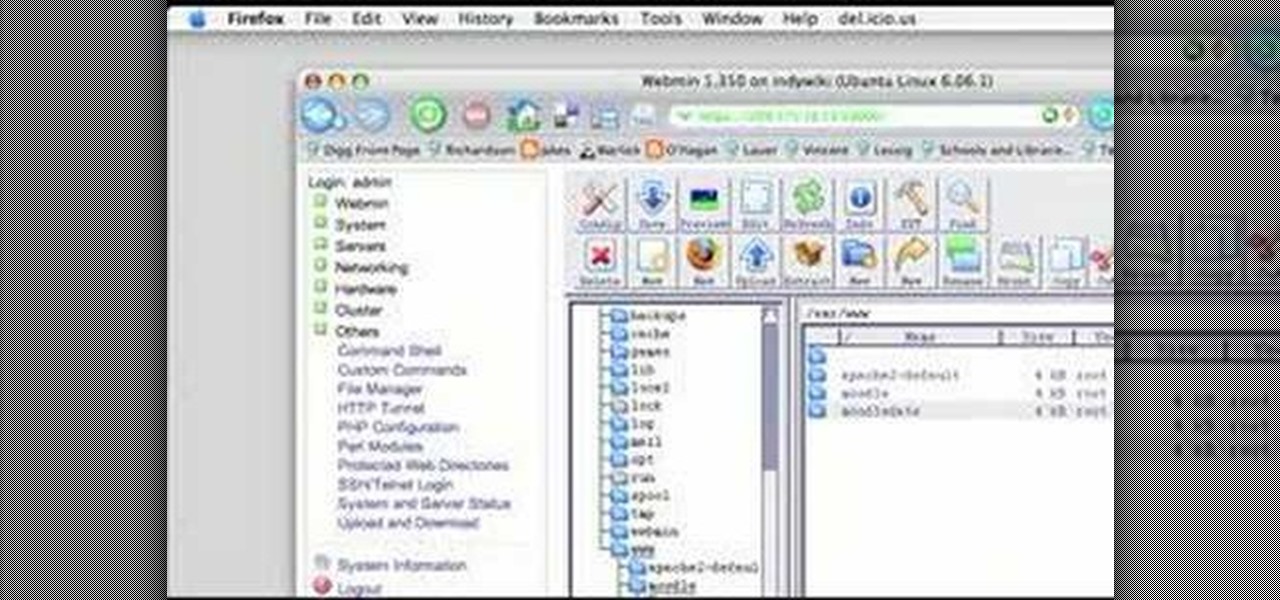
Interested in teaching an online course using your own server but can't quite figure out how to configure everything? This video demonstrates how to adjust folder settings within Moodle, the free, open source course management utility, via the Webmin interface. For step-by-step instructions, take a look.

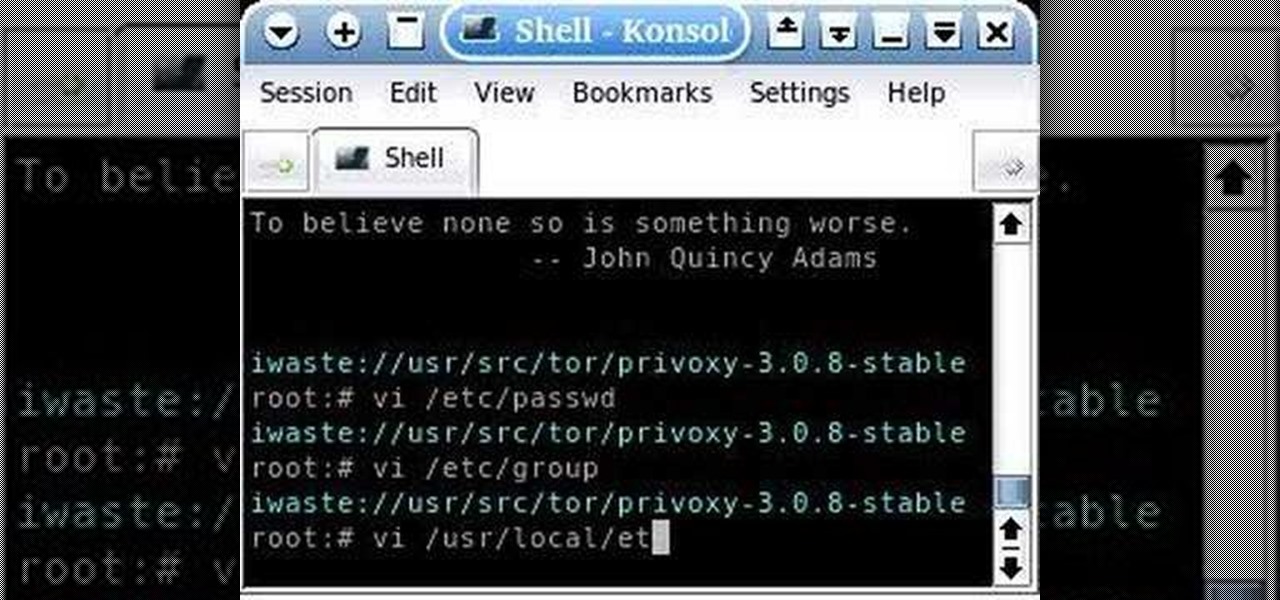
This video demonstrates how to install Webmin via SSH. Once you've downloaded the Webmin interface package, you'll want to install it onto your serve. In order to do that, you'll need to depackage it. If you're new to Linux or otherwise unclear about how to proceed, then watch this video for step-by-step instructions.
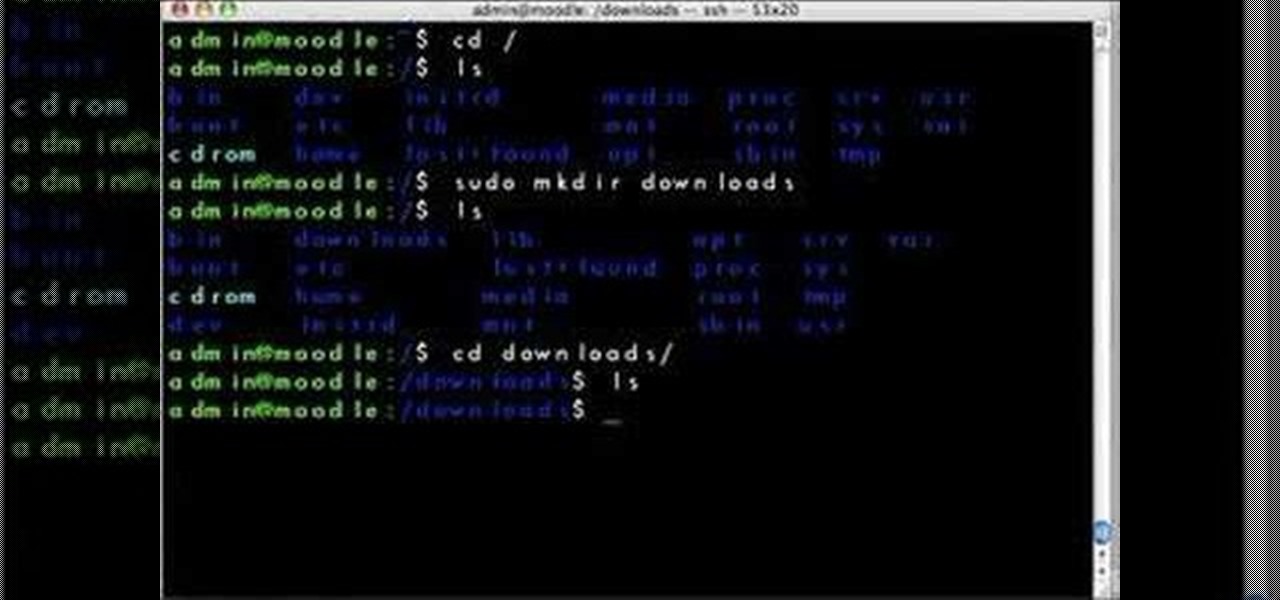
In this video you'll learn how to download Webmin, a web-based Unix administration interface, which will allow you to manage your serve with a web browser. If you're interested in running the Webmin interface, then watch and follow along.
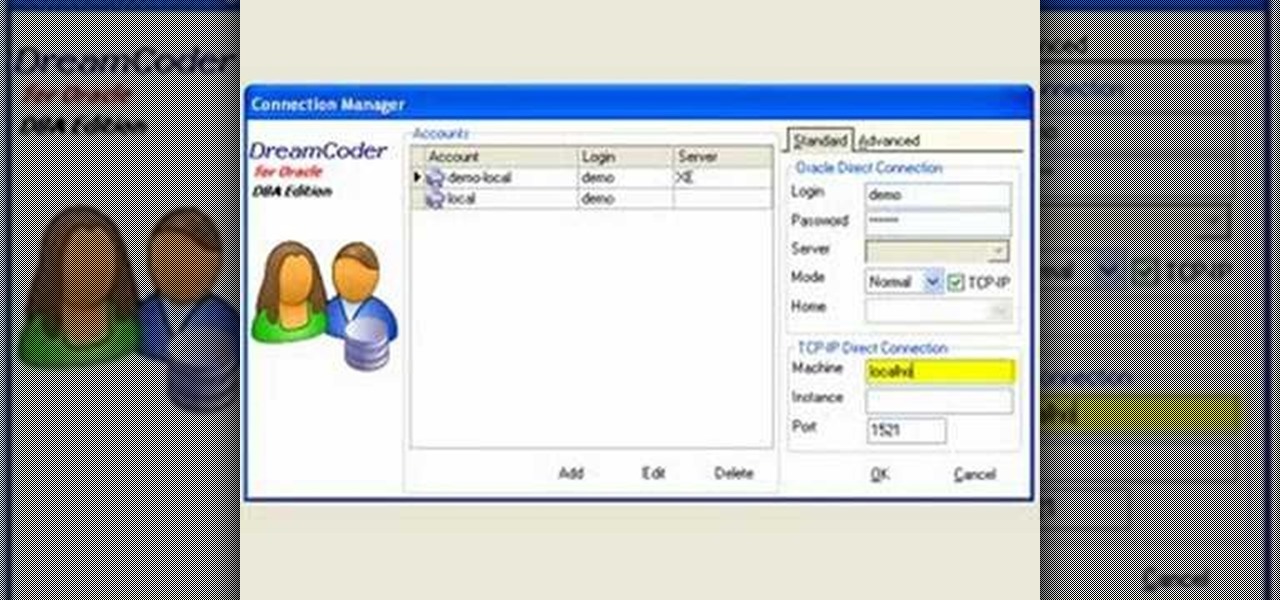
This tutorial will walk you, step by step, through, the process of establishing a connection between Oracle database server and DreamCoder for Oracle using the TCP-IP Direct connection option. To learn more about connecting to an Oracle database without an OCI client, press play!
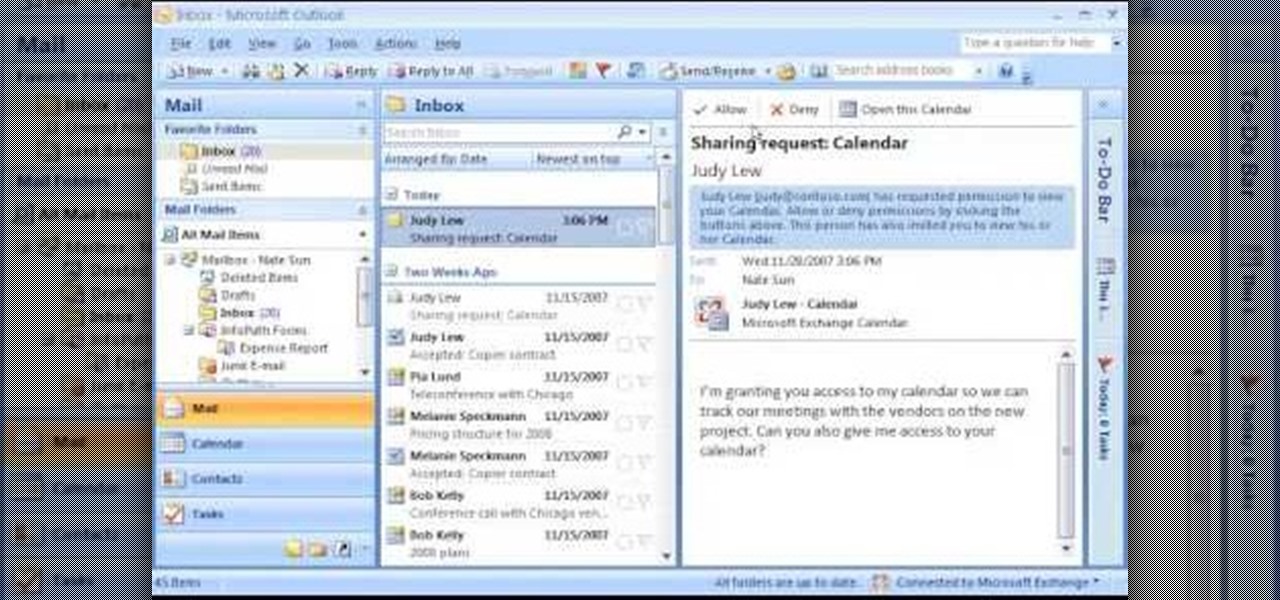
This tutorial shows you how to share your calendar three ways in Microsoft Office Outlook 2007. If your company uses Microsoft Exchange Server, you can share your calendar within the organization by using that feature. You can also send a snapshot of your calendar in e-mail to people outside your company. And you can publish your calendar on the Microsoft Office Online Web site and restrict how much detail is shown and who can access it.
Check out this tutorial and learn how to use Excel Calculation Services to handle processor-intensive calculations from your Microsoft Office SharePoint Server 2007 team site and to control access to external data.

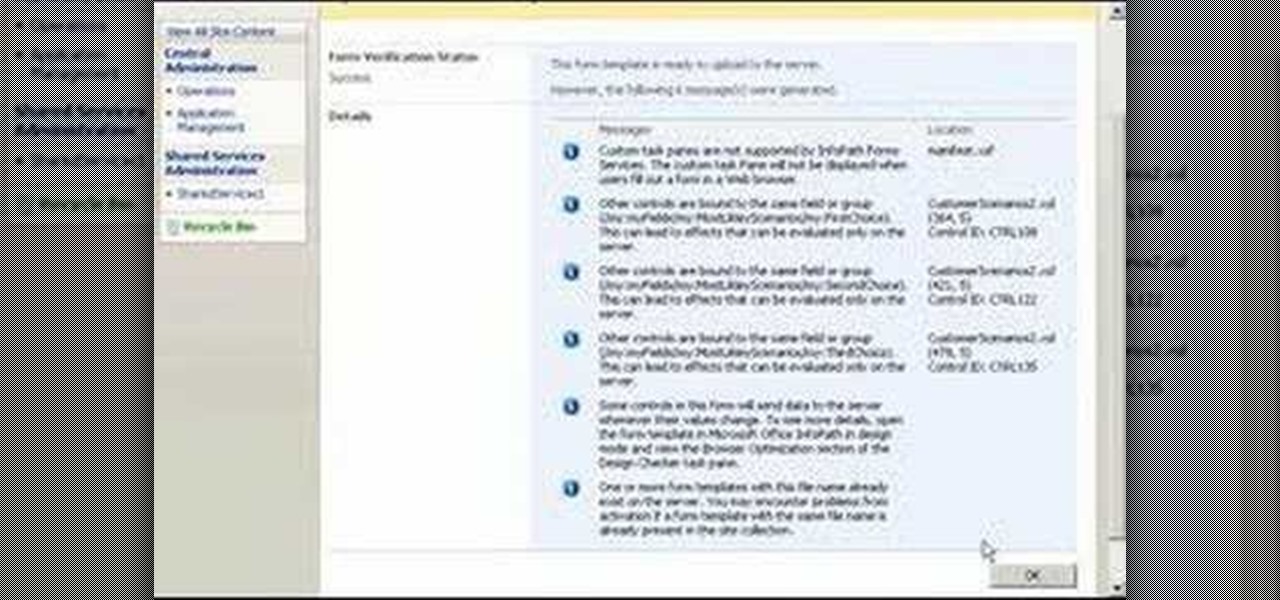
Now you can enable users to fill out Microsoft Office InfoPath 2007 forms by using a Web browser, which makes your forms more accessible to a wider audience. This instructional video shows you how to go through the process an IT Administrator can use to verify, upload, and activate an administrator-approved form template on a Microsoft Office SharePoint Server 2007 site.

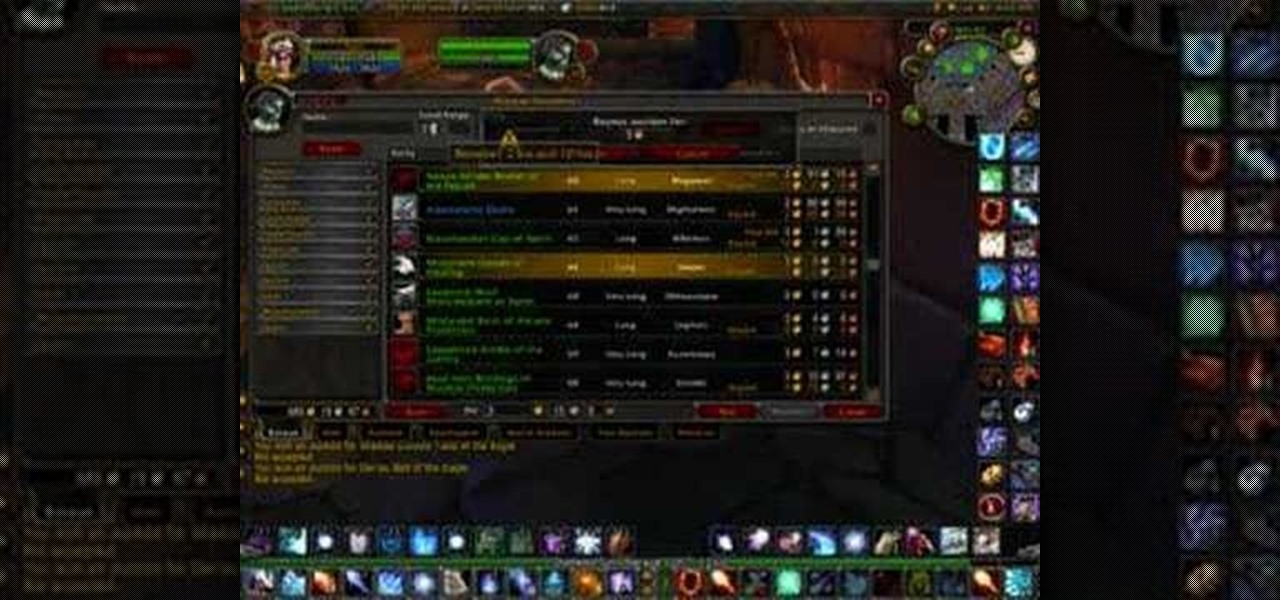
This how-to shows how to make gold in World of Warcraft. With this technique you can easily make 500-1000g a day in your spare time. This completely depends on the economy of your server, but it is amazing how you can make so much money.

In this video tutorial, Chris Pels will show how to persist and restore information in the ViewState of a custom user control. First, learn how to persist simple values containing .NET primitive types such as String, Int32, Boolean, etc. Then see how to persist complex types such as Class which contain properties storing information. The sequence of processing View State information during the lifecycle of an ASP.NET page is also discussed.

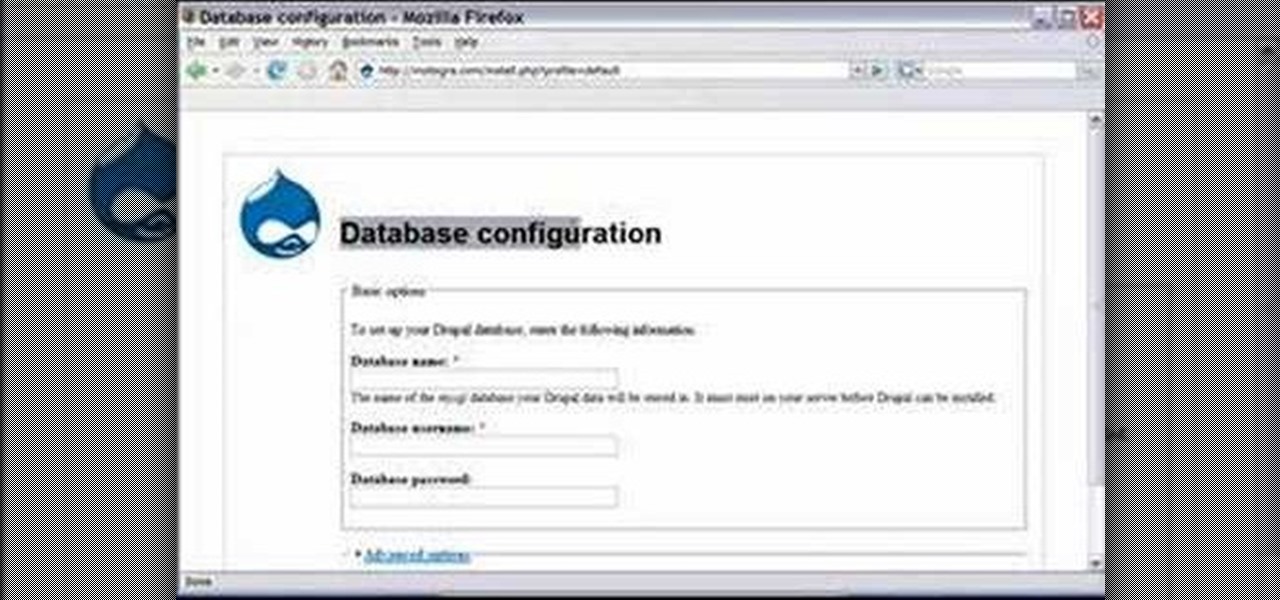
Basic installation of Drupal on a web server from start to finish with good explanations of Drupal's framework. Tutorial assumes viewer knows basic FTP and database configuration.

This is a tutorial about how to browse the web anonymously on a Linux server. Requires some knowledge of Linux. Be sure to note that information sent through this system is ever MORE open to hackers than the normal Internet. Don't send any personal information this way.

If you have been looking for a way to get the popular Joomla Content Management system running on Windows with IIS, you may have run into many problems. In fact, many people spend days trying to get Joomla running on IIS and run into roadblock after roadblock. The problem is getting PHP, MySQL, Joomla and IIS to all play nicely together. As you search for solutions, it is easy to find part of the answer, but rarely do you find it all in one place... until now. In this video tutorial we start ...

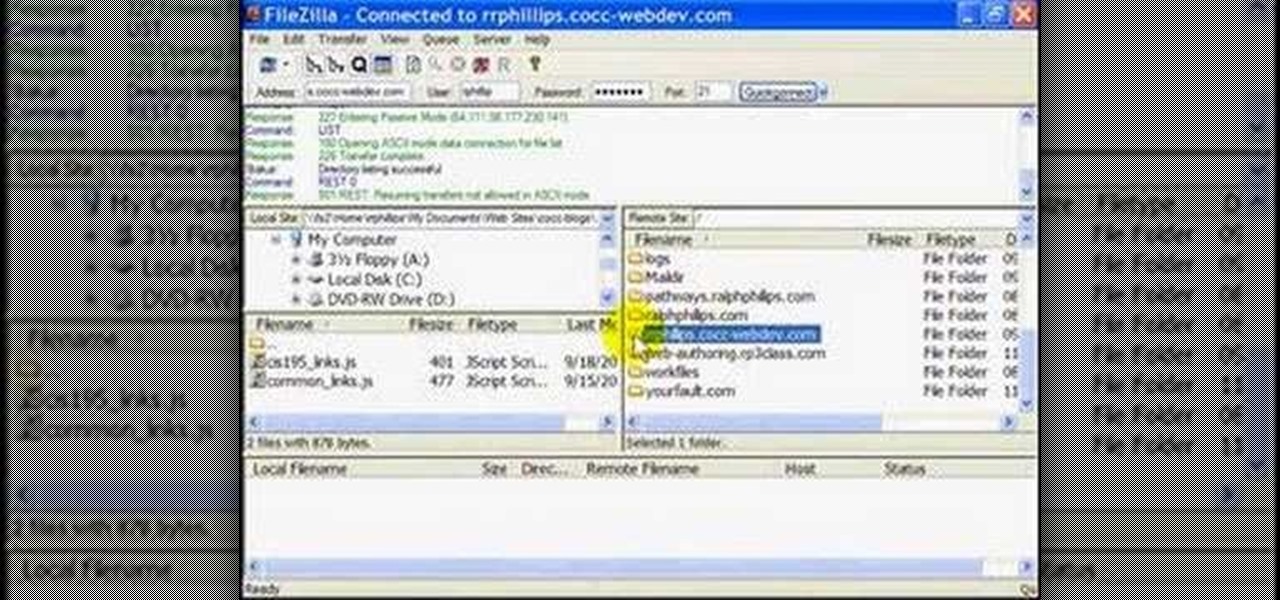
Use the Filezilla FTP client to publish files to your web server.

This video shows a cut and paste illustration of the tools Google offers in it's documents programs. Sharing a document can either occur by transmitting the doc from your home server to another person's home OR you can upload a doc to Google and browse from anywhere-- not just your home computer.

SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to extract information from a target, as well as smbclient to connect to an SMB share and transfer files.

A hacker with privileged access to a Windows 10 computer can configure it to act as a web proxy, which allows the attacker to target devices and services on the network through the compromised computer. The probes and attacks appear to originate from the Windows 10 computer, making it difficult to detect the attacker's actual location.

Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you already have permission. The vulnerability can lead to an attacker gaining complete control over a device.

When Pokémon GO developer Niantic launches its Real World Platform for augmented reality gaming, it will run over 5G speeds courtesy of T-Mobile parent company Deutsche Telekom and the edge servers of its MobiledgeX subsidiary, the companies announced today.

Configuring onion services for the first time can be tricky. A surprising number of system administrators make seemingly trivial mistakes that ultimately lead to catastrophic cases of de-anonymizing supposedly anonymous sites on the dark web. OnionScan is a tool designed to identify common misconfigurations in onion services and aid us in understanding how to fix them.

Tor is an excellent obfuscation network for web traffic, and while instant messaging over the network is very useful, it can be relatively difficult to configure. In this guide, we'll look at two synchronous communications platforms (instant messengers) which can be routed over the Tor network, Ricochet and XMPP.

The pictures we upload online are something we tend to think of as self-expression, but these very images can carry code to steal our passwords and data. Profile pictures, avatars, and image galleries are used all over the internet. While all images carry digital picture data — and many also carry metadata regarding camera or photo edits — it's far less expected that an image might actually be hiding malicious code.

The HoloLens is the world's first untethered holographic head-mounted computer, which Microsoft has been rather proud of—and they have every reason to be. Of course, as soon as we developers get adjusted to the idea of keeping the scope of our projects inside the bounds of the HoloLens' processing power, Microsoft hits us with the Holographic Remoting Player.

Without explicit cooperation between Apple and the US government, authorities could still be monitoring Apple users. According to The Information, Apple is worried the servers it has been using might be bugged. We already know the NSA intercepts equipment to install backdoors, so this is a legitimate concern.

Welcome back, my greenhorn hackers! After the disaster that was Windows Vista and the limited and reluctant adoption of Windows 8 and 8.1, Windows 7 has become the de facto standard operating system on the desktop/client.

If you use apps on your smartphone, chances are you have no idea what those apps are doing with your information. Just this year, there have been several scandals involving apps transmitting user data, like Path uploading users' entire address books onto its servers, HTC's Security Flaw, and Brewster exposing users' personal information (even Ashton Kutcher's). A new service called Mobilescope wants to make sure you always know where—and to whom—your data is going. Lots of apps copy your cont...

Our server is primarily a fun server, so we don't often get huge, epic builds of amazingness. And yet that's exactly what we've got with Mgabrys's build, the Portland. Or, more specifically, Zeppelin City OR-2019 "Portland".

You may not have thought of dorks as powerful, but with the right dorks, you can hack devices just by Googling the password to log in. Because Google is fantastic at indexing everything connected to the internet, it's possible to find files that are exposed accidentally and contain critical information for anyone to see.

KeePassX, 1Password, and LastPass are effective against keyloggers, phishing, and database breaches, but passwords managers rely on the operating system's clipboard to securely move credentials from the password vault to the web browser. It's within these few seconds that an attacker can dump the clipboard contents and exfiltrate passwords.

With a simple social engineering trick, sudo passwords can be captured in seconds without the target's knowledge. The passwords can then be saved to a file or exfiltrated to another computer on the network.

In the world of technology, there's often a trade-off between convenience and security. The Java Remote Method Invocation is a system where that trade-off is all too real. The ability for a program written in Java to communicate with another program remotely can greatly extend the usability of an app, but it can also open up critical vulnerabilities that allow it to be compromised by an attacker.

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.

The microphone in a Windows computer is accessible to most applications running on the device at all times and completely without security limitations. Information gathered from recorded audio conversations taking place in the surrounding area of a compromised computer can be used for social engineering, blackmail, or any number of other reasons.

This guide is written for anyone who is practicing his penetration skills using the Metasploitable 2. The problem that we are facing here is that we have to penetrate to Metasploitable 2 and when this happens we understand that we are not logged in as root but as a user with less privileges!

Welcome back, my hacker novitiates! If you have been following this new Snort series, you know that Snort is the world's most widely used intrusion detection/protection system. Now a part of the world's largest network equipment company, Cisco, it is likely to be found everywhere in one form or another. This makes a compelling argument for learning how to use it, as it will likely be a necessity in any security-related position.

WPA Enterprise is widely used in large corporations as it offers individual and centralized control through a server that authenticate the users (RADIUS server). In this tutorial I will show you how to break the barrier and obtain the user credentials.

Today, I want to share a tutorial on one of the most useful but old methods which you could use to hack websites, that is using the Dot net nuke (DNN) vulnerability . I know some of you already know about this method.

Welcome back, my hacker novitiates! As you know by now, the Metasploit Framework is one of my favorite hacking tools. It is capable of embedding code into a remote system and controlling it, scanning systems for recon, and fuzzing systems to find buffer overflows. Plus, all of this can be integrated into Rapid7's excellent vulnerability scanner Nexpose.

Welcome back, my rookie hackers! Most often, the professional hacker is seeking protected information from the target system or network. This might be credit card numbers, personally identifiable information, or intellectual property (formulas, plans, blueprints, designs, etc.). Most of my Null Byte guides have been focused on getting into the system, but this only begs the question—"what do I do when I get there?"

Welcome back, my fledgling hackers! A short while ago, I did a tutorial on conducting passive OS fingerprinting with p0f. As you remember, p0f is different from other operating system fingerprinting tools as it does not send any packets to the target, instead it simply takes packets off the wire and examines them to determine the operating system that sent them.