How To: Fix videos not playing on your PS3 Media Server
If you're having trouble playing video files on your Playstation 3 from your media server this is a quick fix.


If you're having trouble playing video files on your Playstation 3 from your media server this is a quick fix.

How to set up your Playstation 3's (PS3) media server.

A short tutorial on how to view server resources usage using cPanel. This video is provided to you by Scandicsoft.
Microsoft Visual Studio 2008 is an integrated development environment that lets you develop websites, web applications, and web services. It requires a bit of computer coding to run (C#, Visual Basic, ASP, C++) and will work on any web server that supports Microsoft.
This video shows you how to use the Free Internet Chess server and the BabasChess client for it. This video covers some basics, and hopefully some of you who haven't tried FICS will find it beneficial.
Use an old PC that has been setup as a server to perform helpful tasks such as backing up computers on your network, storing media files in a central location, share one printer with every computers computer in the house.

SQL injection is a type of code injection that takes advantage of security vulnerability at the database level. It's certainly not the easiest form of hacking, but if you're serious about turning a website upside down then this is the way to do it.

If you've been watching the latest USA TV Series Mr Robot, you will have seen the Raspberry Pi used by Fsoeciety to control the HVAC system. OTW covers this very well here with his take on setup they may of used.

This is the first installment in a new series that I am calling "Hacker Hurdles." These are things, methods, techniques that make our job as hackers more challenging and difficult. Don't misunderstand me, these items don't make our task impossible, but rather more challenging and, therefore, more gratifying when we are successful. One of the most important new hurdles for hackers is DEP and ASLR. Data Execution Prevention (DEP) and Address Space Layout Randomization (ASLR) are designed to pre...

Welcome back, my tenderfoot hackers! As you know, DNS, or Domain Name System, is critical to the operation of the Internet. It provides us with the ability to type in domain names such as www.wonderhowto.com rather than the IP address. This simple service saves us from having to memorize thousands of our favorite website IP addresses. Instead, we simply type in a domain name to retrieve the website.

Welcome back, my aspiring hackers! Domain Name System (DNS) is one of those things we seldom think about unless it doesn't work. Then, it can be very frustrating when we attempt to navigate to a website and we get that frustrating error message.

Welcome back, my budding hackers! In my continuing effort to build your basic Linux skills for hacking, I want to show you how to build a secure "tunnel" to MySQL.

Welcome, my neophyte hackers!

Google is the biggest and best search engine on Earth, and if you are a webmaster and want your website to be a big success it would really behoove you to know as much about how it works as possible. The Google Webmasters series of videos and website were created to teach webmasters, SEO professionals, and others how Google works by answering their questions and giving them insights into how they can best integrate and utilize Google's functionality to improve their business. This video will ...

This instructional video shows you how to make a RSS ("Really Simple Syndication") feed using the free program RSS builder. RSS is a script that can be put up on a website that other users can subscribe to in order to get notified when the website gets updated. The xml code behind creating RSS feeds is explained. The code should be entered as shown and the file should be saved as "feed.xml" and upload it to a web server. Go to the URL mentioned, download and install RSS builder. Launch the pr...
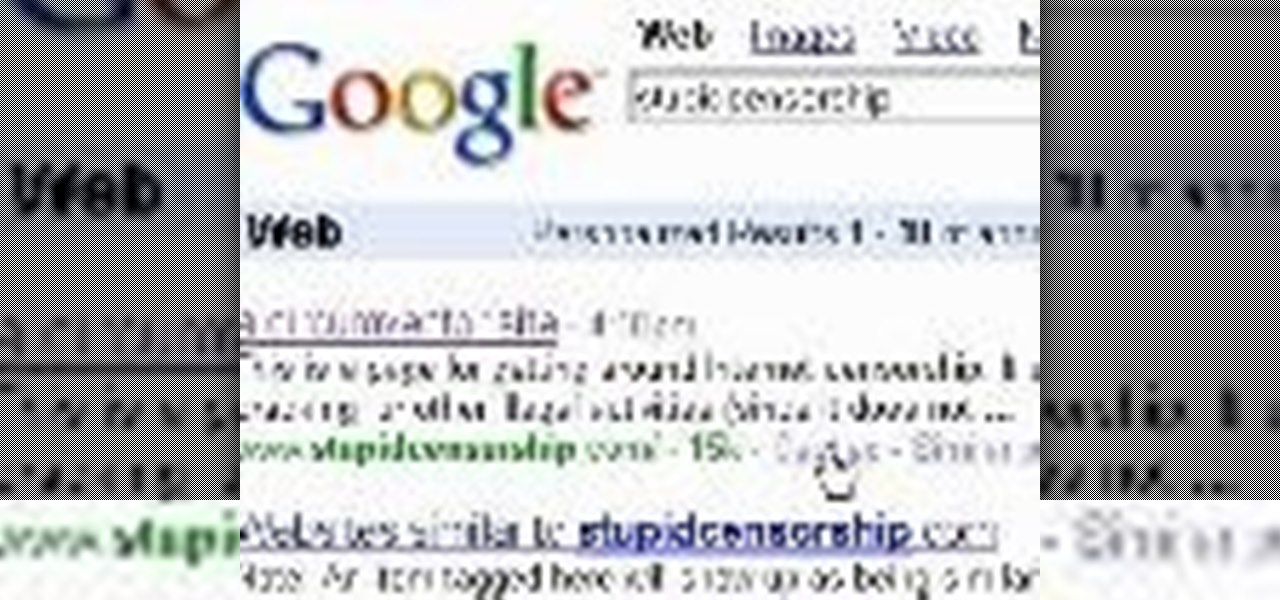
Are you using the Internet at a school, library, or some other place that blocks or restricts web access? Mom and dad still trying to protect you from online predators, even though you're more than old enough to be one yourself? Learn how to bypass proxy servers that block access to certain websites by watching this how-to video. In this case it's done to access Myspace but this method can be used with any blocked website. Follow along with this video tutorial and never get hindered by restri...
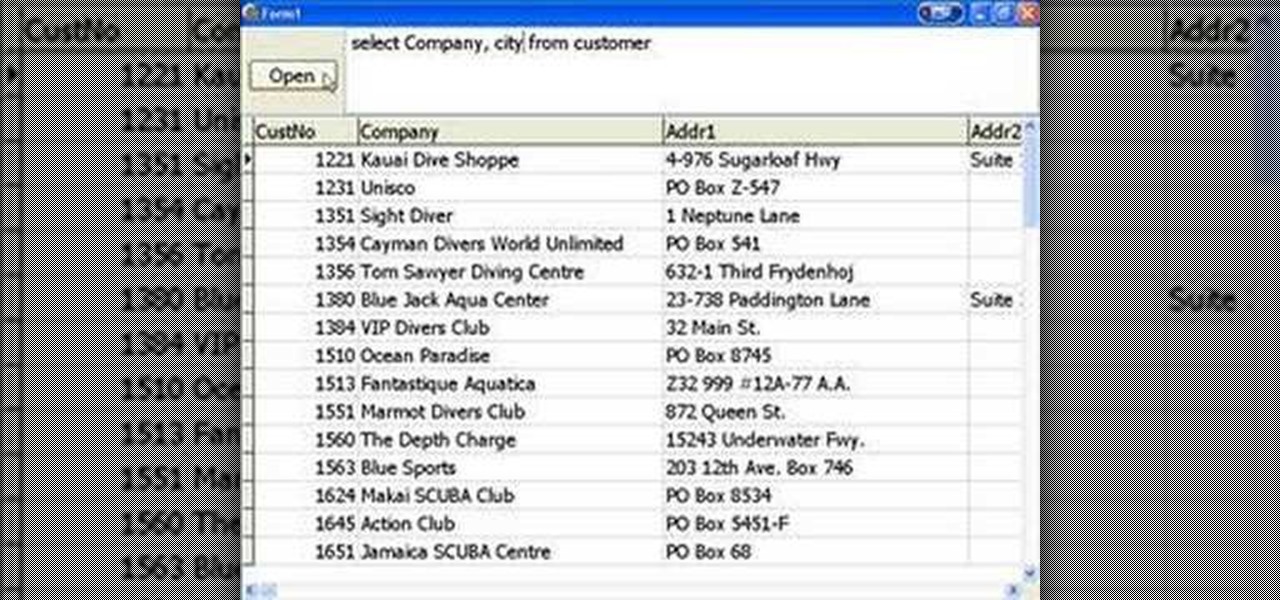
A tutorial on using SQL when programming GUIs in Delphi. Part 1 of 3 - How to Use SQL when programming in Delphi.

With the addition of the OpenSSH client and server in the Windows 10 Fall Creators Update, you no longer have to rely on third-party programs to open an SSH server and connect to a Windows machine. While still a beta feature, this represents a long-overdue update fulfilling a promise made back in 2015.
Hello, I'm a new guy around here and since I'm not seeing much tutorials in C i thought of contributing with something relatively simple. This will be a short series.
Hello guys I am ROMEO 64 (sounds weird I guess but who cares. :D).. Alright....Ever wondered what happens when you login to your Facebook account?

OK, In my last Tutorial we made a Server for sending Instructions to a Client. This time we will build the Client. Fire up your favourite Python environment and get the Code here.

hello hackers,newbies and followers of this great community, after some research here in our community, I noticed that there is not even one tutorial that teach Web Development. We have a lot of tutorials on how to hack web site but many do not know exactly how a web site is composed, then I decided, meeting the community's needs, begin to teach people how to develop web sites.

Welcome back, my nascent hackers! In the conclusion of the Mr. Robot television series, Elliot and fsociety successfully completed their mission of encrypting all of Evil Corp's data with AES-128 encryption and destroying the key.

Welcome back, my greenhorn hackers, and happy New Year! Now that your heads have recovered from your New Year's Eve regaling, I'd like to grab your attention for just a moment to preview 2015 here at Null Byte. I hope you will add your comments as to what you would like to see, and I'll try to honor as many requests as I can.

Welcome back, my greenhorn hackers! In previous Wi-Fi hacking tutorials, I have shown you ways to create an Evil Twin, to DoS a wireless AP, and to crack WEP and WPA2 passwords, but in this tutorial, I will show you something a little bit different.

Probably SSH is not as clean and fast as other useful tools like netcat, but it has some features which are very useful, and when you'll need them, here's how to behave with that huge amount of computers all over your house.

Welcome back, my budding hackers! Recently, I showed you how you could exploit the widely disseminated OpenSSL vulnerability that has to become known as "Heartbleed". Although the world has known about this vulnerability for over a month now, it will likely take many more months—or even years—for everyone to close this vulnerability.

Welcome back, my amateur hackers!

Welcome back, my hacker novitiates! Many of you have probably heard of a man-in-the-middle attack and wondered how difficult an attack like that would be. For those of you who've never heard of one, it's simply where we, the hacker, place ourselves between the victim and the server and send and receive all the communication between the two.

Welcome back, my hacker novitiates! In an earlier Linux Basics tutorial, I had demonstrated the basics of the Apache web server. Since Apache is the world's most widely used web server on the Internet (as of July 2015, Apache was 38%, IIS was 26%, and Nginx is 15%), the more you know about it and understand it, the more success you are likely to have hacking it.

Welcome back, my neophyte hackers! In previous tutorials, we learned how to steal system tokens that we could use to access resources, how to use hashdump to pull password hashes from a local system, and how to grab password hashes from a local system and crack them.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Welcome back, my greenhorn hackers!
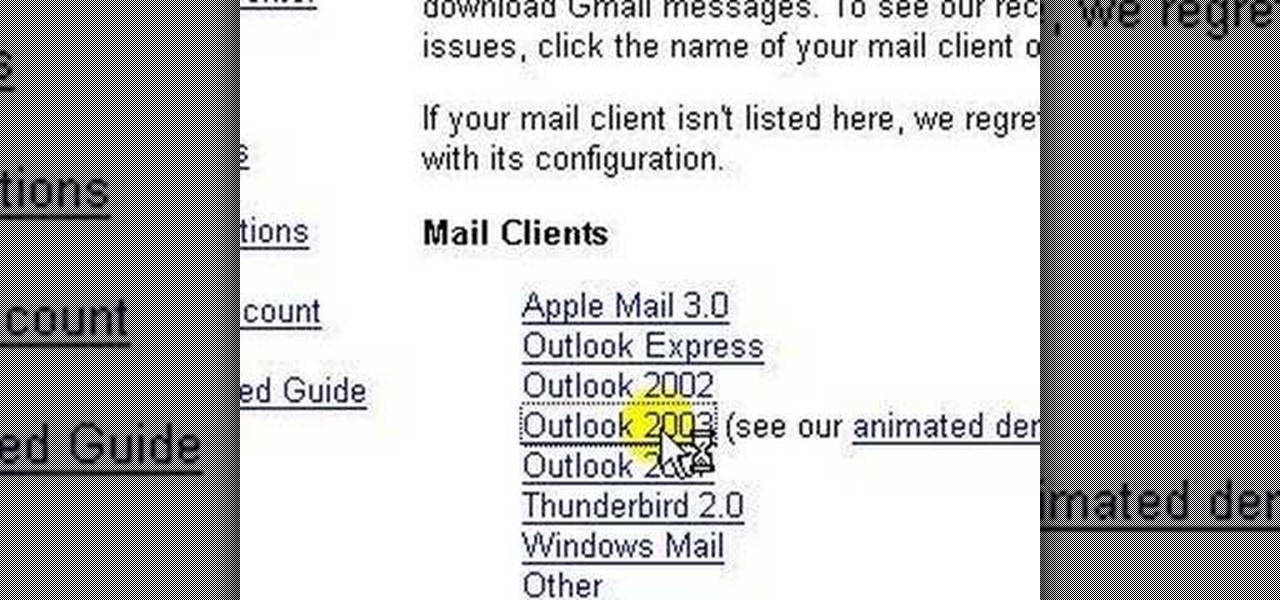
lakercoolman shows us how to set up our gmail account with this quick tutorial. Basically outlook express is a program that helps us to organize our email with added features such as contacts, to do lists and calender entries. Its an offline email client that allows us to work offline and also lets us set up exchange servers aswell. Ohter email servers such as hotmail and yahoo charge for thios service but the advantage of gmail is that IMAP or POP access is free. in ofer to set up, navigate ...
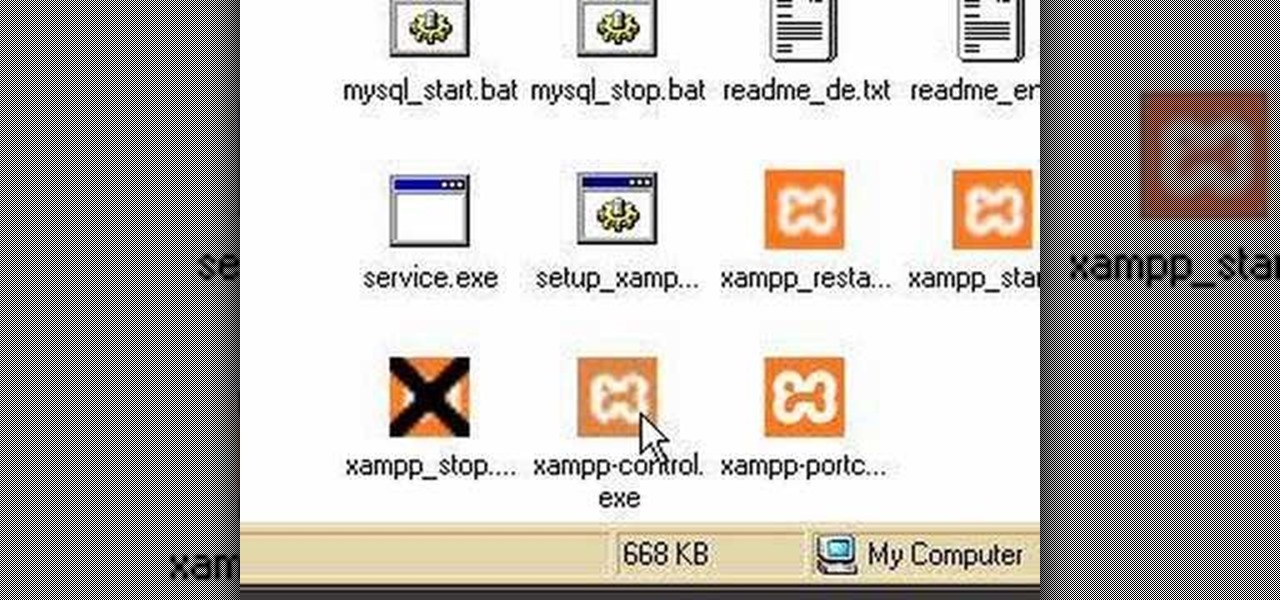
Using a simple peice of software XAMMP to streamline the setup process of apache+php+mysql

Hello everyone, In this video I will be going over what in my opinion are the top 10 bukkit plugins to make a great minecraft server. First thing I would like to state is that Essentials or commandbook was not featured in the video because I didn't want to feature something that big (or essential). I would also like to say it really does matter what kind of server you are going to be running becuase different types of server need different types of plugins.

Video: . Download: here
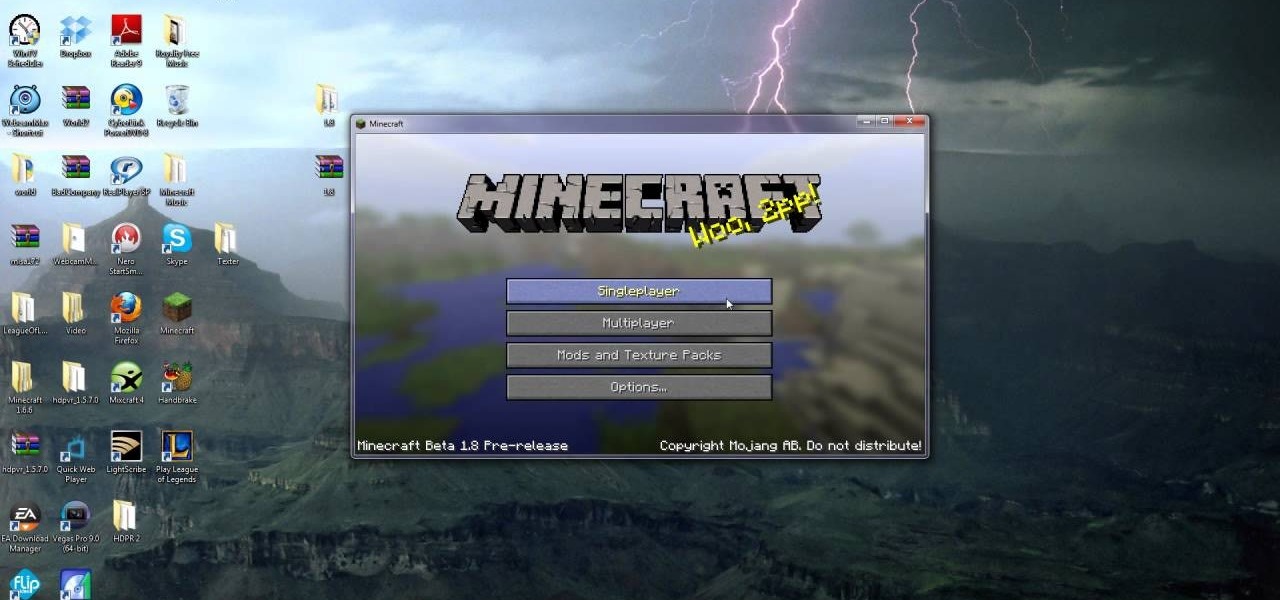
If you want to play the Minecraft 1.8 pre-release you can try it out on a test server. This guide shows you how to download and install the Minecraft 1.8 pre-release and try out the beta on a server before the official release comes out. It also details how to uninstall Minecraft 1.8 so that you can play Minecraft 1.7.3 instead if you have problems starting or playing the newer version.
In this video we learn how to use a proxy server to hack PS3 store. First, go to settings and then internet settings. From here, go to the custom method and then click continue until you see the option for a proxy serve. Then, enable this with it and make sure all your connections are automatic. Then, your internet connection will be tested. When it's finished, test out the connection to see if it's working. Then, go to the PS3 store and you should be able to hack it using your proxy server. ...
In this clip, you'll learn how to get started using Symantec Backup Exec to protect SharePoint & Exchange servers. It's easy! So easy, in fact, that this helpful how-to can present a complete overview of the app in just under five minutes. For more information, including detailed, step-by-step instructions, take a look.