If you or someone you're shopping for has a newer iPhone model or an Android smartphone like the Galaxy Note 9 or Pixel 3, they come with wireless charging capabilities. Problem is, they don't come with wireless chargers. But there's no better time to snag one than on Black Friday, and we've found the best deals out there for 2018's holiday season.

Hundreds of Windows 10, macOS, and Linux vulnerabilities are disclosed every single week, many of which elude mainstream attention. Most users aren't even aware that newly found exploits and vulnerabilities exist, nor that CVEs can be located by anyone in just a few clicks from a selection of websites online.

While many are familiar with Samsung, I'm pretty sure most Americans couldn't name the second-largest smartphone OEM. It's actually Huawei, and they recently released a spec-sheet dream of a phone in the Mate 20 Pro. So naturally, we wanted to see how it compared to the largest OEM's best offering.

Late last year, we got a little surprise from Razer. The gaming company released its first smartphone, and as expected, it targeted gamers. Branded as a gaming phone, it started a trend which several other companies followed soon after, including ASUS, Xiaomi, and even Samsung. So as you can imagine, many are excited about its successor.

This week, we continued our NR30 series highlighting the leaders of augmented reality space by profiling the venture capitalists and strategic corporate investors that sustain the industry.

Having an efficient workflow is an integral part of any craft, but it's especially important when it comes to probing apps for vulnerabilities. While Metasploit is considered the de facto standard when it comes to exploitation, it also contains modules for other activities, such as scanning. Case in point, WMAP, a web application scanner available for use from within the Metasploit framework.

The new iPhone XR, XS, and XS Max have everyone buzzing. But, at first glance, the XR and XS look pretty similar in almost every way. So, what's the difference? It comes down to the XR's "Liquid Retina" LCD screen vs. the XS's "Super Retina" OLED display. How do they compare, and why does it matter when considering which new iPhone to preorder?

In iOS, the Control Center is an easy way to toggle settings such as Wi-Fi, Do Not Disturb, and Low Power Mode. Its Android counterpart is called "Quick Settings," which provides much of the same functionality with a few bonuses. If you're curious about how this toggle menu works or miss having it before you made the switch from Android, you can test it out on your iPhone right now.

If you want the best two-factor authentication app out there, our pick is Authy. A close second is LastPass Authenticator. If neither of those is to your liking, try Duo Mobile or Microsoft Authenticator. But if you're fine with missing out on great features, then and only then should you look at using Google Authenticator.

UPDATE: The ported APK covered below is now obsolete because Fortnite beta is officially available for all Android devices!

Web application vulnerabilities are one of the most crucial points of consideration in any penetration test or security evaluation. While some security areas require a home network or computer for testing, creating a test website to learn web app security requires a slightly different approach. For a safe environment to learn about web app hacking, the OWASP Juice Shop can help.

While many of you were off surfing and lounging on some sandy beach or trying to figure out how to balance work with sky-high summer temperatures, I've been talking to all the companies that make augmented reality what it is today.

While Sony as a company is well-known in the United States, it smartphones are not. For years, Sony has stuck with a boxy design with sharp edges and large bezels — however, they're finally getting with the trends. As a result, the Xperia XZ2 Premium offers a rare combo: A super powerful phone which is also pretty sexy.

With all the web applications out on the internet today, and especially the ones built and configured by novices, it's easy to find vulnerabilities. Some are more perilous than others, but the consequences of even the slightest breach can be tremendous in the hands of a skilled hacker. Directory traversal is a relatively simple attack but can be used to expose sensitive information on a server.

During E3, many major game developers announced plans to bring console and PC franchises to mobile. These titles are designed for more serious gamers with competition in mind. All of this points to a shift in mobile hardware priorities — soon, gamers will need gaming phones just like PC players need a gaming rig.

Apple first included a dual-lens camera onto its iPhone 7 Plus back in late-2016, yet not many developers besides Apple have harnessed the depth data that "Portrait" mode photos provide. A relatively new app is changing that, though, by using that depth information to let you add realistic-looking light sources to your photos.

Now that ARCore is out of its developer preview, it's time to get cracking on building augmented reality apps for the supported selection of Android phones available. Since Google's ARCore 1.0 is fairly new, there's not a lot of information out there for developers yet — but we're about to alleviate that.

A core concept that has resonated through societies of the world over the course the last few hundred years is "knowledge is power." And understanding that concept gives us the drive to push further forward and learn as much as we can on a subject. At the moment, that subject for us at Next Reality is the recently released information about Magic Leap's upcoming Magic Leap One: Creator Edition.

Getting an insider view of the goings-on at Magic Leap is hard to come by, but occasionally, the company lets one of its leaders offer a peek at what's happening at the famously secretive augmented reality startup. One of those opportunities came up a few days ago when Magic Leap's chief futurist and science fiction novelist, Neal Stephenson, sat for an extended interview at the MIT Media Lab.

Since its introduction, the Bixby button has been a big point of contention among Galaxy fans. Many view the dedicated button as a wasted opportunity, which they argue could be put to better use if Samsung would let them use it for other commands. Thanks to an awesome app, you'll be able to remap the Bixby button on your Galaxy S9 to perform almost any function.

BlackBerry has formally unveiled its latest flagship, the KEY2, during an exclusive event in New York. The Android-powered KEY2 retains its distinctive BlackBerry aesthetics with a physical QWERTY keyboard. Here's all the juicy details regarding Blackberry's followup to the venerable KEYone.

After a long hiatus, we shall once again emerge from the shadowy depths of the internet to build an exploit. This time, we'll be looking at how to defeat a non-executable stack by using the ret2libc technique — a lean, mean, and brilliant way of exploiting a stack overflow vulnerability.

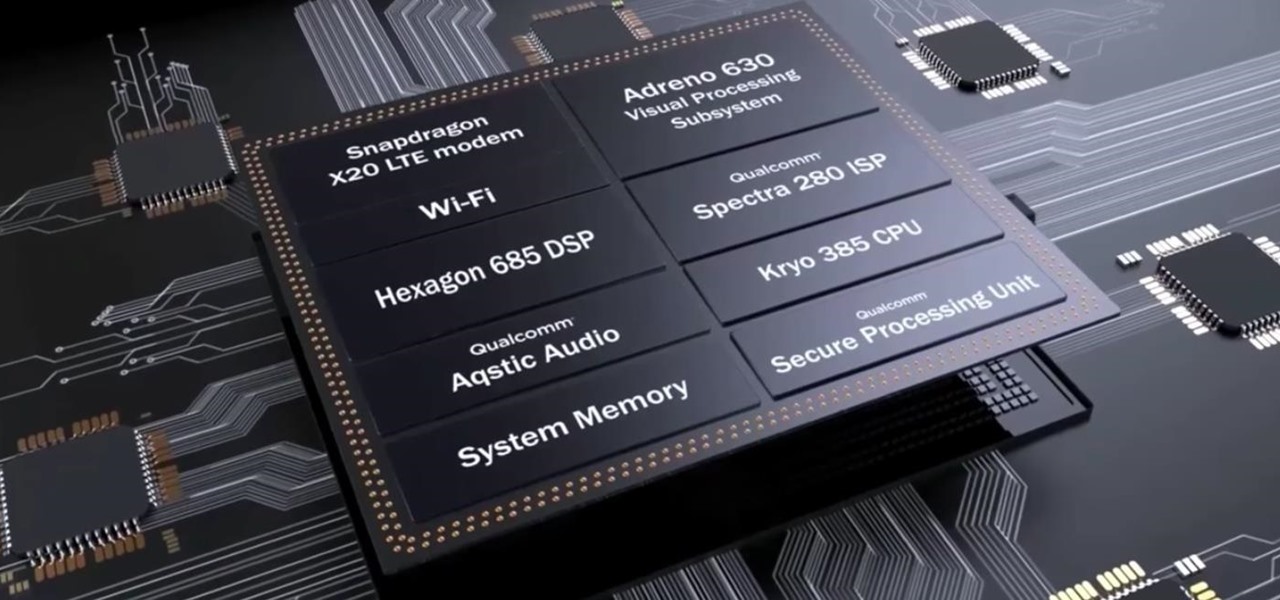
After the success of the Snapdragon 835, Qualcomm now has its eyes set towards the future with the arrival of its next-generation SoC, the Snapdragon 845. Debuting alongside the Samsung Galaxy S9, the 845 is now set to take over the market for flagship Android phones in 2018.

2017 was a down year for HTC. First, the U11 and U Ultra were widely criticized. Later, Google purchased a large chunk of HTC's manufacturing division, leaving the Taiwanese company running with a skeleton crew after losing 2,000 key employees. But that's not stopping HTC — their flagship U12+ was just announced, and it's quite impressive.

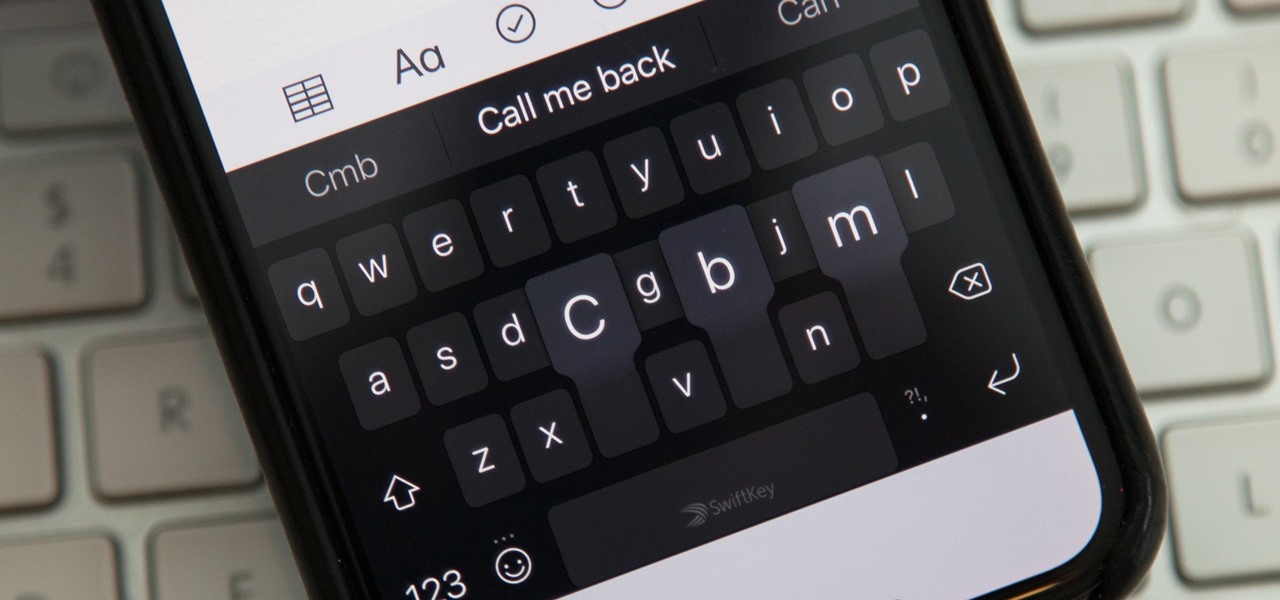
While you're probably already used to the keyboard on your iPhone, you'll likely never be able to type on it as fast as you can on a computer keyboard. But that doesn't mean you can't get any faster at typing on your iPhone. By using keyboard shortcuts to auto-populate commonly used phrases, email addresses, and other big-character items, you can drastically speed up your virtual keyboard skills.

Android users have had access to live wallpapers since the Eclair days, but some newer apps have made this feature even more useful. Now, you have the ability to use GIFs as your wallpaper, and through the marvels of modern technology, you can even set a video as your home screen and lock screen background.

OnePlus is on track to deliver Android 8.0 Oreo to its flagship users by Q1 2018. Open Beta 1 was released for the 5T in late December, and we just received Open Beta 2. But this update isn't just tweaks and bug fixes, OnePlus has included a few new features to enhance the Android experience.

In 2017, major breakthroughs in smartphone-based simultaneous localization and mapping (SLAM) opened up new doorways for developers and users of both Apple and Android phones. Unfortunately for Android users, the solution that Google is previewing, ARCore, currently only works on three Android smartphones. But Silicon Valley start-up uSens is stepping in to fix that with its new engine called uSensAR.

Whether you're a veteran augmented reality developer looking for a quick access point to add a new platform to your arsenal or just getting started with your first AR head-mounted display, get ready to start developing for the Meta 2.

As the calendar year (and, for many companies, the fiscal year) comes to a close, it appears 2017 may stand as the new high-water mark for investment in augmented and virtual reality technology.

It finally happened! In a world of "go big or go home," Magic Leap has finally done something other than tease us with vague promises and rendered video concepts. Although, other than actually showing us what the developer's kit will look like, it seems little more than a slightly different kind of a tease. To demystify this new product, we here at Next Reality decided to put together what we know about the hardware.

Connecting to your headless Raspberry Pi on the go typically requires a network connection or carrying around bulky peripheral hardware like a screen and keyboard. With the help of an old-school connecting standard, though, you can log into your Pi from any computer using a simple cable. If you don't have a power source, you can also power your Linux distro over the cable at the same time.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

Razer just released their first flagship Android smartphone, appropriately named the Razer Phone. While mobile gaming fans are sure to enjoy the Razer Phone, the buttery-smooth 120 Hz display makes this an appealing option for anyone in the market for a new phone. If you've just picked up the Razer Phone or it's piqued your interest, here are ten awesome tips to hit the ground running.

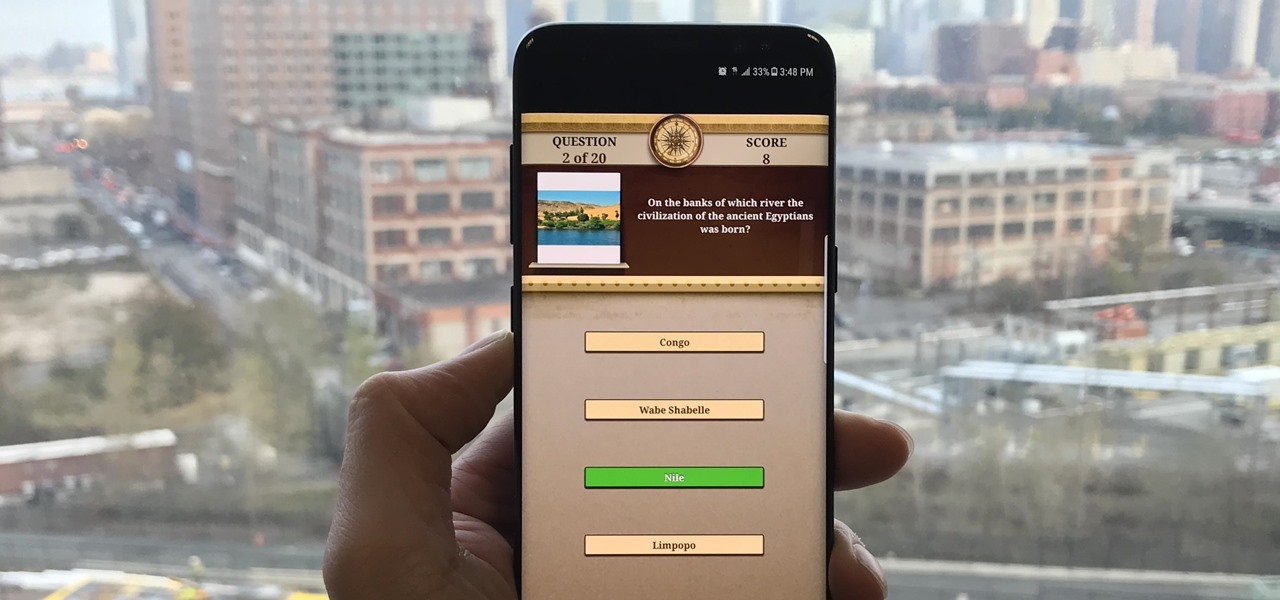
Trivia games are among the most entertaining ways to learn factoids and interesting info you may have never known about before. They're also the perfect genre to enjoy with friends and family, as they're particularly great at breaking the ice to make for a more memorable time together.

The last quarter of 2017 brought us some downright excellent smartphones. Between the iPhone X, Pixel 2, and Note 8, consumers have more fantastic options than ever when choosing a new device. It's now the perfect opportunity for Samsung to set the tone for 2018 smartphones with their exceptional S9 and S9+.

In a previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when a Microsoft Word document is opened. The biggest challenge of this attack is that it requires getting the user to agree to a pop-up prompt. Fortunately, since I posted that article, many new obfuscation techniques have been discovered to make this easier. Today, we explore and combine some of them to make the ultimate hidden DDE attack.

The iPhone X, iPhone 8, and iPhone 8 Plus may be some of the fastest phones of 2o17. However, the equally new iOS 11 isn't quite as impressive. That being said, Apple is continuing updates to the developer beta for iOS 11.1, as it releases the 5th version of the beta today.

Apple's iOS 11 release promises many improvements and fresh ideas. One of those new ideas is an image codec called HEIF (similar to HEVC for videos), designed to reduce the space photos take up on your iPhone. But it's so new that it's already causing issues with compatibility.

In 2013, Offensive Security released Kali Linux, a rebuild of BackTrack Linux derived from Debian. Since then, Kali has gone on to become somewhat of a standard for penetration testing. It comes preconfigured with a collection of tools accessible by a menu system, tied together with the Gnome desktop environment. However, Kali Linux isn't the only penetration-testing distribution available.