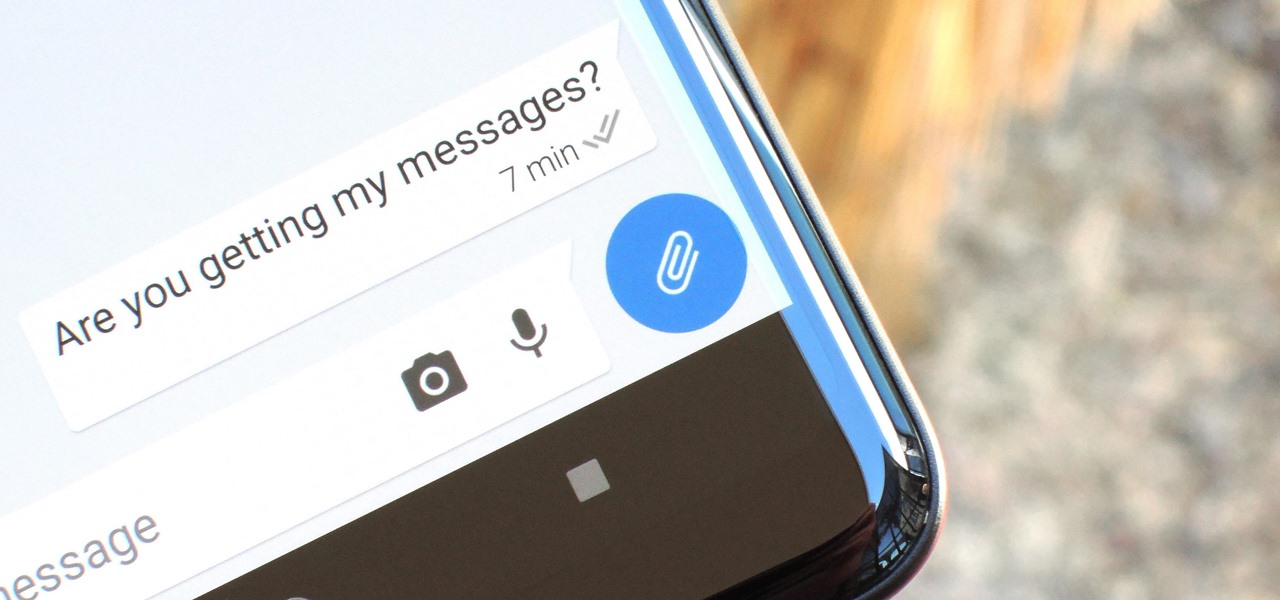
It took many months of cries from all around the internet—and a particularly large groan from an ex-Lifehacker editor-in-chief—but Apple has not only acknowledged the existence of its iMessage problem, it's promising a fix.

In Minecraft, many people enjoy "Faction" aka "Raiding" multiplayer servers for their unique gameplay and survival aspect. Plus, it's always fun when you find a chest full of somebody else's free stuff.

Spend an hour with Oracle PL/SQL expert Steven Feuerstein and explore the code-testing challenges facing PL/SQL developers. He will demonstrate how the new Quest Code Tester for Oracle dramatically simplifies testing because it:

Working with Oracle, odds are you may, on occasion, need to build an Oracle database from MySQL. Happily, this DreamCoder tutorial will walk you, step by step, through the process. To learn how to build an Oracle database from MySQL data, take a look!

If you'd like to have access to all your files at home without the hassle of spending money on expensive file hosting services or installing foreign software on your computer that could potentially harm it? Well Google has the answer for you, taking over the world one more computer at a time! In this video you will learn how to use your Gmail account and a Gmail Drive shell Extension to gain access to your files from any computer regardless of location!

Welcome to a tennis lesson from FuzzyYellowBalls, the the best place to learn how to play tennis online. Our free video tennis lessons teach you how to play the game in a new way that combines technical analysis, visual learning, and step-by-step progressions.

How to Watch Hulu on your Xbox 360. The problem is HULU doesn't look good on some old PCs. Fix this by running it on your TV or projector. This uses the program PlayOn to run Hulu through your XBOX 360. This will tie it into your Media Center. This will make YouTube, Hulu and Netflix on your XBOX video game console. Go to Video Library and access you PlayOn server.

In this tutorial Mike Lively of Northern Kentucky University shows you how to get started with Wireshark. Wireshark is a network protocol analyzer for Unix and Windows. It is used for network troubleshooting, analysis, software and communications protocol development.

Windows 10 passwords stored as NTLM hashes can be dumped and exfiltrated to an attacker's system in seconds. The hashes can be very easily brute-forced and cracked to reveal the passwords in plaintext using a combination of tools, including Mimikatz, ProcDump, John the Ripper, and Hashcat.

Most companies have services like employee login portals, internal-only subdomains, and test servers they would prefer to keep private. Red teams and white hat hackers can find these obscure and often vulnerable services using a tool designed to help protect users from fraudulent certificates.

Hackers rely on good data to be able to pull off an attack, and reconnaissance is the stage of the hack in which they must learn as much as they can to devise a plan of action. Technical details are a critical component of this picture, and with OSINT tools like Maltego, a single domain name is everything you need to fingerprint the tech details of an organization from IP address to AS number.

After receiving many requests for the feature, Signal introduced read receipts last year to its mobile apps. However, some users don't like the idea other people knowing when they've read messages. Luckily, Signal lets you disable this feature and reclaim a little privacy.

JavaScript is one of the most common languages used on the web. It can automate and animate website components, manage website content, and carry out many other useful functions from within a webpage. The scripting language also has many functions which can be used for malicious purposes, including stealing a user's cookies containing passwords and other information.

Internet Relay Chat, or IRC, is one of the most popular chat protocols on the internet. The technology can be connected to the Tor network to create an anonymous and secure chatroom — without the use of public IP addresses.

If you maintain a digital library of your favorite movies, Plex is the perfect solution for bridging the gap between your computer and your mobile device. All you have to do is install the server program on your Mac or PC and point it to the folder where you store your movies, then you can use the Plex app for Android or iOS to watch the movies on your phone or tablet.

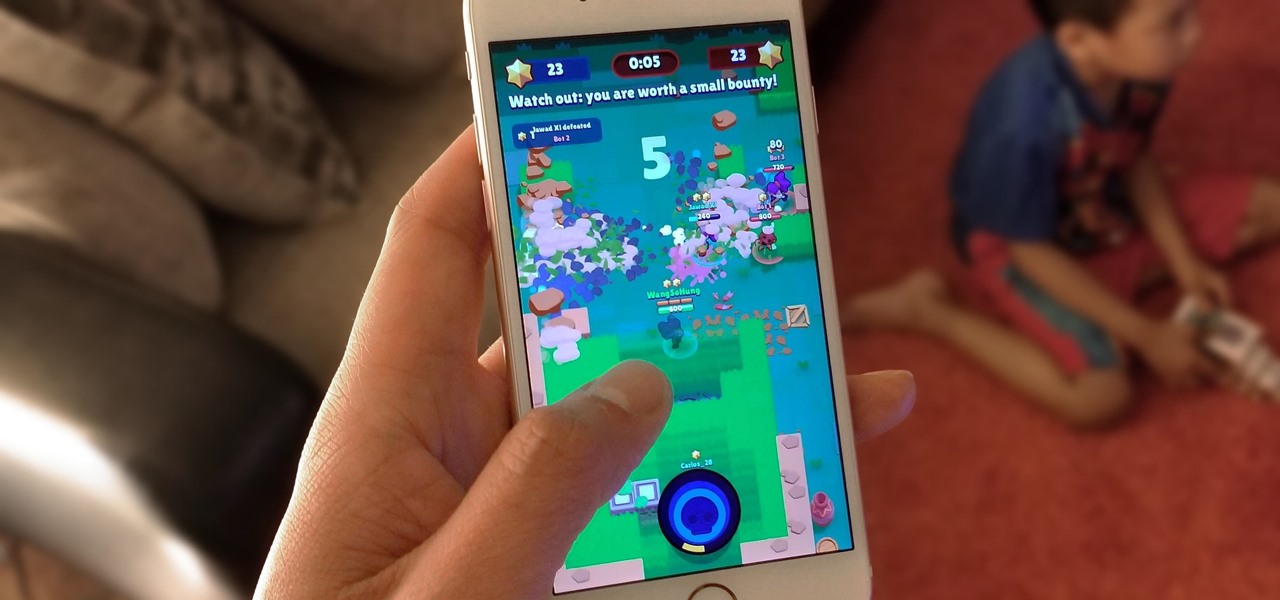
Supercell's highly anticipated Brawl Stars has soft launched in Canada, with gamers worldwide salivating at the prospect of a full debut around the corner. Unbeknownst to many, this game can be played on your iPhone right now, regardless of where you live.

Despite a round of updates to Pokémon GO that patched and eliminated location spoofing, the game still has a difficult time dealing with the most hardcore cheaters. Like weeds on a grassy lawn, third-party bot makers still remain the biggest thorn in Niantic's side and continue to thrive despite the developer's best efforts to root them out. While the latest updates have blocked users from running modded versions of the game, like Pokemon GO++, that feature built-in joysticks to move your pla...

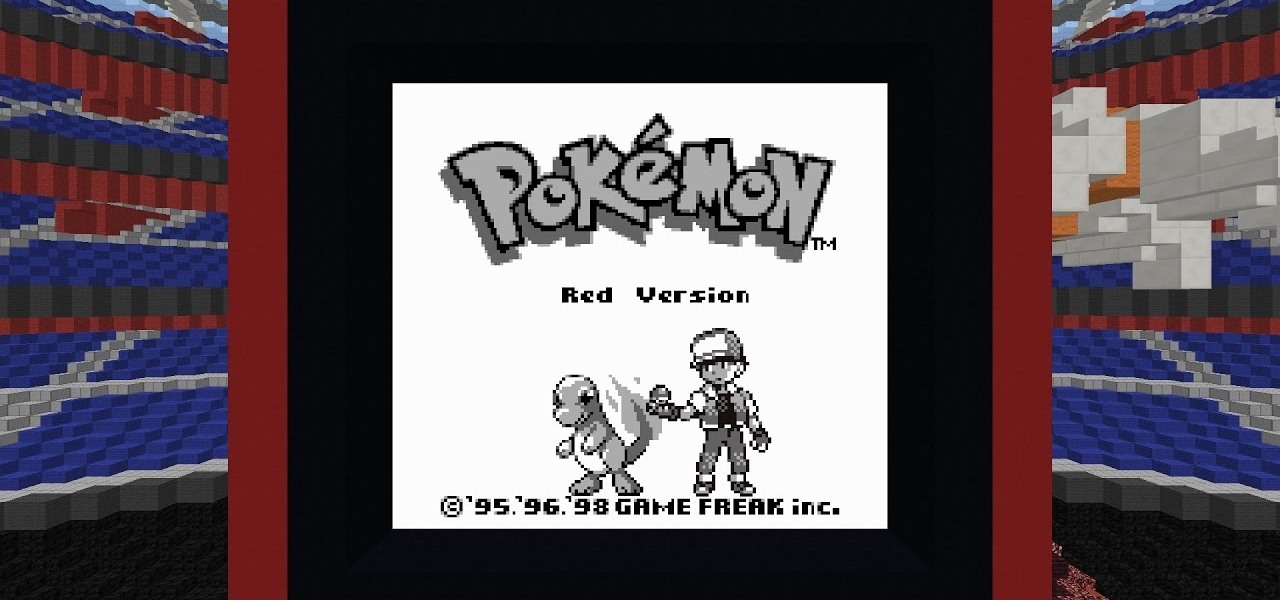
Reddit user Mr. Squishy recreated the entire Game Boy Pokémon Red Version game in Vanilla Minecraft, i.e., a Minecraft server without gameplay modifications. Instead of using mods, he used 357,000 commands blocks—blocks that execute commands in the popular sandbox game. How long did it take him? Almost two years.

The Stagefright exploit, which allowed for malicious code to be embedded in files on your device, is now very real in the form of Metaphor. Developed by software research company NorthBit, Metaphor is their implementation of exploits to the Stagefright library, and when executed, can access and control data on your device.

Alright, this will be my first tutorial in C. Note that this guide is written for Linux.

NMAP is an essential tool in any hacker's arsenal. Originally written by Gordon Lyon aka Fydor, it's used to locate hosts and services and create a map of the network. NMAP has always been an incredibly powerful tool, but with it's newest release, which dropped mid-November of last year, they've really out done themselves.

Hello fellow Null-Byters! This is my first post so please be respectful and constructed criticism is much appreciated. I am no professional, however I believe that it is important to understand technologies before you go poking at them and trying to break them, I therefore decided to make this series. In this "tutorial" we are going to setup a web server with php and mysql. I will be doing this with a raspberry pi because a pi is quite versatile.

Welcome back, my fledgling hackers! Over the years, we have examined multiple ways to own, exploit, or compromise a system. On the other hand, we have not spent a lot of time on denial-of-service (DoS) attacks.

Welcome back, curious hackers! In today's tutorial, we will be diving deep into the manipulation of Google Operators, commonly referred to as "Google Dorks" in order to access Surveillance Cameras and other control panels.

If you're a Mac user with an Android phone, some apps on your computer aren't very useful, such as Messages, which is meant to work and sync with iOS devices. But now, thanks to MDRS, LLC, using the Messages app on your Mac with an Android phone is now possible and easily achievable. Plus, we've got 50 promo codes to give away for a free year of service!

It's really amazing how much you can do with root access on an Android device. From various themes to porting exclusive funtionality from other devices, the power of Superuser privileges is truly awesome.

When browsing the web, you may not be quite as anonymous as you think, especially if you are using public WiFi. The easiest way to stay as anonymous and safe as you are going to get, is to use a VPN (there are a number of great free ones). In this tutorial, we will show you how to set up a VPN on Android, and how this protects you.

Have you ever been called a "noob" or "eZ" after some person kills you? have you ever said "you hack" or "you suck" after getting your butt kicked by another player? this wont ever have to happen again. It is actually possible to be very good at PvP in Minecraft, and you can also be good at it. Now, it is your turn to win in every battle you fight in Minecraft PvP.

This time it's serious. Really. The largest web security vulnerability of all time went public on Monday, April 7th, 2014, resulting in widespread panic throughout the Internet as system administrators scrambled to secure their websites from the OpenSSL bug known as Heartbleed.

For a photo- and video-sharing app based around privacy, Snapchat sure has a lot of security holes floating around. At one time, you were able to take screenshots of Snapchats in iOS 7 without the sender knowing, which is something that you can still do on rooted Android devices.

All of my hacks up to this point have been operating system hacks. In other words, we have exploited a vulnerability usually in an operating system service (SMB, RPC, etc.) that all allow us to install a command shell or other code in the target system.

If you have an iPhone or an iPod Touch then you probably think that the only places you can listen to your MP3 files are on your laptop, your i-gadget of choice, and your car. But in reality anything that you can groove to on your iPhone or iPod Touch can be listened to - and transferred to - your PlayStation 3.

In this video, we learn how to pull a compilation of computer pranks on a friend. The first trip is a mouse prank where you will open up the control panel and find the mouse settings. From here, you can switch the buttons from left to right and change the speeds of the mouse. Next, you can do network pranks by running cmd.exe as administrator. Then, go and see who is on the network and type in "msg /server:(ip address) and message". You can also do a ghost typing prank, which you will create ...

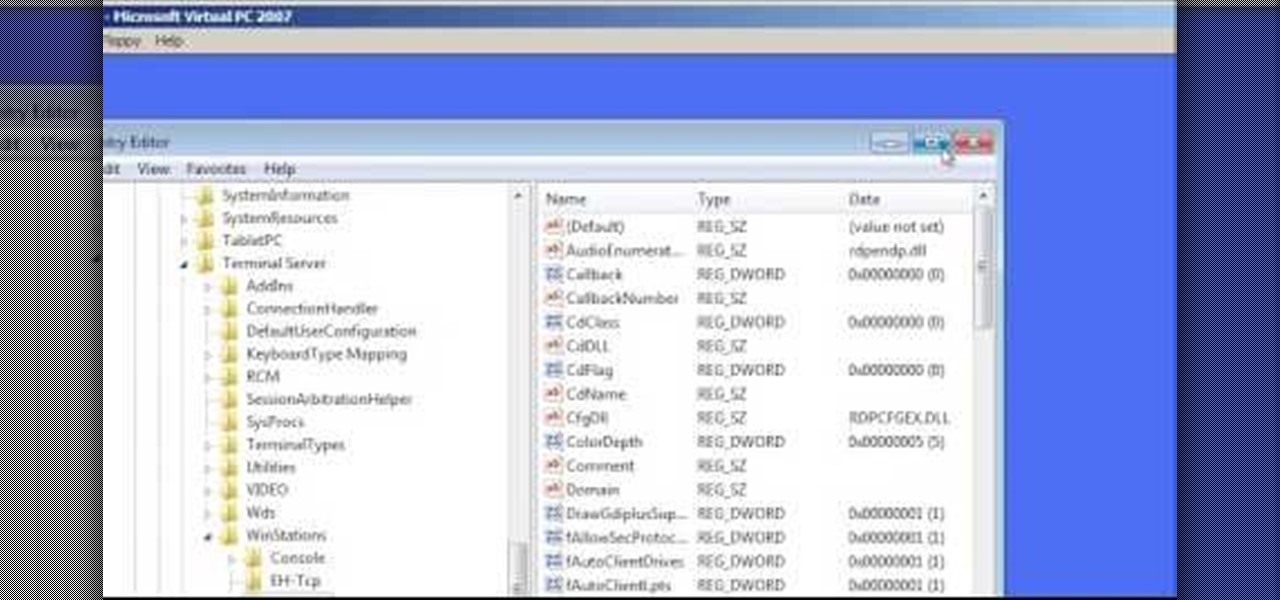
In this Computers & Programming video tutorial you will learn how to change the default Windows Remote Desktop port. It is actually a registry hack. You can check the IP address of our machine by typing ipconfig into the cmd prompt. For hacking into a machine, you should have created a user for the machine and allowed remote desktop to that user. Open up the remote desktop and type in the IP address and it will ask for a login. To hack the registry, click start and type in ‘regedit’ . now go ...

Enabling Telnet in Windows Vista is a little bit more difficult than its predecessors but it still can be done. This video will demonstrate exactly how to enable Telnet in Windows 7 and Vista.

VNC stands for Virtual Network Computing. It is remote control software which allows you to view and fully interact with one computer desktop (the "VNC server") using a simple program (the "VNC viewer") on another computer desktop anywhere on the Internet. The two computers don't even have to be the same type, so for example you can use VNC to view a Windows Vista desktop at the office on a Linux or Mac computer at home. For ultimate simplicity, there is even a Java viewer, so that any deskto...

In this tutorial, Mike Lively of Northern Kentucky University gets you started in getting the Adobe Air Content Management System up and going.

This new episode of Full Disclosure shows you how to use a SSH Tunnel to secure your data when you are on an untrusted LAN (ex. Coffee Shop, School's network, or Defcon). Furthermore, you can use the SSH Tunnel to bypass the LAN's internet filters. The SSH tunnel protocol works by encapsulates your data into an encrypted payload and transmitting it to the SSH Server which is setup on a trusted LAN.

Karma is an idea that exists in the Hindu, Buddhist, Jain, and Sikh religions, which simply holds that all actions have consequences. In other words: karma’s not a bitch, but you might be. If so, here’s how to start sending the world good vibrations. Learn how to store up some good karma for yourself.

There are countless ways in which a talented and trained programmer and tech pro can earn a lucrative living in an increasingly data-driven age — from writing and creating apps and games to working for a cybersecurity firm or even the federal government.