While SSH is a powerful tool for controlling a computer remotely, not all applications can be run over the command line. Some apps (like Firefox) and hacking tools (like Airgeddon) require opening multiple X windows to function, which can be accomplished by taking advantage of built-in graphical X forwarding for SSH.

With an inconspicuous Android phone and USB flash drive, an attacker can compromise a Windows 10 computer in less than 15 seconds. Once a root shell has been established, long-term persistence to the backdoor can be configured with just two simple commands — all while bypassing antivirus software and Windows Defender.

The new iPhone XS and XS Max have more issues than just their hefty price tags. Customers have only had the phones for a handful of days, but some are already complaining of cellular and Wi-Fi connectivity issues on both models. If your experience is the same on your XS or XS Max, there are steps you can take to get your iPhone reliably back online.

Backdooring a powered-off MacBook is easy when a few minutes of physical access is allowed. That attack works well if the hacker also shares a Wi-Fi network with the victim, but this time, I'll show how to remotely establish a connection to the backdoored MacBook as it moves between different Wi-Fi networks.
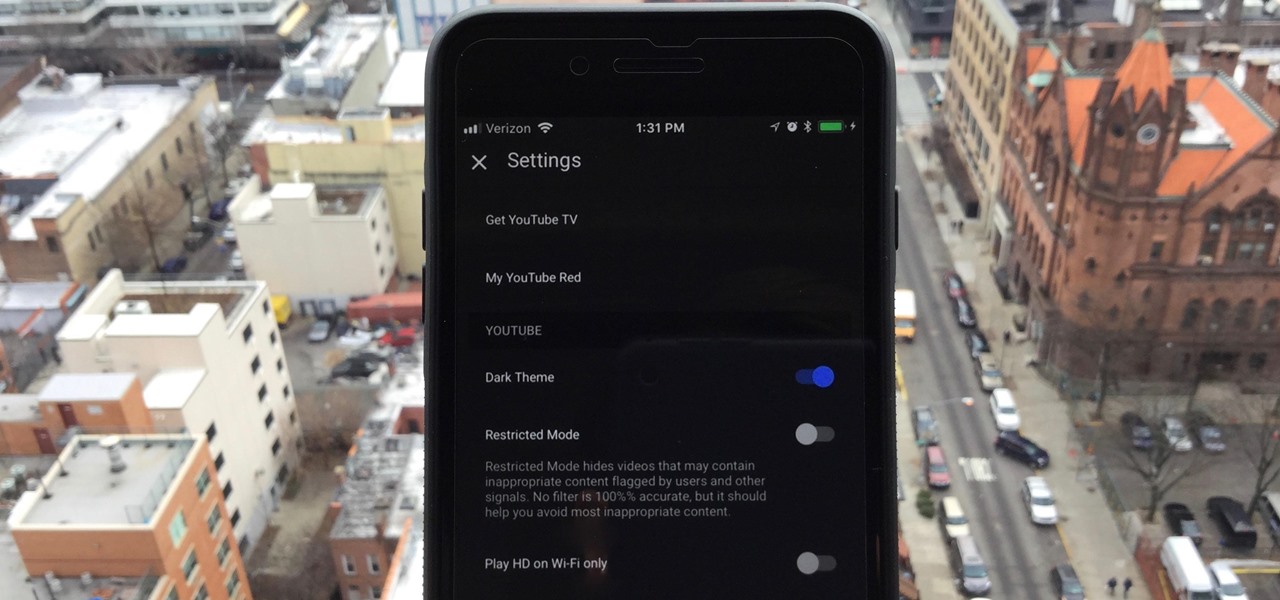
One of the downsides to iOS is the lack of a true dark mode. While Apple has offered a workaround, third-party developers have taken it upon themselves to implement dark themes in their apps. While big names like Twitter and Reddit have led the charge for some time, it appears YouTube is the next app to join the party.

Telegram routinely boasts about its secure messaging for truly private conversations between two parties. However, default cloud chats in Telegram are only encrypted between client and server, not client and client, which means you have to be a little proactive in making sure your private conversations on Telegram are really private.

Welcome back, my greenhorn hackers! Over the years, I have written many articles here on Null Byte chronicling the many the hacks of the NSA, including the recent hack of the Juniper Networks VPN. (By the way, my speculation in that article has proven to be correct. The NSA did embed a backdoor on those devices.)

Welcome back, my greenhorn hackers! Many new hackers come from a Windows background, but seldom, if ever, use its built-in command-line tools. As a hacker, you will often be forced to control the target system using just Windows commands and no GUI.

Not too long ago I showcased ReCam, a free app that lets you schedule recordings and use your Android device as a security or spy camera of sorts. While useful, this app required you to schedule when to record in advance, resulting in you possibly missing the footage you intended to record (assuming your scheduling wasn't as on-point as you wished).

Welcome back, my novice hackers! In this continuing series on Metasploit basics, let's next look at a module that many aspiring hackers find useful—autopwn.

The internet is forever. When you put something out there, it can easily be re-shared, floating from server to server indefinitely with no way of taking it back. It's a scary thought when you consider that a young adult's grandchildren will one day have access to their drunken party pics.

Welcome back, my aspiring hackers! Those of you who use Windows in a LAN environment understand that Windows machines can share directories, files, printers, etc. using "shares." This protocol dates back to the 1980s when the then dominant computer firm, IBM, developed a way for computers to communicate over the LAN by just using computer names rather than MAC or IP addresses.

Welcome back, my novice hackers! Before we try to attack a website, it's worthwhile understanding the structure, directories, and files that the website uses. In this way, we can begin to map an attack strategy that will be most effective.

Welcome back, my novice hackers! There are SOOOO many ways to hack a system or network, which means you need to think creatively in order to be successful.

Welcome back my fellow hackerians, Today i'm going to tell a bit more about the famous DDOS thing. And on top of that we're going to DDOS a website.

With more people joining the internet scene each day it's important that it's security is.. well it has to be good. Of course everything can be hacked and that's the way hackers work. They know there IS a vulnerability but they don't don't know the rest. in this article i'll try to explain the big difference between HTTP and HTTPS

I've had this idea in my head for almost a year now. I knew what I wanted to do, but wasn't sure if it would work. After a long time of armchair-engineering, I decided that the best way to test my idea was with a soldering iron and a screwdriver.

A few days ago, Russian hacker Alexy Borodin found a way to get free in-app purchases on an iPhone or iPad. In-app purchases include things like items and power-ups for iOS games, as well as subscriptions and "premium" memberships for certain apps.

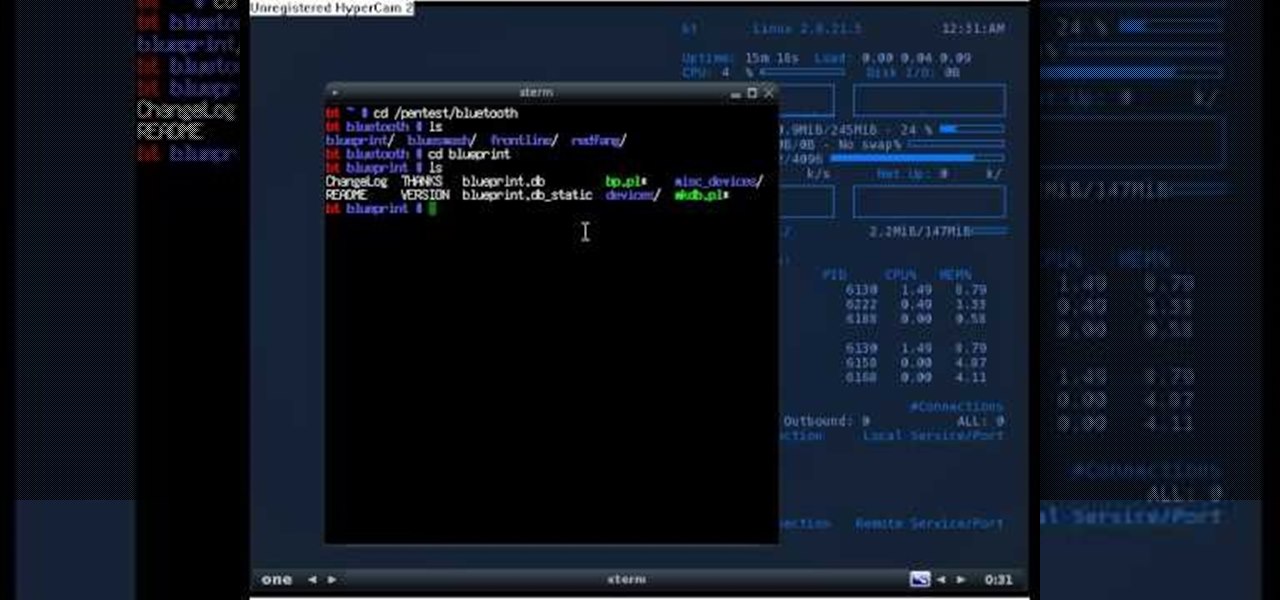
If you're new to the Bluetooth hacking world, here's a little background on using Linux BackTrack to hack a Bluetooh device: Linux Backtrack is a Live DVD device that offers security tools - like password crackers - that allow you penetrate networks.

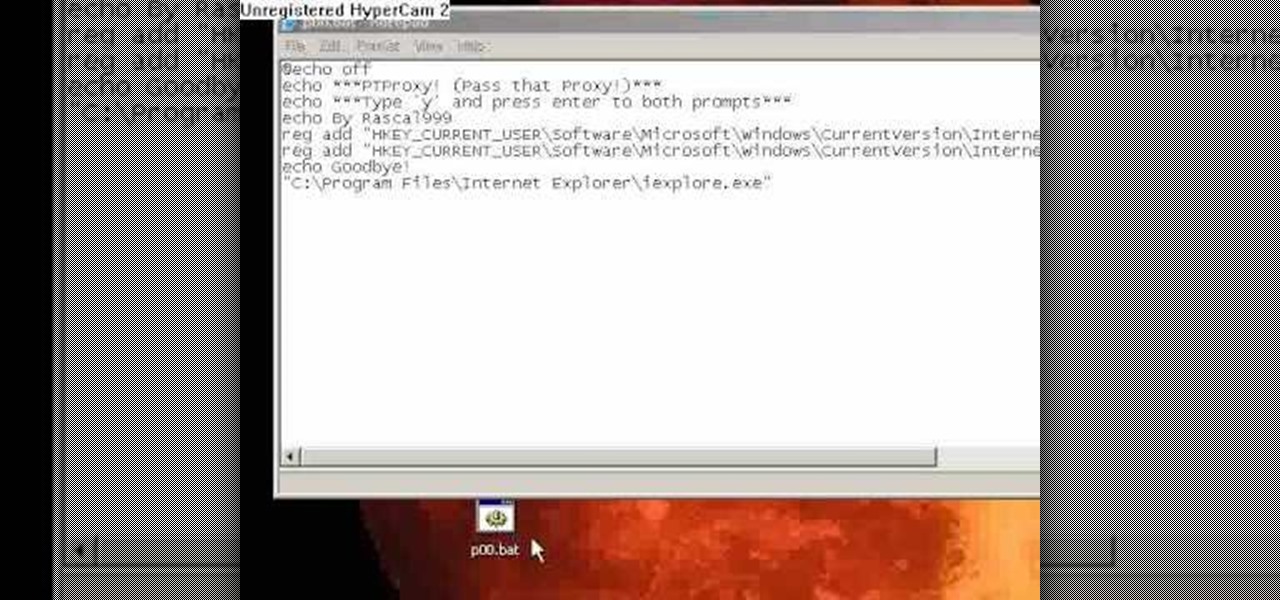
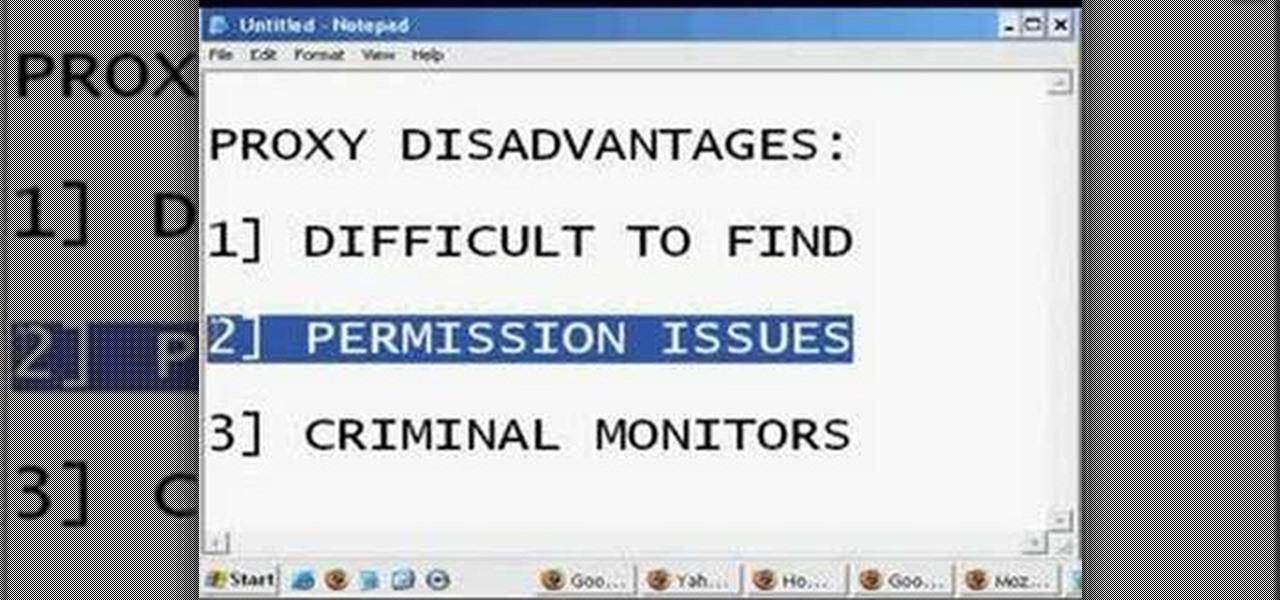
Different ways of using a proxy bypass to access blocks sites is shown with ease in this video. Many places explained to be blocked with internet security such as libraries and schools. Using a search engine such as Google you need to search for a proxy site. After a proxy site has been found you will use it to access the blocked websites through another servers internet provider. The narrator explains that proxies are just a way to bypass internet blocks by avoiding using the blocked compute...

In this tutorial, we learn how to configure Outlook 2007 to work with Gmail. First, go to the start menu and then open up Outlook. From here, go to tools and then options. After this, go to the mail setup tab and then click e-mail accounts. Then, click on "new" and then next. Enter in your information in the blank boxes on the screen. Then, enter in your e-mail address and make sure the server is not checked on this screen. From here, you will continue to go through the wizard until it's comp...

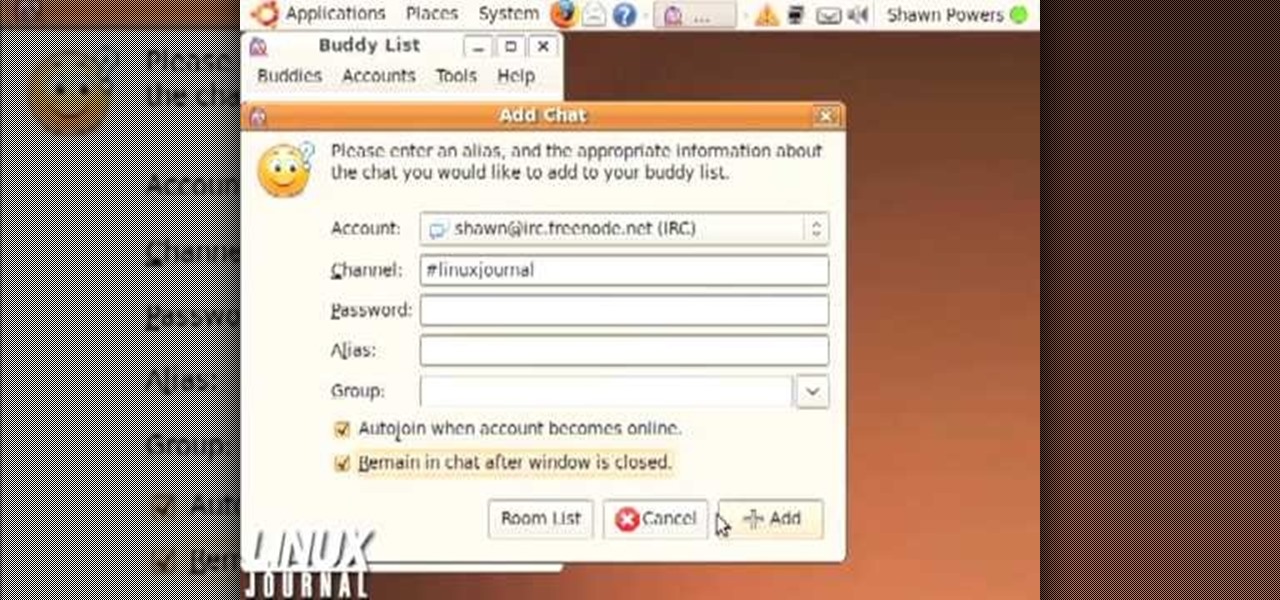
This video shows how to enter an IRC chat with a program called Pidgin, which is normally an instant messaging client. First, you should open Pidgin and open the protocol IRC, selecting or creating a username and changing the server to irc.freenode.net in order to connect to the Linuxjournal channel. After connecting to the channel, wait until you are connected. At this point, you should still not be able to see anything, so you have to go to "Add Chat" and join a channel, in this case #Linux...

In this tutorial, we learn how to change your IP address in five different ways. First, go to your security settings and clear all cookies, then start to browse the internet with private browsing from your internet browser. You can change your IP address by going onto your internet browser and changing the LAN settings. Type in your address and port, then bypass the proxy server. Next, go to options and then advanced on your browser. Type in the proxy and port, then click where it says no pro...

In this video, we learn how to bypass WebSense at school using an http tunnel. First, open up Internet Explorer, then type in http tunnel and go to the website. Download the first link to your computer. Next, start the program and click on "free service". Now, open up the browser again and go to "internet options". Once you are on this, go to "connection", then "lan setting". Check to use a proxy server, then click "advanced", then enter in "http 127.0.01 port 1080". Click "ok", then exit out...

In this tutorial, we learn how to use Microsoft SharePoint to view Acrobat 9 reviews. First, go to the comment bar and click "send for shared review". In this wizard, click internal and then click next. Then, click SharePoint workspace, then type in the URL to the server, then click "get workspaces" and you now may have to enter in your username and password. Now you will have to choose your workspace and document library. After this, click on next and click if you want to have it attached fo...

In order to find out if an email is a scam, you should avoid clicking on any links in that are in any emails. The links that are attached to emails, in this manner, usually have cloned the website of the institution where you do your banking. The link will look similar to your banking institutions site. Do not enter any of your personal information in emails in this fashion. Your bank will not contact you in this way.

Seems like everybody's blogging on the web these days. If you don't want to be the last one to the party, CNET shows you how you can get started with your own blog. If you know how to use a web browser, you should have no problem! Most bloggers use blogging services like Blogger or WordPress. Other sites like MySpace also let you blog. Or if you want, you can set up a blog on your own server. Learn all about getting started.

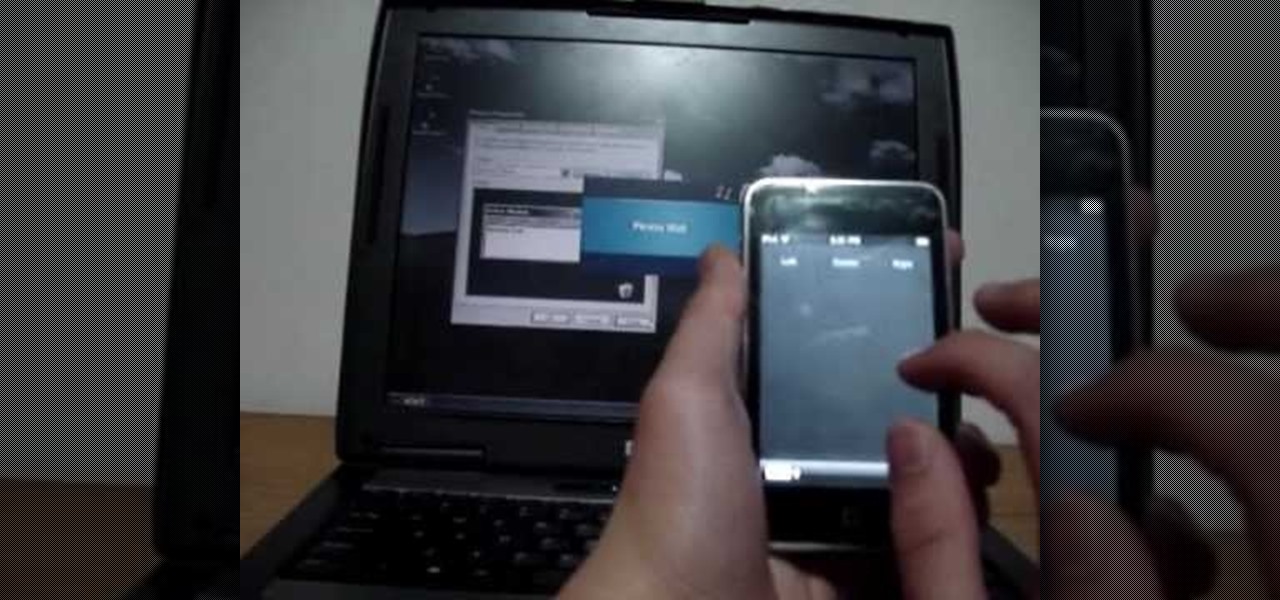
In this video, we learn how to control your Windows PC with an iPod Touch or iPhone. First, go online and search for 'Logitech touch mouse server', then download and install this software. Now, go into the software and launch it on your phone. You should now be able to use your computer and your phone simultaneously as long as you have a wireless connection. Now, you will be dragging the mouse on your phone and it will be working on your computer. You will have full functions while using your...

This video tutorial is in the Computers & Programming category where you will learn how to set up an FTP connection using Firezilla. Open up your filezilla program. On the top left, click on the file menu button, and select 'site manager'. In the window that opens up, select 'new folder' and give it a name. Now create a site to store in this new folder. Click on 'new site' and name it. Now on the right hand side, enter the host and the port. The default port is 21. Under server type, select F...

In this tutorial, we learn how to stream web content to your PS3. If you want to do this for free, you will go to PS3 Media Server. Once on this site, you will download their player, then you will be able to stream content from your computer straight to your PS3. This will give you real time audio and direct streaming of movies. You can do this one other way, which will cost you $49.99, the website you will visit is PlayOn. When you download this, you will be able to stream advanced content t...

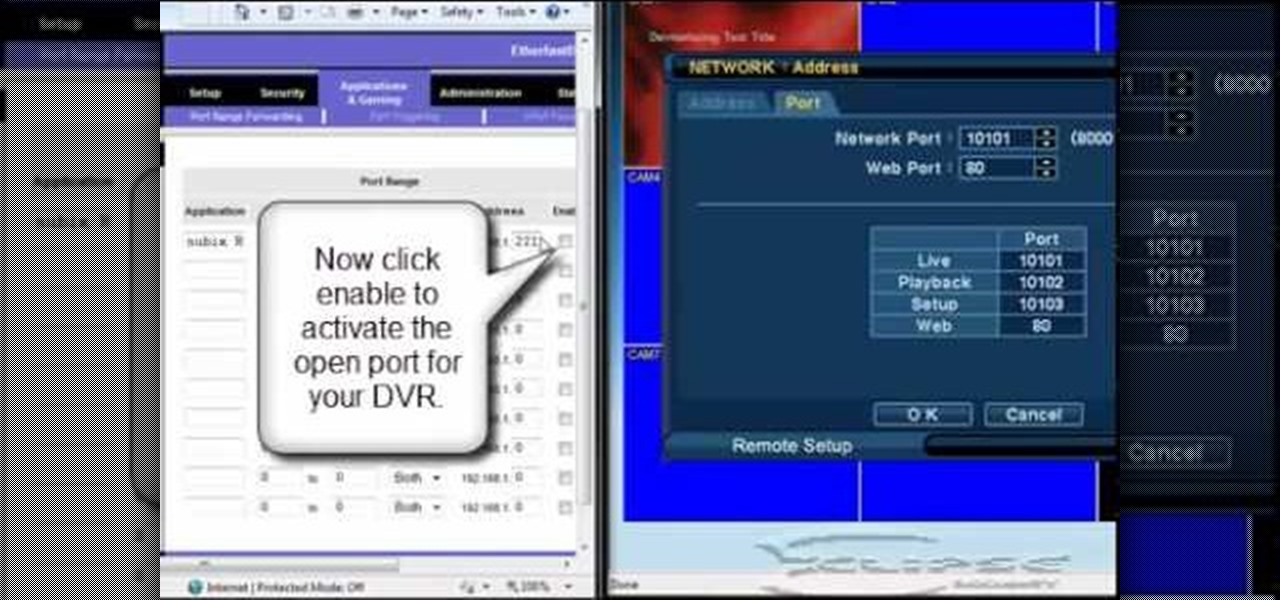
In this tutorial, we learn how to open ports on a Linksys router for your DVR. First, make sure your internet is connected and your DVR is connected to Linksys. Next, log into your Linksys router online and set up your DVR to the "DHCP" section. When you have the information from this, enter this information on your DVR so it has the correct server name. Make sure the IP and other information displayed on your Linksys page is the same as the setup on the DVR page. When finished, change your p...

In this video, we learn how to reset your wireless router. You can use this if you are getting the "server can't be found" error, and it will work most of the time. First, grab your router and unplug the electricity and DSL plugs that are in the router. They will be round and look like post, and shouldn't be hard to find. After you unplug it, plug it back in after about 30-45 seconds. This will reboot your router, so it will most likely fix the problem you are experiencing. You should be able...

In this tutorial above, you'll be finding out how to quickly set up IMAP in order for it to run with your Gmail account. Now first thing is first, IMAP has nothing to do with apps or anything else that is Apple. What it stands for is Internet Message Access Protocol. And what it does is that it's basically email but differs from the other email retrieval program, POP. It keeps email messages in the server while POP deletes them. So check out how to set it up with your Gmail account today! Goo...

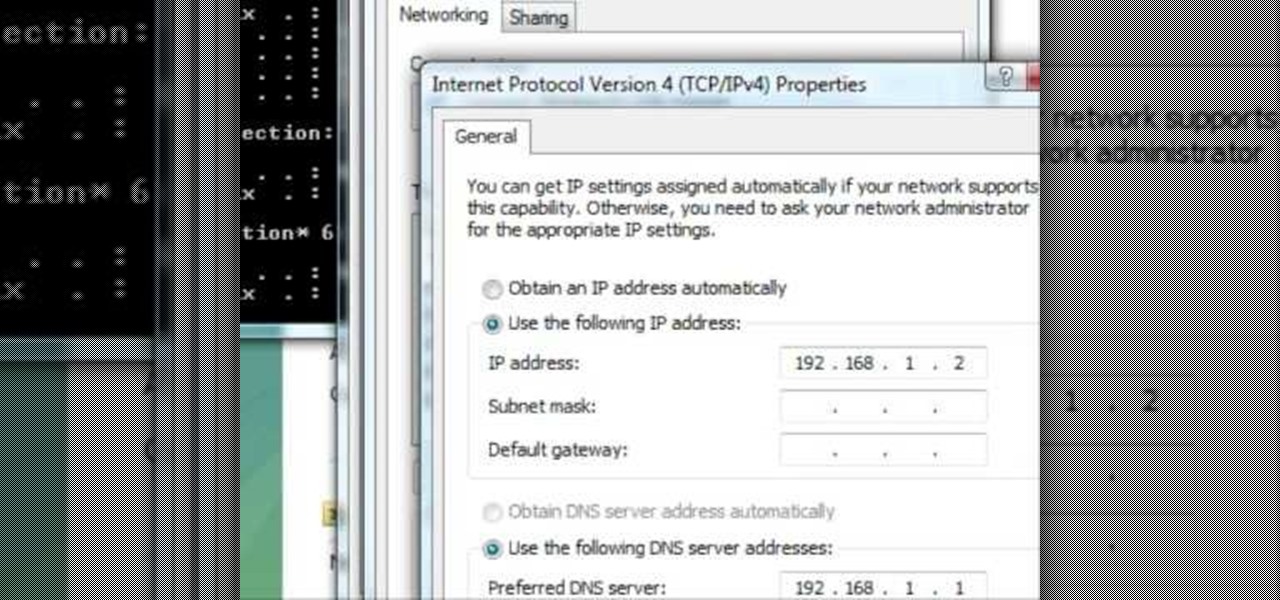
In this tutorial, we learn how to change an IP address in Windows Vista. First, open up cmd on your desktop and a new window will pop up. When the black window comes up, type in "ipconfig". You will now see your IP address, leave this window open and open up the control panel. Once in the control panel, click "view network status and tasks", then click on "view status". After this, click "properties" then click "internet protocal version 4" and click on "properties" again. Now, type your IP a...

In this Software video tutorial you will learn how to setup email in Microsoft Office Outlook 2007. Suppose you have a Yahoo email id and you want it in Outlook, go to tools > account settings > email > new and fill out the details. Then check the box next to ‘manually configure server settings’ and click ‘next’. In the next box, choose the 1st option and click ‘next’. To get the information for filling up in the next box, go to the Yahoo page shown in the video and copy and paste...

This video shows us the method to use iPad as a touchscreen monitor for your Mac. You have to use iDisplay available on app store. Start the application on your iPad and Mac. Tap the server on your iPad and on the Mac click 'Confirm' to connect it to iPad. Hit 'OK' on iPad. Now you can open a window on the Mac. You can drag the window out of the Mac screen on to the iPad. Now it will act as a touch screen. You can use all the touch screen features of iPad for this window. You can drag the win...

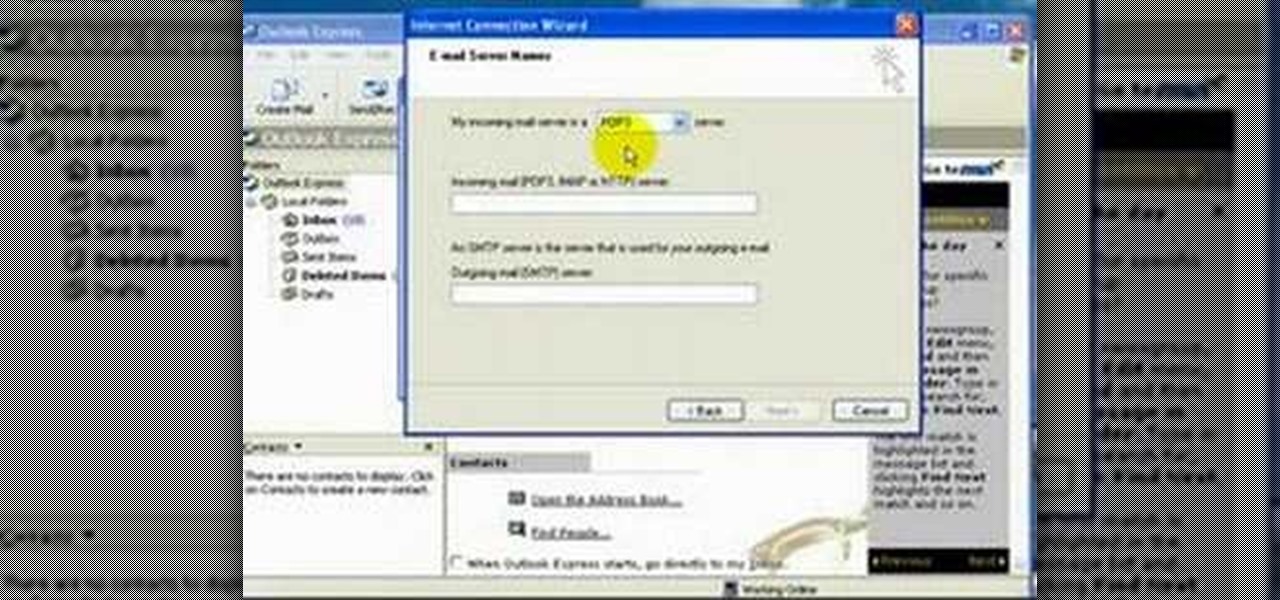
Carole Gallesie from Creative Media Web shows viewers how to set up a new account in Microsoft Outlook Express. Express is preferred because it is a scaled-down version of the popular email client and it is easier to navigate. From your Windows desktop, go to the start menu, all programs, and click on outlook express. When the program opens, look at the top of the page for the "tools" menu, select accounts, add, and mail. The new account wizard will then appear and will walk you through setup...

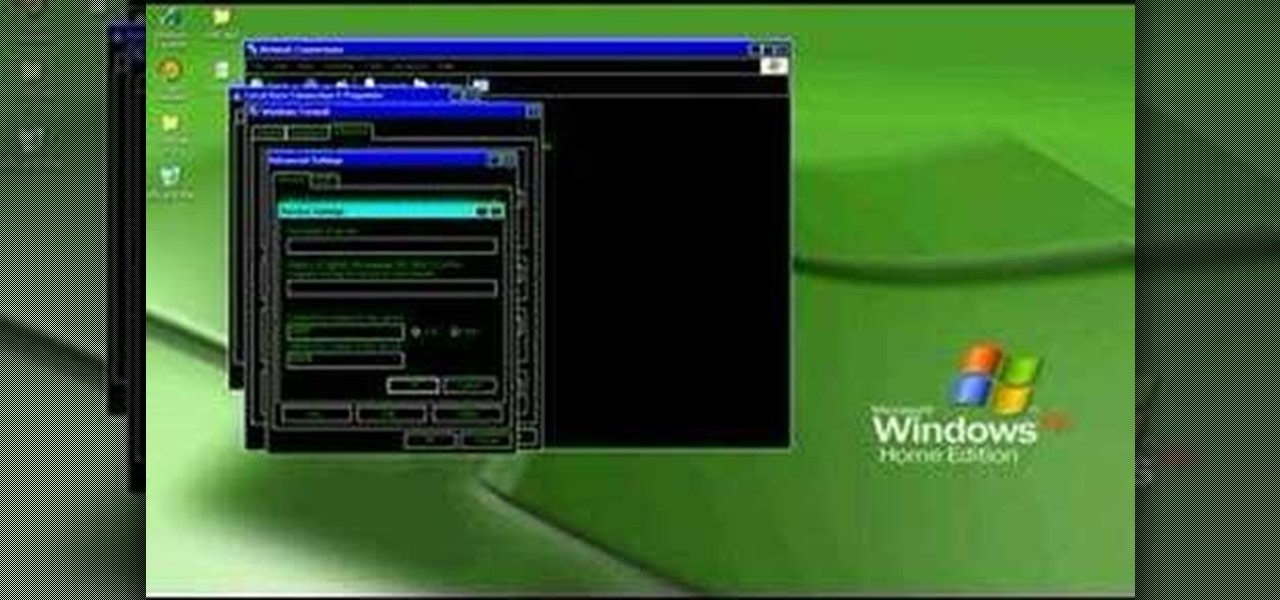
In this video tutorial, viewers learn how to open ports on a Windows XP computer. Begin by clicking on the Start menu and open Control Panel. Double-click on Network Connections and select your network connection. Right-click on it and select Properties. Click on the Advanced tab and click on Settings. Select the Advanced tab again. Click on your internet connection and click on Settings. Click Add and fill in the port information. Click OK. T forward a port, users need to go to their router'...

Brad Garland guides us through the process of sharing our media files so that they can be stored on a single computer in our home, and played on any computer that is connected to this computer with iTunes 9. Using this technique, he and his wife can not only play the music that's stored on the central computer via their laptops, but also copy the desired music and videos over to their laptops much like they would for an iPod. Brad explains that he does not include Podcasts in this process, be...

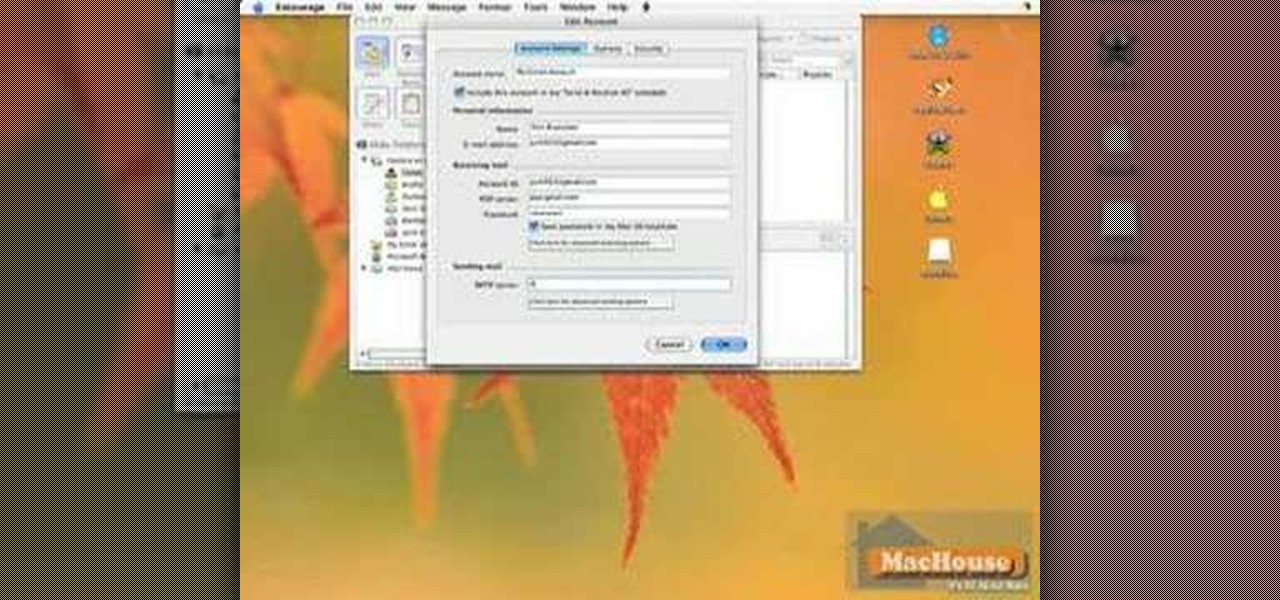
Log in to your account. Go to settings, then go to Forwarding and POP. Then, check in the box for enable POP for all mail. Next, save the changes. Then go back to the settings page and check the first box (to include the mail that has already been downloaded). Save your changes again. Next, select tools>account. In the box that pops up, select POP for the account type and hit OK. Name the account and fill in your email address and POP address. For the SMTP server, put in smtp.gmail.com. Then,...