu, select Accessories and then from Accessories, select System Tools. There are several items under System Tools, but you want to select System Restore. You will follow through the next few scree...

Unlock and jailbreak your iPhone! You can either reinstall the entire operating system, wiping all the data from your phone, or you can wait for Black Snow to come out. In the method shown in the video, you can unlock right away. To restore, hold option (on a Mac) or shift (on a PC) and click restore. After it is done restoring, you should be getting an error message that the phone isn't registered and to insert a SIM card. Insert the SIM card you want to use. Close iTunes and open up www.bla...

The ability to browse the web in coffee shops, libraries, airports, and practically anywhere else you can imagine is more than convenient, but convenience has risks. Using public Wi-Fi allows others to spy on you easily. Even your own internet service provider can see every website you've ever visited. Don't fall into the trap of protecting your identity, data, and devices after it's too late.

Always wanted to learn Python but don't know where to start with the high-level programming language? The Basics for Python Development is perfect for beginners — and right now, it's on sale for just $14.99, which is an impressive 92% off its usual price of $199.

Now that more people are working from home on unsecured networks and personal devices, hackers are having a field day accessing everything from private browsing histories to personal banking information. A virtual private network (VPN) is the first and most important line of defense when it comes to protecting all of your devices from digital intrusions, but not all VPNs are created equal.

Keeping the books in order is one of the great challenges every business owner faces. Having a great product or service is one thing, but managing the minutia of invoicing can trip up a lot of small- and medium-sized businesses.

It's no secret that the vast majority of Null Byte readers range from beginner to seasoned coding pros and developers. Regardless of whether you're interested primarily in building websites or creating best-selling apps and games, working with a wide variety of programming languages remains one of the best ways to make serious money in an increasingly app-driven world.

Few things are more important than being well-versed in data analytics and interpretation when it comes to succeeding in today's increasingly data-driven world. As a data scientist, these skills are the key to a high-paying career. For hackers, there's no better way to defeat the enemy than to become the enemy.

Since its release back in 1988, Microsoft Office has been the top client and server software suite for businesses around the world. Office's domination is thanks to both Microsoft's extraordinary foresight and their continual updates and innovations to ensure that companies always get what they need.

I got my first Philips Hue White and Color Ambiance bulbs because they're the consensus best of the best for colored lighting. But after spending 90 bucks on two light bulbs, when it came to all the accessories like switches and buttons, I went with cheaper third party options. Little did I know, I was overlooking a great first-party accessory with a surprisingly reasonable price.

For anyone interested in using cheap, Wi-Fi-connected microcontrollers like the ESP8266, the Arduino programming language can be a barrier to entry. Based on C++, Arduino requires knowledge of more computer science than languages like Python. Fortunately for beginners, setting up MicroPython on an ESP8266 allows anyone to write Python on affordable microcontrollers in a matter of minutes.

While Magic Leap World gets its share of fun apps for playing with Porgs, watching TV, and exploring the ocean's depths, developers are making a strong business case for the Magic Leap One as well.

They're finally here. Apple revealed the brand new iPhone 11, 11 Pro, and 11 Pro Max on Sept. 10, and despite the questionable names, these are the best iPhone models money can buy. If you're looking to get your hands on one of these devices as soon as possible, there are few important dates you need to know.

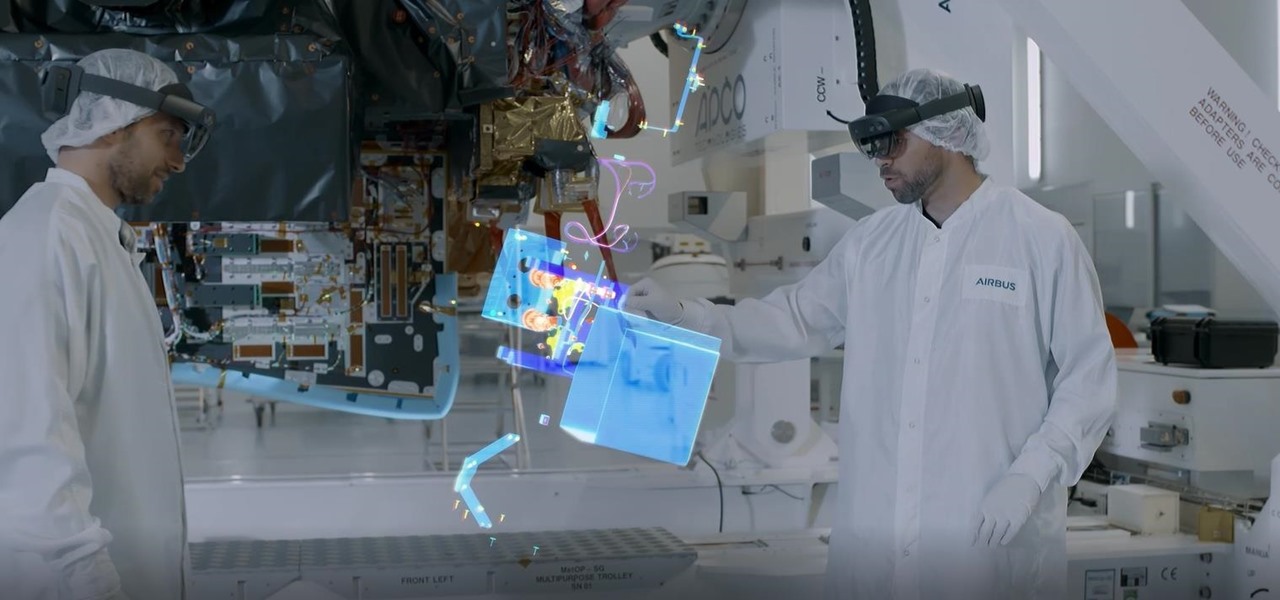
Aircraft manufacturer Airbus is so impressed with the boost in productivity it has gained from Microsoft's HoloLens, the company will begin offering augmented reality software to its customers.